Steps to Effective Third-Party Risk Management - Safeguarding Your Business Partnerships





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
‘You’re only as strong as your weakest link’. In today’s interconnected business landscape, this adage carries more weight than ever before.
Why, you might ask?
Because third-party partnerships, for all their benefits, could very well become that weak link when not properly safeguarded.
Does your organization have a robust third-party risk management program in place?
If the answer gives you pause, you are not alone. Many businesses grapple with the challenge of managing third-party risks effectively.
In this guide, you will learn how to set up a third-party risk management program to help avoid costly mistakes and legal entanglements.
Let’s dive in.
Effective third-party risk management - a step-by-step guide
To effectively manage third-party risks, you should take a step-by-step approach. The following section guides how to set up a robust program that includes the following seven key components:
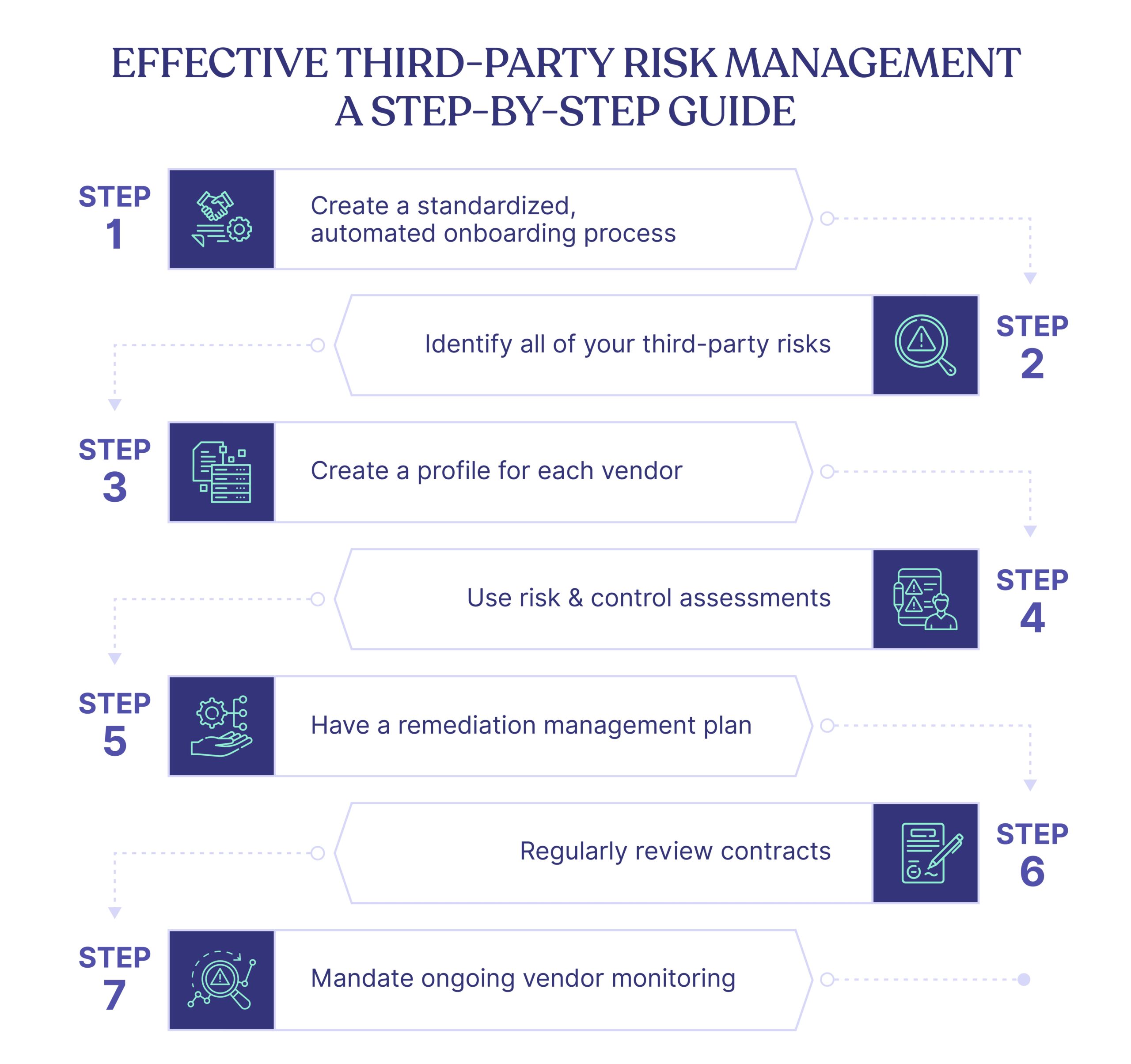

1. Create a standardized, automated onboarding process
A successful third-party risk management starts with a structured onboarding process for every vendor.
