Here’s How to Automate Enterprise Compliance Management





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
SOC 2, ISO 27001, GDPR, CCPA, HIPAA, and so on.
I know. The number of cybersecurity and privacy laws enterprises must attain and stay compliant with can be daunting. Especially if your company operates across multiple jurisdictions. Regardless, Hui Chen, a renowned ethics and corporate compliance leader, advised against treating them like a box-checking exercise.
Hui’s co-authored piece for HBR noted:


You’re probably wondering:
So how can CISOs and IT Executives achieve effectiveness and stop treating compliance like a box-checking exercise? One such way is implementing and managing your enterprise compliance programs holistically. Experts call it enterprise compliance management.
And it has two key areas:
Key Areas of Enterprise Compliance Management
Starting with its top-level definition:


To extend Tzvika Sharaf’s succinct definition, the creation of such high-level workflow must address two key areas:
- External compliance revolves around regulation and rules imposed on a company by the industry or government of the jurisdictions it operates in. For example, per the General Data Protection Regulation (GDPR), if a company misplaces customer personal information from the European Union (EU), they are mandated to provide notification of this mishap within 72 hours.
- Internal compliance, on the other hand, is how an enterprise organization responds to and works within the confines of externally imposed compliance regulations.
So for effective enterprise compliance management, you don’t just need well-defined procedures and policies. These should address both internal and external requirements peculiar to each compliance program your enterprise company implements. Achieving that requires centralization, according to Deloitte:


The second challenge:
How do you achieve this needed centralization?
For the rest of this guide, I’d walk you through three pillars you should centralize with technology for that. You’ll also see how Cyber Sierra’s governance, risk, and compliance (GRC) suite automates and makes everything seamless.
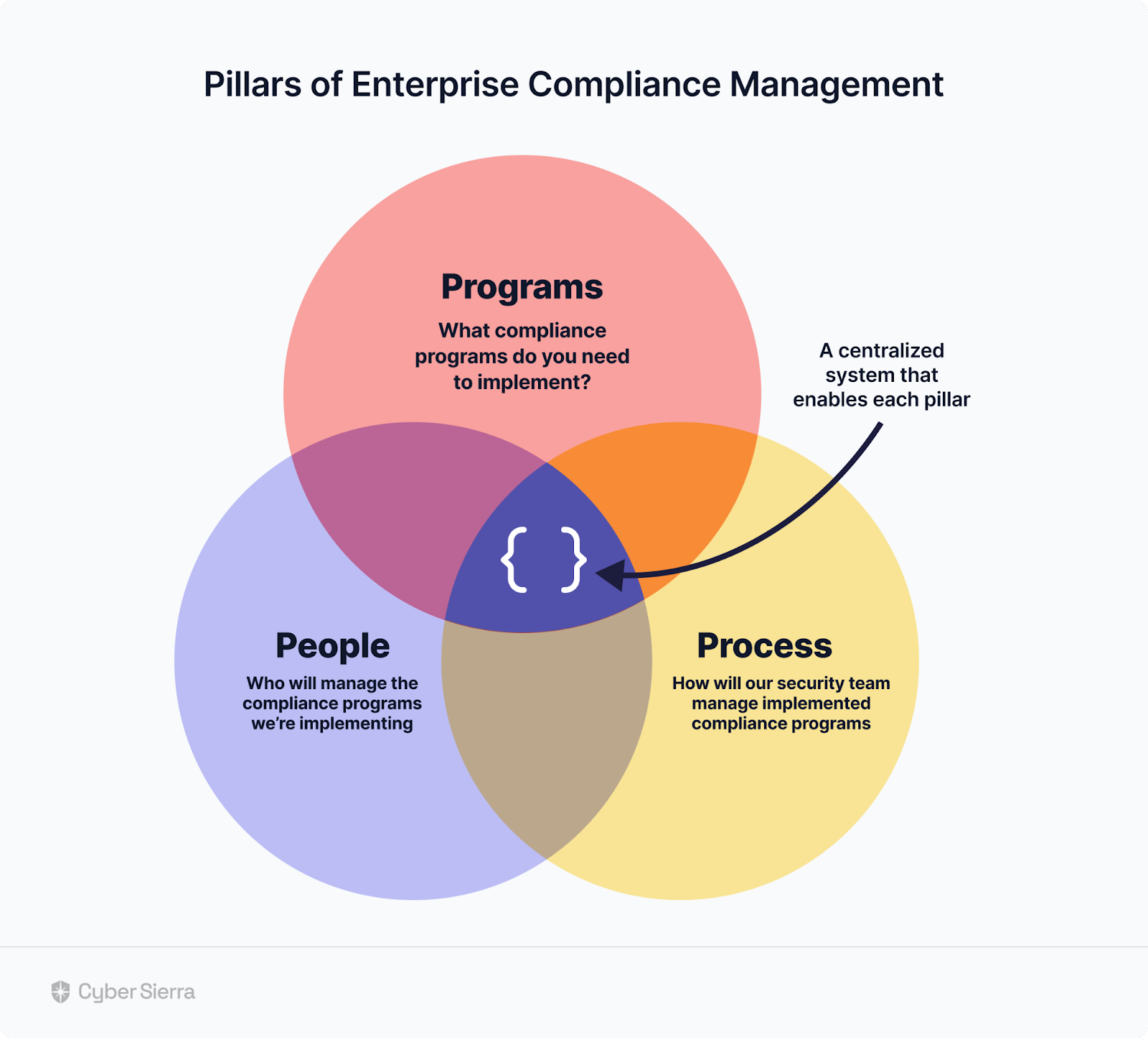
Three Pillars of Enterprise Compliance Management
- Programs,
- People, and
- Processes.
