Enterprise TPRM Buyer’s Guide for CISOs





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
You deserve a pat on the back.
In case you’re wondering why, here goes. Taking the time to explore enterprise TPRM software buyer’s guide before buying one reminds me of this famous Abraham Lincoln-attributed quote:


All things being equal, a sharpened ax will chop down a tree more effectively and efficiently. But you need some time to sharpen it, as Lincoln wisely opined. Similarly, the right third-party risk management (TPRM) tool is like having processes pre-sharpened to be more effective and efficient at tackling all 3rd party risks. But due to the ever-changing cyber threat landscape, choosing the right one requires investing some time to know what works best today.
And the first step is to…
Understand Today’s TPRM Lifecycle
To stay competitive, Gartner’s research found that up to 60% of organizations now partner with over 1,000 3rd party vendors. This number, the study noted, will only increase, giving security teams like yours more work to do. But the most worrying part is what the same research also found: A whopping 83% of organizations identify third-party risks long after performing initial due diligence.
This insight is instructive for chief information security officers (CISOs) and tech executives like you. It calls for a need to rethink the old way of assessing and managing vendor risks. Specifically, it means you must go beyond initial due diligence and perform ongoing categorization, swift remediation, and ongoing monitoring of third party vendors partnering with your company to be able to deal with risks promptly.
That’s what today’s TPRM lifecycle entails:
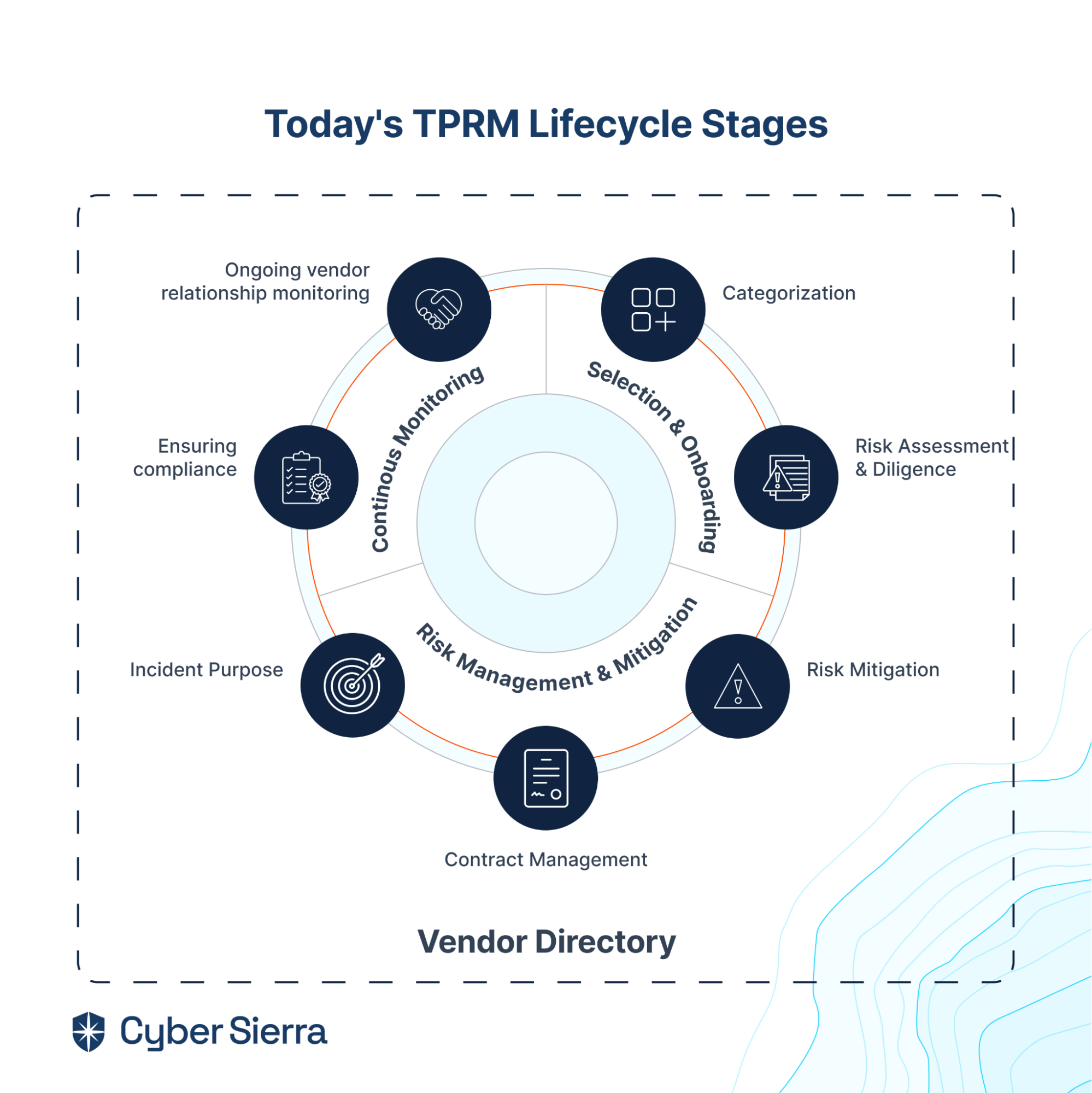

A great way to address each stage and step of the TPRM lifecycle illustrated above is through a unified platform with holistic vendors’ directory management capabilities. With that, at every step of the process, your security team can implement and maintain an effective and efficient TPRM program without losing context of other steps.
Which brings us to…
What to Look Out for in an Enterprise TPRM Solution
Irrespective of your organization’s unique situation, there are must-haves to look out for in an enterprise TPRM platform given today’s precarious threat landscape. The rest of this guide explores those crucial features, so you can make a more informed decision as you embark on buying and adopting an enterprise TPRM solution.
