Busy Tech Executives’ ISO 27001 Compliance Checklist





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
Ron’s startup started expanding globally, going upmarket to enterprise three months ago. In that time, they encountered 63 security questionnaires, but all slowed or blocked the sales process.
Sounds familiar?
Well, you can’t blame prospects fixated on security compliance to win their business. No one wants to suffer data breach costs from working with a company not taking information security (infosec) seriously:


This leaves tech executives (like Ron) with two options:
- Spend weeks filling out prospects’ security questionnaires every time (and still risk losing deals due to inadequate infosec), or
- Get a globally-recognized compliance certificate to ease security questionnaires (and facilitate the sales process).
The latter is where ISO 27001 compliance comes in. But before our checklist to help you ease the process, knowing the mandatory requirements is crucial.
Mandatory ISO 27001 Requirements
The International Standards Organization (ISO) is behind the ISO 27001 compliance. They updated the certification requirements in 2022, highlighting mandatory documentation such as:
- Internal Audit Report
- Risk Assessment Report
- Statement of Applicability
- Information Security Policy
- Information Security Management (ISMS) Scope
Across these compulsory requirements, many security controls must be in place to pass an auditor’s review. But implementing those controls mostly starts with real-time insight into a company’s cybersecurity posture.
This means you’ll need to:
- Navigate the many controls in ISO 27001
- Have a checklist for implementing each, and
- Incorporate a way to automate most processes involved.
This checklist guide will explore all three. So download our ISO 27001 compliance checklist for reference as you follow along:
Navigating the Many Controls in ISO 27001
Although down from 114, the ISO 27001 compliance updated in 2022 still has a whopping 93 security controls across four (4) categories:
- People controls (8)
- Physical controls (14)
- Technological controls (34)
- Organizational controls (37):
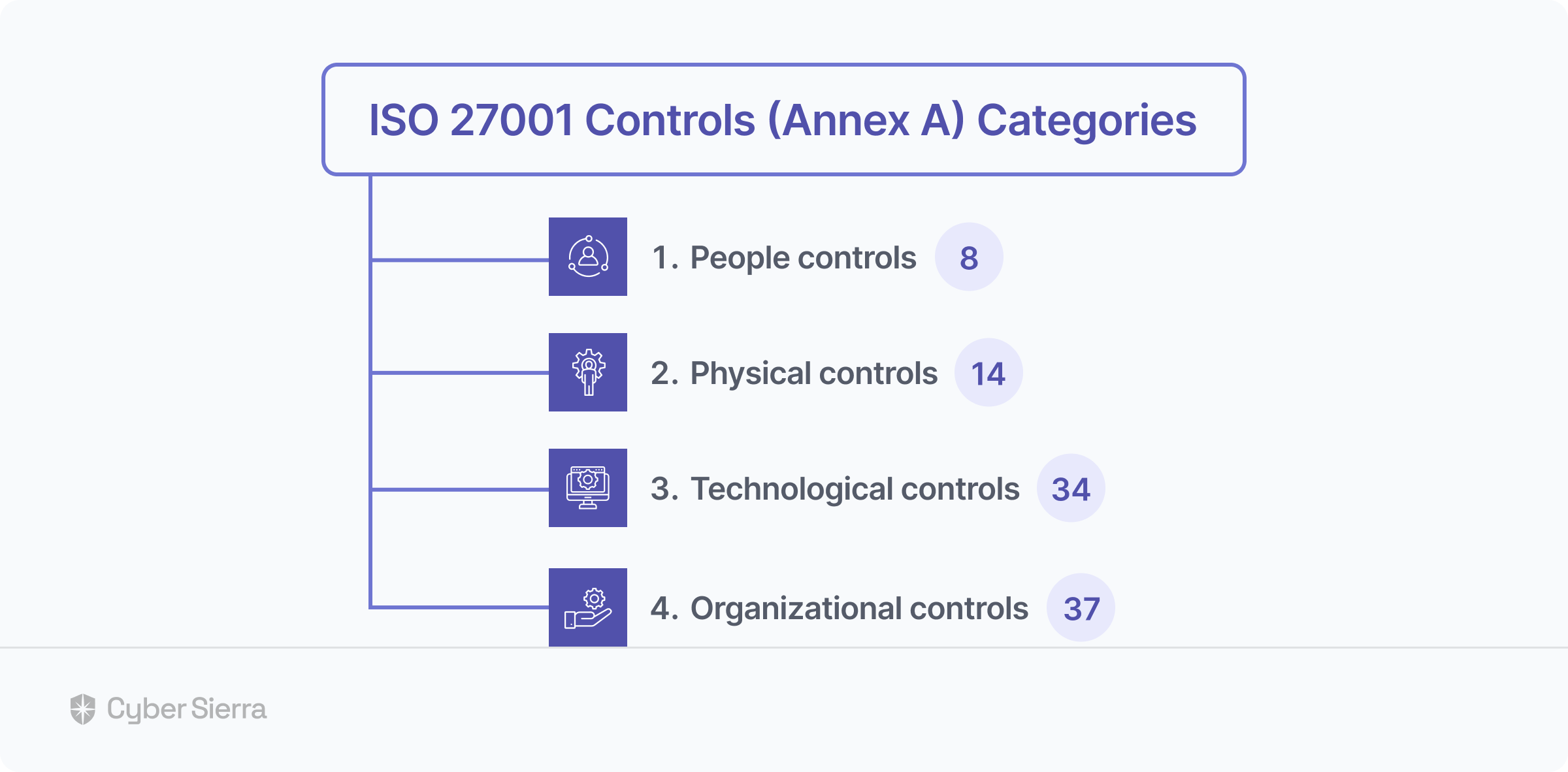

Not all controls are mandatory. Called Annex A, companies are free to implement those relevant to their business.
However, you need sufficient controls to demonstrate how you establish, implement, maintain, and continually improve your company’s information security management system (ISMS).
So knowing what controls to choose is crucial.
And tracking implementation across teams needs more than a checklist, but a centralized platform that can automate most ISO 27001 compliance documentation processes.
