CISOs Checklist for Battling Data Security Risks





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
What a time to be a CTO.
Overseeing cloud acceleration already demands a lot —leading IT initiatives, managing legacy systems, sourcing tech talent, etc. Added to these, ensuring data security has leapfrogged into a top challenge.
Tan’s 2023 survey report of Asian-based CTOs corroborates:
Security is arguably one of the top challenges for both CTOs and CIOS as organizations race to the cloud. While misconfiguration is said to be one of the most common reasons for application breaches, insecure APIs have become a new vector of attack, enabling DDoS attacks or undetected access to sensitive company or customer data.


Tech leaders have no choice but to adapt…
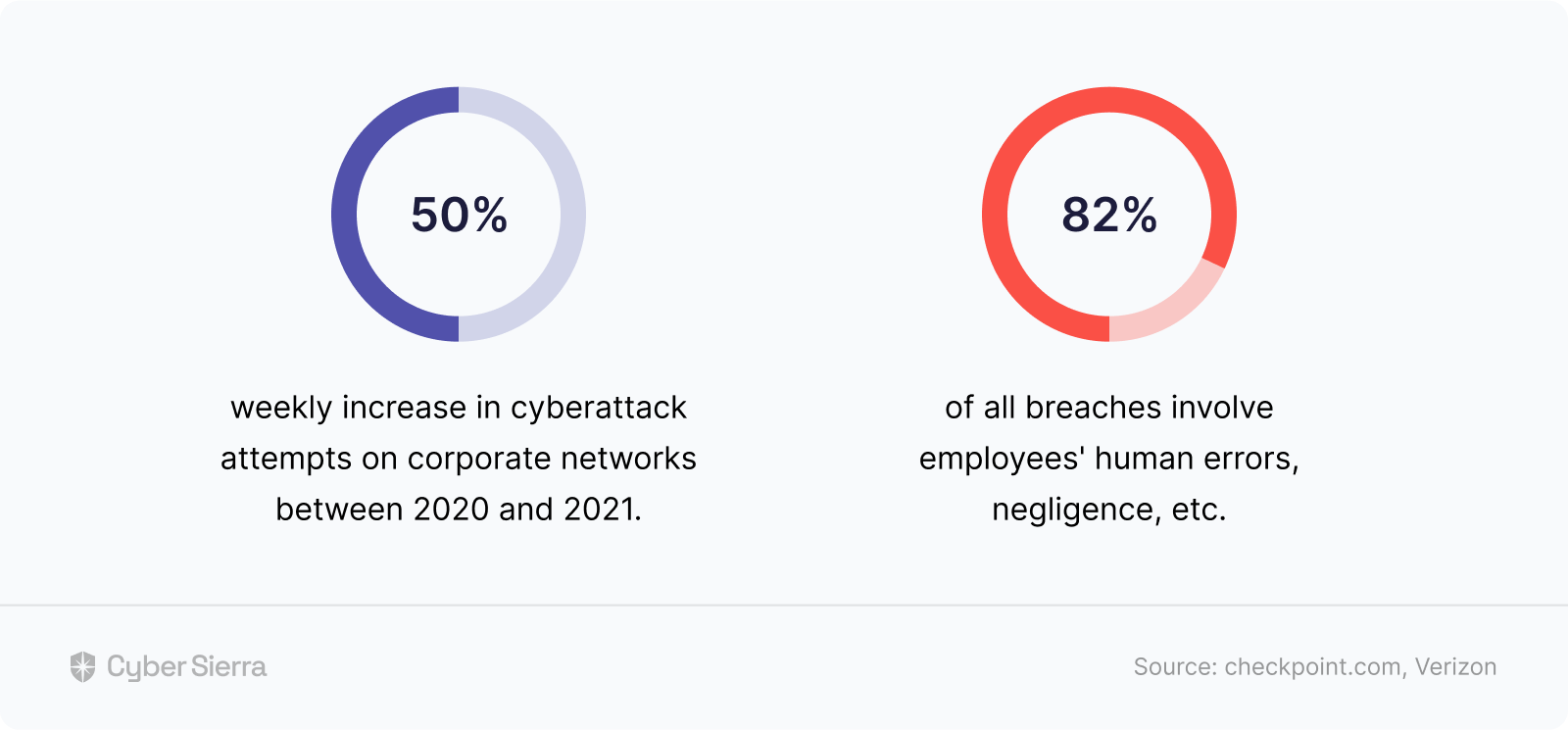
Because data security threats are only getting worse:

Where Should Solving SaaS Data Security Threats Start?
What you focus on is key to solving data security issues.
But with no end to cyber threats like social engineering attacks, phishing, etc., in sight, knowing where to focus isn’t easy. In short, getting it right makes being a CTO harder than ever before.
Even a veteran CTO isn’t finding it easy:
In my 20-plus years working in enterprise security, it's hard to recall a time when it was harder to be a CTO. As a profession, we face so many challenges keeping our organizations secure from attacks in a fast-changing threat landscape that the task can sometimes become overwhelming, leaving us unsure about what to focus on first.


Based on this, here’s our recommendation.
With the fast-changing threat landscape and fact that cyberattacks could be external or from internal mistakes, it’s best to know:
- Today’s top data security challenges,
- Their likely impact on your organization, and
- How to automate tackling them and staying compliant.
This guide (and what should pass as an enterprise CISO data security checklist) will help you do all three:
Today’s Top 3 Data Security Challenges
We perused analyst reports, polls, and surveys featuring CTOs, CISOs, and relevant security execs. All with one goal: To identify today’s top data security challenges and their likelihood to impact cloud-based tech companies.
In no particular order, they are as follows.
1.Lack of Employees’ Awareness
If you’re like most tech companies, you’ve adopted a hybrid or remote-first work culture. This flexibility has advantages. For CTOs, one is that it makes sourcing tech talent beyond a company’s immediate environs possible.
But it also has disadvantages.
First, it increases a company’s data vulnerability layers. That’s because logging into company networks from remote locations opens more data-breaching rooms. Second, and more important, most employees aren’t always up to date on how to spot and counter new attacks.
This lack of awareness has profound implications.
For context, earlier, I cited a study showing that 82% of the time, it takes an internal negligence for cybercriminals to prevail. Well, a similar study by the WEF puts that number at a staggering 95%. This makes ongoing employee awareness a top challenge.
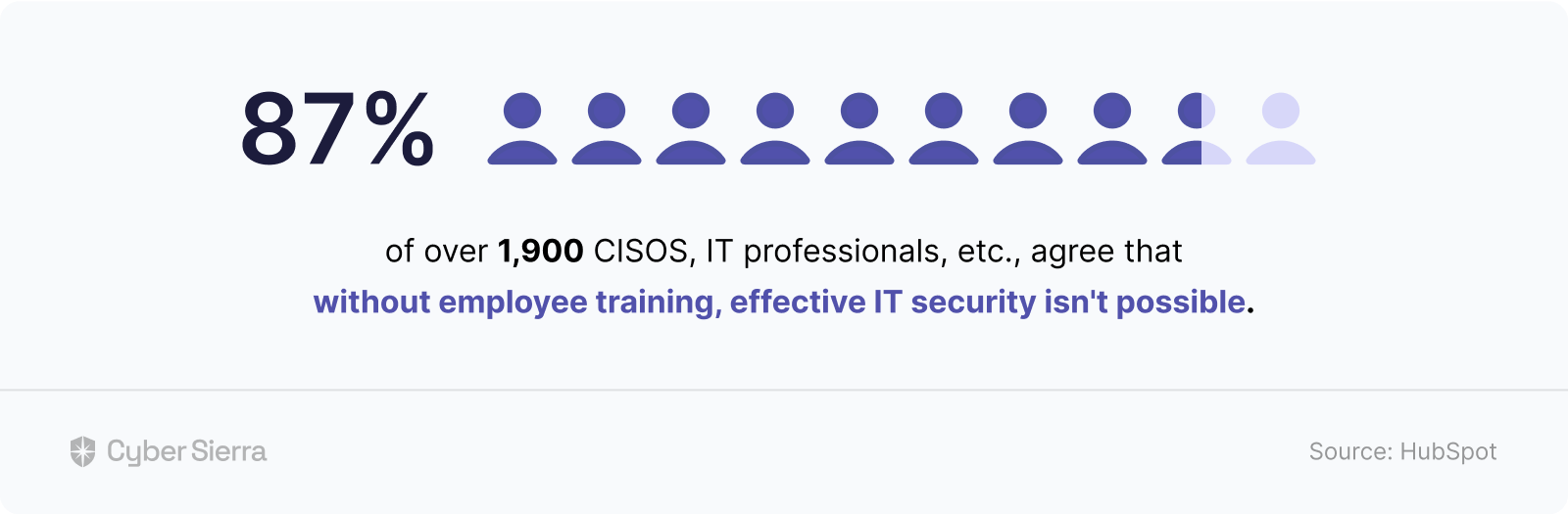
And technology leaders agree.
Of over 1,900 CISOs, IT professionals, etc., polled, about 87% agreed that without employee training, effective IT security isn’t possible:

Solving this problem requires two things.
One, you should launch ongoing phishing campaigns and employee awareness training. Second, ensure each training actually gets completed with a platform that gives you a real-time overview of employees who need a nudge to complete their training:
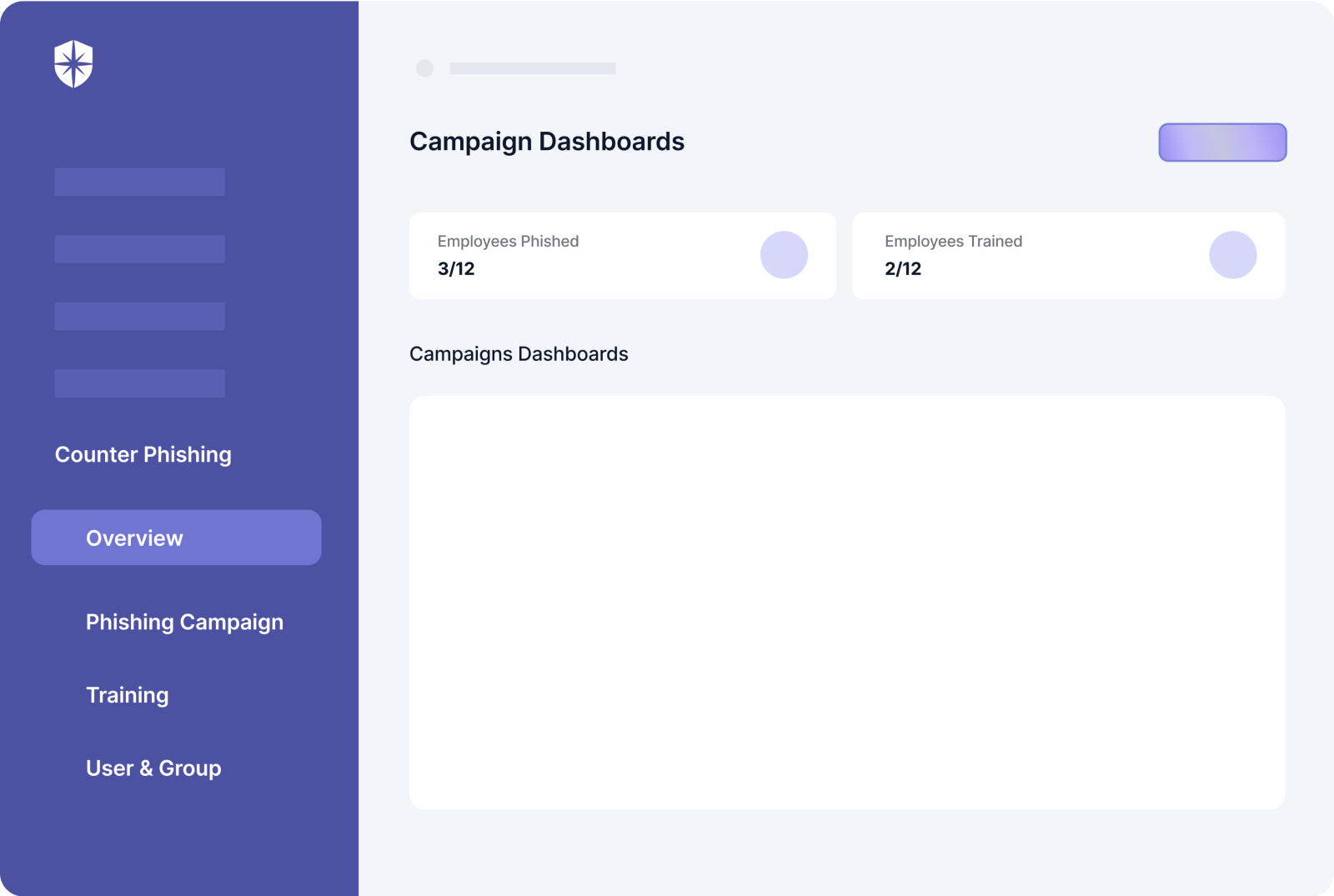

More on that later.
2. Cloud Misconfigurations
A SecurityIntelligence Analyst succinctly captured why misconfigurations rank high among data security threats.
He wrote:
Cloud misconfigurations are vulnerabilities waiting to happen. Malicious attackers are always hunting for misconfigured cloud assets because they can be a doorway to the theft of location data, passwords, financial information, phone numbers, health records and other exploitable personal data.


Let’s put it into perspective.
Imagine you’re the CTO of a US$1 million ARR startup.
According to this VentureBeat report, companies lose 9% of their ARR to network misconfigurations. This means that you could be losing up to US$90,000 yearly to network misconfigurations alone.
And that’s just one type of cloud misconfiguration.
Cybercriminals can also spot data-breaching loopholes in your Kubernetes, cloud, and repository environments. The report by VentureBeat observed why companies are vulnerable to this threat.
Quoting, Tim Keary, the author:
Organizations [are] failing to effectively address misconfigurations due to inconsistent auditing activity. In fact, most organizations are only auditing their devices annually, with switches and routers checked for misconfigurations in just 4% of cases, an approach best described as risk assessment by sampling.


