

Building and Implementing a Continuous Control Monitoring





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
Imagine if companies received real-time alerts whenever their operational controls were compromised. How many data breaches, operational hiccups, and costly regulatory non-compliance issues could be immediately addressed or even completely avoided?
IBM’s Cost of a Data Breach Report found that companies took an average of 277 days to identify and contain a data breach. That’s nearly 9 months of potentially catastrophic damage before an organization even realizes they’ve been compromised!
Delays in cybersecurity can cause drastic damage and significant losses.
That’s where Continuous Control Monitoring (CCM) comes into play and becomes essential for your organization’s resilience and long-term success.
Building and implementing a CCM system requires thoughtful planning, prioritization, and a systematic approach. However, the rewards for enhanced risk management, adherence to regulatory rules, and operational efficiency far outweigh the initial efforts.
In this guide, you will understand how to build and implement a Continuous Control Monitoring system.
Implementing Continuous Control Monitoring
Continuous Control Monitoring (CCM), also called ‘audit in motion’, is a key component of an effective enterprise risk management program. It ensures that your organization adheres to industry, regional, and local regulatory standards at all times.
A CCM system also helps you set clear expectations for employees to follow, and it reduces the risk of non-compliance with laws and regulations.
But setting up a CCM system isn’t just about having control frameworks like COBIT 5 or ISO 27001; it also requires a data-driven approach to ensure you have all the information needed for effective decision-making.
Step by Step Guide to Building and Implementing a Continuous Control Monitoring System
Here is a step-by-step guide to building and implementing your own CCM system.
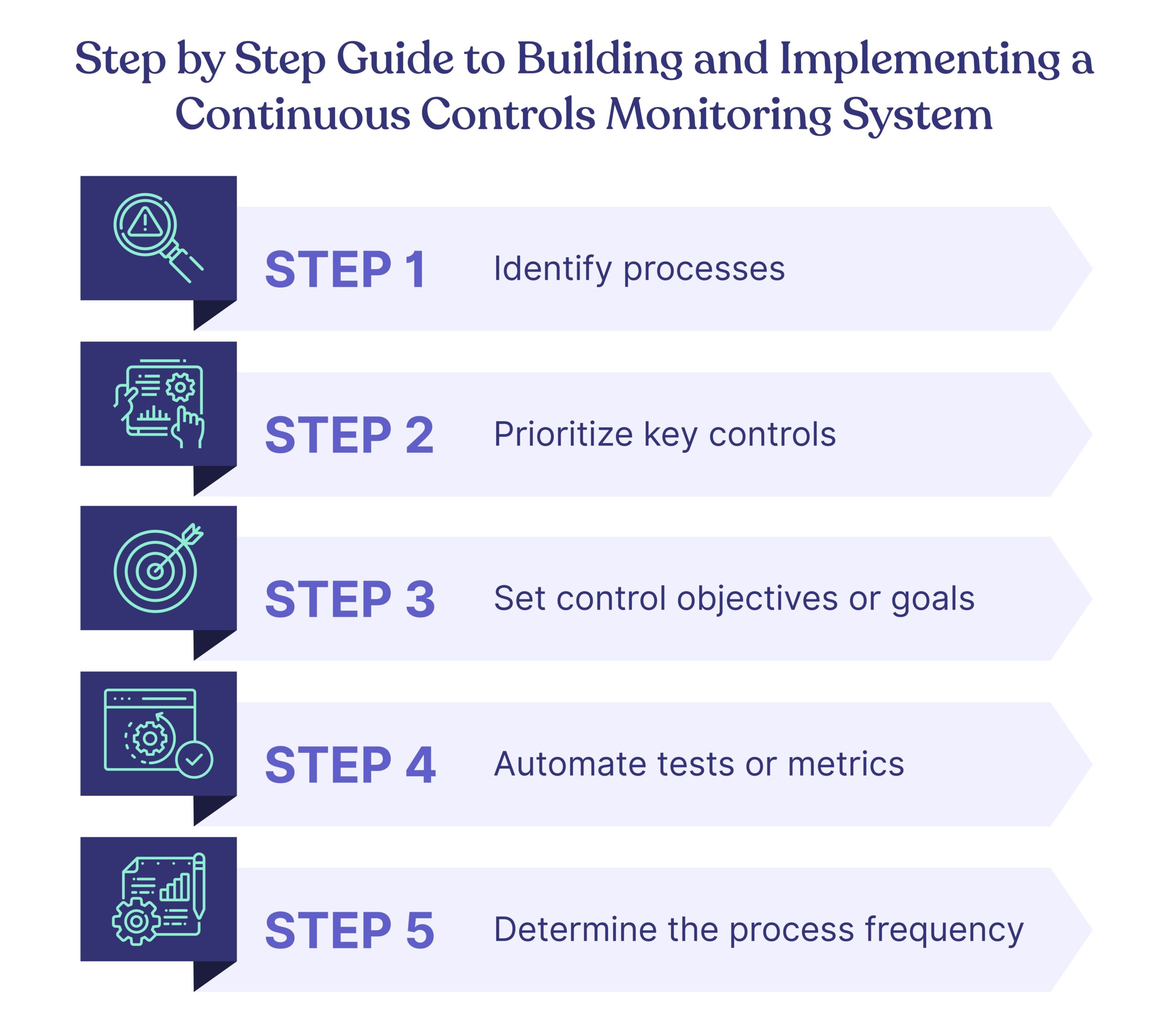