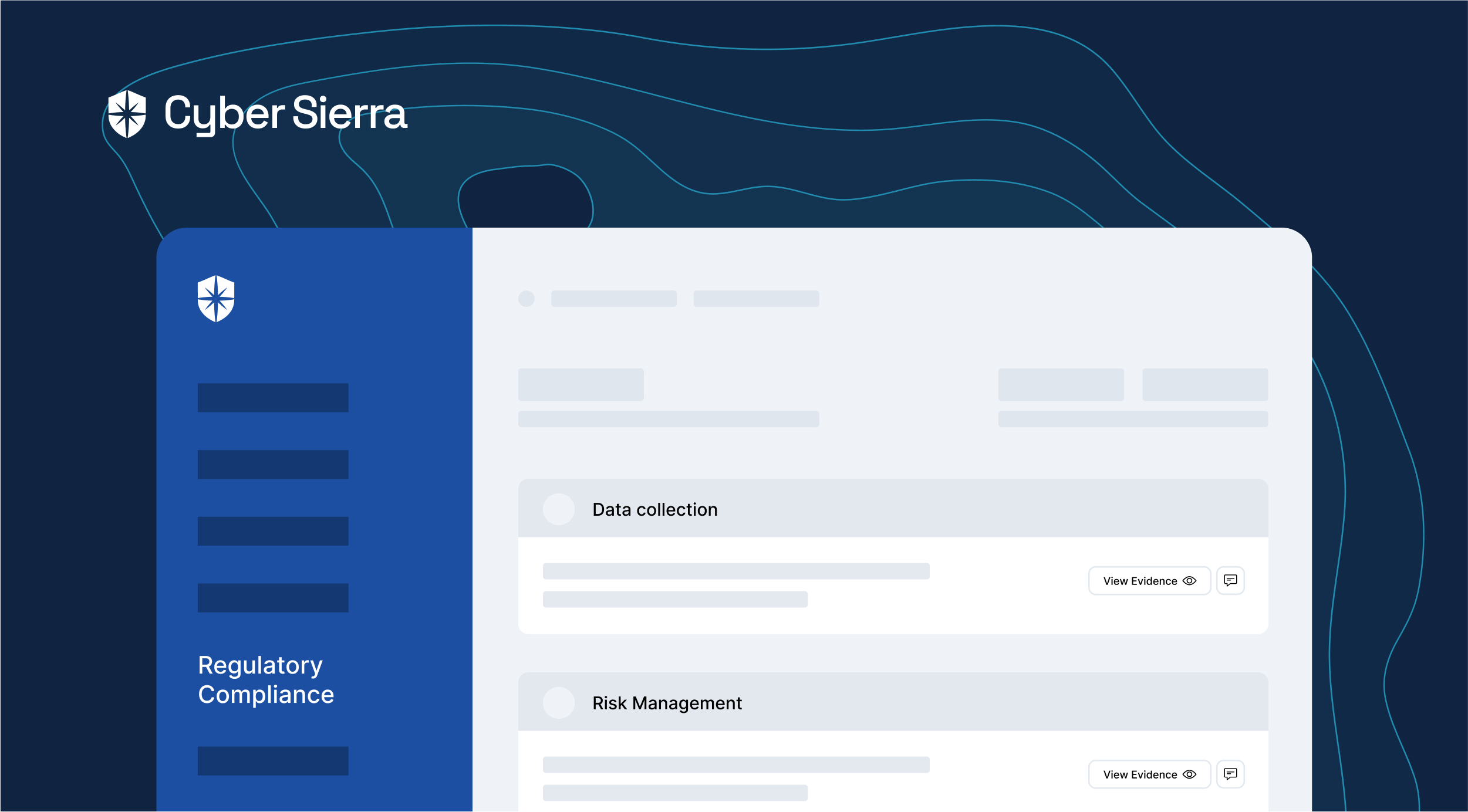
That’s where Cyber Sierra comes in.
Our interoperable cybersecurity platform has the mandatory ISO 27001 policies built into it. Also, across teams, you can assign, track, and automate implementation from one place:





Implement the right controls and automate ISO 27001 Compliance from one place.


Checklist to Implement ISO 27001 Compliance Standards
Many CTOs, CISOs, and tech executives leverage Cyber Sierra to achieve ISO 27001 compliance in record time. They achieve this by streamlining the excessive paperwork required, automating the implementation of controls, and managing everything from one place.
So based on our experience, we’ve created this 7-step ISO 27001 compliance certification checklist guide for your reference.
1. Scope an ISO 27001 Project Plan
ISO 27001 certification is a team effort.
As such, you’d need contributions from relevant team members across your organization. We’ve also found from experience that things move way faster when teammates prioritize the process.
So to create the needed sense of priority, scope a project plan specific to preparing for (and becoming) ISO 27001 compliant.
It should outline:
- Why your startup is pursuing ISO 27001 compliance.
- How it will bolster your company’s security posture.
- Who on your team will be doing what within deadlines.
In addition to these, define the scope of your Information Security Management (ISMS). Like a house depends on its foundation, achieving ISO 27001 compliance depends on this.
And that’s because an ISMS scope succinctly documents the information your startup wants to protect and exclude. The ISMS scope of a software company may include a:
- List of departments/organizational units
- List of processes and services they cover
- List of physical assets/locations
- List of exclusions not in scope.
