The Proactive CISO’s Guide to CCoP 2.0 Regulations




Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
‘A lot more is now required.’
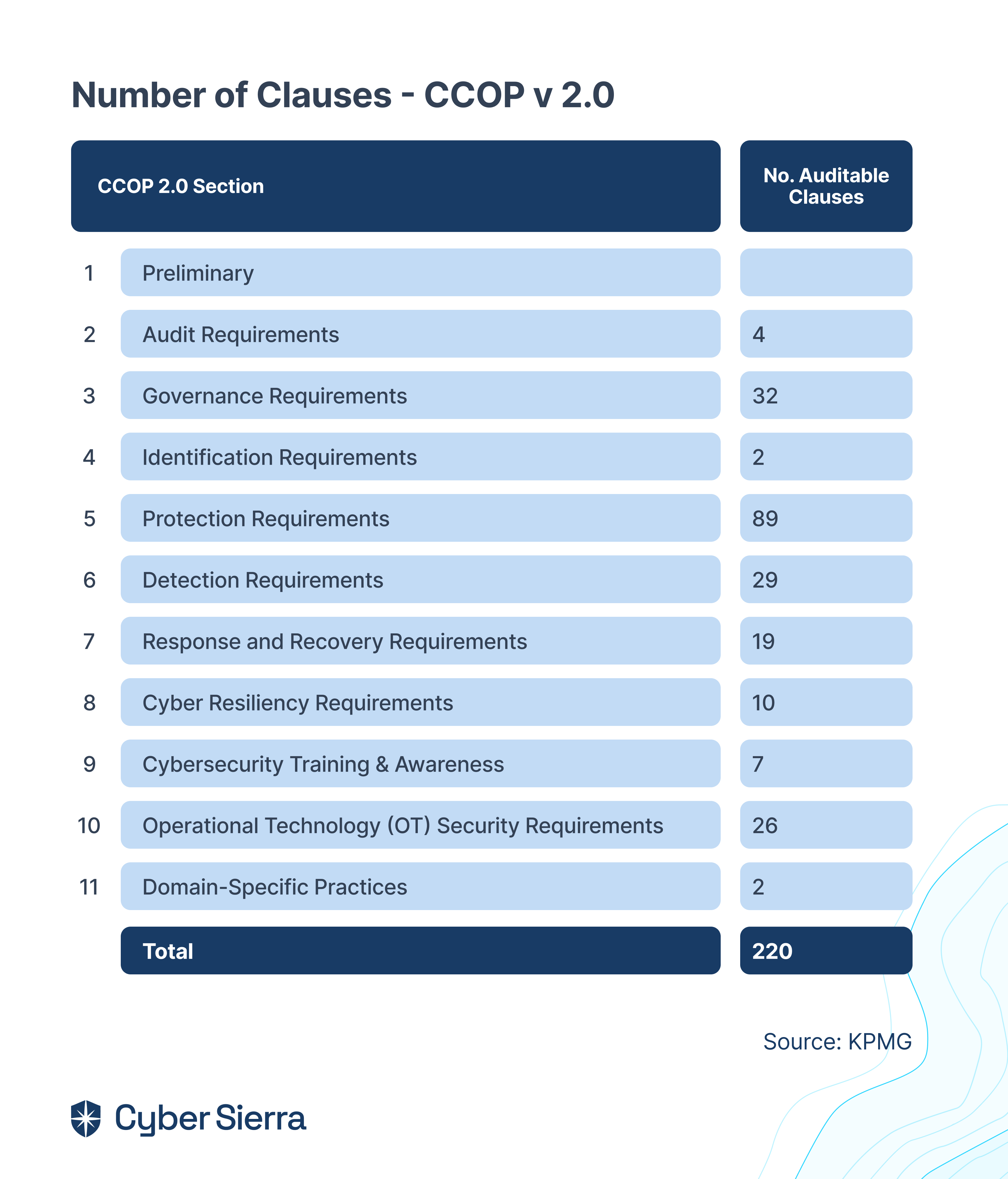
That’s how I’ll summarize the huge lift in requirements in version two of the Cybersecurity Code of Practice (CCoP 2.0) Regulations. Per KPMG’s assessments, to become compliant, clauses companies must now adhere to jumped 116%, from 102 to a whopping 220:


This increase leaves you, a CISO or company executive charged with leading your team’s compliance efforts, with much more to do. It’s also crucial to note that, after CCoP 2.0 went into effect in July 2022, Singapore’s CyberSecurity Act (CSA) allowed a grace period of just twelve (12) months. The implication of this is that you need some urgency to avoid the hammer.
But, first, why so many new security clauses?
Lionel Seaw succinctly answered that:


Who Is CCoP 2.0 Compliance For?
There are two ways to answer this one.
The first are the organizations in sectors explicitly spelled out by the CSA. Per their official statement, Critical Information Infrastructure (CII) of companies in designated sectors responsible for essential services in Singapore must comply.
They include:
- Government
- Energy
- Healthcare
- Banking and Finance
- Transport (Land, Maritime, and Aviation)
- Media
- Infocomm, and
- Security and Energy Services
Your company may not be in these sectors.
Regardless, if your organization works with businesses in those sectors, you also need to comply. This is because of the second way the CSA states who CCoP 2.0 is applicable to:


Based on this, I’d do two things with this guide:
- Explore key CCoP 2.0 compliance requirements, and
- Show how Cyber Sierra’s smart enterprise compliance management suite helps to automate their implementations.
Before that:
Key CCoP 2.0 Requirements for CII
As earlier mentioned, across its eleven (11) requirement sections, there are about 220 auditable security clauses in CCoP 2.0.
As shown below:

Protection, Governance, Detection, Operational Technology (OT) Security, Response & Recovery, Cyber Resilience, and Cybersecurity Training & Awareness. These seven requirements all have over half a dozen security clauses. At face value, it may seem like the key requirements for complying with CCoP 2.0 CII revolve around these.
While they do to some extent, the bulk of what’s needed in the clauses under these requirements comes down to creating policy documents. Companies can work with compliance consultants to get these done. Where you want to channel your efforts is on ensuring that your CII systems are actually secured from cyber threats.
Achieving that goes beyond creating policy documents. You need a way to automate processes for governing, detecting, and training employees on ways to remediate cyber threats and vulnerabilities.
And that’s where Cyber Sierra helps.
Our platform enables you to coordinate your entire team and manage multiple compliance audits from one place. For instance, Speedoc, a Singaporean-based tech company, relies on Cyber Sierra for this:


How to Automate CCoP 2.0 Compliance Audit
The CSA applied five design principles in drafting CCoP 2.0. These principles are important because they provide the guardrails to successfully prepare for CCoP 2.0 compliance audit.
They are illustrated here:


Cumulatively, these principles give organizations the flexibility to focus on CCoP 2.0 requirements they deem necessary. With that in mind, the steps below summarizes how Cyber Sierra automates vital requirements involved in crushing a CCoP compliance audit.
Governance