Let’s look at them one by one.
1. Identify processes
The initial step in implementing CCM involves identifying and thoroughly understanding the crucial processes within your organization that need control monitoring. This identification is vital since it helps prioritize the areas where control monitoring can provide the most value in mitigating risk and ensuring compliance.
To effectively identify these business processes, consider the following factors:
- Alignment with objectives: Prioritize processes closely tied to strategic goals like revenue generation, expense management, or boosting operational efficiency.
- Risk exposure: High-risk processes (financial, operational, regulatory) should be primary candidates for CCM.
- Regulatory requirements: Processes governed by stringent compliance regulations and likely to attract penalties or fines if non-compliant are also crucial for monitoring.
- Past issues: Consider your history of control weaknesses and errors to identify areas needing monitoring and control measures.
With these, you can prioritize the processes and controls that need to be addressed first.
2. Prioritize key controls
The second step in establishing your CCM is prioritizing key controls for critical processes. These controls are guidelines, actions, or procedures implemented to mitigate risks and ensure data accuracy.
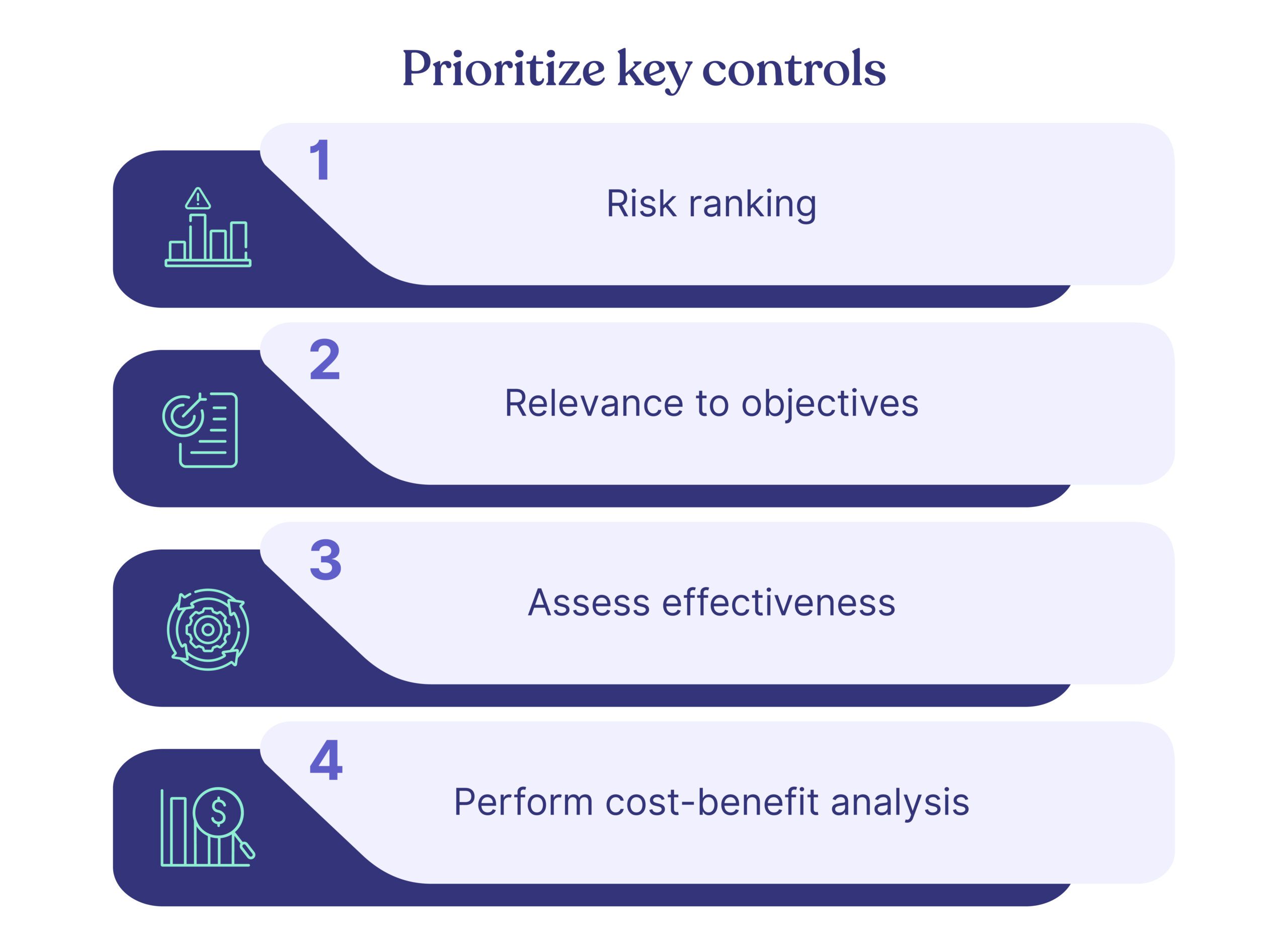

