PCI DSS Compliance Checklist & Guide for Automating the Process





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
Staying compliant to the Payments Card Industry Data Security Standard (PCI DSS) can be overwhelming. To give you a clue, about 60.5% of PCI DSS requirements were unmet by organizations when they suffered a data breach, per SecurityMetrics’ 2021 study:
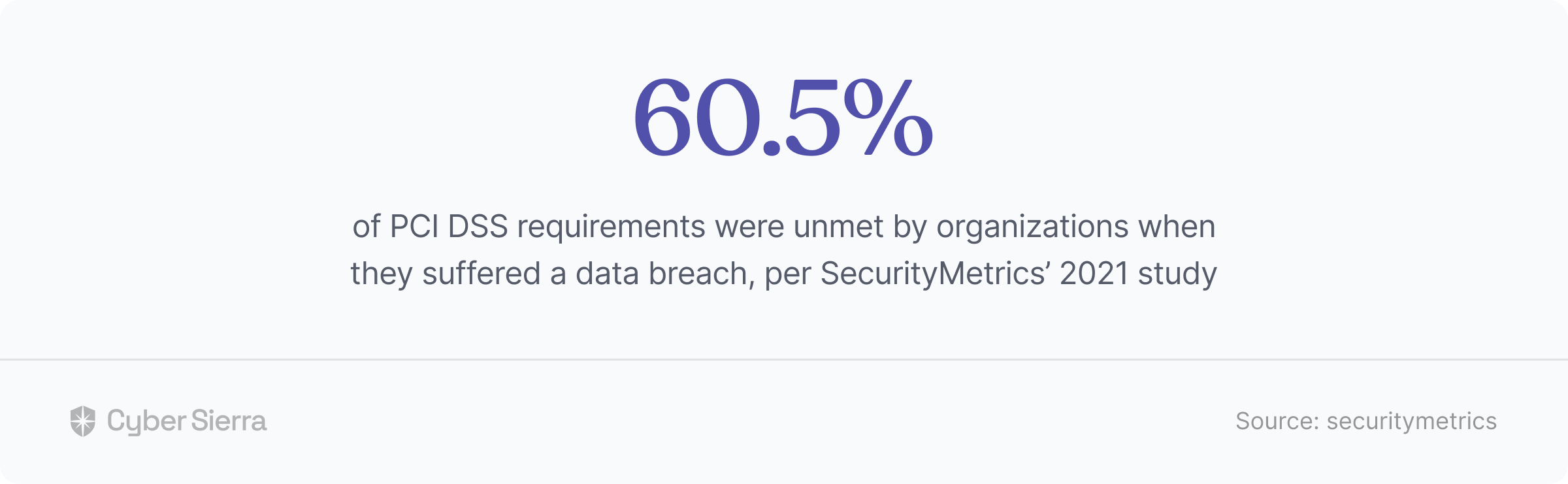

This data confirms three things:
- As the dynamics of processing, storing, and transmitting customers’ payments and credit card info evolve, the potential for data breaches also increases.
- Meeting PCI DSS requirements is difficult.
- You should automate the process of implementing controls to stay compliant, even after meeting initial requirements.
So when seeking a checklist, consider one that covers automating the implementation of controls post PCI DSS compliance. For this, CTOs and IT executives must start by…
Knowing the PCI DSS Controls & Requirements
PCI DSS has over 300+ security controls. So much so that learning all can take days, as observed by a Security Policy Lead at Stripe:


To help, the PCI Council organized these controls into six objectives, along with their corresponding compulsory requirements.
As illustrated below:
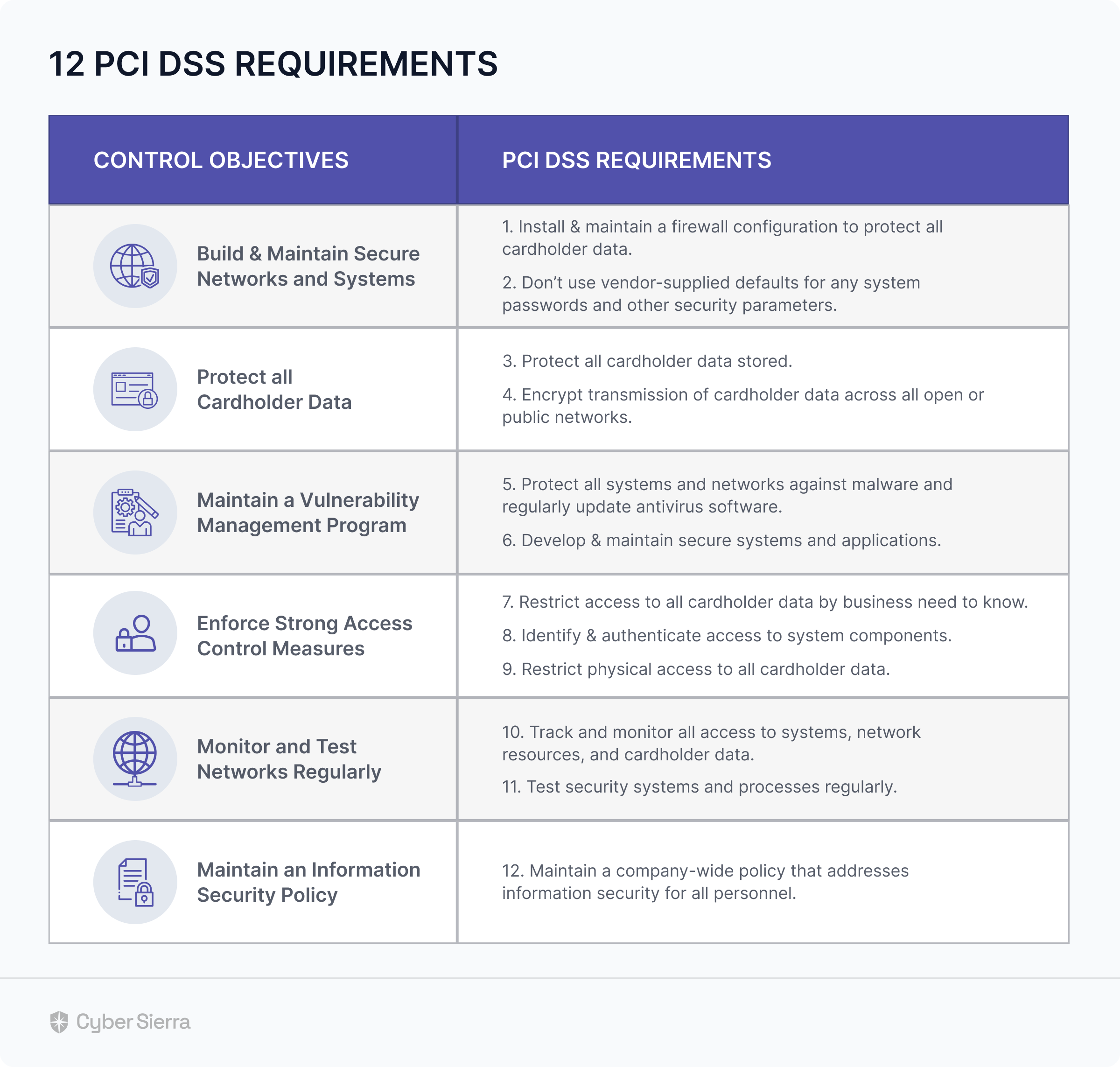

