Top 7 Enterprise Risk Management Software in 2024




Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
Introduction
Organizations constantly face unique risk challenges while adapting to industry demands. 76% of organizations prioritize their enterprise risk management programs, showcasing the increasing recognition of ERM’s role in ensuring the organization’s success.
However, resource constraints, siloed operations, and ineffective tools often hinder security and risk management teams, jeopardizing timely threat detection and response. Choosing the right ERM solution can dramatically improve efficiency and response times, empowering organizations to address potential threats proactively.
This blog post will explore the top 7 Enterprise Risk Management software solutions. Each solution is designed to streamline processes, enhance decision-making, and align risk management with overall business objectives, ultimately driving organizational success.
What is Enterprise Risk Management software?
Enterprise Risk Management (ERM) software is a specialized tool that enables organizations to comprehensively identify, evaluate, and manage operational risks across its operations. It provides a centralized, holistic view of an organization’s exposure to a wide range of risks – strategic, financial, operational, compliance-related, and more – and how these different organizational risk factors intersect and impact one another. This integrated approach allows companies to align their overarching risk management strategies with their core business goals and objectives.
ERM software streamlines collecting and analyzing risk data, conducting risk assessments, generating reports to aid in decision-making, and monitoring adherence to pertinent regulatory mandates. The value proposition is clear – 52% of risk management leaders agree that organizations embracing an integrated methodology for identifying, evaluating, and responding to potential incidents will experience reduced overall risk exposure and superior outcomes.
Seven Best Enterprise Risk Management Tools in 2024
Enterprise Risk Management (ERM) tools offer data analytics, customizable process workflows, and insights into user activity across the organization to monitor vulnerabilities and potential risks in near real-time.
Core capabilities common to enterprise risk management systems include reporting functionalities, advanced analytics, risk prioritization, audit management, threat visibility and monitoring, risk profile assessment, and compliance management.
The following enterprise risk management (ERM) software solutions stand out as the top choices in the market based on comprehensive user reviews, in-depth feature evaluations, and a rigorous assessment of their key capabilities. These powerful tools empower risk management professionals to tackle compliance requirements head-on, identify strategic risks with precision, and conduct thorough analyses of their potential business impacts:
Here is a list of the top ERM software that have been stringently evaluated based on user reviews, feature evaluations, and an assessment of their key capabilities. These solutions empower risk professionals to not only meet the compliance requirements but also proactively identify strategic risks and analyze their potential business impacts:
Cyber Sierra

Cyber Sierra is an enterprise-grade cybersecurity platform engineered to empower security professionals by streamlining security controls, risk assessments, and vendor relationship management. By leveraging artificial intelligence and machine learning capabilities, Cyber Sierra delivers comprehensive insights into risks, vulnerabilities, and compliance postures, enabling proactive, data-driven decision-making.
Cyber Sierra tackles the complexities of cyber risk, simplifying security for businesses. Their intelligent platform delivers actionable insights into risks, vulnerabilities, and compliance. With their platform, you’ll rapidly identify critical threats, allowing you to protect your organization proactively.
Key Features
| Unified Governance | Facilitate compliance with globally recognized standards such as ISO 27001, SOC 2, HIPAA, GDPR, MAS Outsourcing, HKMA, and PDPA. |
| Threat Intelligence | An all-encompassing security solution offering to improve the organization's cybersecurity. It is conducive to receiving key insights about security conditions, scanning for vulnerabilities in internal networks, and managing them. |
| Cybersecurity Risk Management | Identify and contextualize security risks about your organization's assets. |
| Employee Awareness Programs | Provides the latest knowledge, skills, and resources necessary to identify and prevent potential attacks. This includes interactive quizzes, simulated campaigns, and continuous updates. |
| Third-Party Risk Management | Streamline the process of vendor security assessments and enable continuous risk monitoring in a unified platform. |
| Two-factor authentication (2FA) | Incorporates 2FA verification beyond just the password to access applications. |
Strengths
| Unified & Interoperable Platform | Combines governance, risk, cybersecurity compliance, cyber insurance, threat intelligence, and employee training capabilities in a single platform. |
| Continuous Control Monitoring | Provides near real-time monitoring of controls, enables risk assessments, and supports proactive threat management. |
| Seamless Third-Party Risk Management | Streamlines management of third-party vendors' risks with continuous monitoring. |
| Improved Compliance and Controls Management | Receive a deep monitoring and evaluation of the potential challenges that may impact your company. Additionally, get the proper measures to reduce the effect of the recognized problems. |
Best For:
Cyber Sierra is best suited for established enterprises and mid-to-late-stage startups grappling with regulatory compliance requirements, data security challenges, and compliance issues.
The platform is also immensely effective for enterprises seeking to consolidate their cybersecurity, governance, and insurance processes from multiple vendors into one intelligent platform. Book a free demo here.
Duo Security

