

What are the top 7 Third Party Risk Management Tools?



Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
From business affiliates and contractors to partners and suppliers, most organizations utilize third-party relationships to run their day-to-day activities. This exposes them to more third-party risks that can be complex to manage without the right tools.
For instance, on May 31, 2023, MOVEit, a third-party file transfer software owned by Progress, a NASDAQ listed software company, that’s used by thousands of private and government organizations to transfer and receive data was attacked by a group of cybercriminals. The attack enabled cybercriminals to access and download files belonging to a handful of agencies in the State of Maine.
These widespread attacks can impact organizations due to the hefty costs and fines they come with. According to a report by IBM, the global average cost of data breaches increased by 2.3% from USD 4.35 million in 2022 to USD 4.45 million in 2023.
To avoid these insane costs, organizations need to invest in powerful third-party risk management software that can help implement a robust risk management program.
Sadly, most organizations still rely on outdated third-party risk management solutions that leave them vulnerable to data breaches and compliance issues.
Let's face it – using outdated or inadequate software only exposes your organization to more vulnerabilities and hefty fines.
If you are looking to safeguard your business from third-party risks, this blog explores the top 7 third-party risk management platforms that can help your organization better assess, monitor, and mitigate risks associated with external partners and vendors.
But before that, let’s clear out a few things.
What is Third-Party Risk Management Software?
Third-party risk management software is a set of tools that can help organizations identify, analyze, and mitigate the external challenges posed by their service providers, IT vendors, contractors, and other third parties.
These tools enable organizations to assess the risks associated with these entities and take appropriate measures to rectify and remediate them, thus safeguarding against institutional and reputational damage.
One of the primary roles of third-party risk management tools is to assess the potential risks in engaging with third-party vendors.
By evaluating factors such as financial stability, security protocols, regulatory compliance, and past performance, organizations can make informed decisions regarding the selection and initial onboarding of third parties.
The software also facilitates ongoing monitoring of these entities to ensure that they continue to meet the necessary standards and requirements.
In the event of identifying risks or issues, the software plays a vital role in guiding organizations through rectification and remediation efforts.
It assists in implementing corrective actions, ensuring that the third party addresses the identified vulnerabilities promptly.
Investing in a third-party risk management system can be beneficial for organizations in many ways including:
- Automated vendor risk management which leads to increased efficiency