Those are the three pillars of enterprise compliance.
Per Deloitte’s report cited above, these pillars must be centralized with a system that enables each to function efficiently and effectively:

1. Programs
The first step in enterprise compliance management is choosing programs to implement and in what order. Both criteria are crucial to avoid treating compliance like a box-checking exercise, as Hui advised against.
Two reasons for that are:
- Choosing the right programs ensures your company adheres to industry- and location-specific compliance regulations.
- Implementing compliance programs in the right order makes the process easier to navigate and manage for your company.
For instance, if your company handles financial and personal data of European-based customers, PCI DSS and GDPR are a necessity. On the other hand, although ISO 27001 and SOC 2 aren’t compulsory, they are widely recognized and can ease your team’s implementation of other programs.
The order of importance differs depending on whether your company handles health information of customers. In that case, HIPAA is a compliance program to also prioritize. In some cases, it may be necessary to first implement internal compliance and security controls to guide data security management across your company.
Navigating all this can be gruesome.
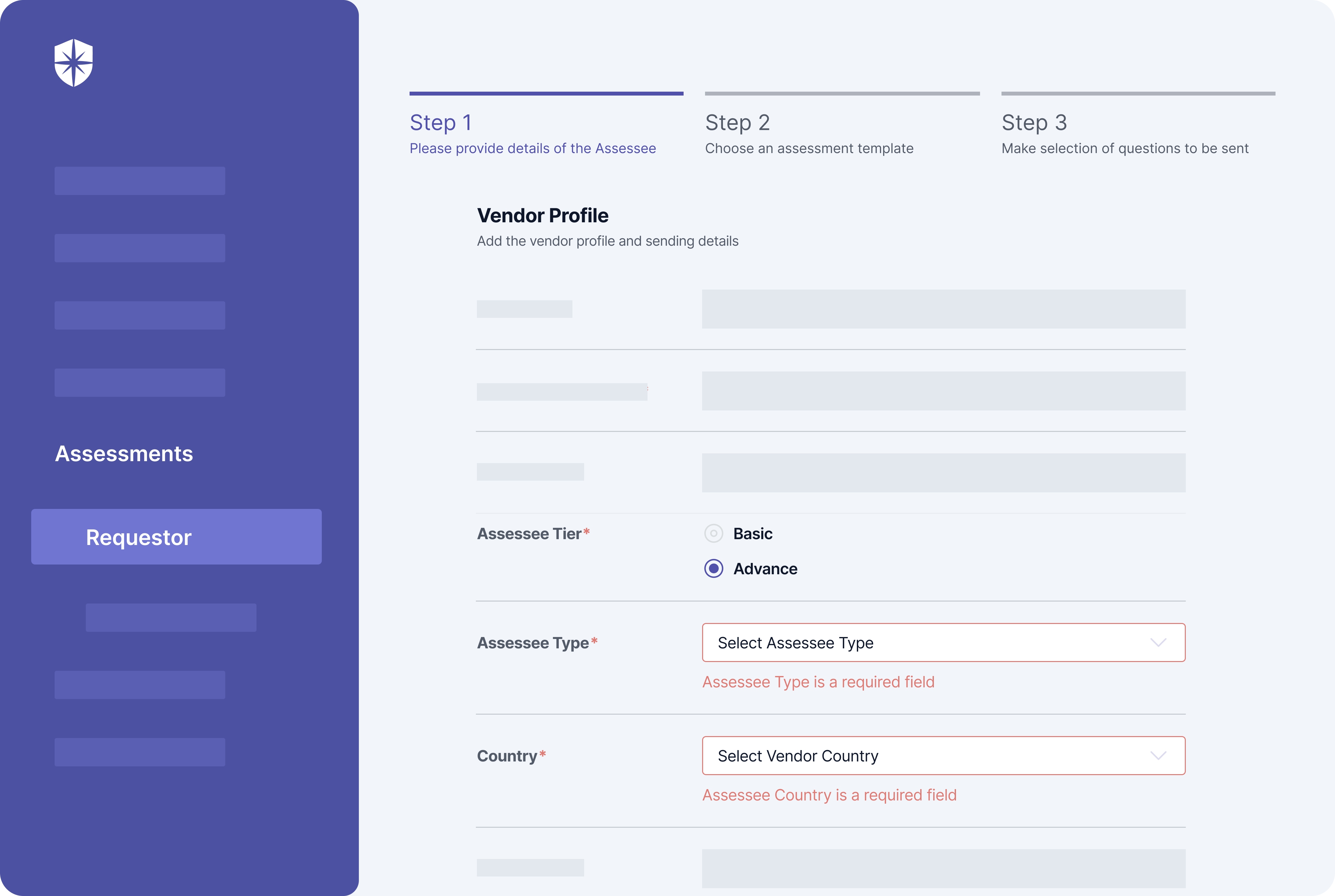
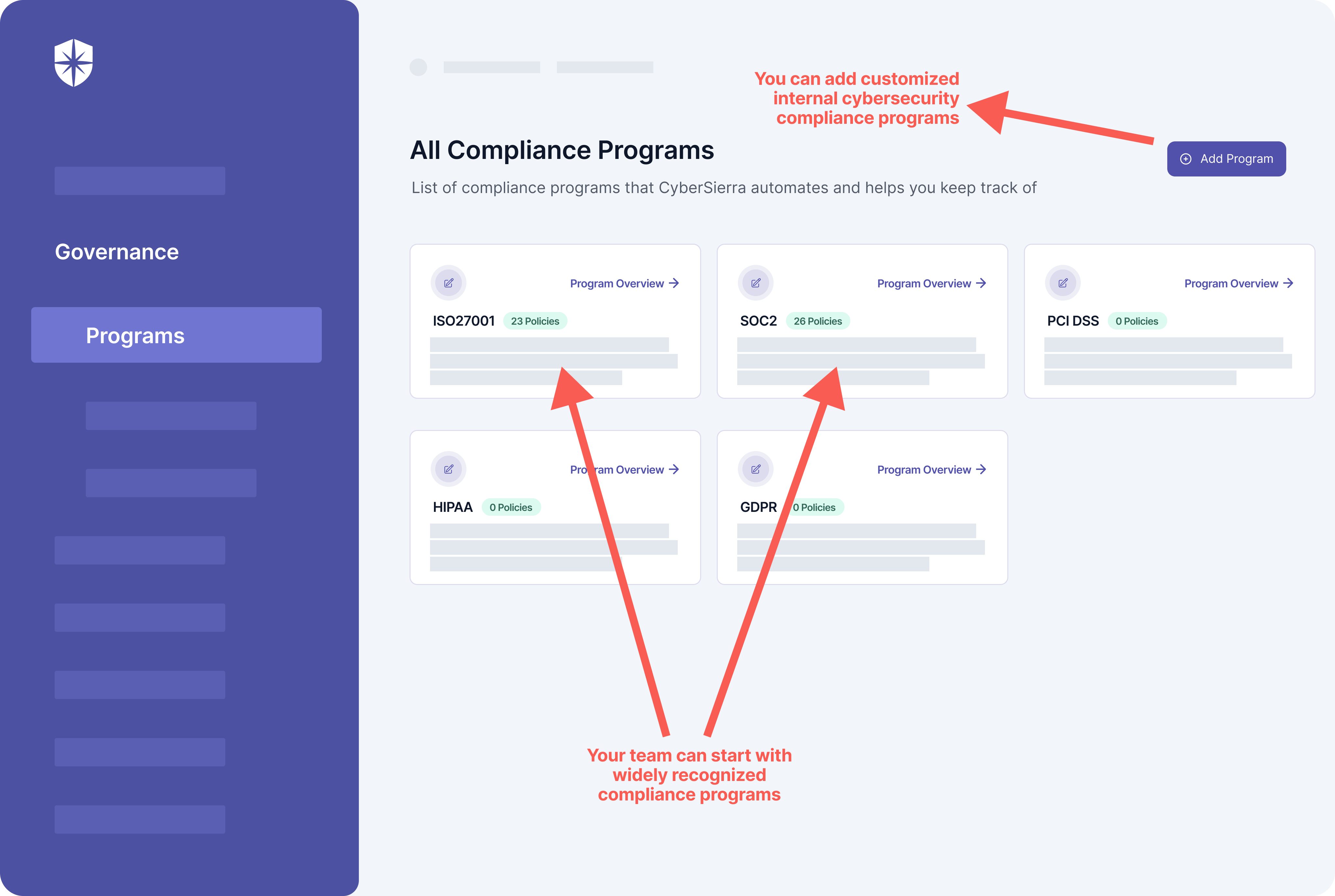
Which is where a tool with extensive GRC capabilities is crucial. With Cyber Sierra, for instance, choosing and implementing enterprise compliance programs is streamlined. You can implement internal cybersecurity compliance controls. And your security team can also start with widely recognized compliance programs like SOC 2, GDPR, and ISO 27001 that ease the implementation of all other programs.