Duo Security, incorporated into Cisco, is a cloud-based security platform that safeguards users, data, and applications from emerging threats. It verifies users’ identities and assesses the security posture of their devices before allowing application access, aligning with stringent business unit security and compliance mandates.
Key Features
| Two-factor authentication (2FA) | By providing a secondary form of verification beyond just the password, Duo improves the security of accessing networks and applications. |
| Device Trust | Device Trust scrutinizes every device attempting to access applications, ensuring it adheres to predefined security benchmarks before access is permitted. |
| Adaptive Authentication | By utilizing adaptive policies and machine learning, Duo tailors access security based on nuanced user behavior and device-specific insights. |
| Secure Single Sign-On (SSO) | Duo's SSO provides users with a streamlined, secure pathway to multiple applications, enhancing the user experience without compromising security. |
Strengths
| User-Friendly | Known for its intuitive interface and ease of deployment, Duo simplifies the user experience. |
| Robust Security | The platform’s reliance on two-factor authentication effectively minimizes the likelihood of unauthorized access. |
| Extensive Integration Capabilities | Duo integrates with various VPNs, cloud services, and network infrastructures. |
| Responsive Customer Support | Users frequently commend Duo for its proactive and helpful customer support team. |
Best For
Companies with various applications and devices will particularly benefit from Duo’s security framework.
Wiz
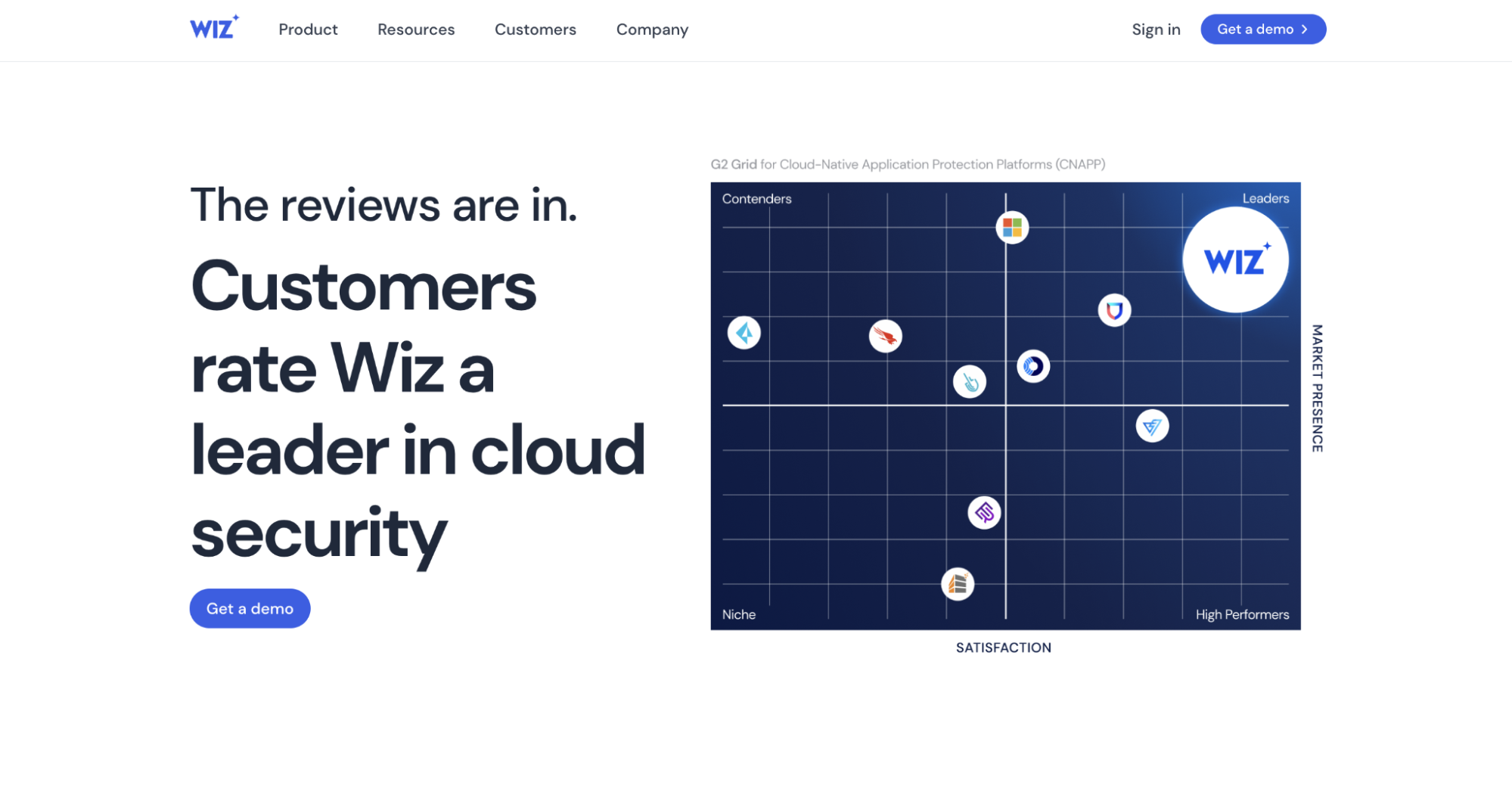