This requirement essentially mandates having qualified employees assigned to the right roles and working collaboratively to:
- Provide cybersecurity leadership and oversight
- Handle cybersecurity change management
- Create policies, standards, and guidelines
- Perform periodic internal compliance audits
- Select necessary cloud security requirements
- Implement vendor risk management framework.
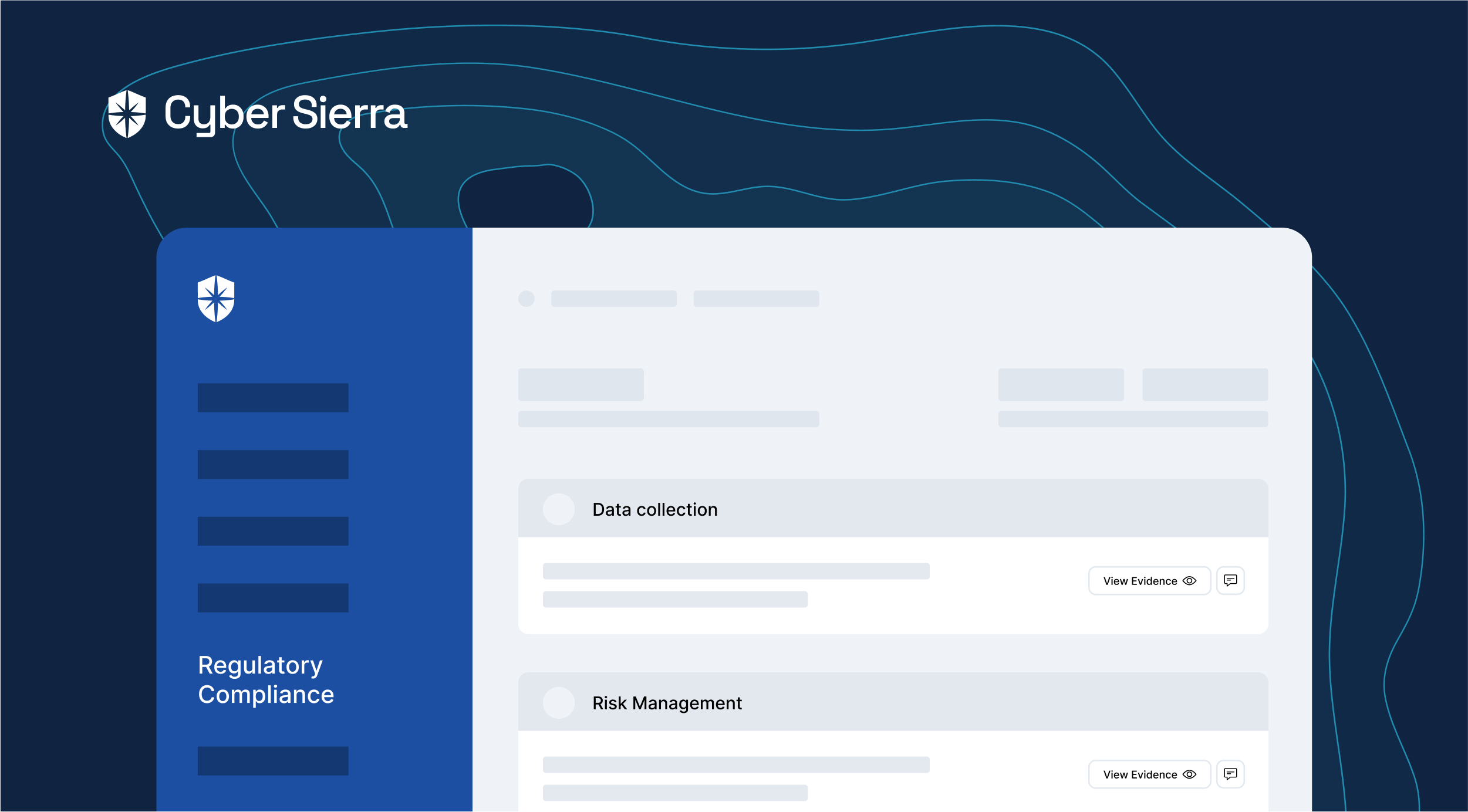
Cyber Sierra makes doing all these easier. With our platform, you can add all employees on your Governance team, assign responsibilities, and work collaboratively from one place:
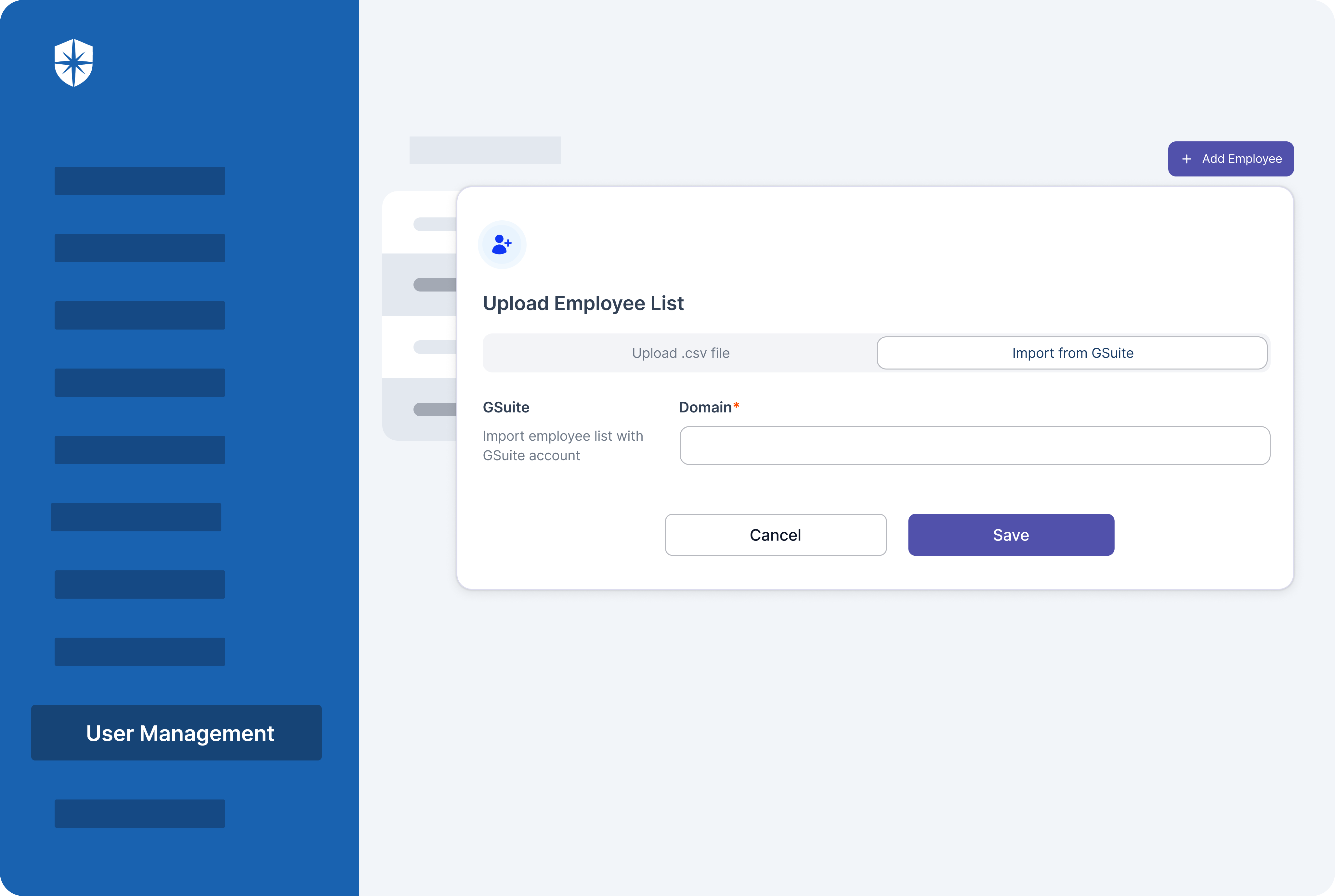