- Enhanced visibility of each activity in the lifecycle and centralization of your processes and data, which improves collaboration across your organization
- Better contract management
- Reduced errors often found in manual processes
- Ease of reporting
- Improved risk management
- Enhanced compliance
- Better decision-making
7 Best TPRM Tools in 2024
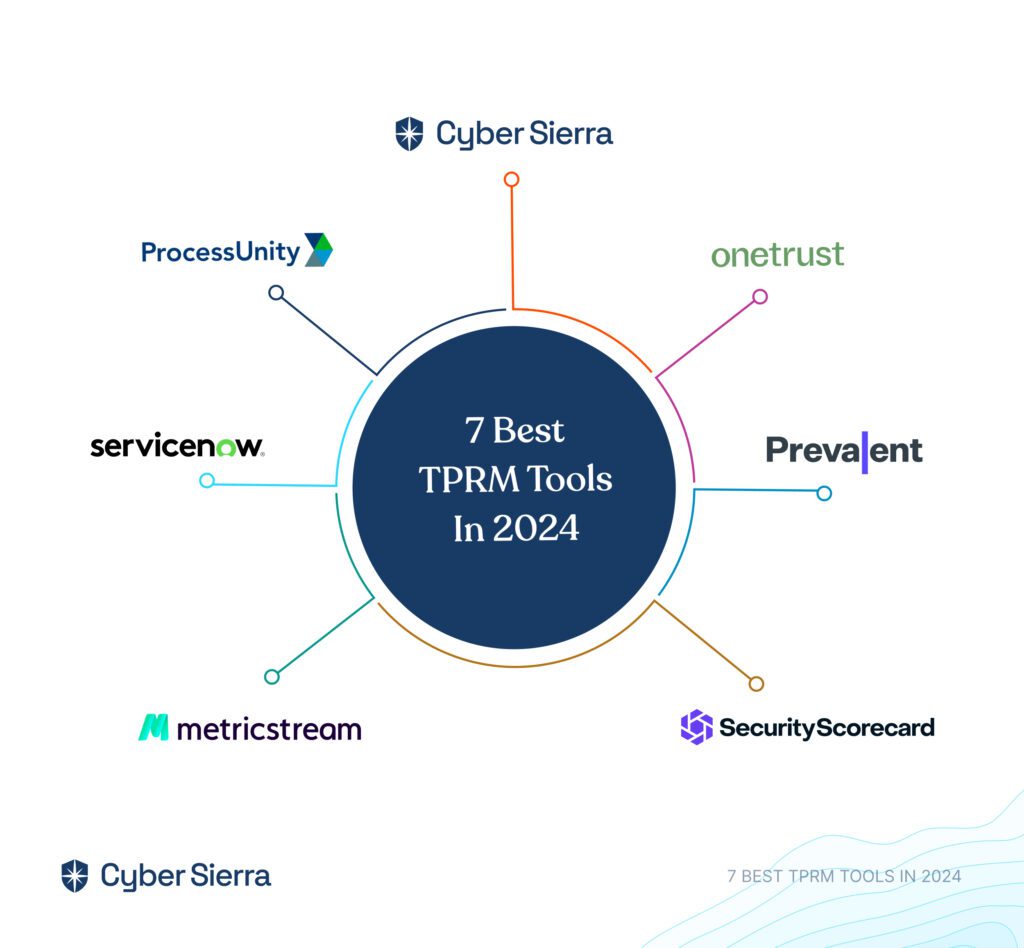

Here are the top 7 best third-party risk management platforms.
1. Cyber Sierra

Best for: Large enterprises looking for innovative, customizable solutions with advanced risk assessment methodologies and scalability. The platform however can be tailored to suit the needs of mid-sized organizations also.
Cyber Sierra’s third-party risk management tool is a comprehensive solution designed to help organizations effectively manage the risks associated with their third-party relationships.
With a range of key features and benefits, this solution empowers users to take control of their third-party cyber risk management.
The tool is a game-changer in the realm of safeguarding against cyber risks from external partners. With its robust capabilities, it outshines competitors like MetricStream, Prevalent, and others.
The software excels in managing third-party risk by providing a comprehensive suite of tools for supplier assessments, risk identification, and continuous monitoring. Its key feature lies in offering real-time insights into vendor risks, allowing organizations to stay ahead of potential threats.
One standout aspect is its integration capabilities, seamlessly connecting with existing systems to streamline workflows. This ensures that risk management teams have a complete picture of vendor risks to launch effective risk mitigation strategies.
Cyber Sierra’s solution empowers users to take control of their third-party cyber risk assessments by providing intuitive user experiences and collaborative platforms. It goes beyond mere compliance management by offering advanced features for ongoing monitoring and risk mitigation.
Here's what sets Cyber Sierra apart:
- Streamlined workflows: Cyber Sierra boasts an intuitive user experience that simplifies tasks for your risk management teams.
- Real-time monitoring: The software continuously monitors the security posture of your vendors to give you a complete picture of their current risk profile.
- Customization: Every company's needs are different. The platform lets you tailor your risk assessments and compliance management programs to fit your industry and regulatory requirements.
- Comprehensive cyber risk check: Unlike its competitors, Cyber Sierra offers a deep dive into cybersecurity risk factors associated with third-party vendors. Its advanced algorithms analyze a multitude of risk factors to provide users with a thorough understanding of potential security risks.
- Robust third-party risk analysis: The tool goes beyond basic risk assessments by providing industry-leading third-party risk analysis capabilities. It not only identifies risks but also offers insights into the root causes which empowers organizations to make informed decisions about risk mitigation strategies.