In other words, countering this data security threat starts with regular audit scans. And it should be across all crucial configuration types —cloud, Kubernetes, network, and repository.
Better if your team can do all that in one place and in a few clicks:
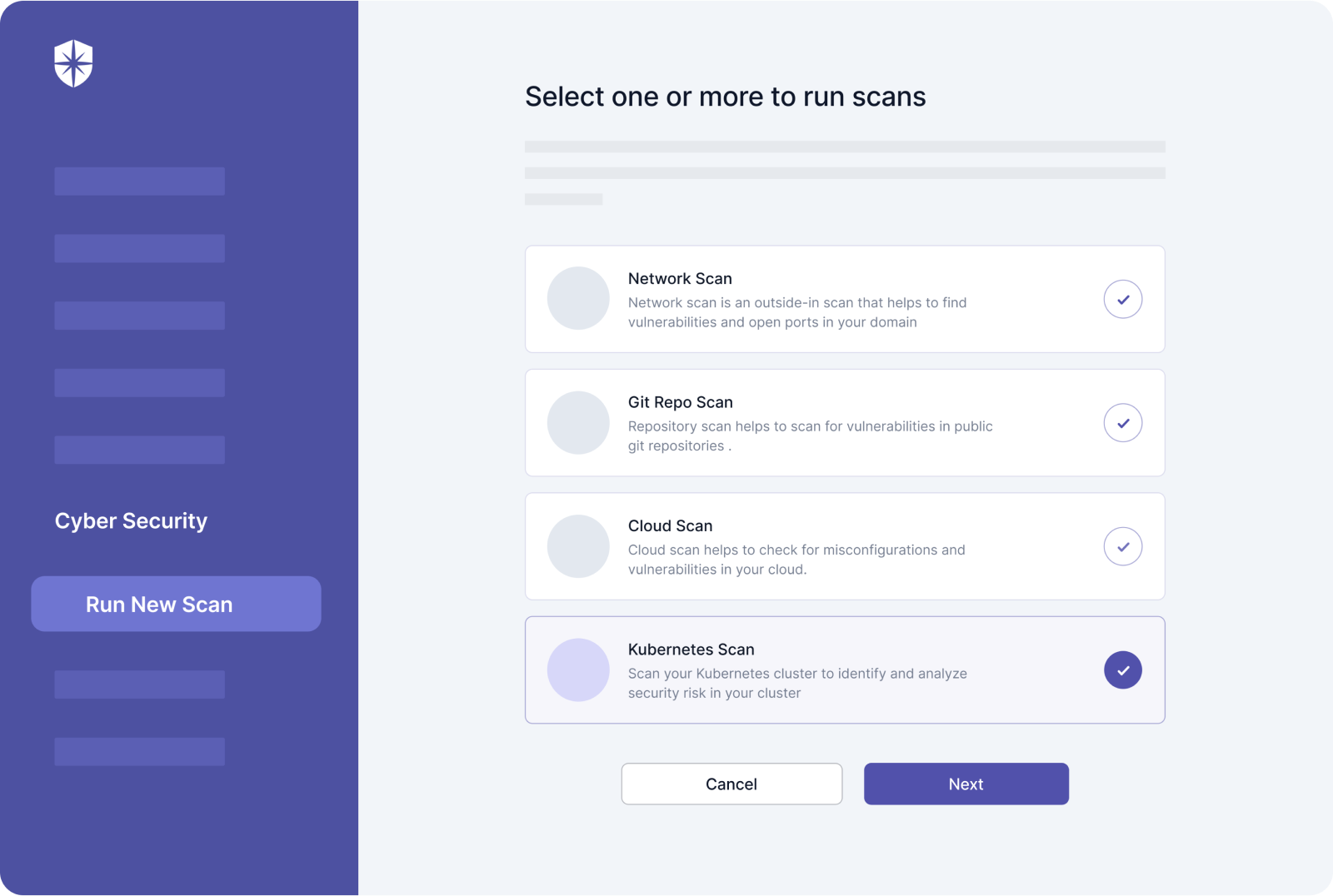

3. Third-Party Vendor Risks
Businesses need other businesses to thrive.
This explains why we increasingly rely on third-party vendor networks of software, services, etc., to deliver effective value to customers.
That’s the upside.
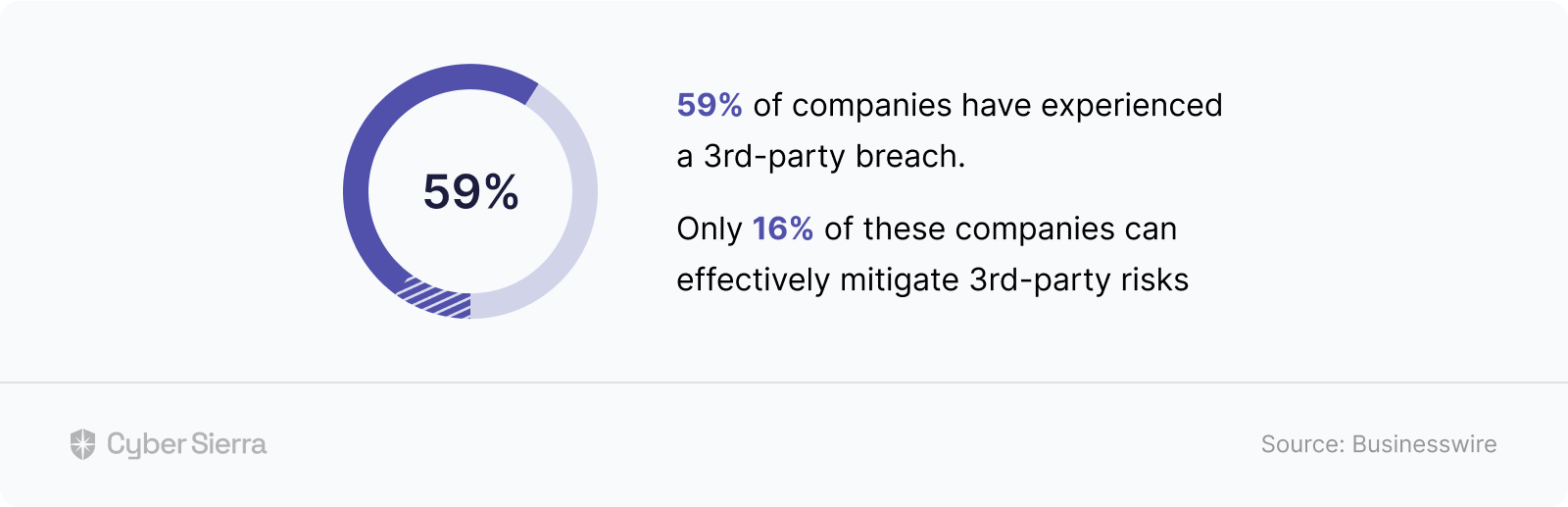
The downside is that giving vendors access to your product or network or accessing theirs poses enormous data security risks. To give you a clue, a 2018 study found that over 59% of companies have experienced a third-party data breach.
What’s more worrying is what the same study revealed: Only 16% of companies can effectively mitigate 3rd-party risks:

There’s a reason for this.
Running even one-time security checks on every new vendor takes a lot of manual back and forth. And it’s worse in this ever-evolving threat landscape requiring ongoing security checks on vendors.
But what if you could automate most of the process?
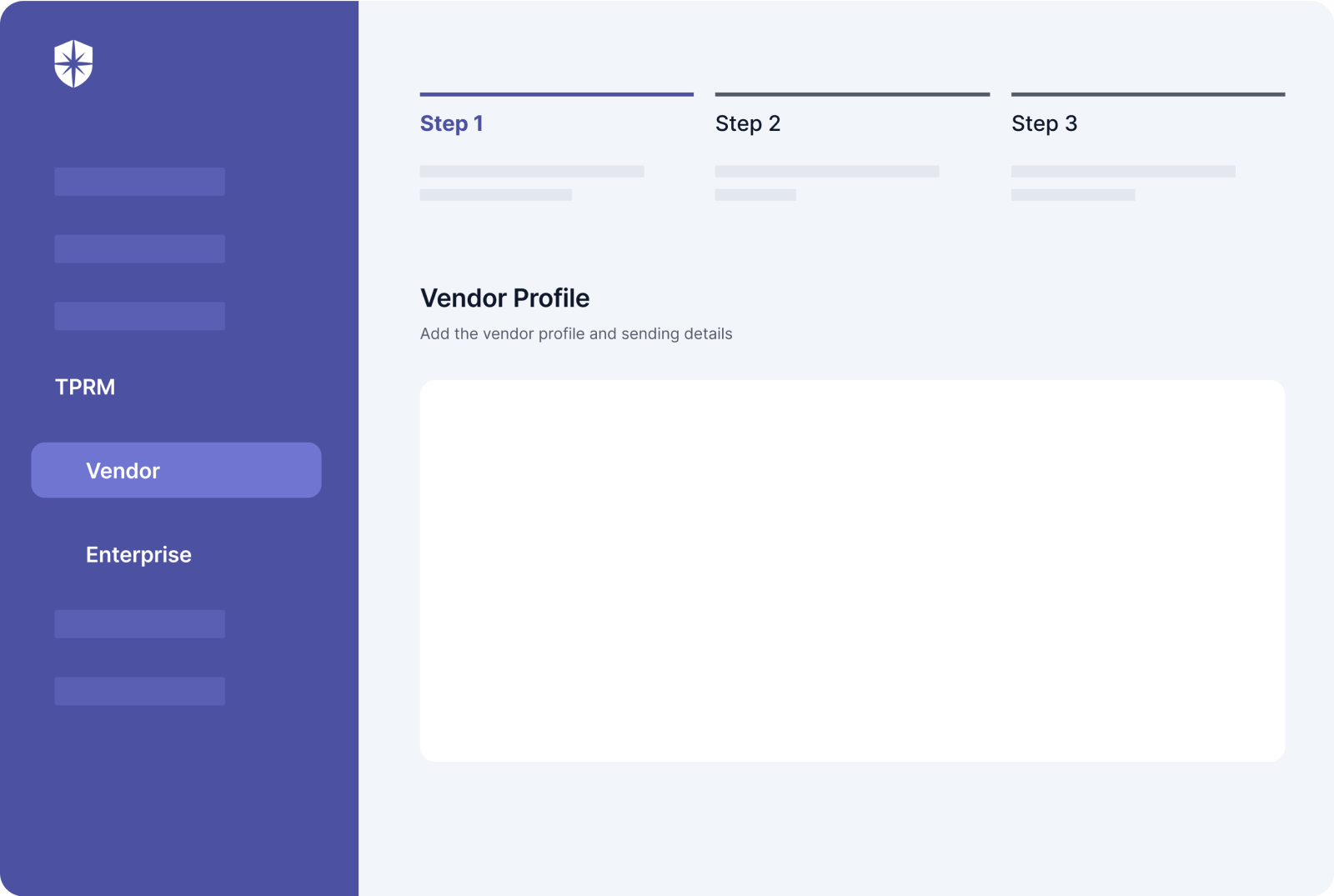
- Add new vendors in a few clicks,
- Send mandatory data security assessments,
- Assign due dates and follow-ups, and
- Manage multiple vendor types from one dashboard.
A platform that makes doing all these a simple, 3-step process tech leaders can complete in no time is optimal:

Why CTOs Should Automate Solving Data Security Risks
Did you notice a common denominator across the top three SaaS data security risks outlined above? In case you missed it, here goes:
Mitigating each isn’t a one-time affair.
As the threat landscape evolves, there’s need to continuously train employees, scan for cloud misconfigurations, and assess 3rd-party vendor risks. This means that to combat threats, CTOs need to:
- Automate each data security risk-mitigating process, and
- Integrate these threat-averting processes into modules that speak to each other (i.e., interoperable).
The benefit of this is that, from one dashboard, your team will know overall risk scores and what threats to prioritize. Solving data security issues this way (i.e., with a single suite like Cyber Sierra) has other benefits.
We’ll get to them soon.
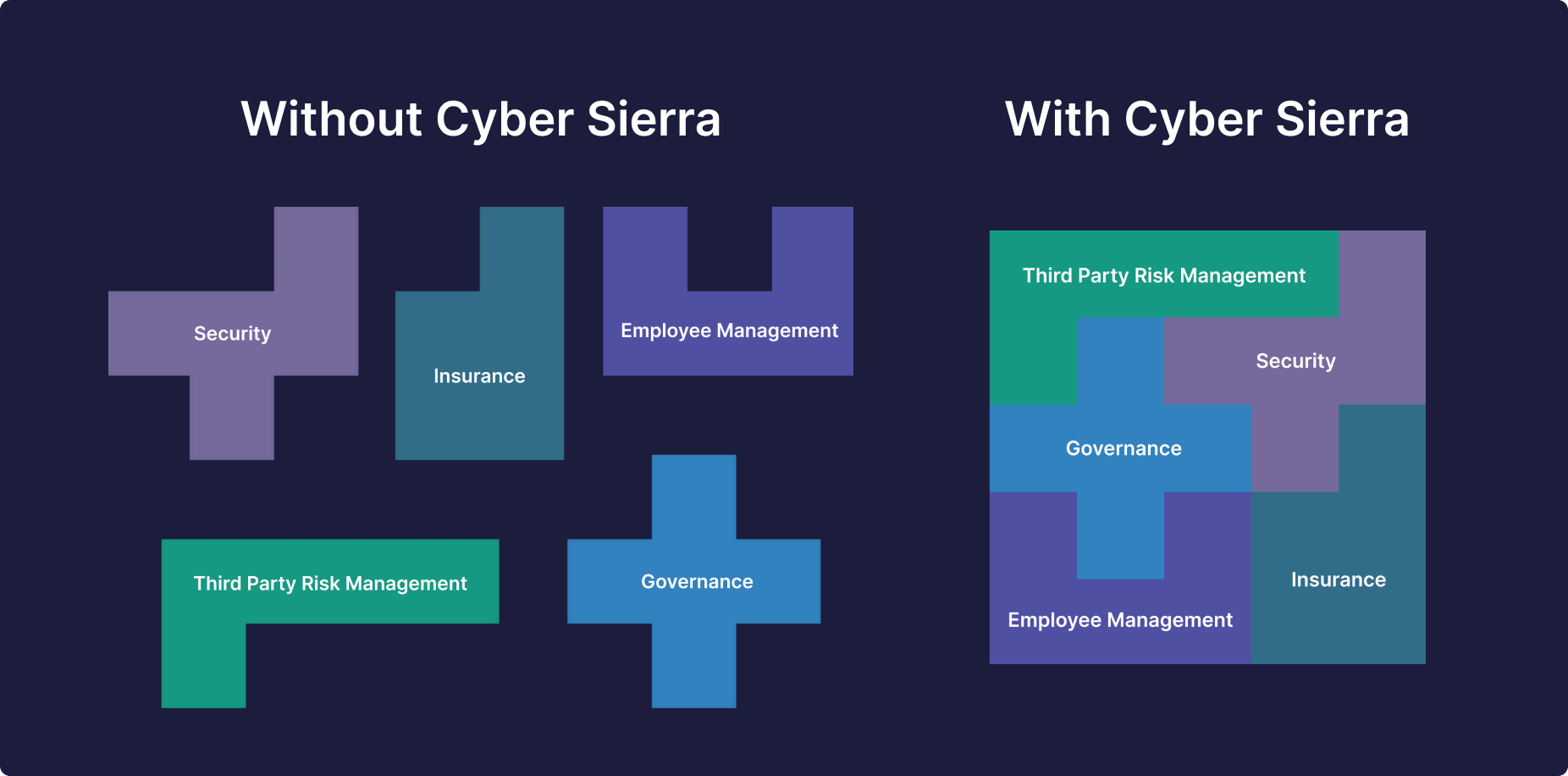
First, here’s how our platform makes it all possible. From the ground up, we built it to automate parts of each process. And to solve interoperability issues arising from combating security risks with different tools:




Automate Solving Crucial Data Security Threats with One, Interoperable Platform


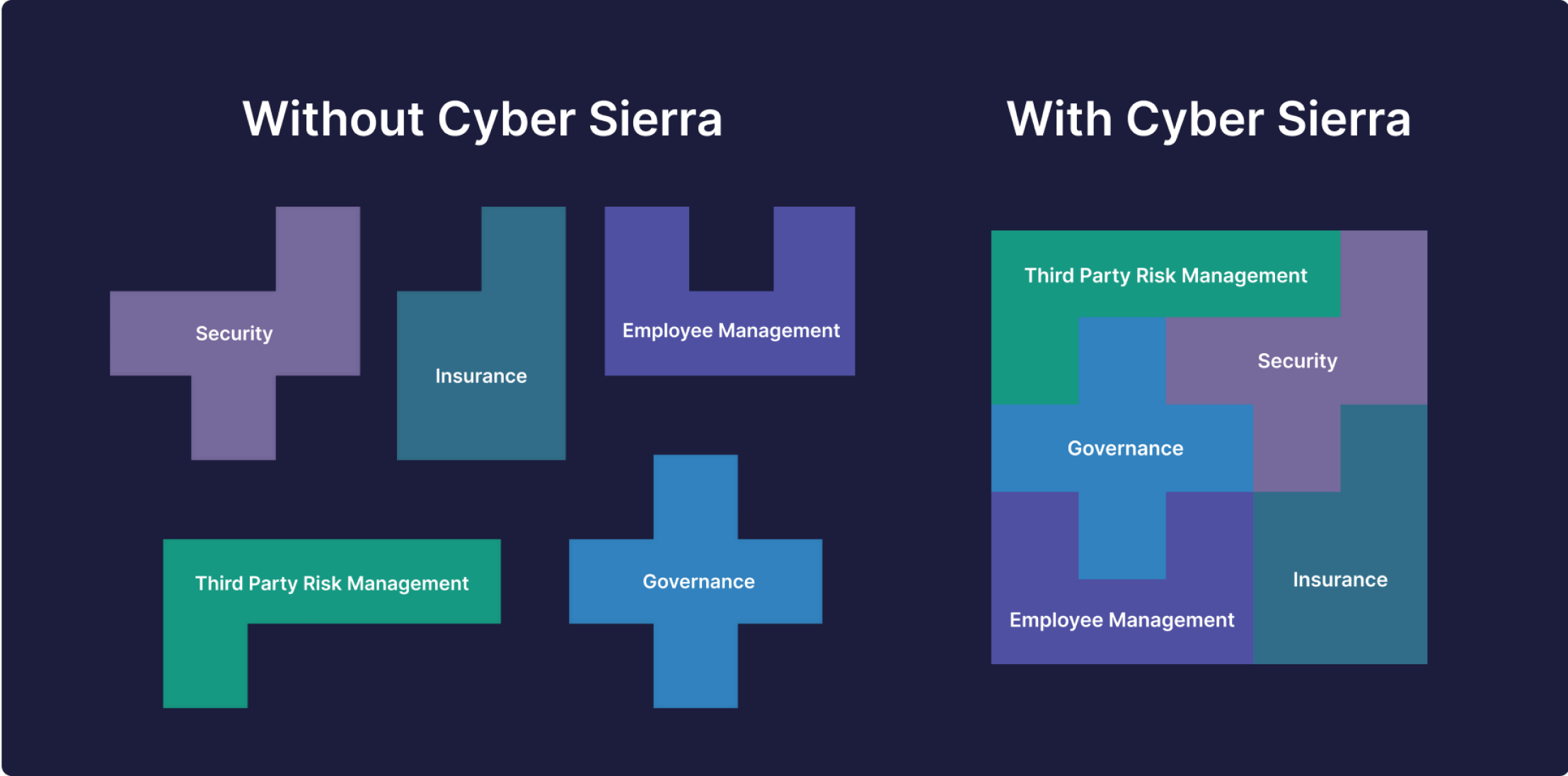


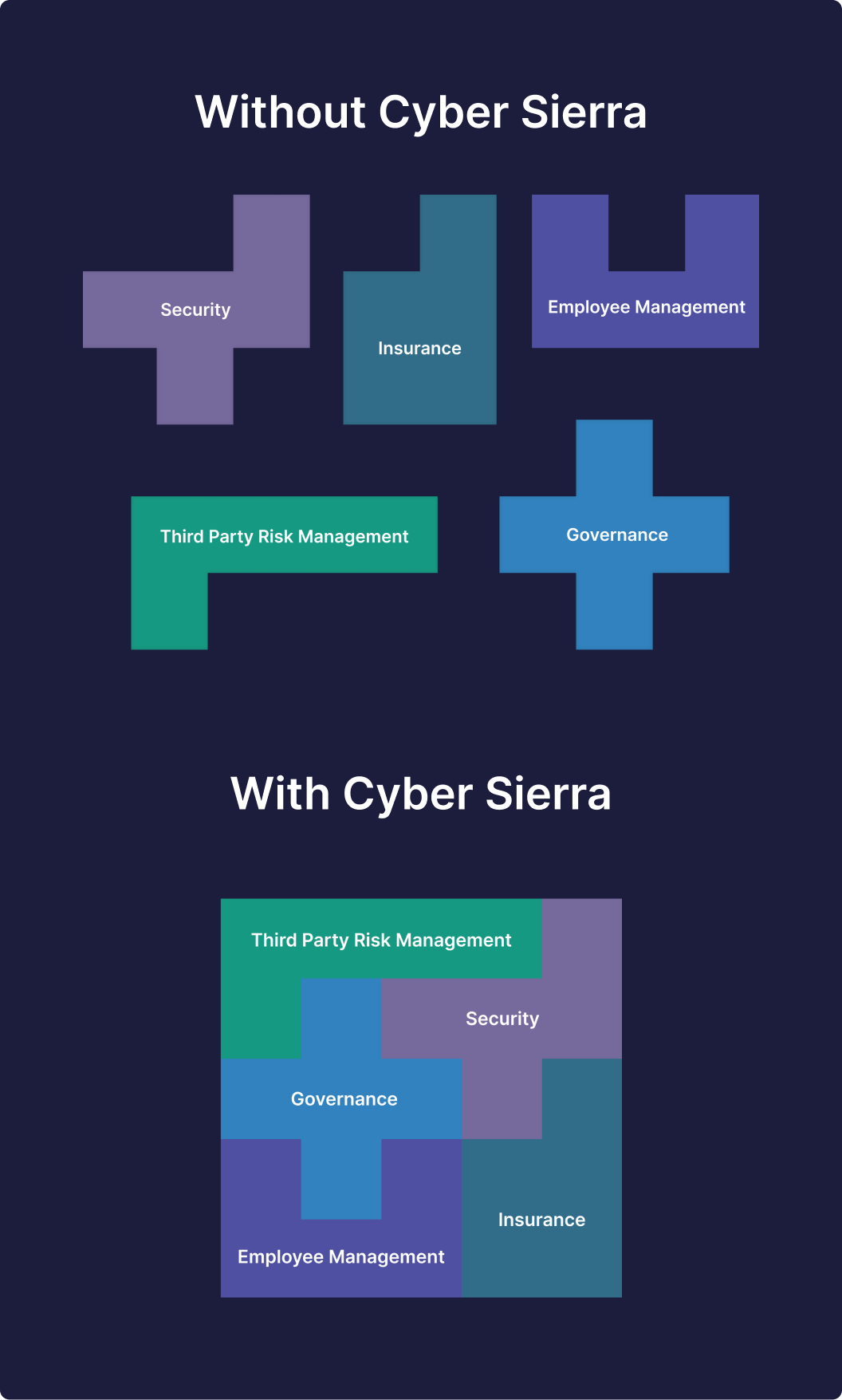


How to Automate Mitigating Data Security Challenges
Reality check.
Data breaches arising from failure to mitigate security risks is more likely to happen, per IBM’s recent study. While that’s the reality 87% of companies must deal with, our interest in this study is the role automation plays:
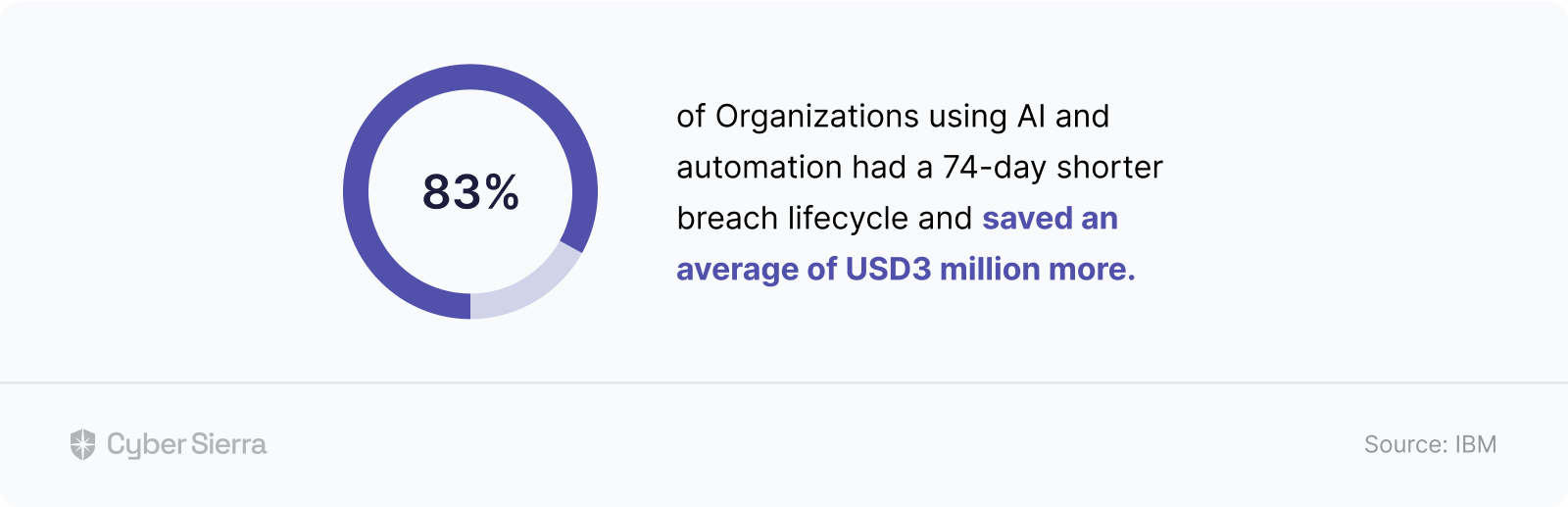

In other words, to maximize such time and money savings highlighted above, consider using some form of automation to:
- Cut off all unnecessary manual back and forth required to implement each risk-countering process. Examples include ongoing employee awareness training, cloud misconfiguration scans, third-party vendor risk assessments, etc.
- Automatically consolidate results from each process into a single view, so stakeholders can see your company’s cyber hygiene in real-time. This simplifies the process of acquiring and renewing compliance certifications and securing cyber insurance.
With Cyber Sierra, achieving both is within reach.
Say you want to automate solving data security threats arising from cloud misconfigurations. It’ll only take two initial steps.
Integrate your company tools (cloud, network, repository, and Kubernetes) directly on the Cyber Sierra platform:
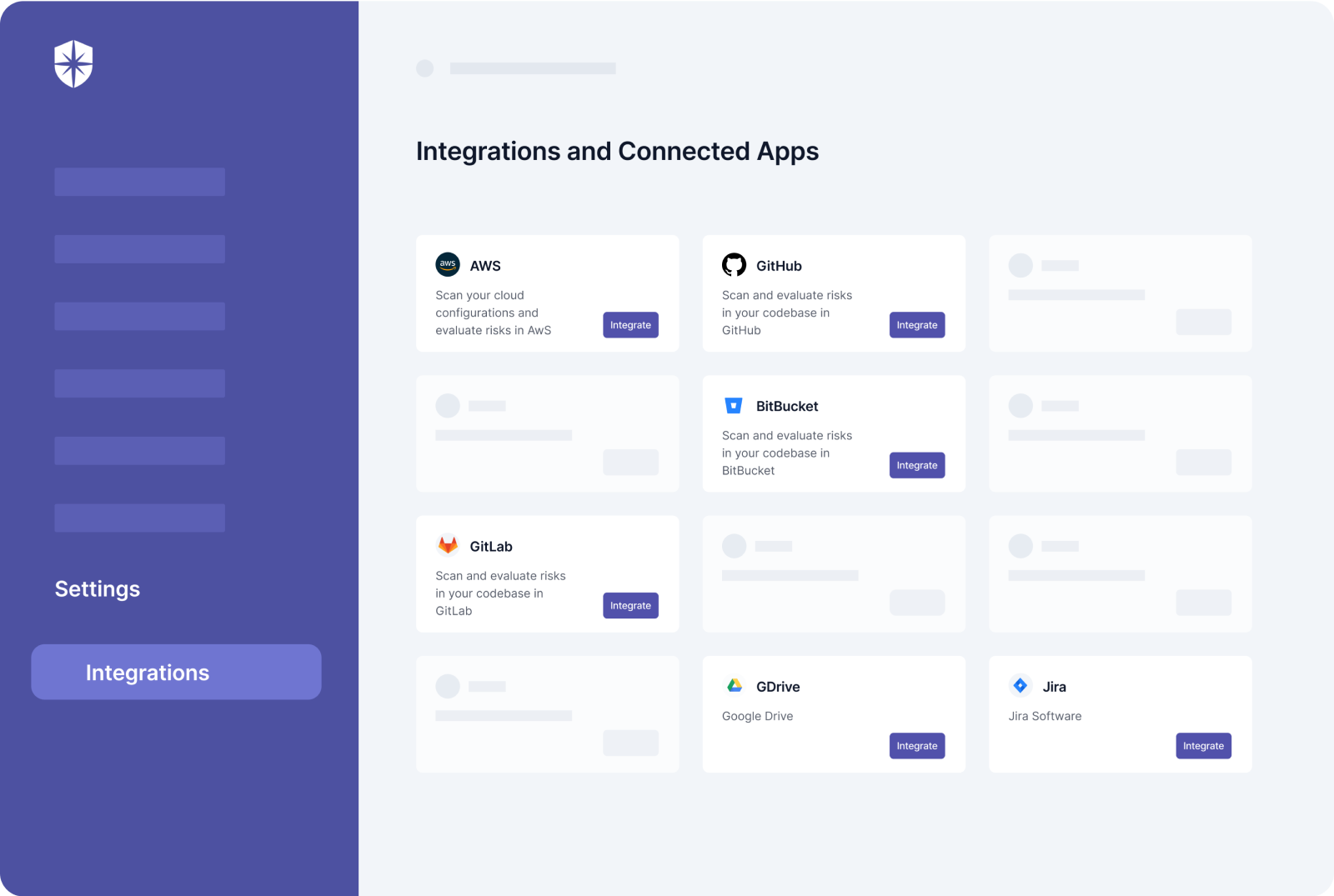