Here’s how to do it:
- Risk ranking: List your processes according to their associated risks. Give higher priority to key controls that target your riskiest processes.
- Relevance to objectives: Analyze how each control contributes to meeting business goals. Those directly supporting essential objectives should gain precedence.
- Assess effectiveness: Evaluate past performance of controls. Those proven to reduce risks and uphold data accuracy should be a focus.
- Perform cost-benefit analysis: Weigh the cost of implementing each control against its benefits. Maximize return on investment by focusing on cost-effective controls.
Through these steps, you can prioritize key controls, effectively use resources, and create the most considerable impact on risk management and objective fulfillment.
3. Set control objectives or goals
After identifying and prioritizing key controls, the next step is to establish what you want those controls to accomplish. Control objectives act as reference points, enabling you to validate the performance of your selected controls in decreasing risks and upholding regulatory compliance. Ensuring these objectives align with your wider risk management strategy and business goals is essential.
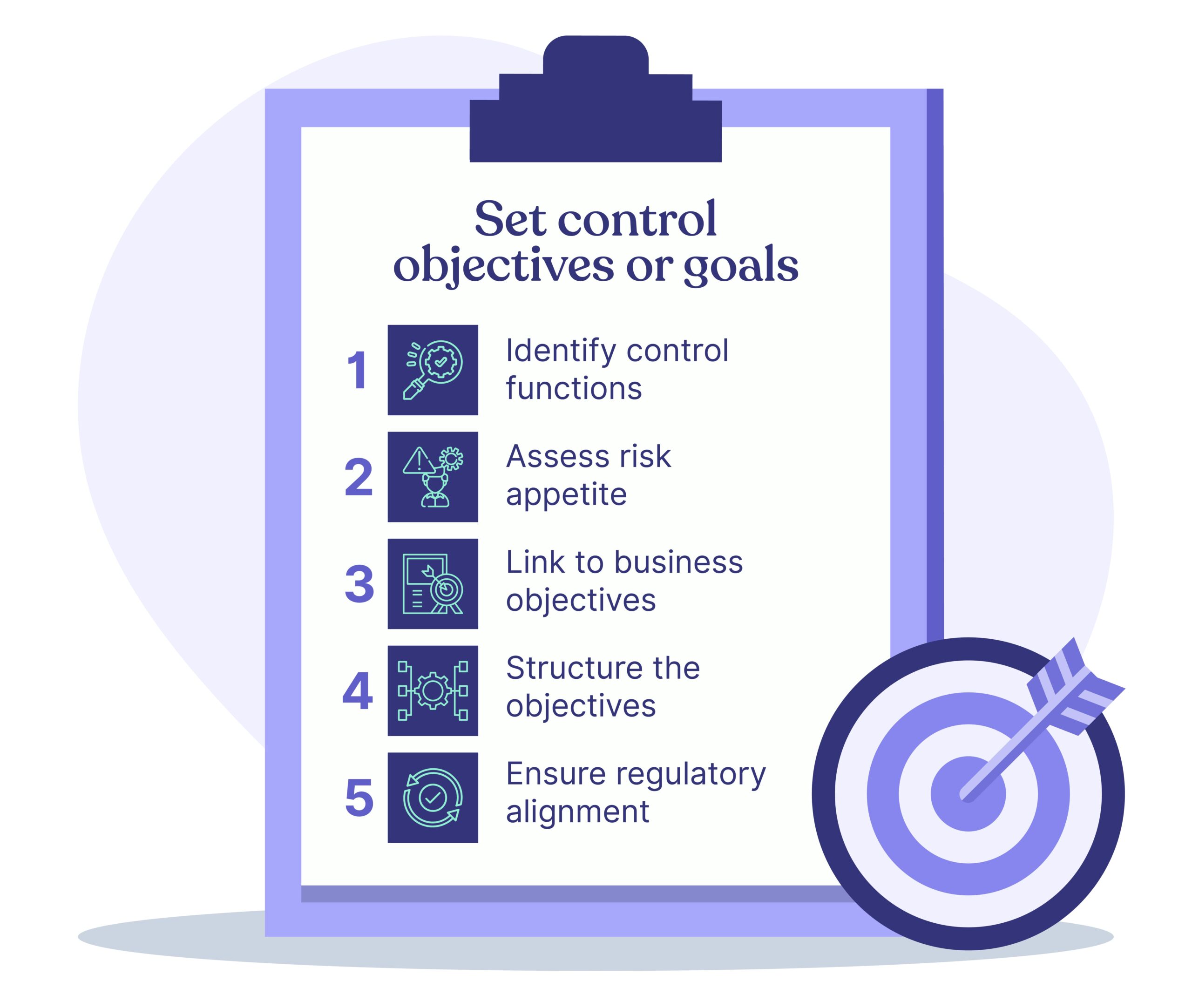