1. Holistic Vendor Directory
Imagine waking up to the news that a severe cyberattack has breached the data of many tech companies located in Singapore. Knowing your company partners with third-party vendors located in Singapore, you’d want to ensure they aren’t among those affected.
Doing that would be a stretch without a TPRM platform with holistic vendor directory capabilities. If the tool you choose lacks this feature, your vendor risk management team will rely on a mishmash of spreadsheets —with disconnected and disorganized pieces of information about the vendors your company is working with.
And it’d be difficult for you, the security leader or tech executive, to quickly filter and find specific lists of vendors any time the need arises. A holistic vendor directory solves that in three ways:
- All vendors’ info management: From documents, to risk profiles, and policies in a centralized cloud-based platform.
- Automatic segmentation: Leverages attributes like vendor location, vendor tiers, and others to automatically segment third-parties in your overall vendor ecosystem.
- Easy searchability: Ability to quickly filter and find vendors that match whatever criteria relevant to you at any given time.
Based on what’s itemized above, here’s how to view a holistic vendor directory. It is a central place where all details of past and existing third-party vendors working with your organization can be easily filtered and retrieved by authorized persons.
2. Selection & Onboarding
Each time a new 3rd party is allowed into your vendor ecosystem, varying degrees of new cyber risks are introduced. The extent to which your team can know which vendors are likely to introduce more risks depends so much on how well you select and onboard them.
This is why vendor selection and onboarding is the first stage of the TPRM lifecycle. It sets your cybersecurity team up to manage each third-party allowed into your vendor ecosystem successfully:
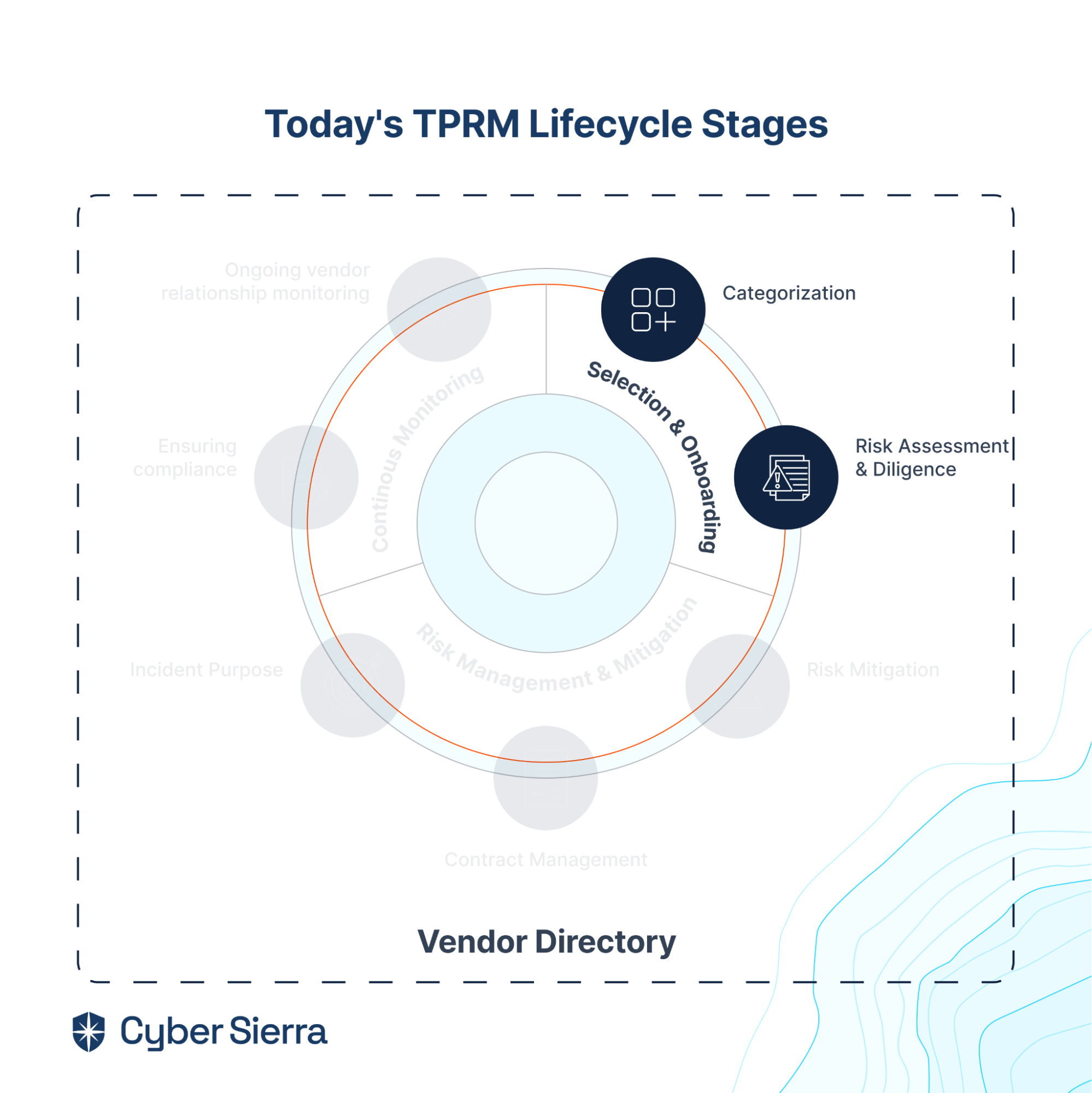

As shown, the two steps in this stage, categorization and risk assessment and due diligence, helps your team tier vendors to be prioritized for ongoing risk monitoring. So vendor selection and onboarding capabilities a TPRM platform should have are:
- Pre-onboarding risk analysis: Streamline the risk-profiling process for new vendors through security assessment surveys.