All from one dashboard:

2. People
Effective compliance management starts with people —your security team and employees across the organization. When grounded and empowered to adhere to all cybersecurity compliance requirements, they can be your greatest asset for staying compliant. Otherwise, they can be your biggest burden and window to data security breaches.
To stress the point:
leading to these data security breaches and compliance failures include:
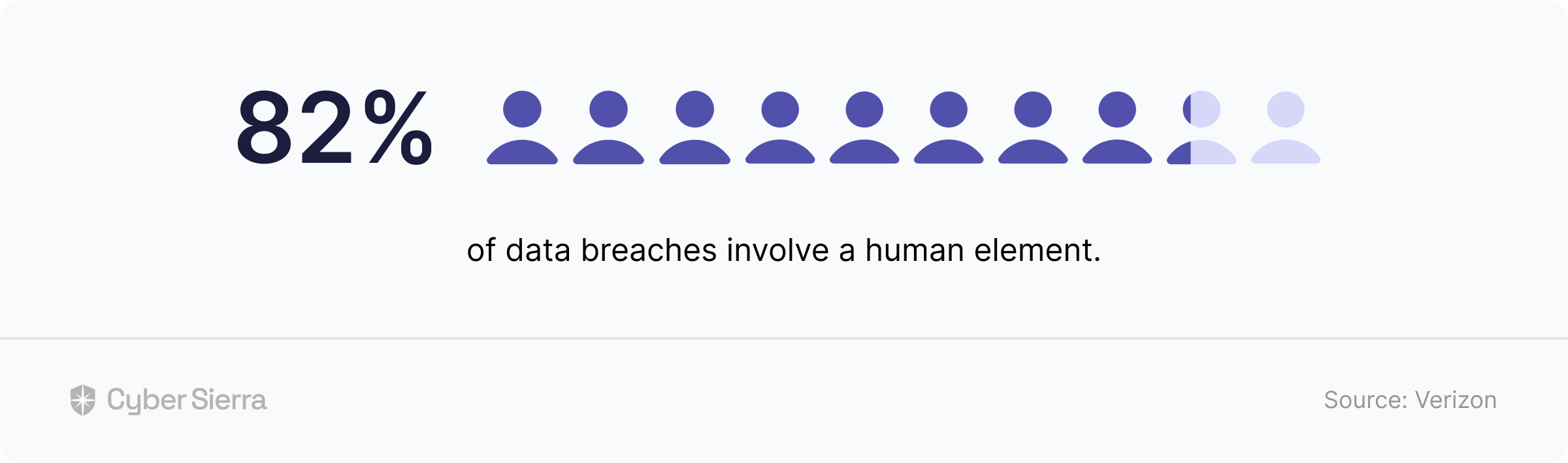

Per this Verizon study, dominant incidents
Employees mis-configuring a database and directly exposing information, and
- Employees making errors that enable cybercriminals to access privileged information in a company’s systems.
Here’s why I’m addressing the ‘people’ pillar in enterprise compliance management from the angle of your entire company employees. Having a Director of Compliance and managers to oversee the implementation of compliance programs is crucial. However, if all employees aren’t trained on being compliant, the chances of getting breached and facing non-compliance fines remain high.
It’s why in a Forbes article, Justin Rende wrote:


It is also important for ongoing security awareness training to cut across all implementable compliance programs. This streamlines the training experience for the staff without overwhelming them with new training for each program.
But that’s not all.