Wiz is a Cloud Security Posture Management (CSPM) platform that scans your cloud stack to uncover hidden vulnerabilities, misconfigurations, and emerging threats.
Key Features
| Comprehensive Visibility | Gain a complete, centralized understanding of security risks across your multi-cloud landscape. |
| Actionable Remediation | Receive clear guidance to address vulnerabilities and strengthen your security posture proactively. |
| Team Collaboration | Empower seamless cooperation between DevOps, security, and cloud infrastructure teams. |
| Real-time Insights and Monitoring | Detect new threats and misconfigurations as they arise for rapid response. |
Strengths
| Holistic Security | Benefit from a unified assessment across all major cloud platforms. |
| Powerful Automation | Streamline security processes with intelligent automation and intuitive dashboards. |
| Rapid Deployment | Experience fast setup and minimal configuration for quick time-to-value. |
Best For
Wiz is the choice for organizations operating in multi-cloud environments seeking a comprehensive cloud security solution.
Vanta

Vanta is a security and compliance management platform designed to streamline SOC 2 compliance. By continuously monitoring your technology stack, Vanta automates many tedious tasks in achieving and maintaining SOC 2 certification, saving you time and resources.
Key Features
| Continuous Monitoring | Ensures ongoing compliance with SOC 2 standards through real-time vigilance. |
| Automation | Simplifies and speeds up compliance processes, accelerating your path to SOC 2 certification. |
| Seamless Integrations | Connects effortlessly with cloud platforms like AWS, GCP, and Azure for a centralized view of your environment. |
Strengths
| Rapid Compliance | Reduces the time and effort needed to achieve and maintain SOC 2 compliance. |
| Easy Integration | Works seamlessly with your existing tech stack for straightforward implementation. |
Best For:
Vanta can be considered for mid-sized to large businesses, especially those in tech, healthcare, or finance, where strict security compliance is paramount.
AuditBoard