- Customizing assessments: Enable leveraging standard vendor assessment templates like NIST and ISO, and the ability to customize them per your organization and vendor needs.
- Pre-contract due diligence: Automate the cybersecurity due diligence processes before vendor contracts are approved.
- Multiple vendor tiering: Automatically segmenting vendors into multiple tiers such as those with inherent or critical risks.
An easy way to simplify achieving the steps above is to start with standard cybersecurity assessment frameworks like NIST and ISO. Once you can customize any of these to your company’s specific needs, the other things can easily fall into place.
3. Risk Management & Remediation
To win your company’s business, third-party vendors will do everything within their power to pass initial security assessments. But once most are in, they become lackluster about security. This is why you shouldn’t rely on the first, positive impressions of vendors.
It’s also why your cybersecurity team needs processes in place for managing and remediating vendor risks should they emerge. This TPRM lifecycle stage ensures that, and its importance is shown in the fact that it has the most steps compared to other two stages:
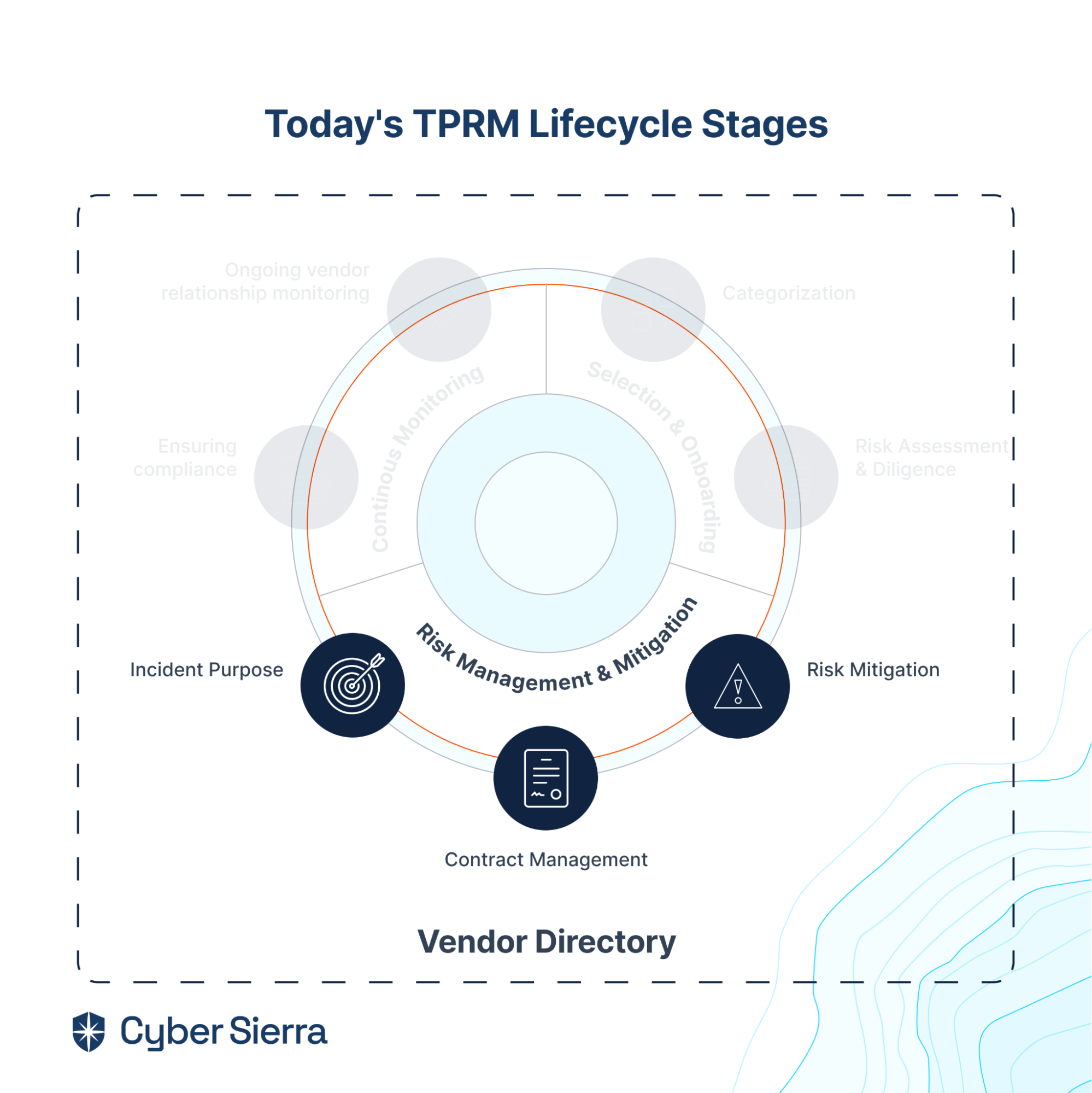

So after guiding vendors through onboarding and performing due diligence, seek a TPRM platform that also helps your team to:
- Track security assessment progress: Streamline the process of tracking the due dates and review statuses of sent security assessment questionnaires across all vendors.
- Re-populate questionnaires: Use answers previously submitted by vendors to re-populate questionnaires for what has changed.
- Auto-score assessment responses: Automatically score responses and evidence provided by vendors to security assessment questions to understand possible risks.
- Get swift incident response insights: Access actionable, in-context insight for responding to and remediating risks.
- Adjust vendor contracts: Append changing risk profiles of vendors to relevant sections of their contracts and streamline the processes of using the same to request contract adjustments.