Executives need to track all staff training, so they can follow up and ensure they are being completed. This is where an interoperable cybersecurity platform like Cyber Sierra comes in:
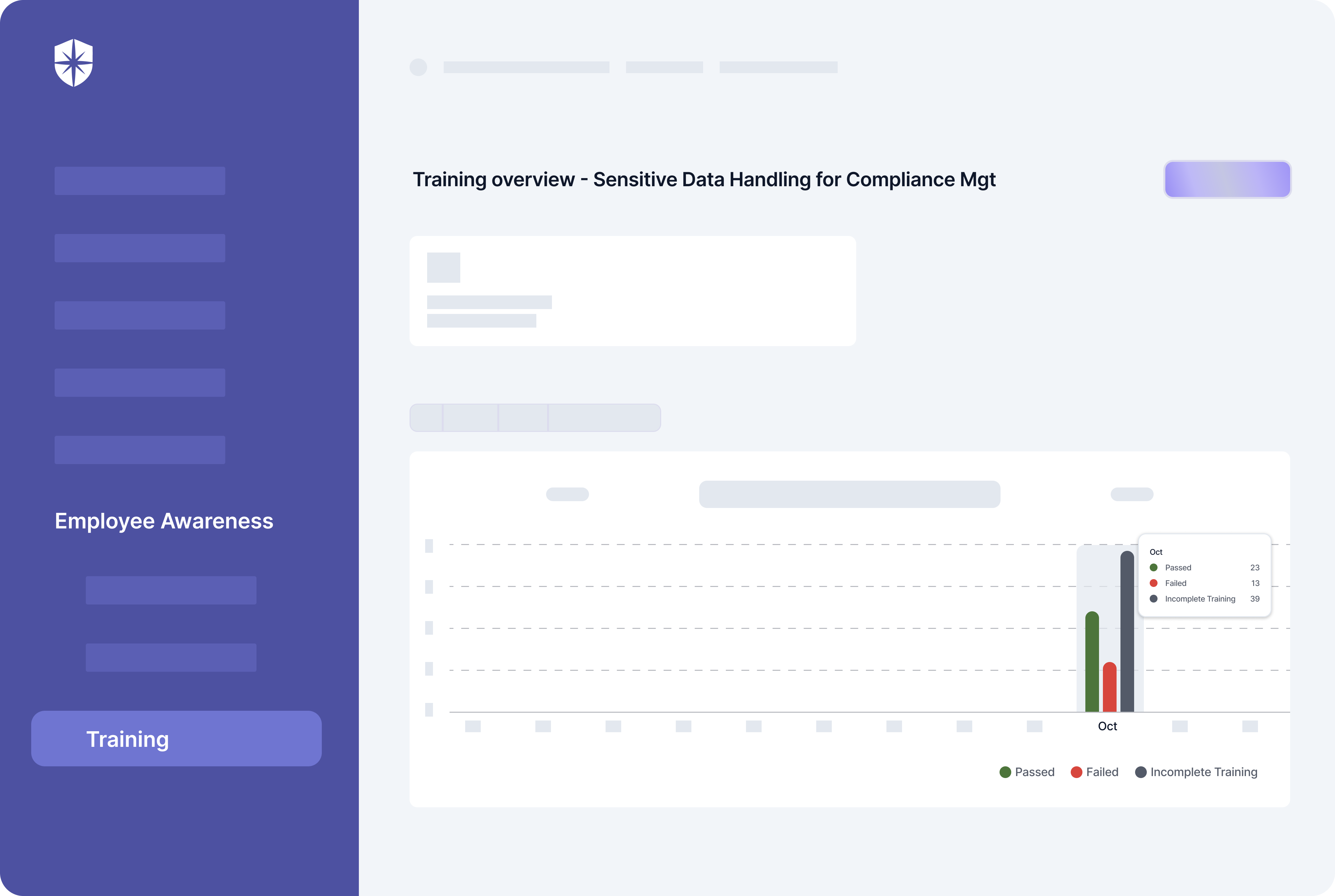

As shown, your team can launch staff-wide ongoing security awareness training that cuts across all compliance programs. More importantly, executives like you get a dashboard to monitor how employees are completing them on our platform, too.
3. Processes
Processes are crucial for managing enterprise compliance. First, they create a culture of transparency on how to implement programs. Second, processes ensure accountability within your team and promotes a methodical approach to compliance management.
Essentially, processes guide employees through the decision-making and actions needed to attain and stay compliant. And aid in documenting and creating audit trails required to demonstrate compliance to auditors, stakeholders, and regulators.
For instance, you need efficient processes for:
- Continuous risk assessments
- Internal and external security audits
- Compliance programs’ policy development
- Mapping security controls to each compliance program
- Ongoing risk monitoring, scoring, mitigation, and so on.
But each of these processes must be meticulous and adjusted as the regulatory compliance landscape evolves. This is why corporate compliance experts recommend the automation of these processes.