To give you an idea, here’s a section of GitLab’s:


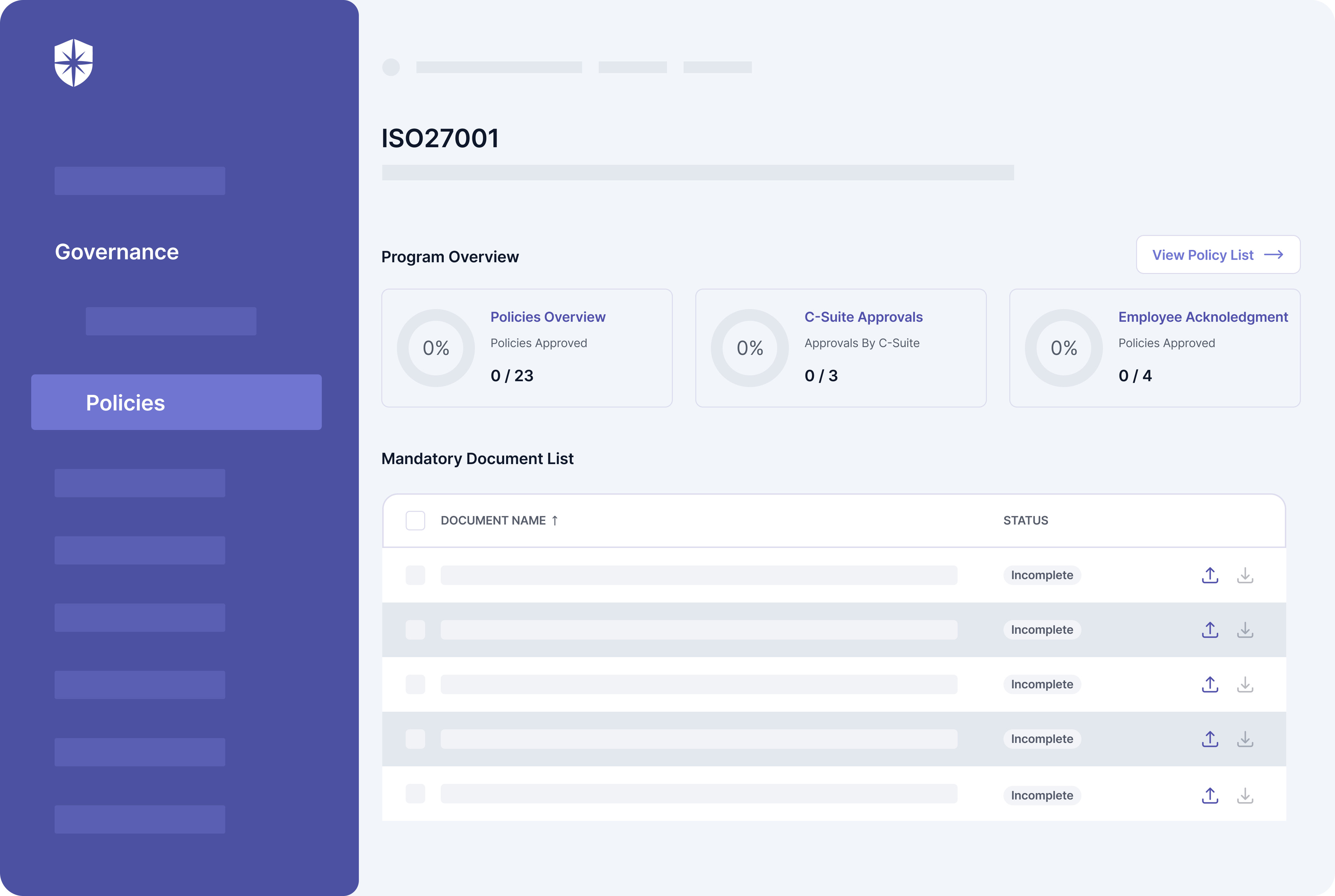
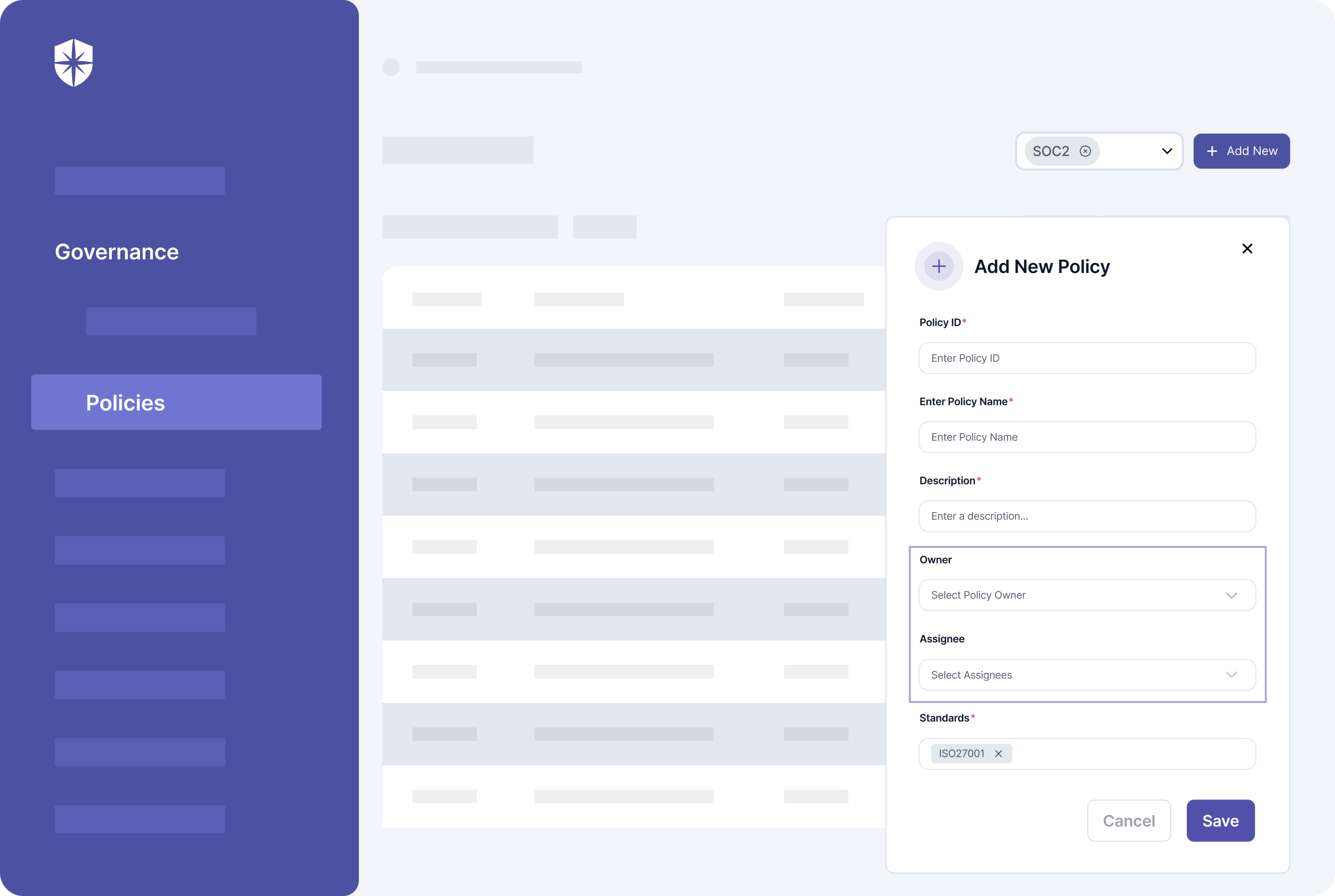
2. Create ISMS Policies
Your ISMS scope determines what ISO 27001 policies need to be created. But there are mandatory ISMS policies such as:
- Incident Management Policy
- Acceptable Use Policy
- Access Control Policy
- Assets Management Policy
- Backup Management Policy
- Business Continuity Policy
- Change Management Policy
- Cloud Services Security Policy
- And 15 others.