Why?
To ensure all necessary compliance checks are conducted with the same level of rigor, regardless of the vendor.
The process must entail:
- Background Checks: Do a complete background and reputation check on the vendor, including operational history and potential compliance issues.
- Financial Stability Assessment: This helps understand the vendor’s operational robustness and prevent unexpected business operation disruptions.
- Security: Review the vendor’s security practices, data management policies, and disaster recovery plans to prevent future data breaches.
- Regulatory Compliance: Check their adherence to industry regulations, licenses, and data protection laws.
Automating these tasks ensures fewer errors and consistency.
2. Identify all of your third-party risks
Upon onboarding, thoroughly evaluate any existing and potential third-party risks associated with new vendors. This process includes identifying financial, legal, operational, cybersecurity, and reputational risks.
- Financial risks require understanding a third party’s financial stability, which is crucial to ensure uninterrupted service delivery.
- Legal risks encompass potential litigation or regulatory sanctions due to the third party’s actions. You must ensure your partner’s adherence to regulations and laws to safeguard your legal position.
- Operational risks involve potential losses due to the third party’s failed internal processes, people, or systems.
- Cybersecurity risks, prevalent and growing, relate to potential data breaches and cyber threats.
- Lastly, reputational risks can cause significant damage due to a third party’s unethical or controversial actions.
To address each risk effectively, you should collaborate with stakeholders from different departments to gain insight into every aspect of the third-party relationship.
3. Create a profile for each vendor
Establishing a complete vendor profile helps maintain an organized database of all current and prospective vendors.
Each vendor profile should include essential information such as company details, risk assessments, contracts, performance reviews, and other relevant documentation. A comprehensive vendor profile enables you to make informed decisions about your partnerships while evaluating risk and adjusting as needed.