With an intelligent, unified platform like Cyber Sierra, crucial compliance program processes are automated out of the box. For instance, our platform maintains auto-updated versions of policies mapped to different compliance programs:
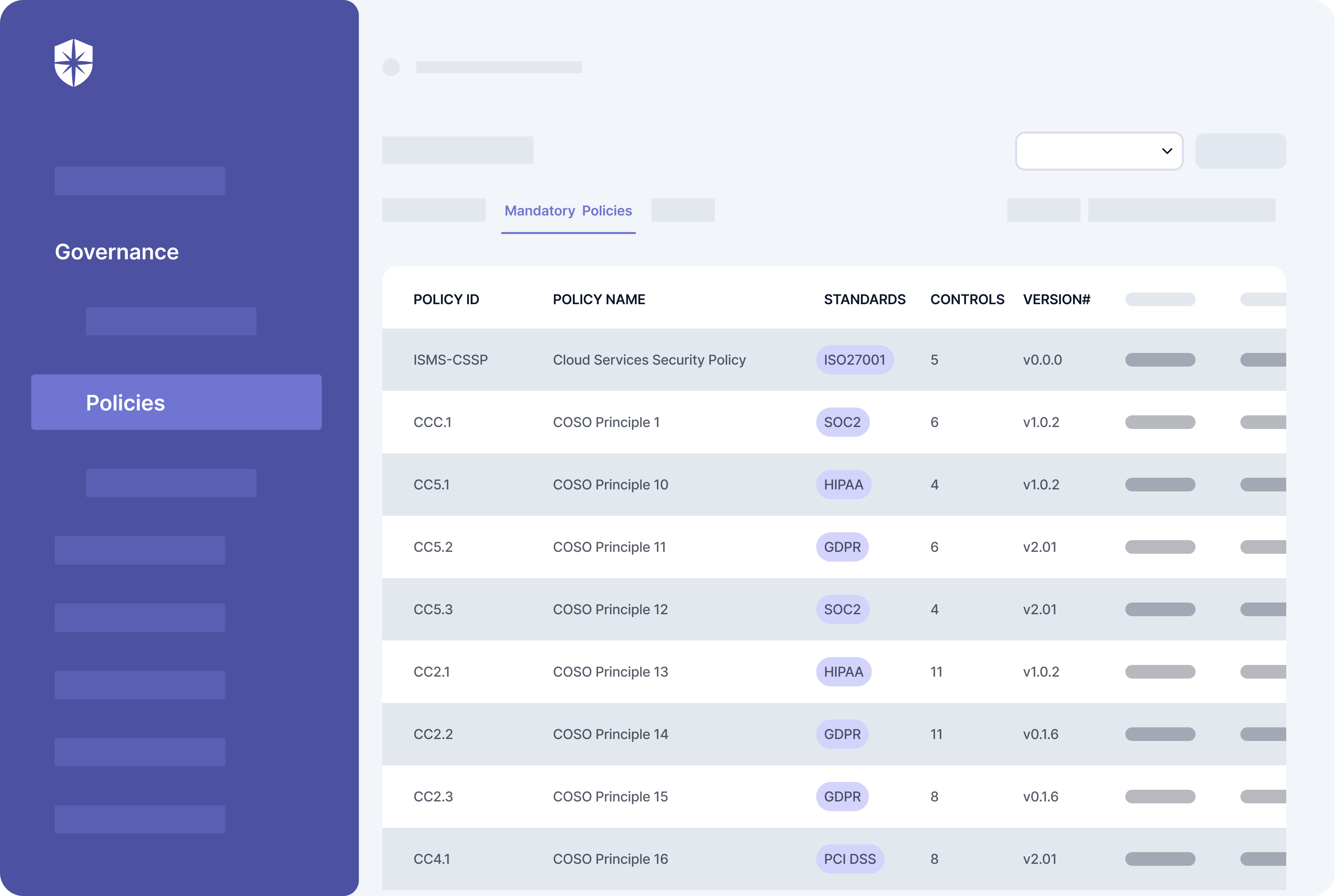

Having compliance policies in a central place like this cuts off all the gruesome manual work involved in effecting processes for creating, uploading, and maintaining them as the regulatory landscape evolves.
Other Areas Automation Aids Compliance Management
Having a centralized enterprise compliance management system goes beyond enabling its pillars. Although this is crucial as shown so far, there are other areas where automation streamlines compliance management for the CISO and IT Executives.
1. Compliance Controls’ Management
Compliance programs have dozens, and for some, hundreds of security controls that must be implemented. And as each compliance program evolves, evidence of each control must be updated to confirm that security measures are in place and avoid fines.