Documenting these policies and implementing their corresponding controls takes heavy paperwork. To help automate the process, Cyber Sierra comes prebuilt with these mandatory policies.
And you can even assign them to relevant teammates, track status, and implementation progress in one pane:
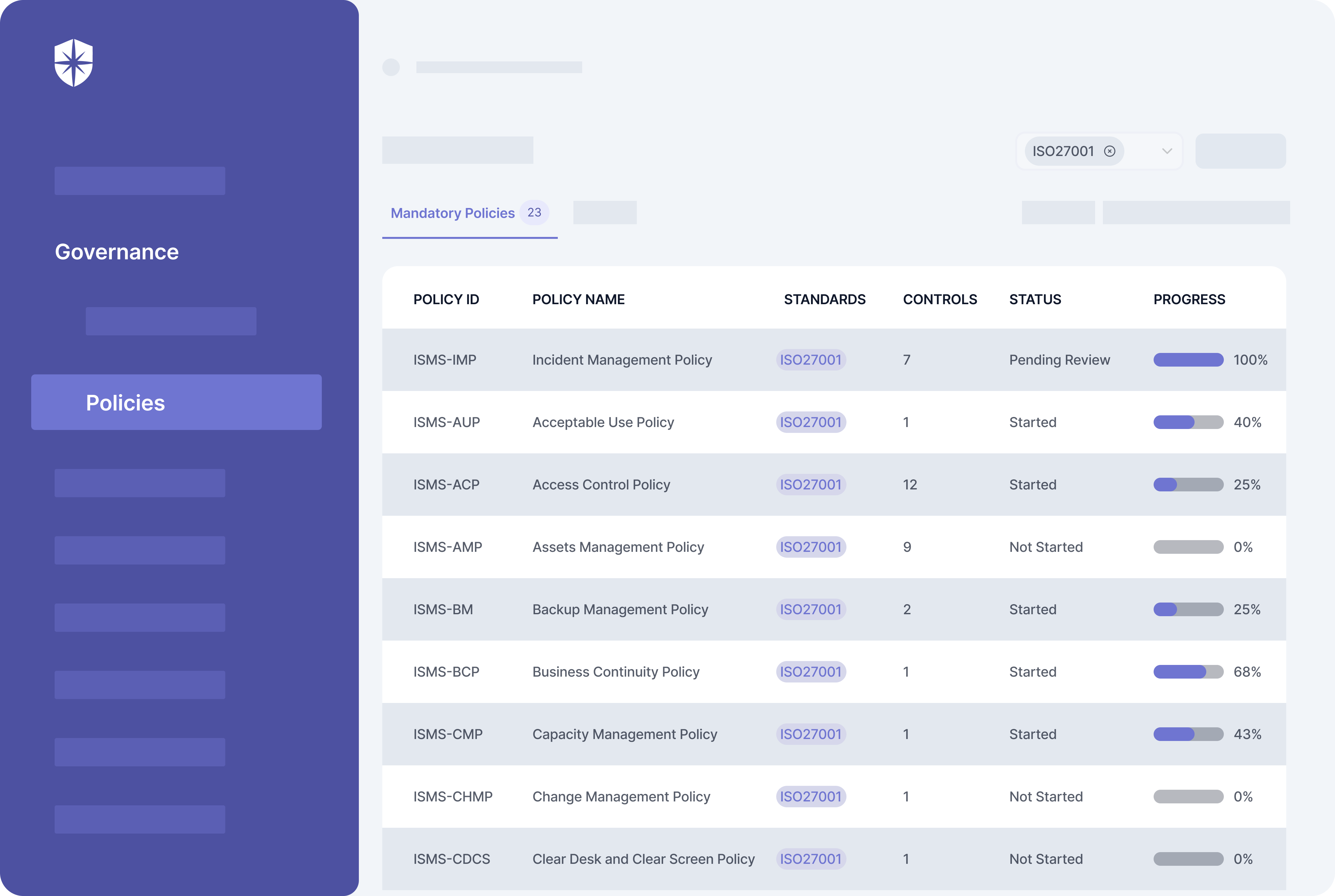

It doesn’t end there.