- Efficient remediation efforts: With Cyber Sierra, organizations can efficiently streamline their remediation efforts. The software not only identifies vulnerabilities but also provides actionable recommendations for addressing them effectively. This ensures that organizations can quickly resolve security issues and minimize potential damage. The platform also helps get cyber insurance in case of risk transfer.
Pricing
Cyber Sierra’s pricing is customizable based on your needs and available upon request.
2. OneTrust
Ideal for: Organizations seeking a third-party risk assessment and management solution to streamline data processing and compliance reporting.
OneTrust's third-party risk management solution facilitates third-party risk assessment and management. It provides out-of-the-box templates for building custom assessments, simplifying the process of evaluating third-party risks.
This solution aids users in managing third-party risk by automating various aspects of the risk management process. It enables organizations to automate third-party risk assessments, streamline third-party onboarding, and implement risk mitigation strategies effectively.
OneTrust helps reduce reputational risk by providing out-of-the-box mitigation recommendations and workflows. It allows users to maintain a comprehensive third-party inventory and track risk exposure across the vendor ecosystem.
Even though OneTrust boasts powerful tools for automating third-party risk management programs, it can lack some of the unique features that Cyber Sierra provides.
For instance, Cyber Sierra simplifies complex data and provides actionable insights through features like dashboards or automated reporting. Besides, while both likely offer TPRM features, Cyber Sierra includes regular security awareness training for employees. This could be a valuable addition depending on your overall security strategy.
Key features
- Automated workflows: The platform automates and streamlines workflows for vendor onboarding, risk assessment, remediation, and ongoing monitoring to enhance efficiency and consistency in third-party risk management processes.
- Build an inventory of third parties and track the information you care about most: OneTrust third-party risk management helps you build an inventory of third parties and track the information you care about most.
- Continuous monitoring: It continuously monitors the security posture and compliance status of third-party vendors throughout the vendor lifecycle to enable organizations to proactively identify and address emerging risks and vulnerabilities.
Pricing
OneTrust pricing is available upon request.
3. Prevalent
Ideal for: Companies seeking a comprehensive TPRM solution with a focus on post-contract due diligence and inherent risk.
Prevalent is a prominent SaaS platform offering a handy third-party risk management platform to help organizations streamline vendor and supplier risk management.
With the Prevalent third-party risk management platform, users can evaluate and manage third-party risks efficiently. Besides, the software allows users to onboard third-party vendors, conduct risk assessments, and perform post-contract due diligence.
One notable feature is its auto-inherent risk scores, which provide users with insights into the inherent risk associated with each vendor. This allows organizations to prioritize their risk management efforts and focus on vendors with higher inherent risk profiles.
Prevalent enables users to take control of their third-party risk assessment and management by streamlining the vendor onboarding process and automating risk assessments. By providing a structured approach to vendor risk management, the platform helps organizations identify and mitigate potential risks effectively.
While Prevalent offers valuable capabilities for managing third-party risks, it's important to consider how it aligns with the specific needs and priorities of the organization.
If your organization requires highly customized workflows, assessments, or reporting capabilities, Cyber Sierra might offer a more flexible and customizable platform compared to Prevalent.
Key features
- Inherent risk assessment: Prevalent provides auto-inherent risk scores, allowing users to quickly assess the inherent risk associated with each third-party vendor.
- Streamlined vendor onboarding: The platform facilitates seamless third-party onboarding, simplifying the process for both vendors and organizations.
- Post-contract due diligence: The software supports post-contract due diligence activities, helping organizations monitor and manage ongoing vendor relationships effectively. This feature is valuable for organizations seeking to continuously evaluate and mitigate risks throughout the vendor lifecycle.
- Contract process integration: The platform seamlessly integrates with the contract process, enabling organizations to incorporate risk management considerations into contract negotiations and agreements.
Pricing
Prevalent pricing is available upon request.