To define control objectives:
- Identify control functions: Start by identifying the specific function each control serves. Determine if it is designed to prevent, detect, or correct losses, errors, or incidents that pose risks.
- Assess risk appetite: Understand your organization’s risk tolerance, including acceptable levels of risk exposure and potential impacts. Incorporate risk appetite into your control objectives to maintain a balanced approach.
- Link to business objectives: Your control objectives should support your strategic goals. Ensure each control objective is linked to a corresponding business objective or overarching risk management strategy.
- Structure the objectives: Your control objectives should be specific, measurable, attainable, relevant, and time-bound (SMART). Ensure they are clear and concise, providing a solid framework for assessment.
- Ensure regulatory alignment: Factor regulatory and compliance requirements into your control objectives to avoid pitfalls.
Defining well-aligned control objectives will guide the implementation and evaluation of your Continuous Control Monitoring (CCM), helping to improve efficiency and effectiveness across your organization’s risk management and compliance efforts.
4. Automate tests or metrics
Once you’ve set your control objectives, you must develop automated tests or metrics. Automated tests allow you to check the effectiveness of your key controls continuously. This strategic move toward automation reduces your need for manual oversight, minimizes the potential for human errors, and speeds up your ability to spot control weaknesses. These benefits boost your risk management efforts and can lead to cost savings and improved operational efficiency.
Using these automated systems, you’ll gain real-time insights into how well your control measures are performing. These tests regularly monitor key indicators and produce quantitative evaluations, helping you make informed decisions. This is where the role of third-party solutions comes into play.
Third-party solutions are especially important when you’re dealing with a large number of data points and multiple control measures. They help ensure that the tests are conducted consistently across all channels, reducing human error risk.
With Cyber Sierra, you can streamline continuous control monitoring through automation, effortless integration into current systems, and a scalable infrastructure. The platform is purpose-built to help you achieve regulatory compliance even while it offers robust analytics for identifying risks and reporting on control performance.
5. Determine the process frequency
The final step in establishing your Continuous Control Monitoring (CCM) system entails choosing the appropriate monitoring frequency and establishing a consistent review process for the results generated by your automated tests or metrics. Once the controls are in place and metrics established, continuous checks provide near real-time assurance of effectiveness.
The frequency of monitoring isn’t a one-size-fits-all solution. It’s influenced by numerous elements, such as your organization’s risk profile and industry-specific regulatory requirements. The key is to identify a balance; too frequent checks may burden your resources, while infrequent monitoring could miss out on critical early warning signs.
You must institute regular review processes alongside determining the appropriate monitoring frequency. This guarantees that the data collected from automated tests is analyzed thoroughly and turned into actionable insights on a scheduled basis.
With continuous monitoring and effective review processes, you’ll achieve prompt identification of control weak spots and faster resolution of any rising issues. Ensuring these issues are intercepted and rectified as soon as possible prevents them from escalating further, providing an overall safety net and boosting the efficiency of your organization’s risk and compliance management.
Wrapping Up
Building and implementing a Continuous Control Monitoring system requires thoughtful planning, prioritization, and a systematic approach. However, the rewards for enhanced risk management, adherence to regulatory rules, and operational efficiency far outweigh the initial efforts.
Remember, CCM is not a one-off strategy; instead, it’s an ongoing commitment to designing, measuring, monitoring, and refining your controls to ensure their alignment with your evolving business objectives and the changing risk and regulatory landscapes.

Cyber Sierra’s platform enables enterprises to keep company policies in one central location and make them accessible to all employees. The platform also offers a comprehensive training regimen that addresses the risks posed by today’s most pressing cybersecurity issues.
To discover how Cyber Sierra can help you establish your CCM program, book a demo today.



A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.