You can also create policies unique to your ISMS scope, upload corresponding documentation, and assign them to teammates:
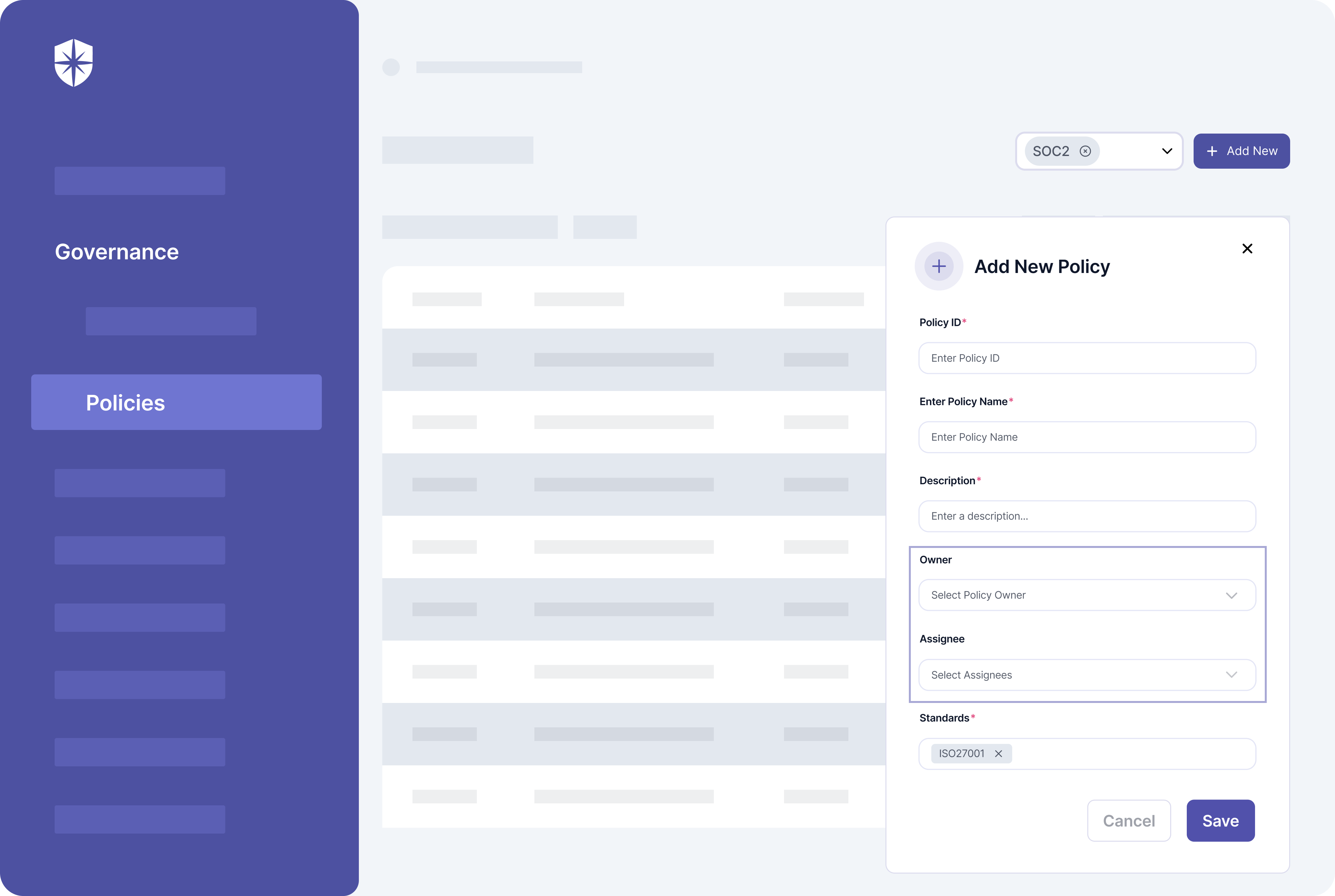

3. Conduct Risk Assessments
This step has two objectives:
- To detect data security risks across your company’s systems, networks, and cloud assets.
- To evaluate identified risks based on their potential impact on the confidentiality, integrity, and availability of data accessed by your company.
Passing the ISO 27001 audit review and becoming certified depends on how well your company manages cybersecurity threats. So the goal of this assessment is to develop a risk register for managing… risks.
And technology can simplify things here. For instance, with Cyber Sierra, connect your tech stack prone to cybersecurity risks, and it’ll:
- Automatically scan your cloud assets
- Detect risks and vulnerabilities in real-time
- Assess and score the impact of those risks, and
- Enable you to assign remediation tasks to teammates.
All that from one Risk Register pane:
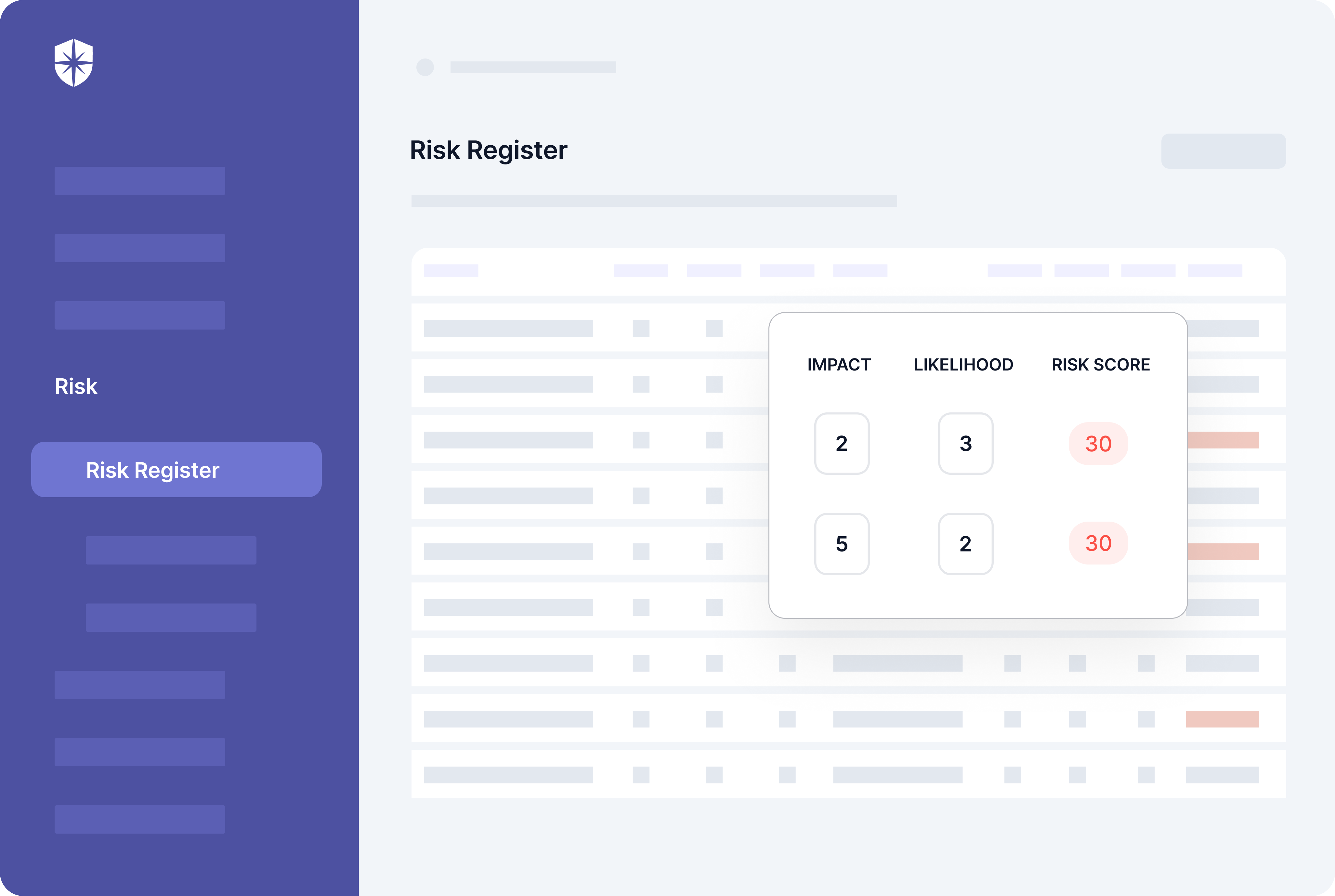

4. Define Statement of Applicability
A Statement of Applicability (SoA) is required for ISO 27001. As the name suggests, it is a document stating the Annex A security controls that are applicable —or aren’t applicable— to an organization.
So in defining one, you should:
- List the security controls your company wants to manage and mitigate against based on your risk assessment.