4. SecurityScorecard
Designed for: Cybersecurity teams looking for a third-party cyber risk management solution to monitor and manage the cybersecurity of their extensive vendor networks and improve their security posture
SecurityScorecard offers a comprehensive third-party risk management solution that supports the overall cybersecurity risk management workflow.
It provides organizations with the necessary tools and insights to effectively assess, monitor, and mitigate cyber risks associated with their third-party vendors.
This solution begins by conducting an initial assessment of all third-party vendors based on various risk factors. It analyzes the security posture of each vendor, evaluating factors such as their network security, patching cadence, endpoint security, DNS health, and other critical indicators.
The gathered data is then used to generate a risk score for each vendor, which aids in prioritizing risk mitigation efforts.
Once the risk assessment is complete, the software continuously monitors the security posture of third-party vendors.
It alerts organizations to any changes or incidents that may impact the security of the organization's data or systems. This allows organizations to proactively identify and address potential risks before they escalate into major security incidents.
While SecurityScorecard may offer valuable functionalities for managing third-party cyber risks, it may lack the advanced capabilities offered by Cyber Sierra.
For instance, Cyber Sierra’s third-party risk management solution offers a more comprehensive risk assessment by integrating various data sources and factors.
The software performs deep scanning of networks, supplier-specific risk profiles, and real-time threat intelligence, providing a more holistic view of third-party risks.
Key features
- Continuous monitoring: The tool provides ongoing assessment and monitoring of third-party vendors' cybersecurity posture.
- Evidence locker: It securely stores documentation and evidence related to third-party assessments, audits, and compliance.
- Score & action plans: SecurityScorecard generates risk scores for each vendor based on various factors, along with actionable insights and customized mitigation plans to address identified vulnerabilities and improve overall security posture.
Pricing
SecurityScorecard pricing is available upon request.
5. MetricStream
Suitable for: Best for larger organizations with intricate vendor networks.
MetricStream third-party risk management (TPRM) software offers a range of capabilities for managing vendor relationships and mitigating associated risks.
The software facilitates initial onboarding and ongoing management of third-party vendors, covering the complete vendor lifecycle from onboarding to risk management.
Key features include dynamic questionnaires and a library of questionnaire templates, allowing users to assess cybersecurity performance and compliance with security standards effectively.
This enables organizations to gain insights into vendor risk profiles and make informed decisions regarding risk mitigation strategies.
MetricStream provides tools for seamless onboarding to risk management processes. It enables organizations to streamline vendor assessments and ensure compliance with regulatory requirements.
While MetricStream offers robust capabilities for third-party risk management, it's important to note that it doesn’t offer customization capabilities as Cyber Sierra does. Furthermore, the software may be more complex and expensive for smaller businesses due to its broader feature set–Cyber Sierra’s TPRM can support small, mid and large enterprises.
Key features
- Streamlined third-party lifecycle management: MetricStream facilitates managing the entire third-party relationship, from onboarding and due diligence through ongoing monitoring and eventual offboarding.
- Dynamic questionnaires: The software offers dynamic questionnaires tailored to assess cybersecurity performance and compliance with security standards.
- Library of questionnaire templates: MetricStream provides a library of pre-built questionnaire templates, saving time and effort in creating assessments. These templates cover various risk domains and regulatory requirements, providing a solid foundation for vendor risk monitoring and assessments.
Pricing
MetricStream’s price is available upon request.
6. ServiceNow
Suitable for: Organizations looking to continuously monitor critical vendors so they can evaluate, mitigate, and remediate risks.
ServiceNow offers a robust third-party risk management platform in its suite of products to support users in managing third-party risks. The platform facilitates the organization's ability to track and assess risks associated with external vendors.
This solution helps users with third-party risk management by centralizing information and workflows related to vendor risk assessments. It allows organizations to streamline processes such as vendor onboarding, risk assessments, and risk mitigation efforts.
In addition, ServiceNow enables users to automate various aspects of third-party risk management to improve efficiency and accuracy in risk assessment processes. It also offers functionalities for tracking and monitoring vendor performance over time.