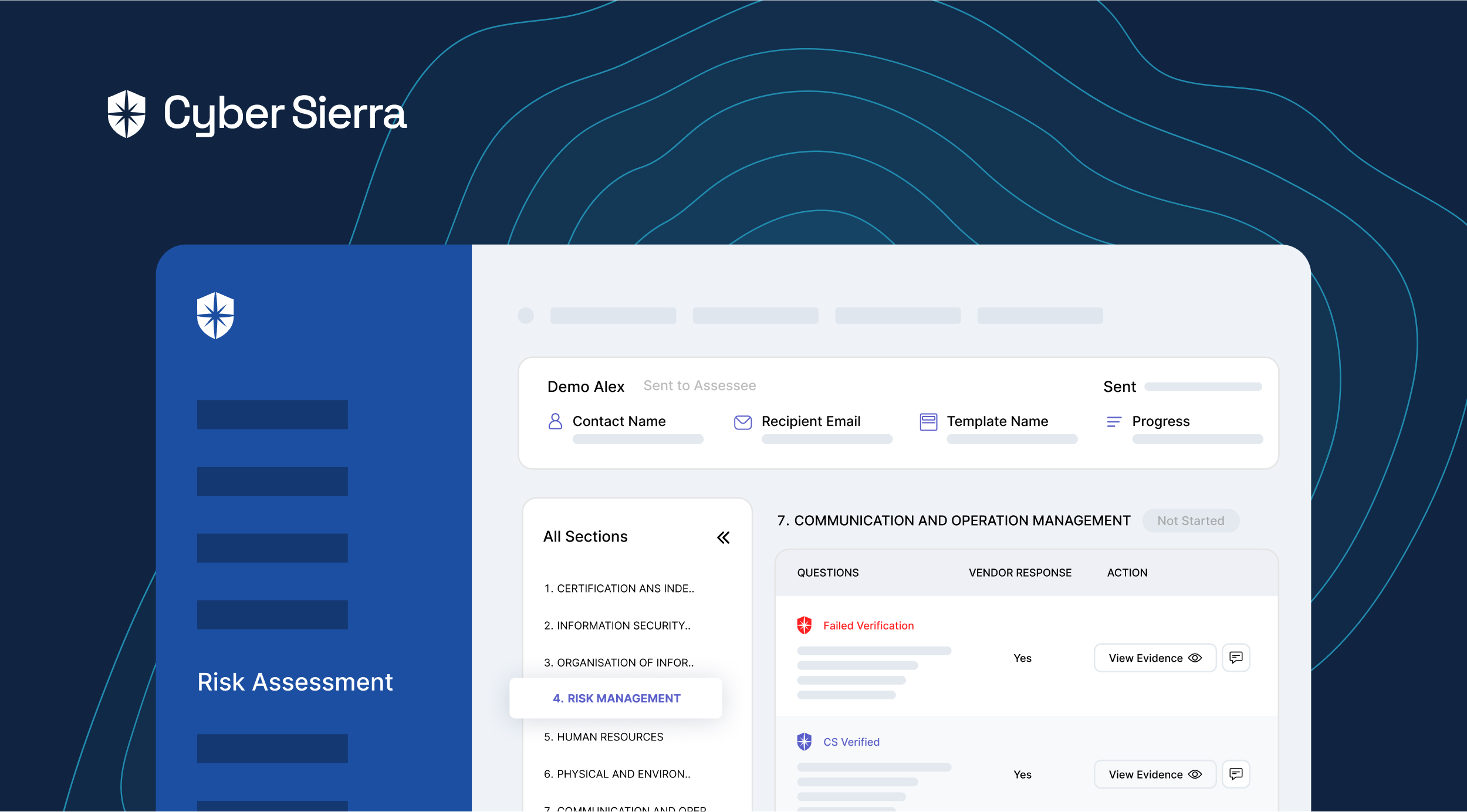
Even with all these in place, in most cases, managing and remediating risks requires vendors to make adjustments to their internal systems that are outside your team’s control. This requires collaborating with vendors whenever the need arises. And to be effective, communicating with them should be streamlined and in-context of specific risks. As you’d see below, the TPRM comments’ feature on Cyber Sierra enables that.
4. Continuous Vendors’ Monitoring
As the cyber threat landscape evolves, so would 3rd parties in your company’s vendor ecosystem need to adjust to changing regulatory requirements. But the onus is on your security team to ensure vendors are staying compliant with those changing compliance regulations. Failure to do this can result in collateral data breach damages and the hefty regulatory fines that come with them.
Avoiding such requires continuous vendor monitoring. First to ensure adherence to evolving compliance requirements. And second to reap the added advantage of identifying and proactively remediating risks from all vendor relationships before it’s too late.