A few clicks after integration scans your company’s cloud, repository, network, or Kubernetes’ environments. And in real-time, you get a risk registry that gets automatically updated.
Here’s what it’ll look like:
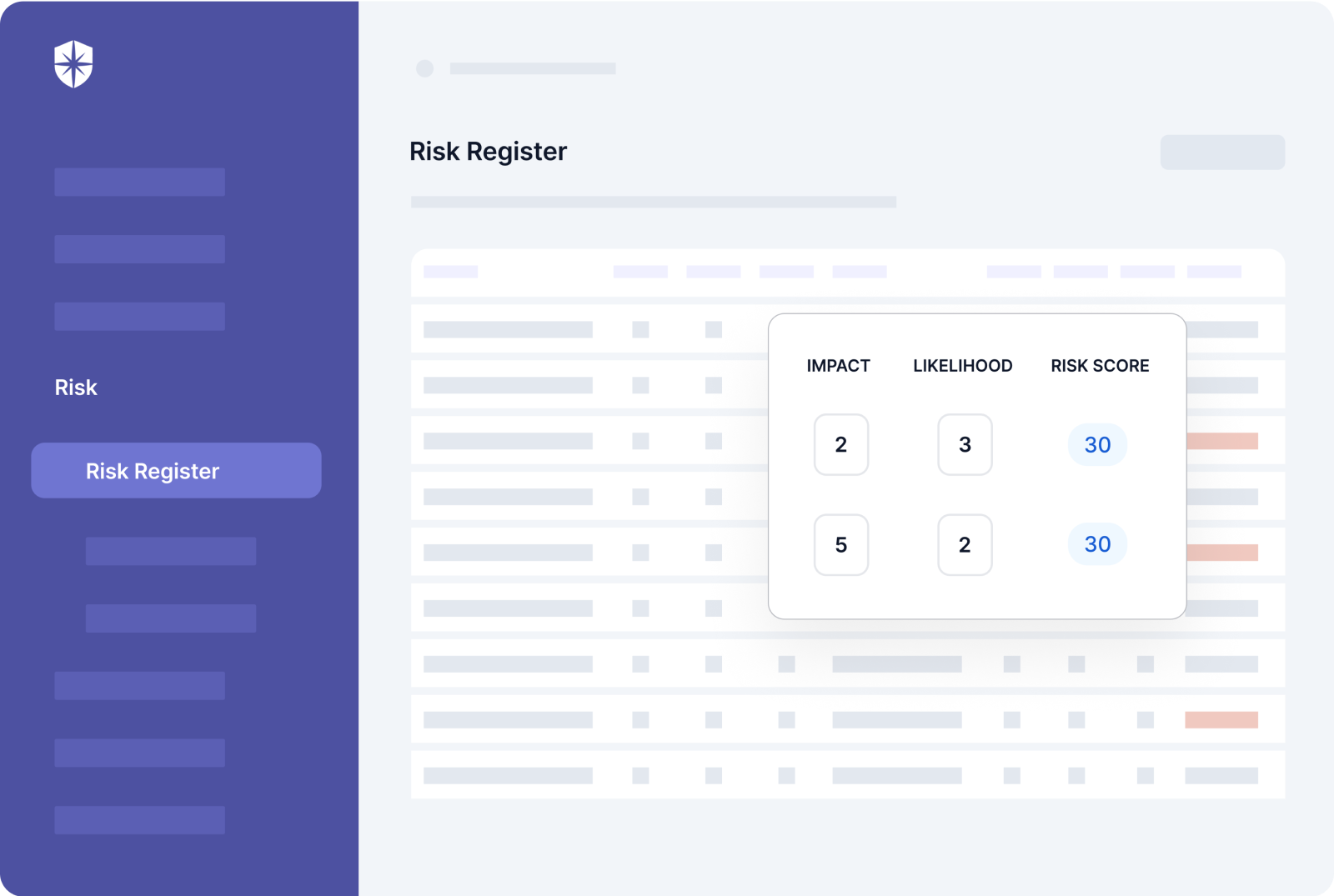

The other benefits to tackling data security issues this way are:
1. Detecting Vulnerabilities Early
As shown above, having a real-time risk registry gives your team one view to see and jump on tackling vulnerabilities early. This can have profound data security risk-mitigating and business impact.
For instance, the IBM study cited earlier also found that:
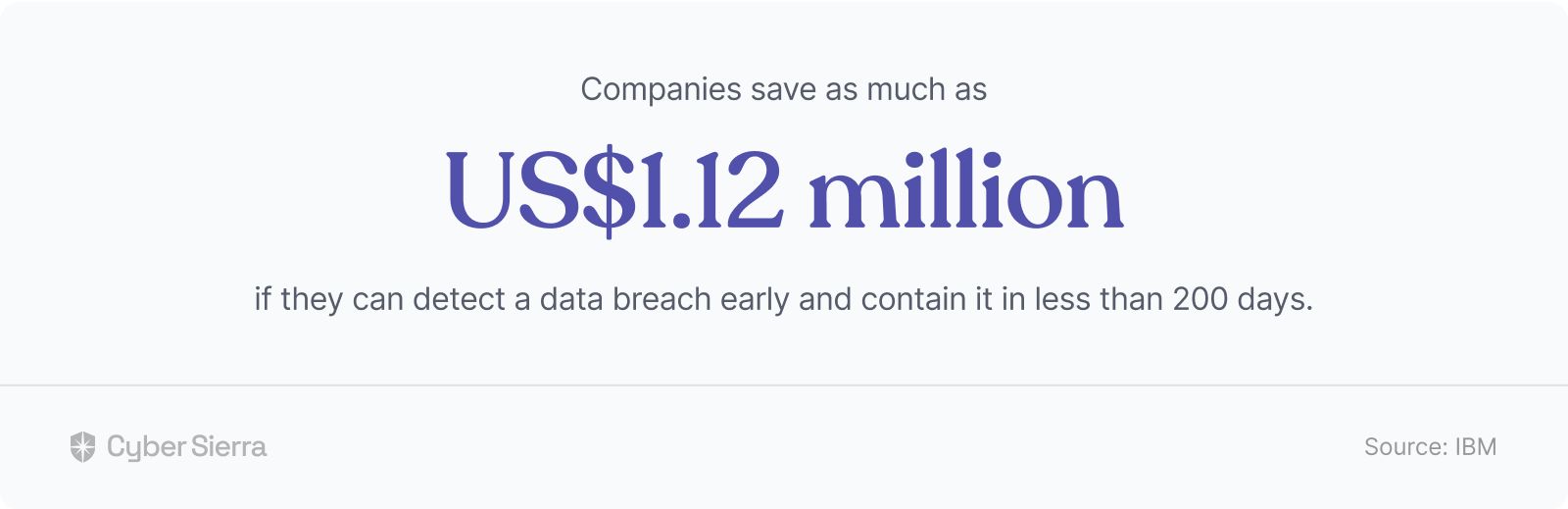

Your company could be one of those making such savings.
2. Automating Compliance Certifications
The initial effort and costs of getting crucial compliance certifications (SOC 2, ISO 27001, HIPAA, etc.) depends on one thing: How great your organization’s existing security program is.
Rob Black of Fractional CISO shared this view:
Many clients ask us how much their time/effort is going to cost. The answer is the same… it depends! Do you have a great security program that just needs validation or are you building everything from scratch? The former is going to be a lot less work than the latter.