Note that even though ServiceNow and Cyber Sierra offer capabilities for third-party risk management, some key features set them apart. For instance, Cyber Sierra offers highly customizable vendor risk assessment templates that can be tailored to specific industries, regulatory requirements, or organizational preferences.
Key features
- Full lifecycle support: ServiceNow handles onboarding, renewals, and offboarding. The platform helps you gather info and assess risks throughout the entire dance with your third parties.
- Third-party portal: The software provides a centralized platform for third parties to interact with the organization, submit documentation, and communicate on risk-related matters.
- Risk intelligence and ongoing monitoring: ServiceNow utilizes intelligence tools to assess and monitor risks associated with third parties continuously, helping to identify potential issues proactively.
- Third-party portfolio management: It enables organizations to manage their entire portfolio of third-party relationships efficiently, including categorization, tracking, and analysis.
Pricing
ServiceNow pricing is available upon request.
7. ProcessUnity
Developed for: Companies looking to automate the third-party lifecycle and reduce risks from third parties, vendors, and suppliers.
ProcessUnity for third-party risk management is designed to safeguard companies from risks posed by third parties, vendors, and suppliers.
TPRM extends risk management beyond internal operations to encompass any external entity that could potentially threaten an organization's security or reputation.
The software offers key functions such as risk assessment, vendor onboarding, and ongoing monitoring. It enables users to centralize vendor information, conduct risk assessments, and track vendor performance over time.
Additionally, ProcessUnity provides out-of-the-box templates and customizable workflows to streamline the risk management process.
This solution aids users in managing third-party risk by providing a comprehensive view of vendor relationships and associated risks. It helps organizations identify and prioritize risks, implement mitigation strategies, and monitor vendor compliance with security standards and regulations.
ProcessUnity is particularly beneficial for organizations seeking to enhance their vendor risk management processes. It allows users to automate various aspects of third-party risk management, improving efficiency and accuracy in risk assessment processes.
Key features
- Vendor due diligence & ongoing monitoring: ProcessUnity facilitates thorough due diligence on vendors by providing tools for assessing their risk profiles and ongoing monitoring capabilities.
- Vendor onboarding: The platform streamlines the vendor onboarding process, making it efficient and effective.
- Risk domain screening: ProcessUnity offers risk domain screening functionality, allowing organizations to assess vendors across various risk domains such as cybersecurity, financial stability, compliance, and reputation.
- Inherent risk scores and vendor criticality tiers: The platform offers inherent risk scoring functionality to assess the inherent risk associated with each vendor based on factors such as industry, geography, and the nature of the services provided.
Pricing
ProcessUnity pricing is available upon request.
How to Choose the Best TPRM Tool for Your Organization
Selecting the right third-party risk management software can significantly impact your organization's security and resilience. However, this isn’t always easy for most people.


Here are some of the most important features to look for in your chosen TPRM software.
User Friendliness
The tool should be intuitive and easy to navigate for everyone involved, from technical experts to occasional users. This ensures ease of use and efficient adoption and reduces training time.
Responsive Customer Support
Opt for a provider that offers responsive and knowledgeable customer support, promptly addressing any issues or questions that may arise during tool implementation and usage. Look for vendors with multiple support channels and a proven track record of resolving customer issues effectively.
Third-Party Risk Identification
Look for software equipped with robust capabilities to proactively identify and catalog third-party risks across various categories and levels for comprehensive risk management.
Third-Party Risk Analysis
Select a tool that goes beyond basic risk identification to provide an in-depth analysis of identified risks, including their potential impact and likelihood, enabling the prioritization of mitigation efforts effectively.
Vendor Onboarding & Offboarding
Ensure the tool streamlines the process of onboarding new vendors and offboarding discontinued ones while maintaining data integrity and compliance with organizational policies and regulations.
Vendor Risk Assessment
Choose a tool that facilitates a comprehensive assessment of vendor risks through customizable questionnaires, scoring mechanisms, and risk rating methodologies, enabling informed decision-making regarding vendor relationships.