This stage of the TPRM lifecycle addresses both:
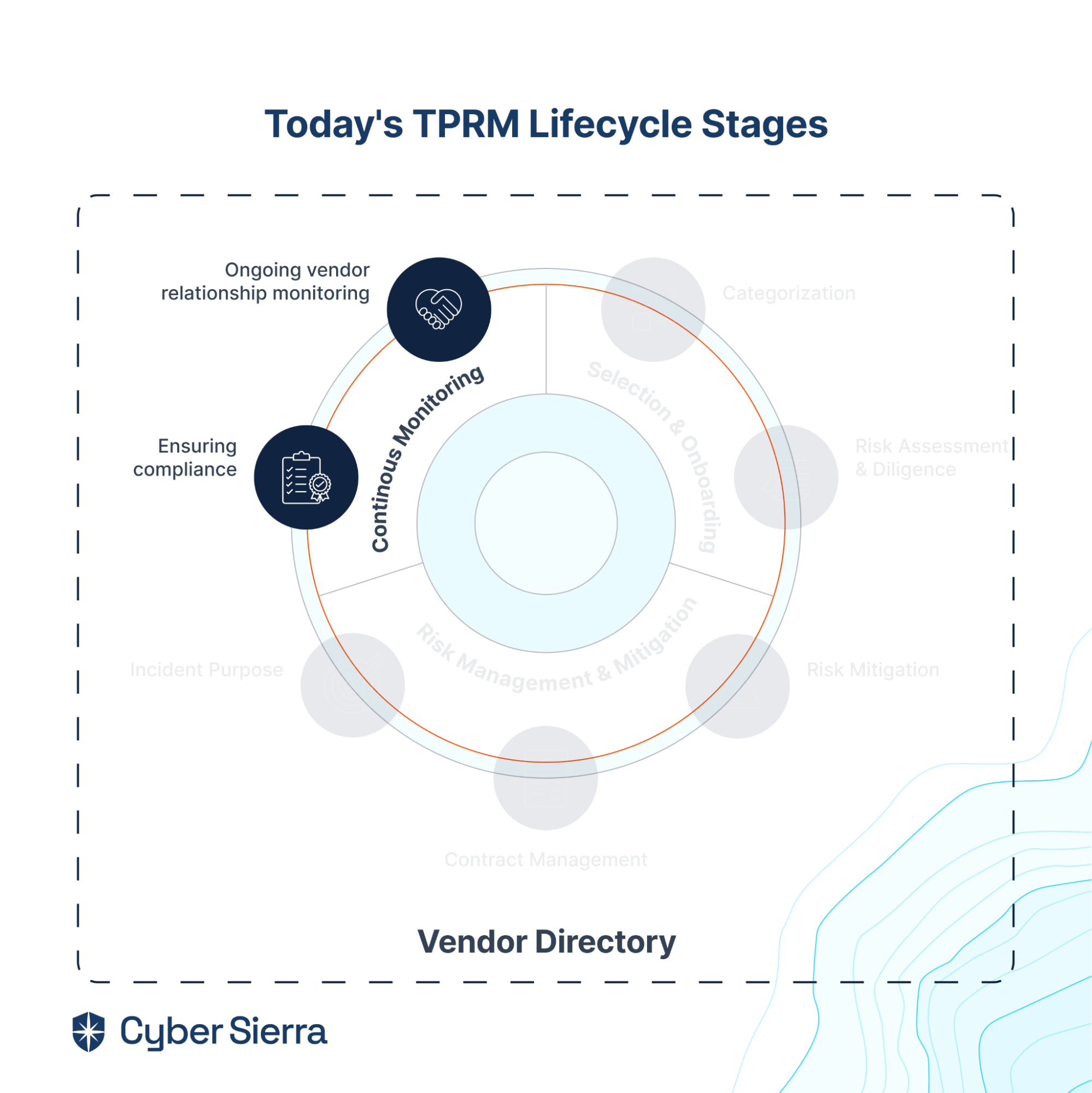

TPRM capabilities needed here are:
- Real-time vendor monitoring: Track vendors’ posture against compliance failures and cybersecurity risks in real-time.
- Continuous risk trends’ visibility: Gain comprehensive, continuous visibility into vendors’ statuses against evolving risk trends and regulatory compliance requirements.
- Auto-risk flagging and scoring: Flag all risks and automatically assign scores to each, enabling your team to prioritize.
- Actionable remediation insights: Provide useful insights your team can use to prevent data breaches and compliance failures.
These continuous vendor risk monitoring capabilities are pre-built into Cyber Sierra’s TPRM suite. And it’s one of the reasons a global bank headquartered in Singapore relies on us for its TPRM needs.
More on that below.
Choosing the Right TPRM Tool
Even with everything above checked, are there other things to consider before choosing an enterprise TPRM platform?
There are, so let’s discuss them.
1. Adaptability
This one goes both ways.
As much as vendors need your organization’s business, your organization also needs vendors to stay competitive. The implication of this is that a TPRM platform must be adaptable to both parties.
On the one hand, it should streamline your team’s processes of managing risks posed by vendors. On the other hand, it should also streamline the steps vendors need to answer security assessment questions and provide necessary compliance evidence.
No party should feel like it’s extra work.