- Explain why you chose those security controls for your information security management system (ISMS).
- State the status of your chosen controls (i.e., have they been fully implemented? If no, why not?).
- Briefly explain excluded controls and why they aren’t applicable to your organization.
As the points above show, the SoA document summarizes your ISMS policies and risk assessment. So a good place to start is revisiting steps 1-3 of this checklist. And this is crucial because your SoA is what ISO 27001 auditors rely on during audit reviews.
5. Implement Policies & Controls
This step is where you begin to implement the security controls for your chosen ISMS policies. And you do this by providing appropriate documentation of each control. It’s typically the most difficult part of the project, requiring loads of implementation evidence to be uploaded ahead of an audit review.
Take the mandatory Cloud Services Security (CSS) policy.
You’ll need to implement:
- A document describing this policy per your ISMS, and
- Twelve (12) documents as evidence to show you’ve implemented its corresponding 12 controls.
Cyber Sierra streamlines this cumbersome process. For instance, you can quickly edit a pre-built CSS policy document to suit your ISMS scope and upload evidence of controls, all from one place:
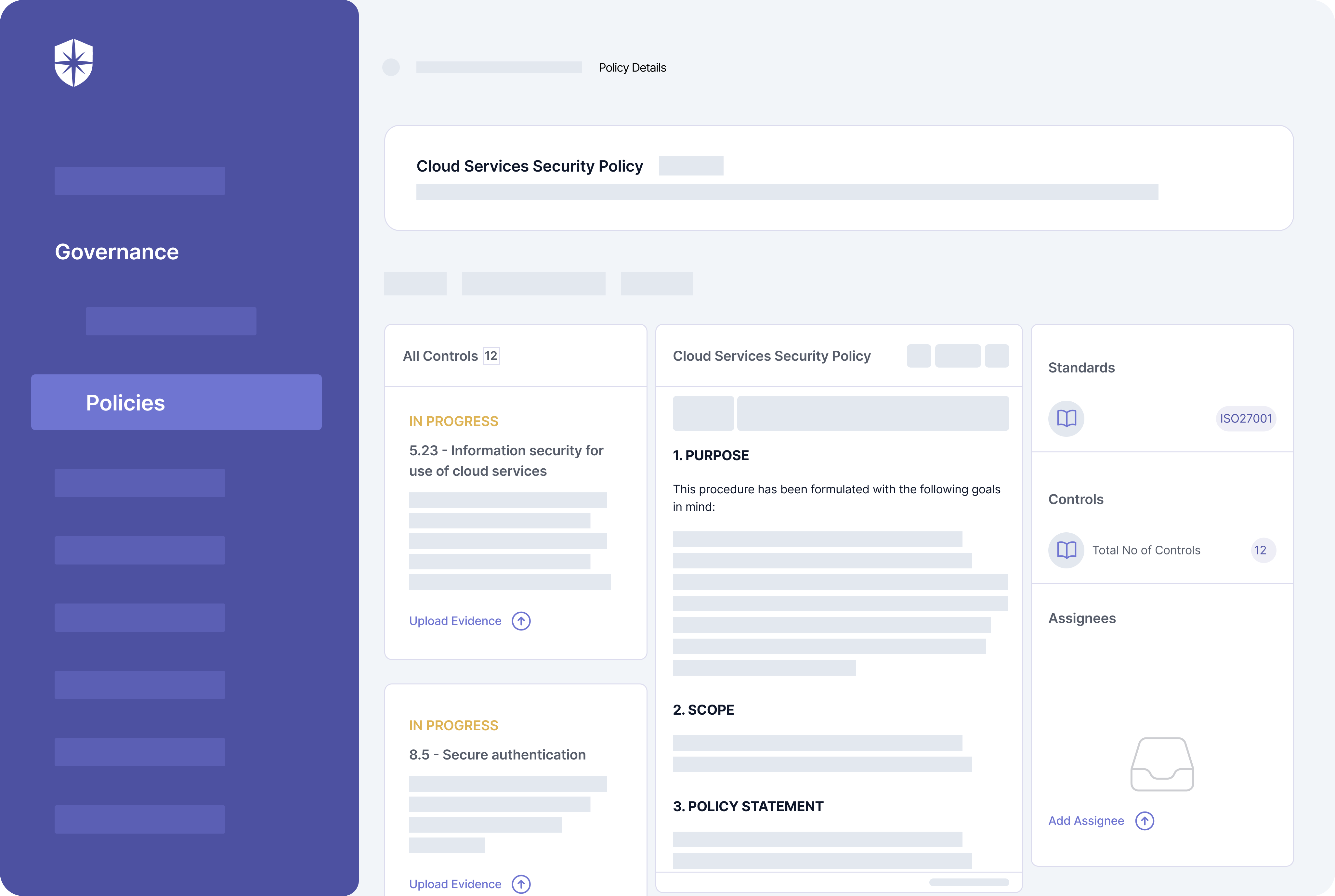

6. Establish Employee Security Awareness & Training
Ongoing security awareness and training for employees is indispensable for becoming (and remaining) ISO 27001 compliant.