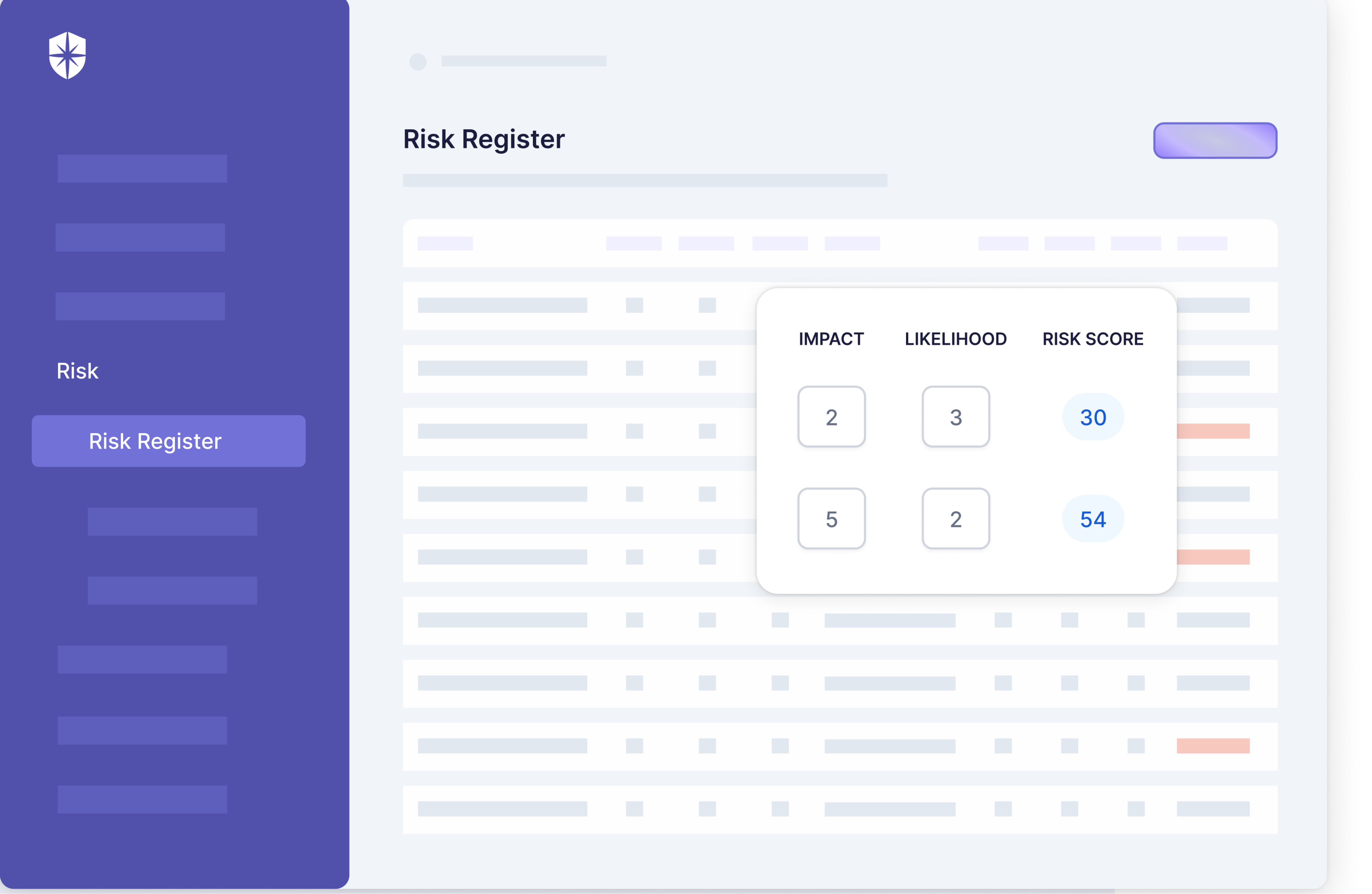
4. Use risk & control assessments
Risk and control assessments are vital for efficient third-party risk management. They evaluate vendors’ compliance with your organization’s policies, procedures, and relevant regulations.
Risk assessments identify vulnerabilities, estimate threats’ probability and impact, and measure associated risks with each vendor. Control assessments focus on the effectiveness of vendors’ measures to mitigate acknowledged risks, including procedures to prevent or manage threats.
Tailor assessments to each third-party relationship, considering the specific services, industry context, and unique risks. Assessments should be iterative, reflecting changes in the business risk profile, vendor operations, or relevant laws and regulations.
These assessments’ results inform risk management decisions, such as avoidance, transfer, mitigation, or acceptance. They offer insights into vendor performance and improvement opportunities, guiding decisions like contract renewals or terminations and aiding in enhancing vendors’ risk management practices.
5. Have a remediation management plan
A remediation management plan is crucial in third-party risk management as it addresses risks and issues identified during risk and controls assessments.
This plan should clearly outline the required actions for each risk, assigning responsibilities to specific individuals or teams. Deadlines should be set to ensure timely implementation. Additionally, monitoring the progress of the remediation plan is essential.
Regular reporting and follow-ups should be built into the plan to hold vendors accountable for mitigating the risks per the agreed timelines. Doing so assures proactive management of issues before they manifest into tangible problems affecting your operations or reputation.
For instance, Cyber Sierra offers a continuous monitoring system that can help identify vulnerabilities in near real-time and guides steps to overcome them.