2. Interoperability
Third-party risk management is crucial. But it is one piece of risk management in the overall enterprise governance, risk management, and regulatory compliance (GRC) pie:
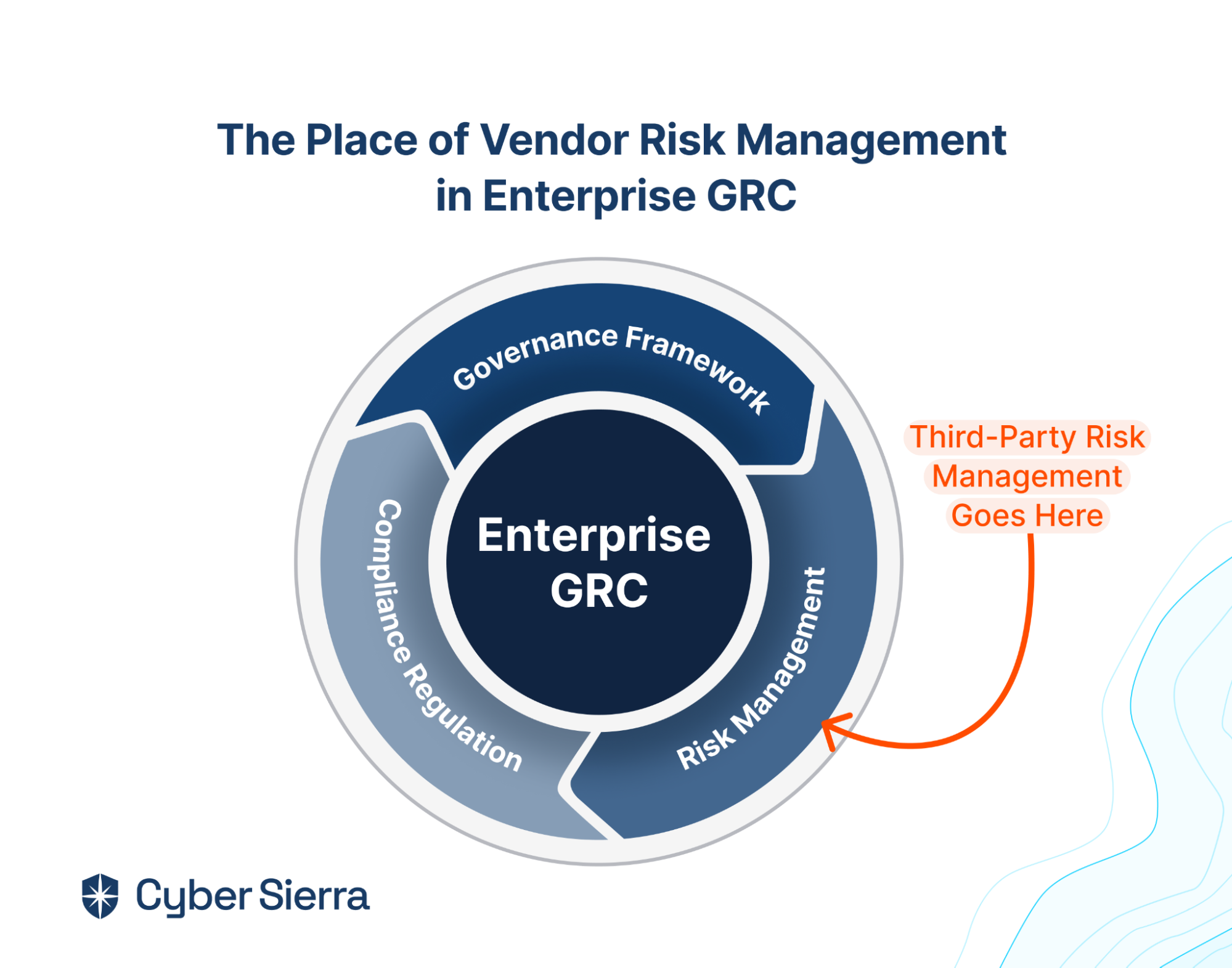

Consider this when choosing a TPRM solution. Because if you choose a point TPRM tool, you’d also need to spend hard-earned resources on other tools for cybersecurity governance and compliance. In addition to wasted spend, point cybersecurity solutions have other downsides.
Says Matt Kapko of CybersecurityDive:


To avoid these issues, seek a platform where your team can tackle vendor risks in the context of your company’s security governance, overall risk management, and regulatory compliance, all in one place.
This is why interoperability is crucial and should be prioritized.
3. Value
While price is a major consideration with any enterprise software purchase, what you really want to focus on is the value you’d get. And staying with the need for interoperability over a point tool, it makes sense to prioritize a TPRM solution with full-fledged capabilities for tackling interrelated, enterprise cybersecurity needs.
Some things to look out for are:
- Beyond TPRM, does it provide a centralized solution suite for addressing other cybersecurity concerns from one place?
- Is there unlimited access, so your core security team and employees can collaborate in tackling cybersecurity?
- Can you integrate all tools and services across your organization for continuous scanning for threats and cyber risks?
- Can you customize the platform, per your organization’s specific cybersecurity needs?
- Is the platform enterprise-ready and built to scale as teams across your organization, cybersecurity, regulatory compliance, and vendor risk management needs grow?
The correct answers to these questions varies from one company to another and will ultimately depend on a company’s unique needs. So to get the most value out of a TPRM solution, it’s best to reach out and see if it can be tailored to your needs before talking about pricing.
Try Cyber Sierra, the Interoperable TPRM Platform
All TPRM solutions aren’t created equal.
Most are built to be pure-play or point TPRM tools. As stressed in this guide, the downside is that your team can end up with more vulnerabilities if a tool doesn’t work well with other tools in your tech stack. This is why to get the most value, consider a comprehensive, interoperable cybersecurity platform with full-fledged enterprise TPRM capabilities.
If that sounds inviting, here are just two reasons to try Cyber Sierra.