And that’s for three reasons:
- To train relevant employees on how to implement your ISO 27001 policies and security controls to maintain your ISMS.
- To make them aware of security risks your company is currently facing and the processes for mitigating them.
- To continually educate them about emerging security threats and the best practices for defending against them.
These ongoing training programs should cut across cloud security, common cybersecurity threats, anti-phishing, and others. And you can launch and manage them all with Cyber Sierra:
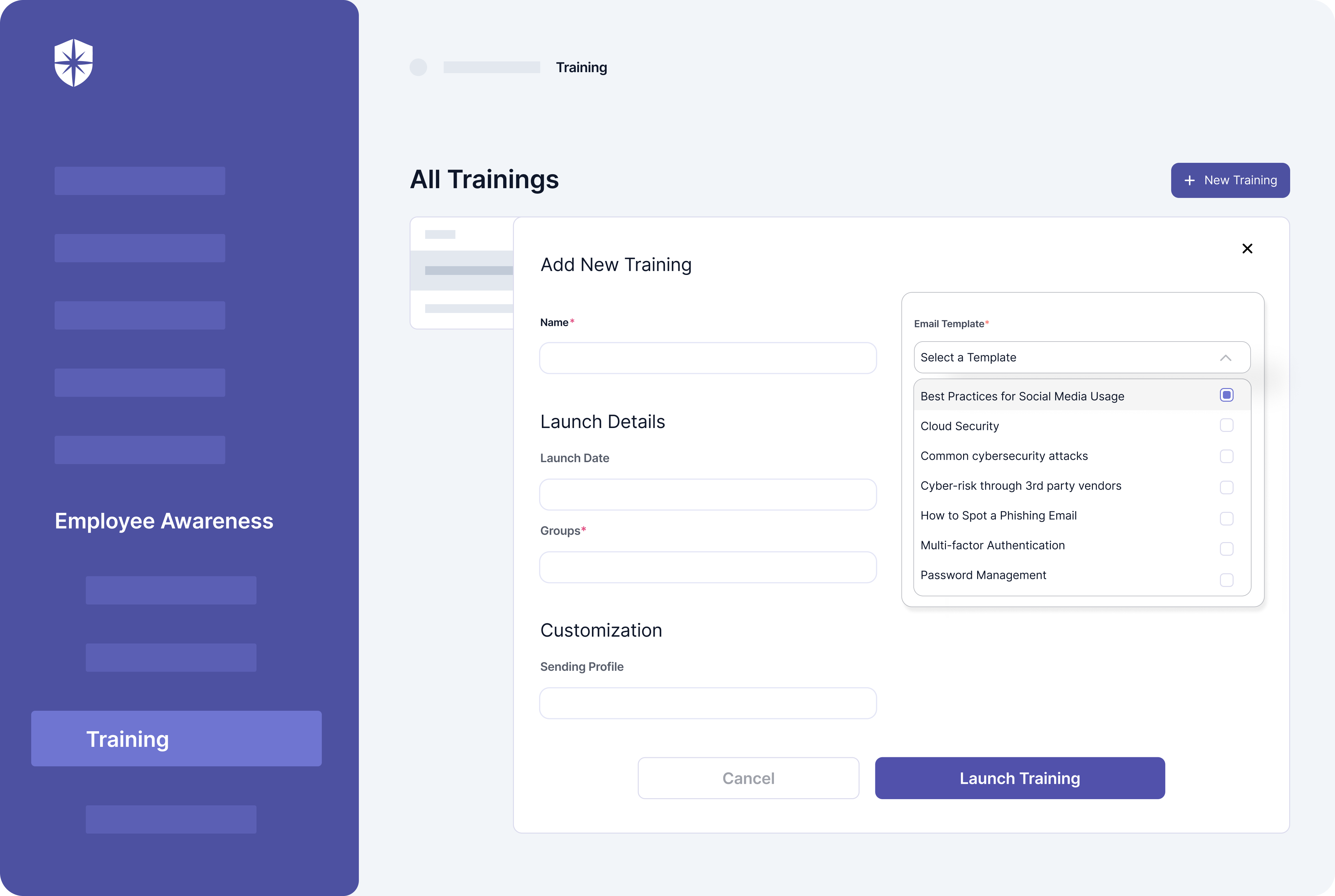

7. Perform Internal & External Audits
Without an external audit spearheaded by an accredited ISO 27001 compliance auditor, an organization can’t be certified.
But before that, a series of internal audits are necessary. These prepare your company for the external one, and hiring consultants to review all implemented ISO 27001 documentation is also advised.
Typically, your team should:
- Double review internal policies and procedures’ documentation
- Sample all uploaded evidence as part of the internal review to demonstrate correct implementation of policies and controls
- Analyze findings from all document reviews to ensure they meet your ISMS scope and ISO 27001 certification requirements
- Implement improvements, as needed, based on audit findings ahead of the external certification audit review.