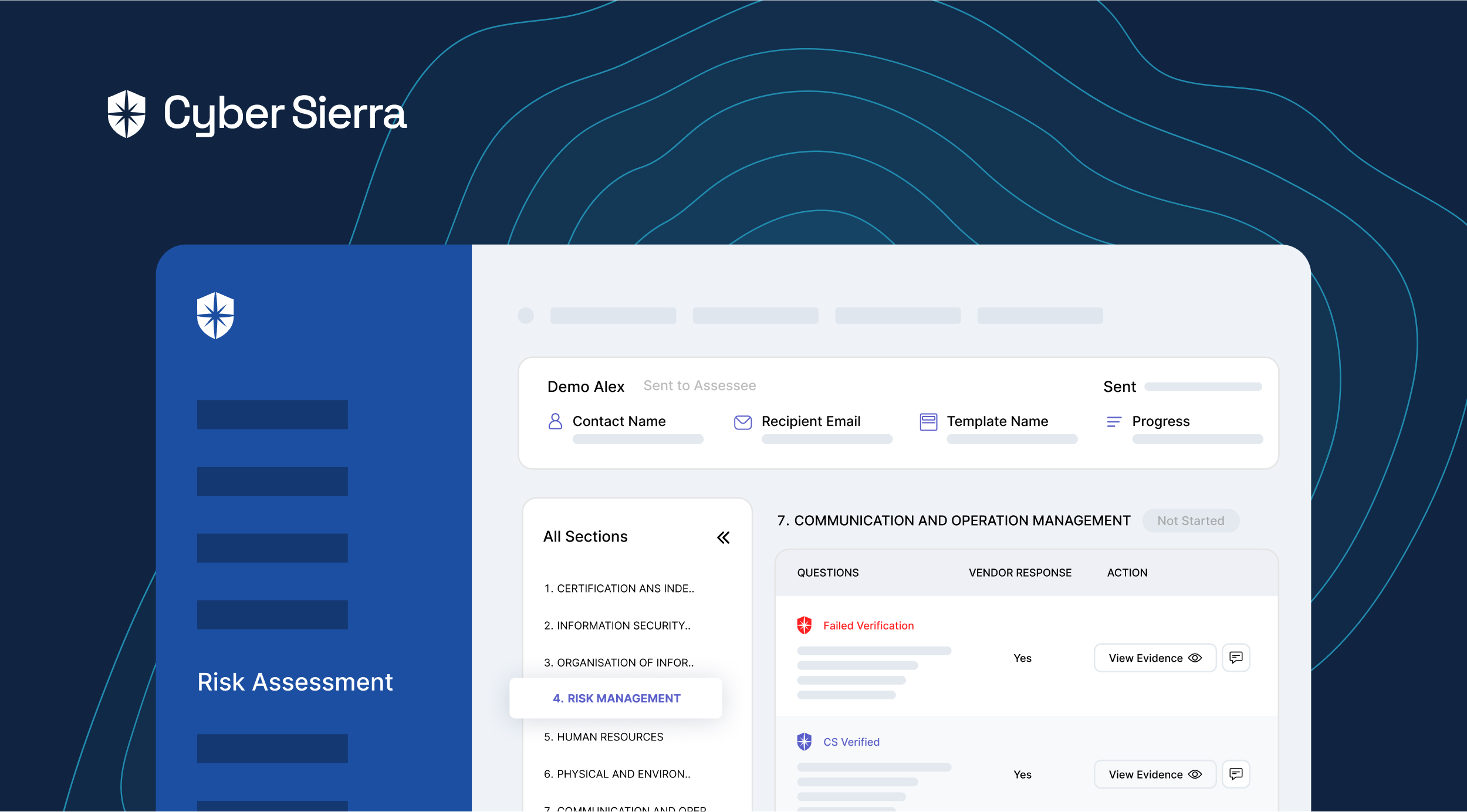
6. Regularly review contracts
Third-party contracts need regular reviews to ensure they remain current and effective in the light of evolving business requirements, regulatory environment, or identified risks.
This practice helps incorporate new standards or regulations into existing agreements, thereby ensuring compliance.
In this way, contract reviews turn into a preventive measure, minimizing the probability of unanticipated risks and safeguarding your organization’s interests.
7. Mandate ongoing vendor monitoring
Ongoing vendor monitoring helps detect and manage emerging risks in third-party relationships in real time. This process validates that vendors uphold their agreed-upon performance levels and continually meet your organization’s risk management objectives.
Effective vendor monitoring may comprise periodic assessments, performance evaluations, and regular audits. Not only does this practice help identify potential issues early, but it also triggers timely actions to prevent any negative impact.
Consequently, ongoing monitoring strengthens business partnerships, maintains operational stability, and fosters trust and reliability between your organization and its vendors.