Compliance and Audit Management
Prioritize tools that offer features to manage compliance requirements and facilitate audit processes seamlessly, including tracking regulatory changes and ensuring adherence to industry standards.
Vendor Due Diligence
Opt for third-party risk management software that supports thorough due diligence processes, including background checks, financial assessments, and legal reviews, to evaluate vendor reliability and trustworthiness effectively.
Cybersecurity Ratings
Consider tools that integrate cybersecurity ratings from reputable sources to assess the security posture of third-party vendors accurately for overall risk assessment and management efforts.
Scalability and Automation
Look for TPRM software capable of scaling your organization's growth and automating repetitive tasks such as data collection, analysis, and monitoring to improve operational efficiency and reduce manual effort.
Remediation Workflows
Choose a tool with built-in workflows to manage remediation efforts, assign tasks, track progress, and ensure timely resolution of identified risks to streamline the risk mitigation process effectively.
Advanced Reporting
Prioritize tools that offer customizable reporting functionalities, including real-time dashboards, executive summaries, and detailed reports to facilitate informed decision-making and communication at all levels of the organization.
Continuous Monitoring of Third-Party Risks
Select a tool capable of providing ongoing monitoring of third-party activities and changes in risk factors, enabling the prompt identification of emerging threats and vulnerabilities for proactive risk management.
Cost
Evaluate the total cost of ownership, including licensing fees, implementation costs, and ongoing maintenance expenses, to ensure the chosen tool aligns with your budget constraints and provides value for money in addressing your organization's risk management needs.
Integration Capabilities
Look for a third-party risk management system with robust integration capabilities, allowing seamless connectivity with existing systems such as enterprise resource planning (ERP), customer relationship management (CRM), and security information and event management (SIEM) solutions.
This ensures data synchronization and workflow automation across platforms, streamlining risk management processes and enhancing overall operational efficiency.
Additionally, prioritize tools that support integration with third-party APIs and offer flexibility to adapt to evolving technology ecosystems, enabling future-proofing and scalability of your risk management infrastructure.
Use Cyber Sierra for Robust Third-Party Risk Management Program
While most of the third-party risk management tools we’ve highlighted above can be helpful for any organization, Cyber Sierra stands out for its comprehensive features and automation capabilities.
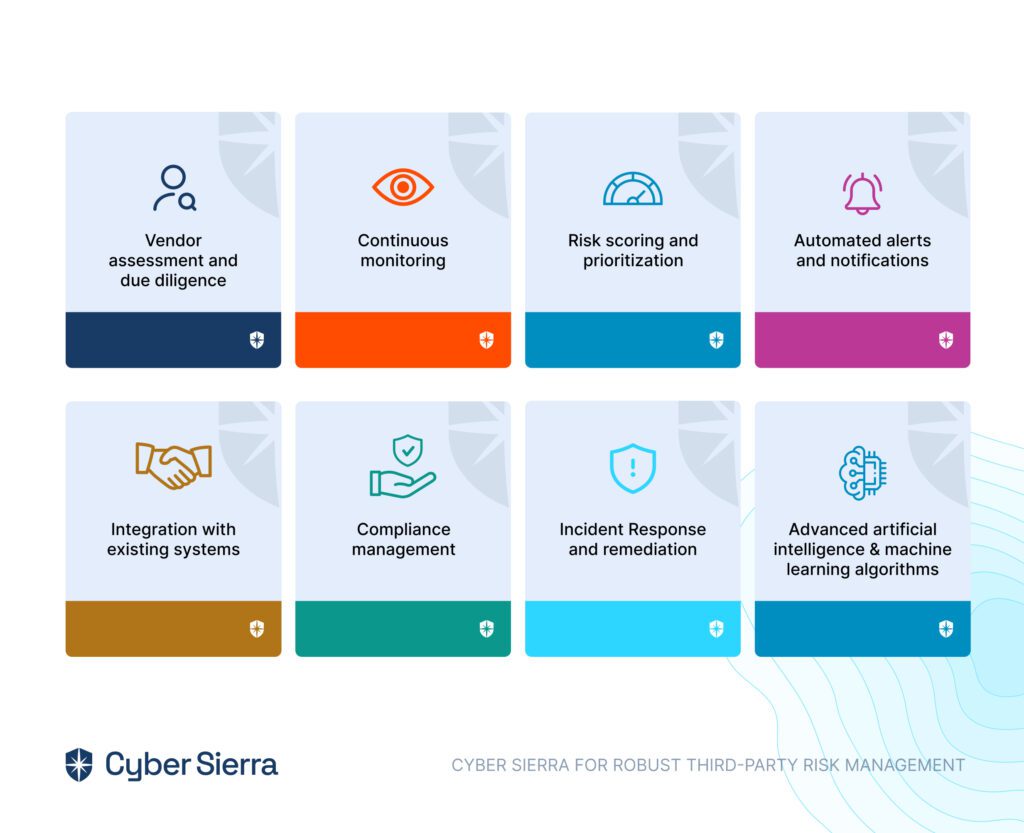

Here are Cyber Sierra’s unique features that make it ideal for your organization’s third-party risk management needs:
- Vendor assessment and due diligence: Cyber Sierra offers advanced features for assessing and evaluating third-party vendors before engaging in business relationships. Better yet, it automates the process of collecting information about vendors' security practices, certifications, and compliance with industry standards.