AuditBoard is a platform that streamlines the entire audit process, from planning and execution to reporting. It allows teams to manage compliance confidently, reduce risk, and minimize costly incidents across your organization.
Key Features:
| Centralized Control | A single dashboard provides a real-time, comprehensive view of auditable entities, risks, and key metrics. |
| Efficient Risk Assessment | Conduct risk assessments and pinpoint potential gaps in compliance coverage. |
| Seamless Issue Management | Track issues, assign ownership for remediation, and generate reports quickly and efficiently. |
| Standardized Workflows | Create audit templates and automate processes to ensure consistency and timely completion. |
Strengths
| Better engagement and response | Equips risk owners with insights to power up risk management across the company. |
| Scale Risk Management | Receive information about the risk environment from your organization's front line. Recognize operational weaknesses before challenges arise. |
Best For
Mid and large-scale companies looking for a solution to mitigate risks.
LogicGate

LogicGate is a solution that allows businesses to manage risk by streamlining and automating compliance processes proactively. Its centralized platform consolidates risk management, controls, and evidence collection, eliminating redundancy and boosting efficiency.
Key Features:
| Eliminate Silos | Connect internal controls across multiple frameworks to uncover gaps and overlapping compliance requirements, reducing wasted effort. |
| Automate Evidence Management | Automate control evaluations, notify relevant stakeholders, and securely link cloud-based evidence for streamlined documentation and reporting. |
| Increased Collaboration | Facilitate stakeholder engagement and demonstrate audit readiness by sharing progress and corrective action plans. |
| Audit Preparation | Continuously evaluate and optimize your governance, risk, and control programs to ensure a smooth audit cycle. |
Strengths
| Automate tedious tasks | Eliminate manual tracking and streamline compliance workflows. |
| Stay up-to-date on regulations | Receive alerts and updates on the latest compliance changes. |
| Reduce error | Minimize the risk of mistakes that lead to non-compliance. |
Best for
It is suitable for various industries, including software, telecommunications, banking, insurance, and investment services.
Sprinto