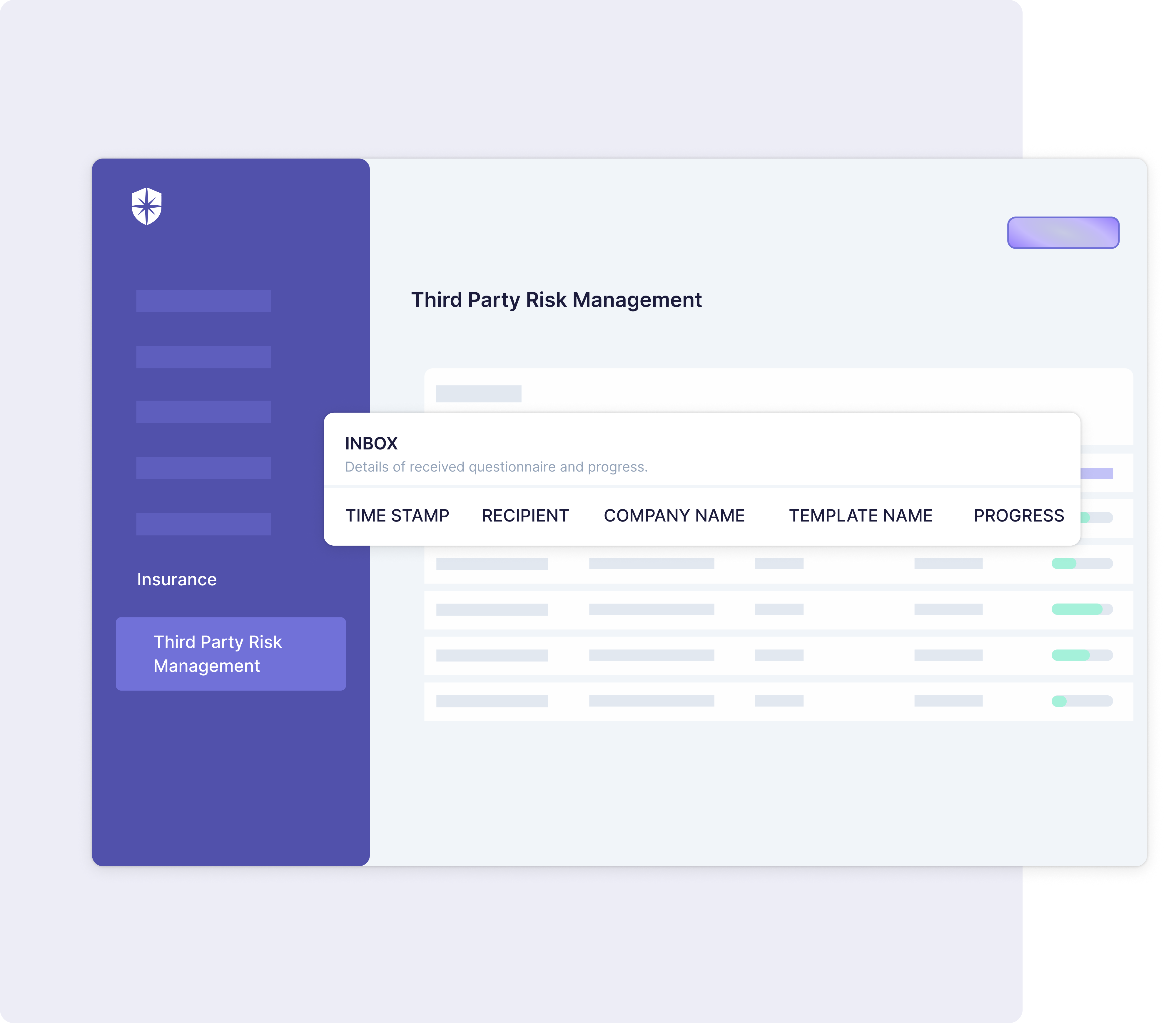

The Cyber Sierra platform integrates seamlessly into your systems, allowing for ongoing monitoring of potential threats. It provides a robust solution for real-time vendor risk monitoring, empowering your organization to meet its third-party risk management objectives proactively.
Wrapping Up
Implementing a robust third-party risk management program is indispensable in today’s business environment. Not only does it establish secure business partnerships, but it also guards the very future of your organization. An effective program can build trust, increase resilience, and offer a competitive edge despite potential risks and uncertainties.
However, addressing third-party risk management’s complexity requires an integrated, comprehensive solution.
This is where Cyber Sierra can make a difference. With the ability to connect the dots across your entire organization, Cyber Sierra provides a comprehensive risk management solution to help you identify and manage third-party risks.
Book a demo to learn more.



A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.