Protection


Protection is the CCoP 2.0 requirement with the most number of security clauses. Clauses under this requirement primarily force organizations to protect their CII from unauthorized access.
Twelve crucial clauses covered includes:
- Privilege access management
- Access control
- Patch management
- System hardening
- Database security
- Penetration testing
- Network segmentation
- Windows domain controller
- Cryptography key management
- Network segmentation
- Application security, and
- Vulnerability management.
To meet CCoP 2.0’s Protection requirements, having a solid process for detecting threats is an important step. This is because in Clause 5.14.2, the Code states:


To achieve this, you need to automate detecting where threats and vulnerabilities are coming and get insights for remediating them.
And that’s the next vital requirement.
Detection


This requirement can be summarized to one thing: Your organization should have technology for enacting cybersecurity controls that helps your security team streamline processes involved in:
- Cyber threat intelligence
- Continuous controls’ monitoring
- Cybersecurity log management, and
- Threat hunting.
Cyber Sierra’s Risk Dashboard automates all that:
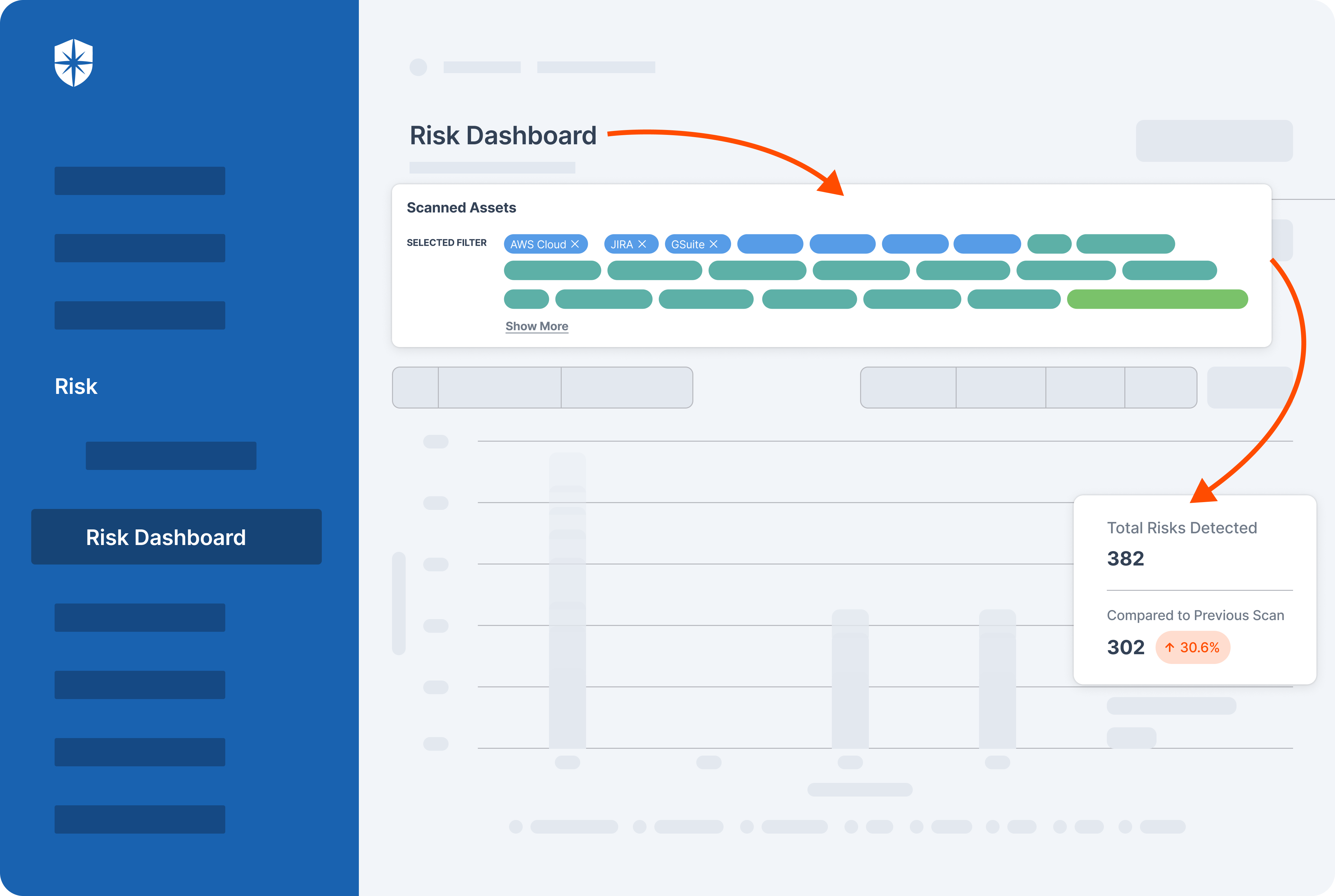

As shown, this feature enables your team to filter and scan Critical Information Infrastructure assets continuously. Besides detecting and identifying cyber threats and vulnerabilities that could affect your CII from this, you also get a dashboard with real-time reports needed for compliance audits. On the same dashboard, your team can manage and get factual insights for resolving vulnerabilities.
Cybersecurity Training & Awareness


Clauses under this requirement can be split into two parts:
- Cybersecurity awareness programme, and
- Cybersecurity training and skills.
Both may sound like the same thing, but they are not. One is about keeping employees aware of existing and emerging cybersecurity attack types. The other is concerned with equipping them with the skills needed to counter threats and effect cybersecurity responsibilities.
To comply with both, in 9.1.3, the CCoP 2.0 mandates that:


Cyber Sierra helps you automate this. Our Employee Awareness suite gives you a single pane to:
- Launch and manage employee awareness and training programs
- Monitor and nudge employees to complete programs, so everyone is always ready for CCoP 2.0 compliance audits:
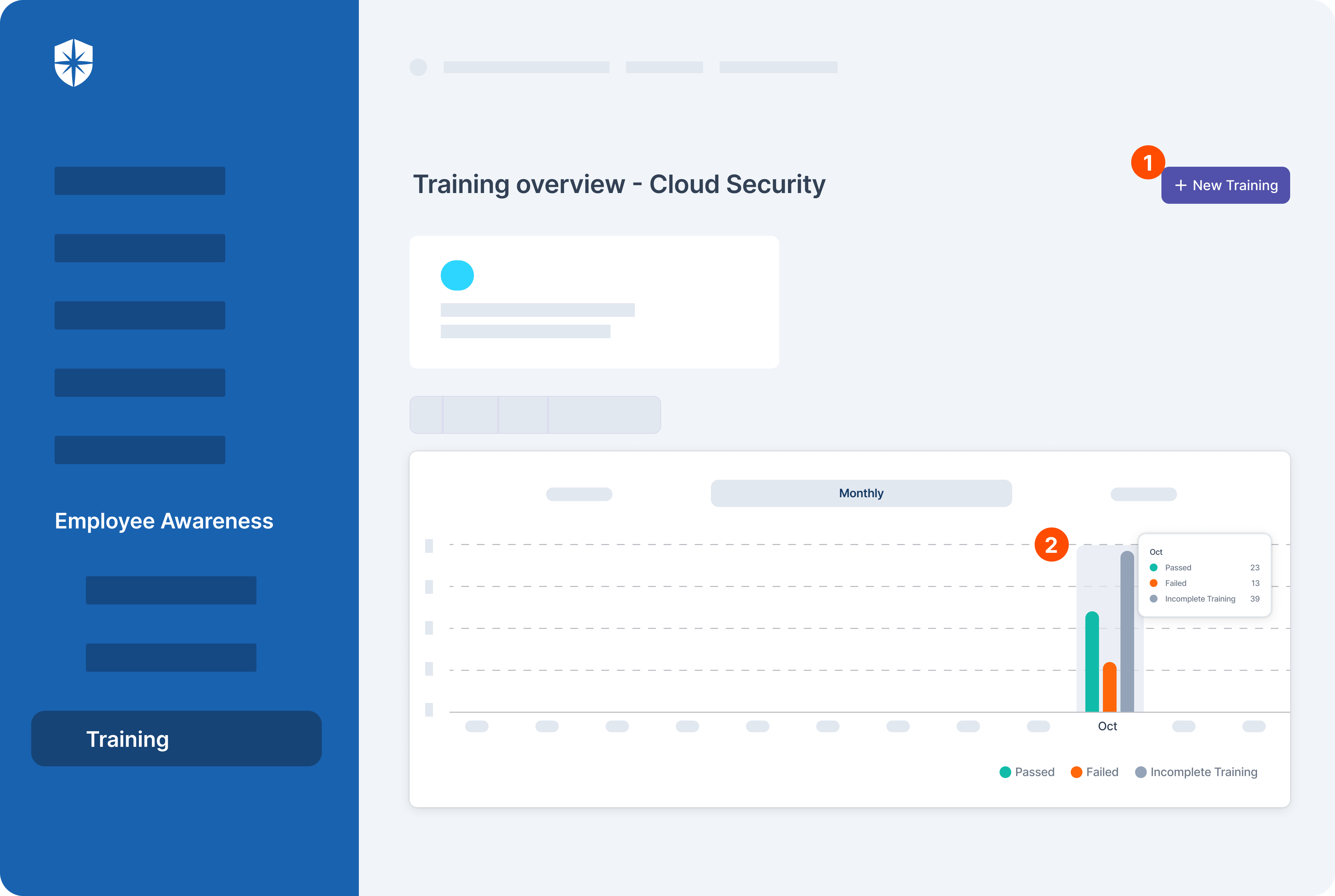