- Continuous monitoring: TPRM involves continuously monitoring third-party vendors for any changes in their security posture or potential risks. Cyber Sierra provides functionalities for real-time monitoring of vendors' networks, systems, and activities to detect any anomalies or security breaches promptly.
- Risk scoring and prioritization: An effective third-party risk management program requires prioritizing vendors based on the level of risk they pose to the organization. Cyber Sierra offers capabilities for assigning risk scores to vendors based on factors such as the sensitivity of the data they handle, their security controls, and any past security incidents.
- Automated alerts and notifications: In TPRM, timely detection of security incidents or vulnerabilities is crucial. Cyber Sierra includes automated alerting and notification features to promptly notify users about any security issues or changes in vendors' risk profiles.
- Integration with existing systems: Seamless integration with existing security systems and tools is essential for TPRM effectiveness. Cyber Sierra offers integrations with other cybersecurity solutions such as threat intelligence platforms, security information and event management (SIEM) systems, and vulnerability management tools.
- Compliance management: TPRM often involves ensuring that third-party vendors comply with relevant regulatory requirements and industry standards. Cyber Sierra assists in managing compliance assessments, audits, and documentation to ensure that vendors meet the necessary security and privacy standards.
- Incident Response and remediation: In the event of a security incident involving a third-party vendor, the software provides capabilities for facilitating incident response activities and coordinating remediation efforts to mitigate the impact of the incident on the organization.
- Advanced artificial intelligence and machine learning algorithms: CS' AI-powered platform monitors security risks and offers suggestions on mitigating them.
The platform also helps in getting cyber insurance in case the risk needs to be transferred.
FAQs
Let’s answer a few questions asked by users of TPRM tools
What is the best third-party risk management software?
There's no single "best" TPRM tool, as the ideal choice depends on your specific needs and budget. When choosing software for your organization, look for one that offers comprehensive features for risk identification, assessment, and mitigation tailored to various industries and compliance standards.
What is third-party risk management?
Third-party risk management involves identifying, assessing, and mitigating risks associated with outsourcing tasks, services, or operations to external parties, such as vendors, suppliers, or contractors. It aims to safeguard an organization from potential harm or disruptions caused by the actions or shortcomings of third parties, ensuring business continuity and resilience.
Who is responsible for third-party risk management?
Responsibility for third-party risk management typically falls on various stakeholders within an organization, including executives, risk management professionals, compliance officers, and procurement teams. Each contributing expertise and oversight to effectively mitigate risks associated with external partners.