First, our TPRM suite has a holistic vendor inventory directory that automatically updates once a new 3rd party enters your vendors’ ecosystem. This capability enables authorized persons in your team and across the company to filter specific vendors at any time, using various filtering options like location, vendor type, status, and so on:
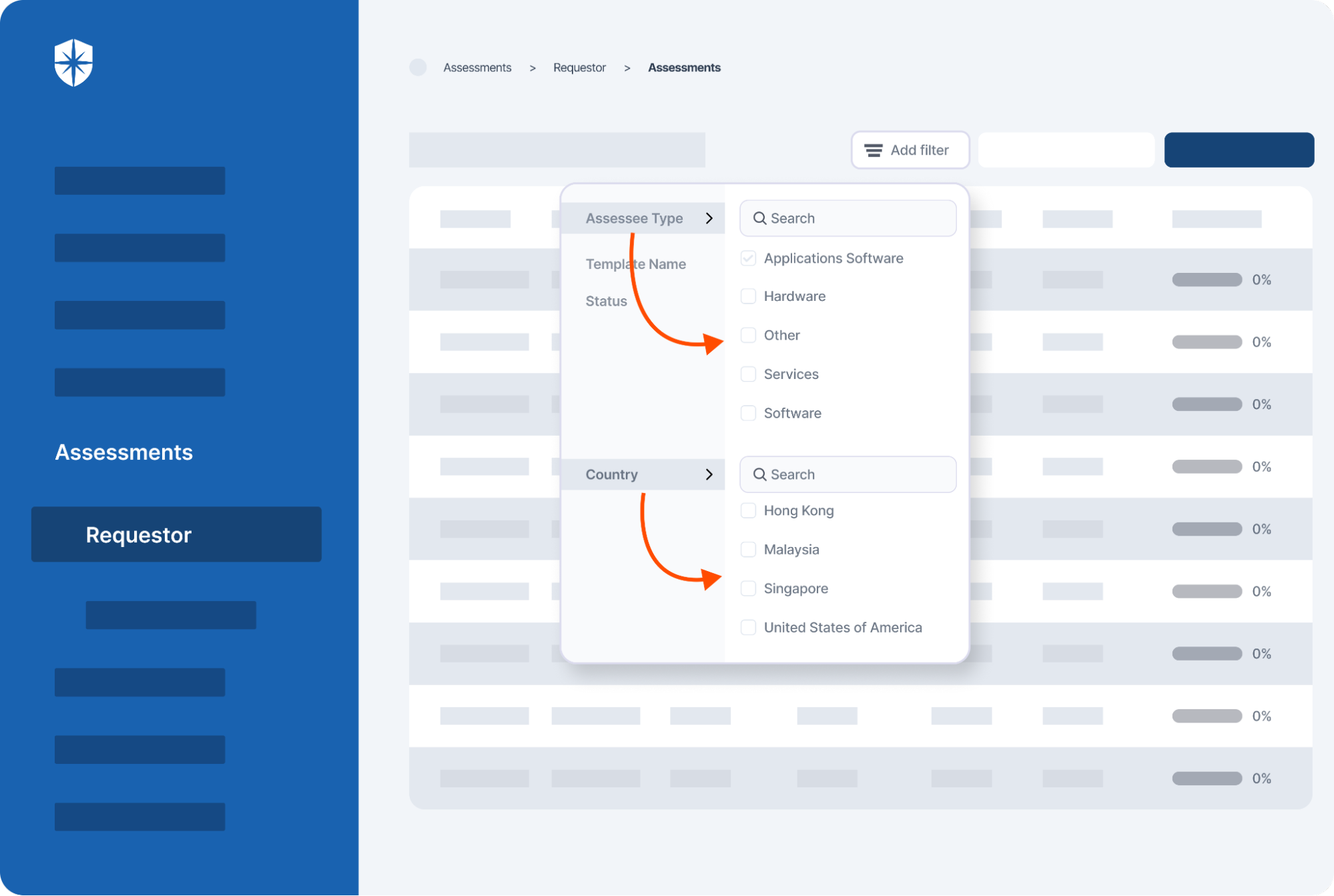

Second, and this is crucial, is how our platform removes lots of back and forth when managing and remediating vendor risks. Automating the various processes involved in selecting and onboarding vendors is usually pre-built into most TPRM tools. But even with this, most tools still require you to send back and forth emails, requiring vendors to do their bit in staying compliant or remediating threats and cybersecurity risks.
Not with Cyber Sierra.
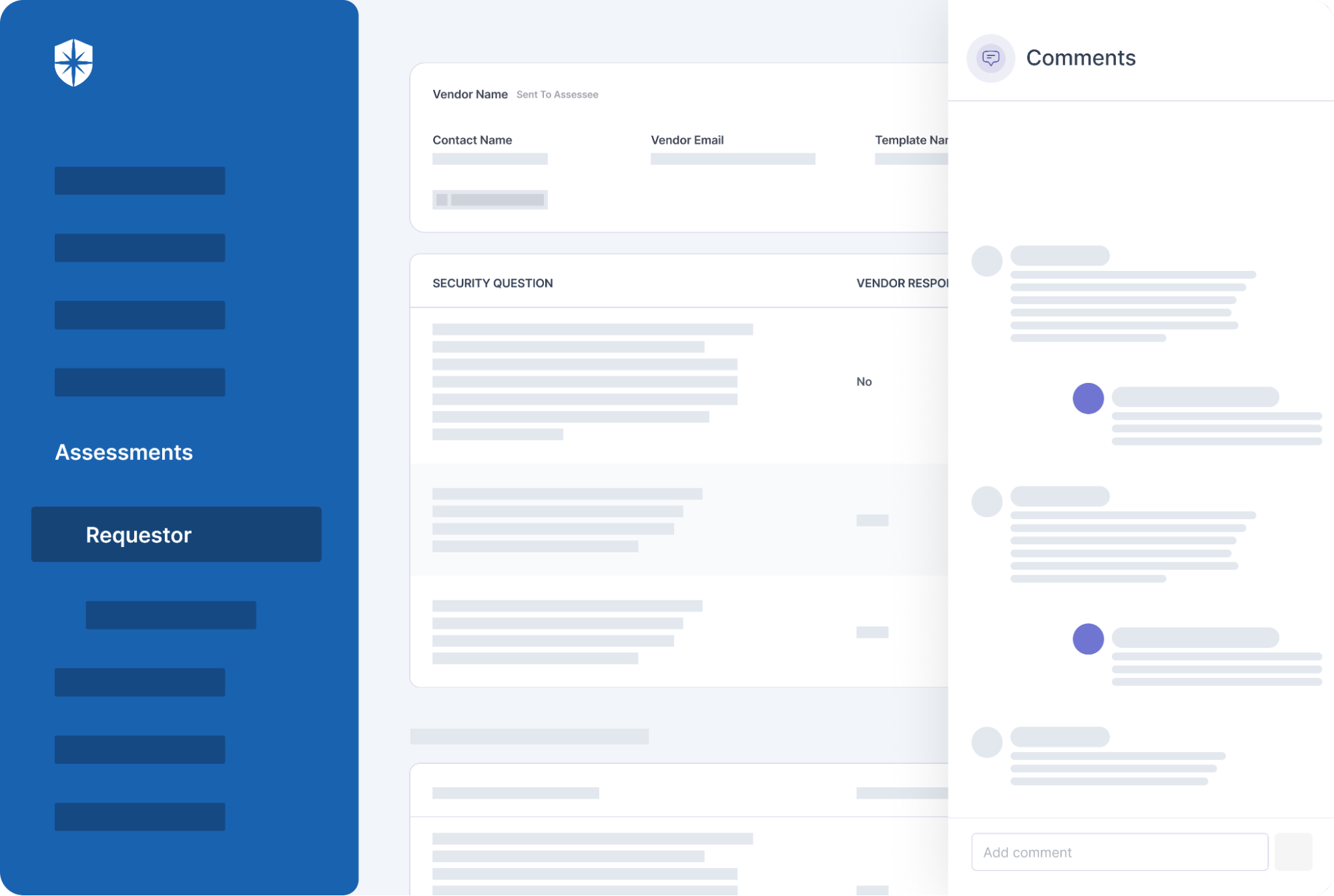
In many, if not all, cases, managing and remediating risks requires vendors to adjust internal systems outside your team’s control. This requires real-time collaboration whenever the need arises. And to be effective, communication should be streamlined and in-context of specific risk-remediation tasks.