Staying Compliant with CCoP 2.0 Regulations
Achieving CCoP 2.0 compliance is flexible.
As the guiding principles used in creating its draft revealed, organizations are free to choose and only comply with CII requirements that are applicable to them. But once those initial requirements have been chosen and their corresponding security controls defined, staying compliant can’t be treated flexibly.
The CSA mandates organizations to implement a continuous cycle of security assessments to enable swift responses to cybersecurity incidents. This was hammered in clause 13.21 of their official documentation of responses to feedback on CCoP 2.0 compliance:


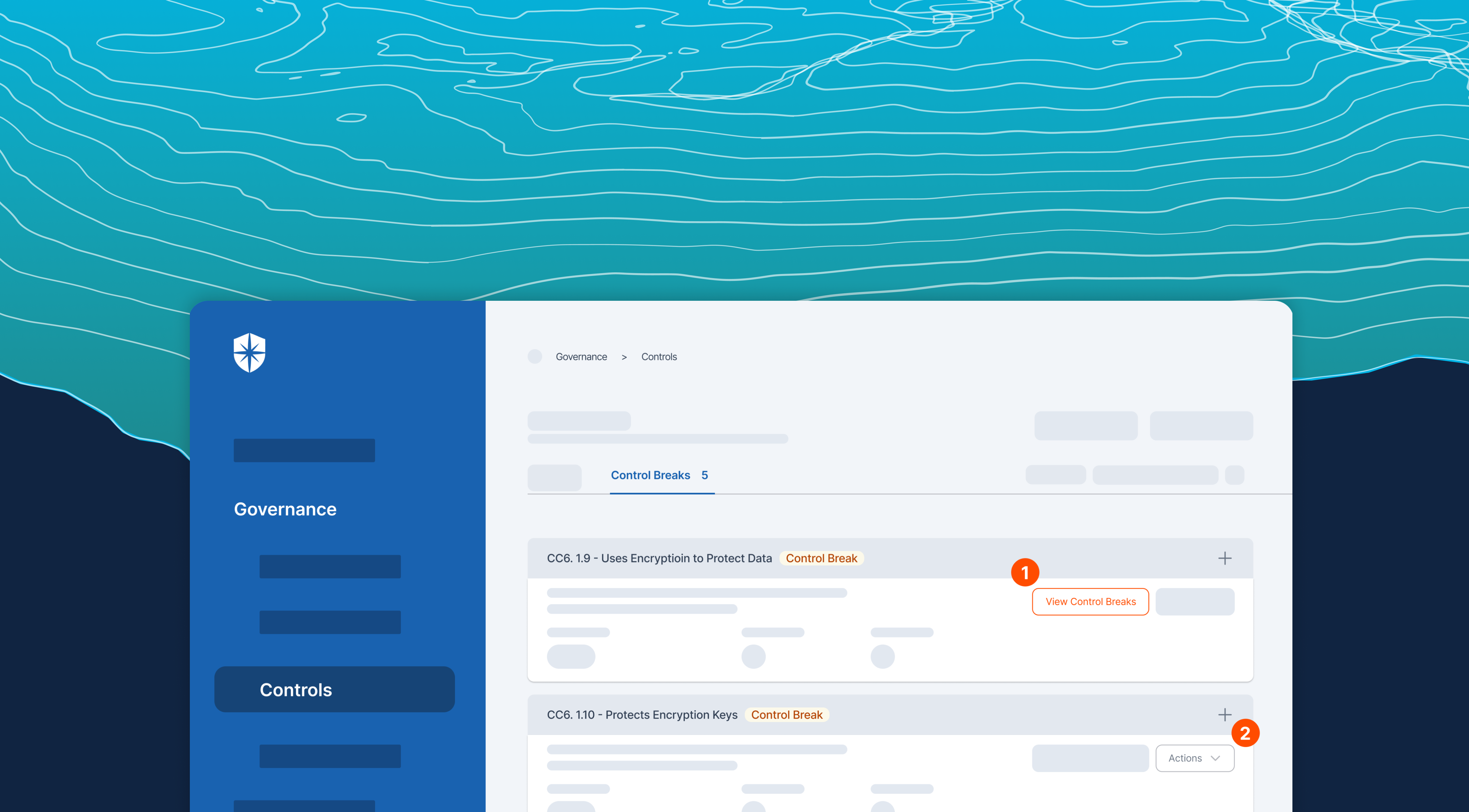
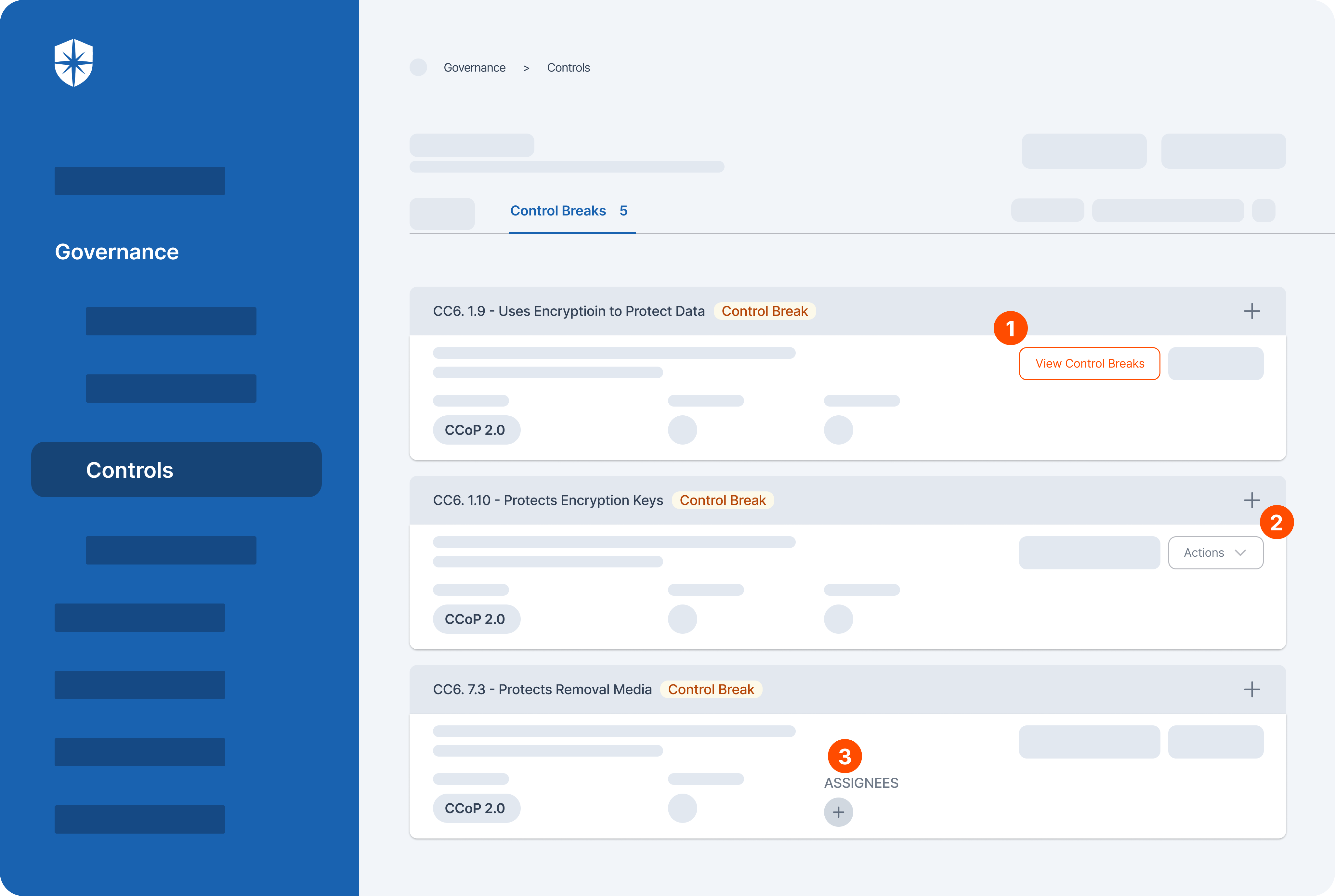
In other words, you should monitor the cybersecurity controls defined in your CCoP 2.0 compliance continuously to stay compliant. Cyber Sierra’s Governance suite enables that.
Organizations leverage it to:
- Monitor CCoP 2.0 compliance control breaks continuously
- Get practical remediation insights
- Assign and remediate risks with teammates collaboratively.
Here’s a peek:




A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.