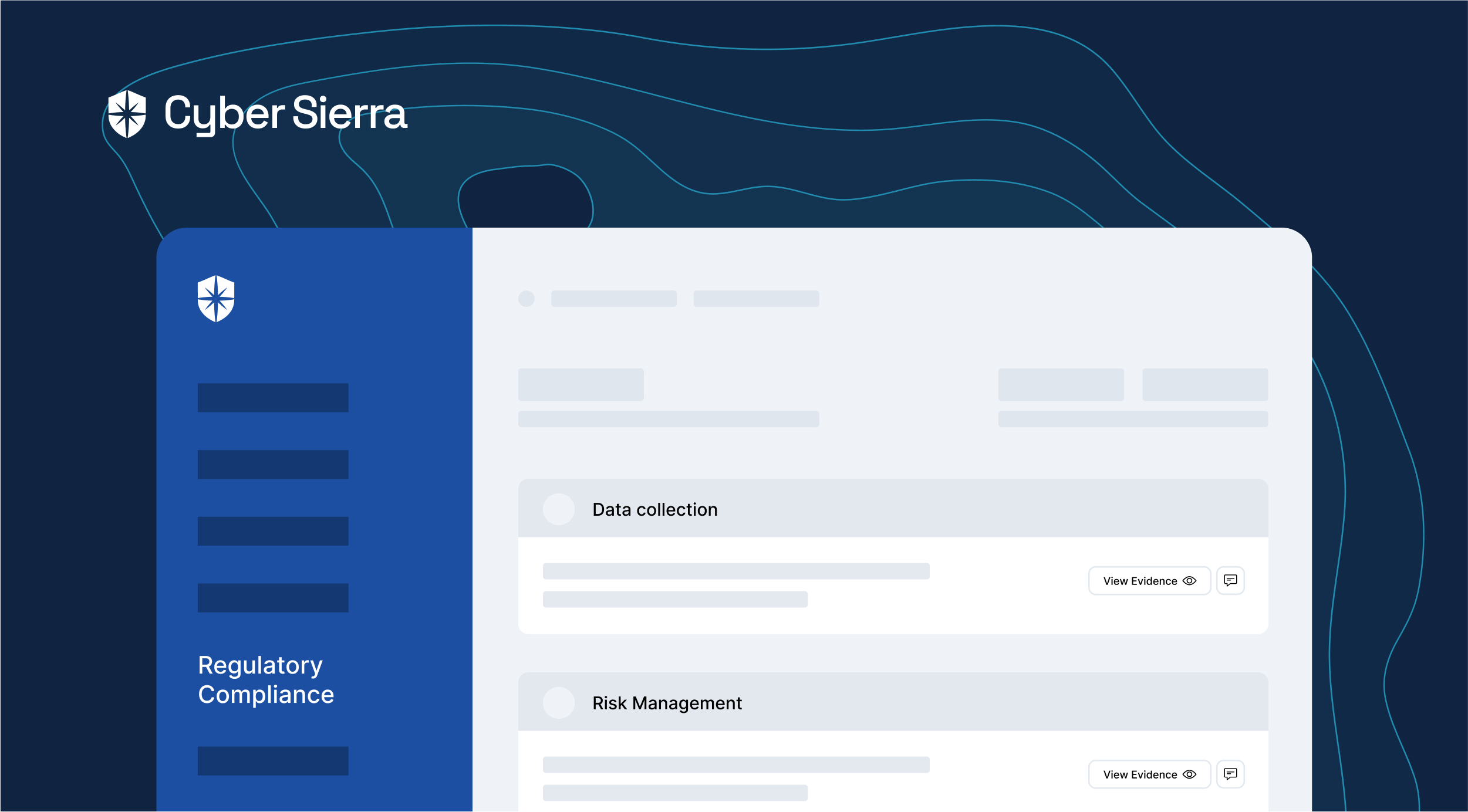
Doing this at scale, considering there are hundreds of controls across compliance programs, requires a central place for tracking them:
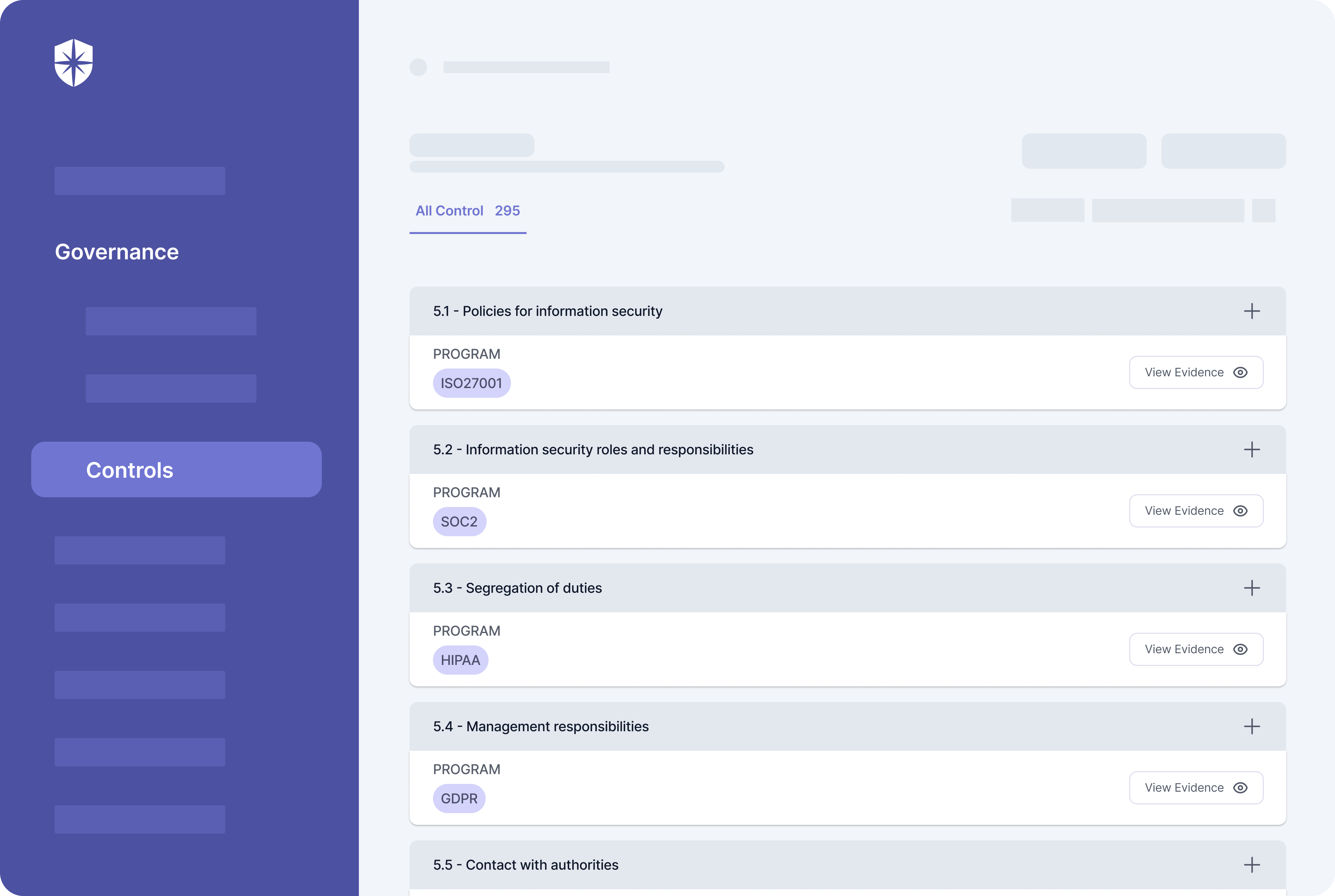

As shown, Cyber Sierra has a robust compliance controls’ management dashboard. Having all controls auto-mapped to different programs like this streamlines the steps usually spent tracking and updating evidence in spreadsheets for your team. It also gives you, the executive, a way to monitor and view uploaded compliance controls’ evidence from one view.
2. Risk Insights and Analysis
Negligence isn’t the sole cause of compliance issues.
Often, failure to proactively identify and mitigate external risks from third-party vendors can result in breaching your compliance stance. In the words of a veteran CISO, Jay Pasteris:


To avoid this, it helps to manage your company’s compliance programs with an interoperable cybersecurity platform like Cyber Sierra. This is because our platform has capabilities for automating continuous 3rd party risk assessments and ongoing risk monitoring.
Automate Enterprise Compliance Management
Managing enterprise compliance manually can be time-consuming and extremely challenging, often leading to costly inefficiencies. Also, it takes more than having software that streamlines becoming and staying compliant with specific programs.
The need to map and manage security controls per compliance program is crucial. And so is the need to automate the process of continuously analyzing, identifying, and mitigating all third-party vendor risks. As shown so far, without these, all efforts toward compliance management could still lead to hefty fines.
It is therefore necessary to automate the entire enterprise compliance management lifecycle with an interoperable cybersecurity platform like Cyber Sierra. Our platform enables the core pillars of enterprise compliance management and has capabilities for the other areas.
And we’re on standby to give you a free tour:



A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.