This cloud-based platform is a governance, compliance, and risk management toolkit, helping organizations to mitigate risks seamlessly throughout their operational ecosystem.
Key Features:
| Proactive Notification System | Notification triggers and flags for non-compliant actions direct to risk owners, providing deep insights into risk specifics, recommended actions, urgency, focal areas, and tailored data. |
| Integrated Risk Assessment | A function that delivers exhaustive risk data across the ecosystem, aiding teams in documenting acknowledged, transferred, and mitigated risks. |
| Risk Overview | A comprehensive risk overview for establishing compliance protocols, risk mitigation workflows, and ensuring thorough compliance. |
| Dynamic Risk Library Usage | Utilization of an extensive risk library for crafting a risk register, enabling the addition or removal of risks, application of numerous checks, and selection of tailored risk treatment strategies. |
Strengths
| Audit readiness support | Gather all the compliance directly from the platform and share it easily with the team. You can also include the auditor in the dashboard and share it for review. |
| Zero trust security | Offers to simplify and implement security compliant with the current security frameworks. |
Best for
It is a cloud-based solution, making it a good fit for organizations requiring a similar enterprise risk management system deployed into their tech stack.
How to Choose the Right ERM for Your Business?
When choosing the right ERM for your business, you must consider the following critical attributes:
- Evaluate your requirements
- Explore niche solutions
- Access the security
- Request for references
- User interface – Is it easy and intuitive to use?
- Scope for customization
- Integration capabilities
Selecting the right ERM solution for your business is critical for creating a successful risk management strategy. Additionally, with diverse enterprise risk management (ERM) software tools available in the market, choosing the right one can be challenging.
Now let’s take a detailed look at the critical attributes that you need to look for while deciding upon the right software –
Evaluate your requirements – Before looking for the right solution, you must be clear about your organization’s fundamental needs. Start with an extensive study or survey of all the requirements considering the organization’s different teams and their challenges and experiences. This would be beneficial in finding the right software that adheres to your organization’s particular needs.
Explore niche solutions – There is a wide range of risk management solutions available in the market. However, some tools cater to specific industries such as banking, energy, the construction sector, and so on. That’s why you must look for solutions that complement your niche, as they can offer focused features that might be helpful in managing the risks that your organization faces on a frequent basis.
Assess the security – Risk management often involves dealing with sensitive information, so choosing a secure solution that proactively protects your organization’s data privacy is non-negotiable. Always ensure the tool you select has robust security measures.
Request for references and opt for a trial – Before deciding upon the right tool, it’s a good idea to get references and have your organization experience it. This means be sure to go for a vendor that provides a trial period or demo to learn more about the tool. You can also ask the vendors for references from previous clients who have utilized the tool to learn about their experiences.
Apart from all the above-mentioned factors, you also need to ensure the solution has the following traits, which can help in making an informed decision –
- User-friendliness and intuitive user interface – Simple navigation in the ERM solution is crucial as it aids in a successful user experience for the entire organization.
- Scope for customization – The solution should adapt quickly to your company’s specific risk management needs and requirements.
- Integration – The solution should seamlessly integrate with other existing systems and processes in the company.
How can Cyber Sierra help you?
Cyber Sierra is a unified and interoperable risk management platform that integrates smart GRC (Governance, Risk, and Compliance), third-party risk management, continuous control monitoring, and cyber insurance capabilities. It combines features such as automated security alerts, threat intelligence feeds, vulnerability scanning, expert guidance, and employee security training, equipping organizations with the necessary resources to fortify their security posture.
The platform flags control breaks, control gaps, deviations, and non-compliant actions to risk owners, offering suggestions for risk mitigation and transfer through cyber insurance. Automated evidence collection, documentation, and detailed audit logs streamline risk management processes for mid to large-sized enterprises using Cyber Sierra.
Explore how Cyber Sierra can alleviate your security challenges by scheduling a demo call today.
FAQ
Here are some of the most common FAQs on the topic of Enterprise Risk Management (ERM) Software:
What is Enterprise Risk Management (ERM) Software?
Enterprise Risk Management Software is a specialized software solution designed to help organizations identify, assess, monitor, and mitigate various business risks across the entire enterprise. It provides a centralized platform for managing strategic, operational, financial, regulatory compliance, and other external risks in an integrated and holistic manner.
What are the critical features of ERM Software?
Standard features of ERM software include risk level identification and assessment tools, risk reporting and analytics, risk monitoring and tracking, compliance management, incident management, risk mitigation planning, and risk data aggregation from various sources. Advanced ERM solutions may also incorporate features like risk modeling, scenario analysis, and automated risk control testing.
What are the benefits of using ERM Software?
Key benefits of using ERM software include improved risk visibility across the organization, enhanced risk-based decision-making, better compliance with regulatory requirements, improved risk monitoring and early warning systems, centralized risk data management, and streamlined risk reporting. ERM software can also help organizations optimize risk management processes and resource allocation.
Who typically uses ERM Software?
Organizations across various major industries, including financial services, healthcare, manufacturing, energy, and more, use ERM software. It is commonly adopted by large enterprises with complex risk landscapes but can also benefit smaller organizations. Key users within an organization include risk managers, compliance officers, internal auditors, and senior executives responsible for risk oversight.
How is ERM Software deployed?
ERM software can be deployed in various ways, including on-premises (installed on the organization’s servers), cloud-based (hosted by the software vendor), or as a hybrid solution. Cloud-based deployments are becoming increasingly popular due to their scalability, accessibility, and reduced IT overhead. The deployment method chosen often depends on the organization’s IT infrastructure, data security requirements, and budgetary considerations.



A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.