Our TPRM comments’ feature enables that:

There are other reasons to consider an interoperable, cybersecurity suite with enterprise TPRM capabilities like Cyber Sierra.
But the two reasons shown above is why a global bank in Singapore relies on us for its extensive TPRM needs:
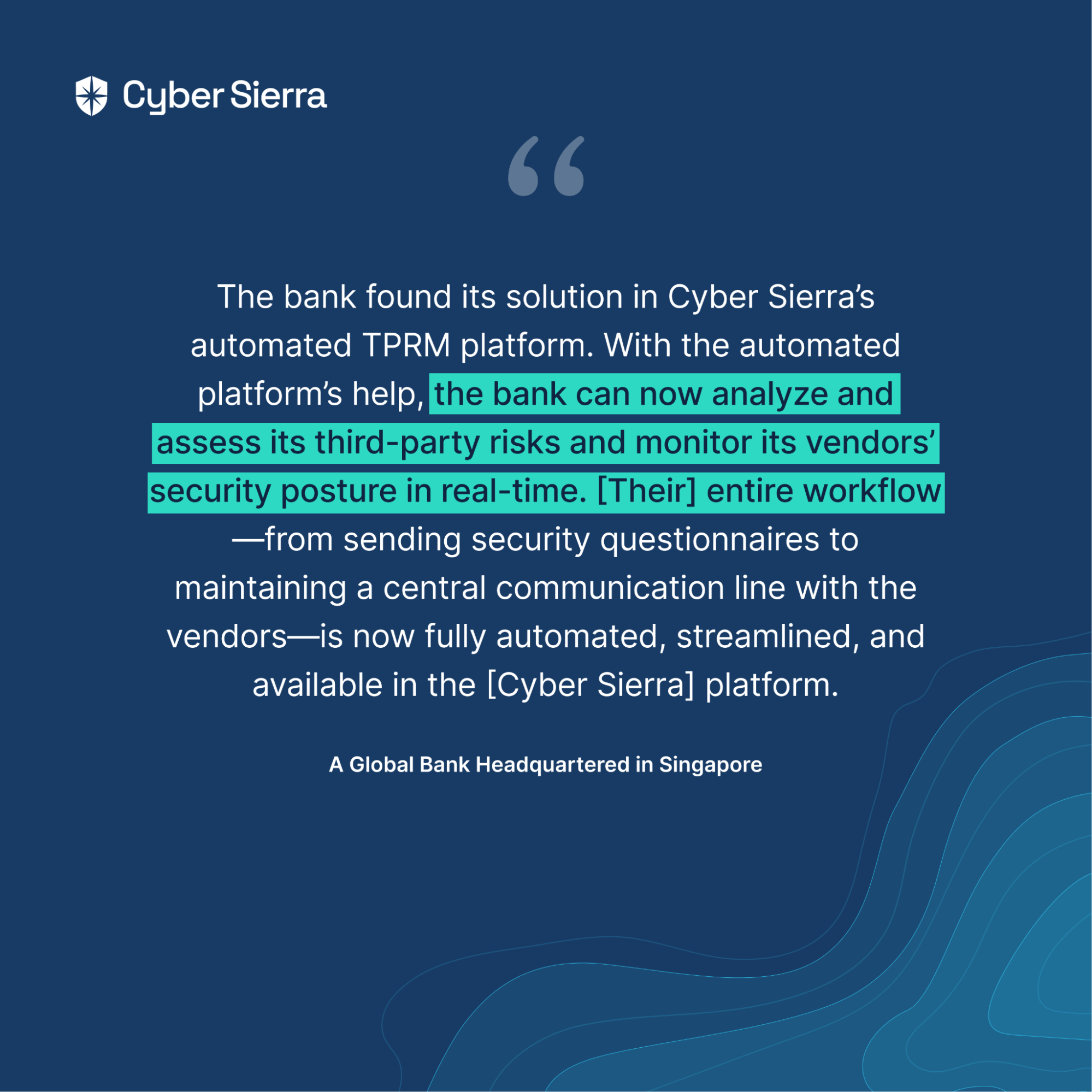

Read their success story here.
If that sounds inviting, give Cyber Sierra a try:




A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.