Here’s what this means for you.
Automating parts of the various processes of mitigating data security risks reduces the time, effort, and costs required to get compliance certifications.
And with Cyber Sierra, it doesn’t end there.
All your core security modules live in a single, interoperable platform that works well together. So beyond being much easier to get initial certifications, your team can monitor controls continuously, making the renewal of certificates smoother.
It also means you can apply for new compliance programs faster, and from the same dashboard:
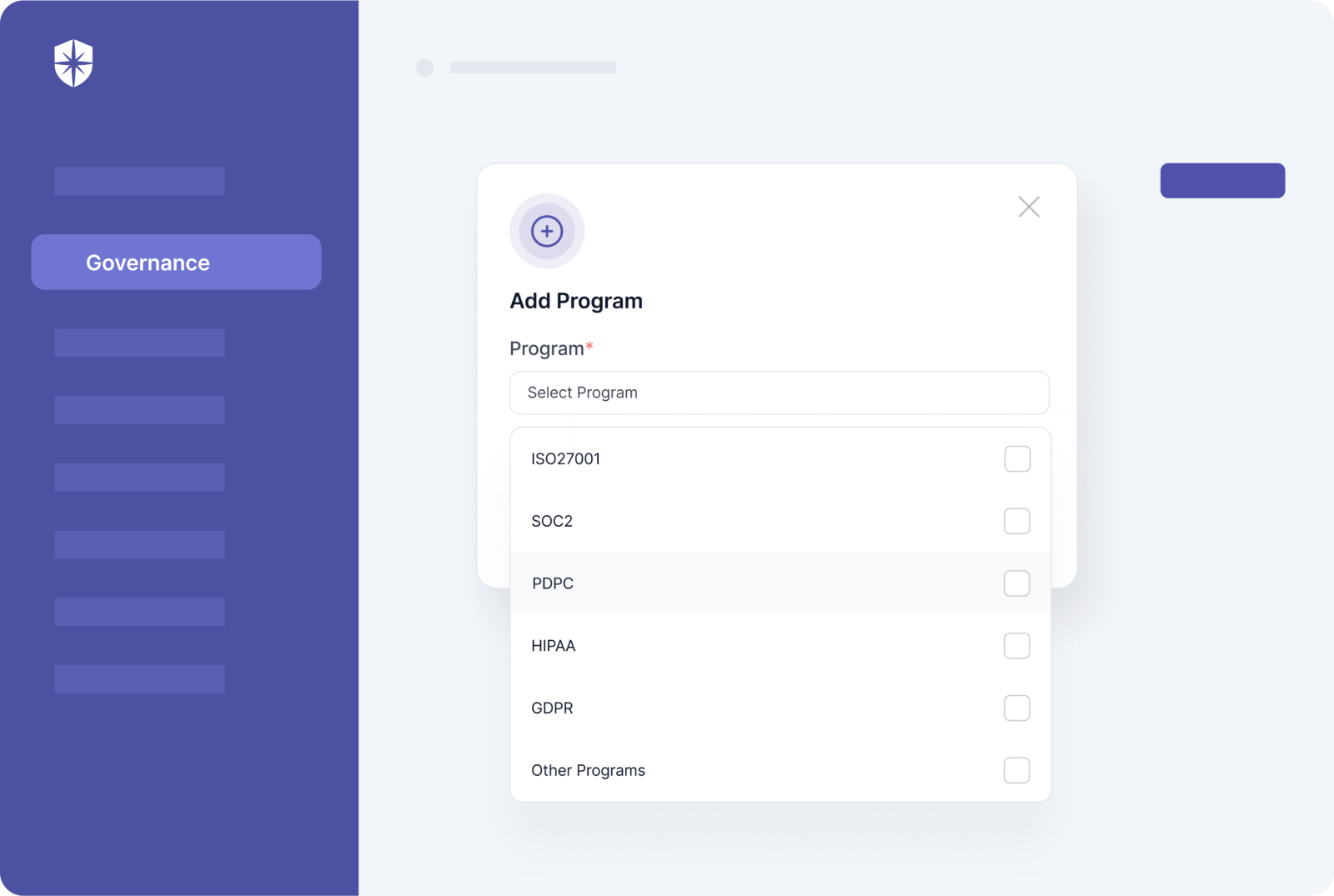

3. Securing Cyber Insurance with Ease
To buy life insurance, you must meet certain health conditions.
The same applies to securing cyber insurance to protect your organization, as cybercriminals devise new and more sophisticated data-breaching methods. To get favorable premiums, you need an optimal cyber hygiene posture, which comes from having a mature data security system in place.
Sue from SecurityIntelligence said it best:
Companies that have a mature cyber security system should be ready to meet the requirements set by cyber insurers. Others with less mature systems or that have struggled to meet risk assessment goals during the pandemic will need to be more proactive.


As it is with getting and renewing compliance certifications, so it is with securing and renewing cyber insurance. It starts with automating bits of the processes of solving data security threats. This makes your company more eligible for coverage by improving your cyber posture.
Cyber Sierra helps you achieve all that.
And you can also streamline parts of the process of getting cyber insurance coverage right on our platform:
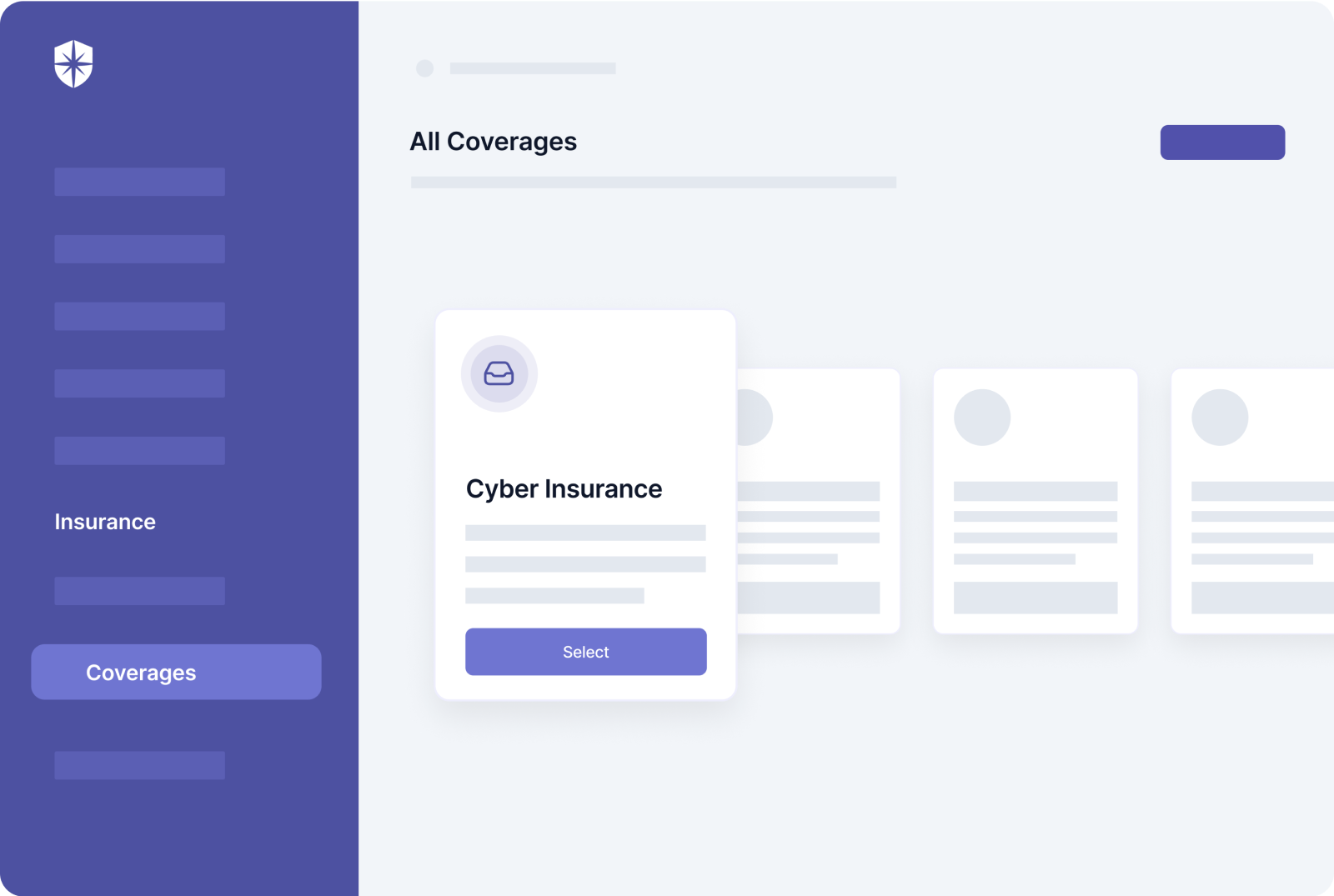

Stay In the Know, Always
Here’s a CTO’s advice to CTOs:
The CTO should help create a culture that prioritizes security as the responsibility of the whole organization instead of considering it a function of the IT department alone. This requires analyzing security risks at many different levels and engaging everyone in the organization about the necessity of following organizational security practices.


From this advice comes the question:
How do you create a culture that prioritizes data security as a responsibility of the whole organization?
Our recommendations:
- Launch ongoing employee awareness training programs to keep employees in the know of security updates, always. This will protect your company from internal errors and negligence.
- Automate ongoing cloud misconfiguration scans to keep your IT team in the know of vulnerabilities to prioritize. This protects you from external actors looking for exploitable data-breaching loopholes.
- Automate third-party risk management to keep vendors in the know of data security assessments they must complete to continue working with you. This saves you from getting breached through 3rd parties who access your networks.
All these are easier with Cyber Sierra:




Automate Solving Crucial Data Security Threats with One, Interoperable Platform












A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.