After the internal audit comes the external one.
So request an accredited auditor to review your company’s implementation of ISMS policies and security controls against the official ISO 27001 standard. Then proceed to the Certification Audit for a final review of your company’s business processes, policies, and security controls to get certified in ISO 27001 compliance.
8. Implement Continuous Security Controls’ Monitoring
ISO 27001 compliance isn’t a one-time affair.
Certification must be renewed every three years. And to meet requirements when recertification is due, companies must undergo and pass yearly Periodic Surveillance Audits.
The annual surveillance audits follow the same process as the final audit before the initial ISO 27001 certification. It seeks to identify and correct nonconformities in the maintenance of implemented ISMS policies and security controls. And here’s how you ensure that:
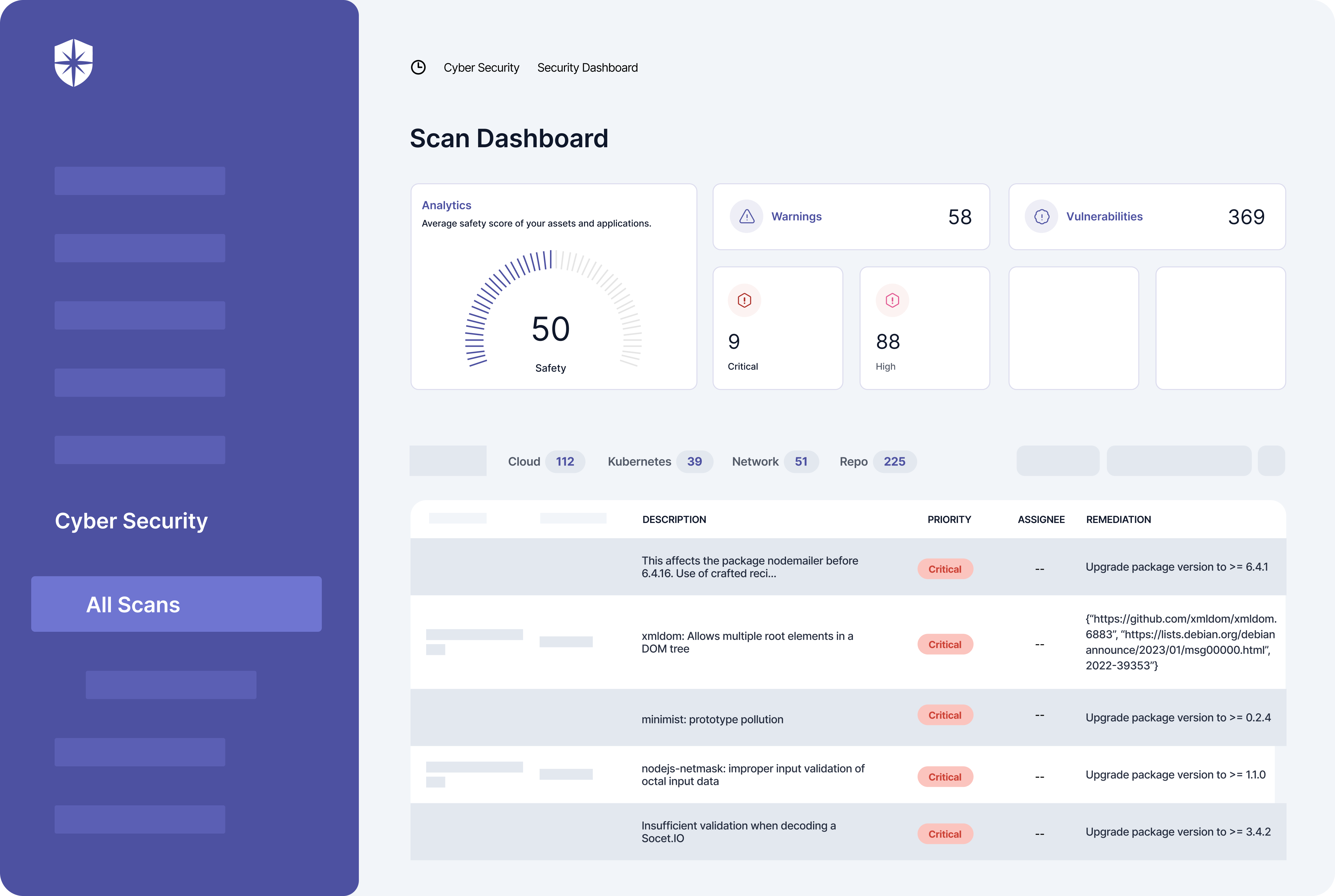
- Continuously scan your cloud assets, repository, Kubernetes, and network environments to identify security risks as they emerge.
- Assign critical risks to relevant team members with tips on how to remediate them to pass periodic surveillance audits and retain your ISO 27001 compliance.
Your team can do both of these with Cyber Sierra:

The Advantage of ISO 27001, Without the Hassle
Imagine you had all the steps in this gruesome ISO 27001 compliance certification checklist in one interoperable cybersecurity platform.
Imagine in one pane, your team could:
- Understand each step of the process
- Manage the completion of each step
- Implement ISMS policies and security controls
- Automate evidence collection to show proof of compliance, correction of non-conformities, if any found during audits.
- Perform risk assessment and assign remediation tasks
- Establish ongoing employees’ security awareness & training
- Go through the various audit reviews required without going back and forth with teammates and auditors over spreadsheets
- Implement continuous monitoring of security controls, manage emerging threats, and mitigate critical ones to stay compliant.
Imagine the benefits of ISO 27001 (i.e., no need to fill security questionnaires or miss competitive deals) without the hassle of the steps above. As shown throughout this checklist guide, Cyber Sierra makes it possible by automating most processes involved in becoming (and remaining) ISO 27001 compliant.
Why not talk to one of our ISO 27001 experts?




Implement the right controls and automate ISO 27001 Compliance from one place.






A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.