With the mandatory control objectives and their corresponding requirements outlined, to become and stay compliant teams must:
- Adhere to the core PCI DSS requirements per control group
- Automate their implementation to save time & money.
This checklist guide (you can download it below) will help you achieve both. As we go through it, you’ll also see how Cyber Sierra automates their implementation to save you time and money:
The 8-Step PCI DSS Compliance Checklist
The PCI Council’s official reference guide outlined three steps for ongoing adherence and compliance to the PCI DSS. The steps are:
- Assess: Identify all locations of cardholder data by taking inventory of all your IT assets and business processes for payments and card processing. Analyze them to detect vulnerabilities that could expose sensitive cardholder data.
- Repair: Fix identified risks and vulnerabilities, securely remove unneeded cardholder data storage, and implement secure business processes.
- Report: Document assessment and remediation details and submit compliance reports to your acquiring bank(s) and card brands you do business with (or relevant requesting entities):
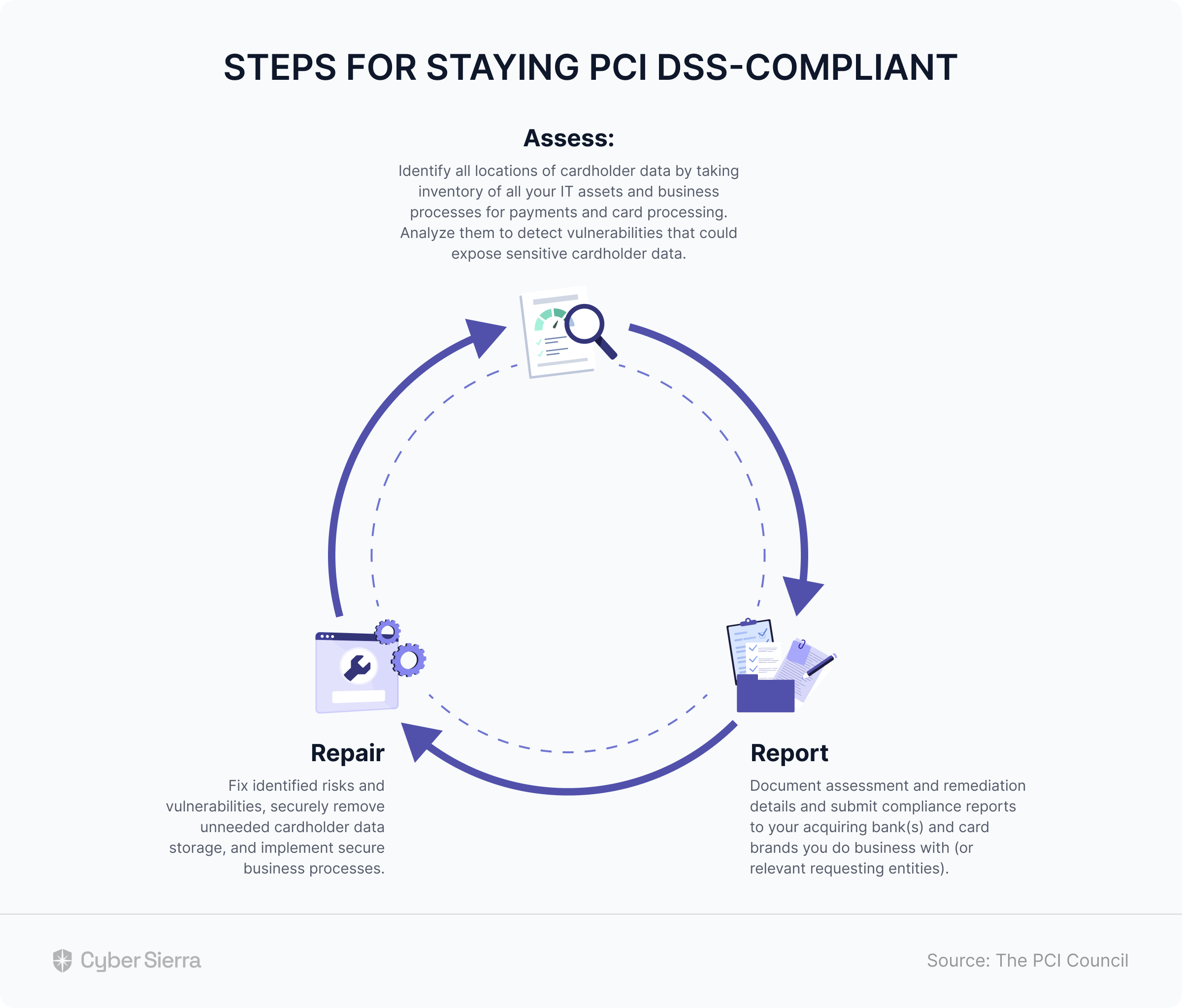

This 8-step checklist is designed to help you adhere to these ongoing requirements, as they are crucial to earning PCI DSS certification.
1. Determine PCI Level
Achieving PCI DSS compliance starts with knowing what PCI level your organization falls under. It could be one of four levels typically ranked based on credit card transactions:


2. Map All Cardholder Data Flows
Three things your team should do here are:
- Detect all customer-facing areas involved in processing payment transactions across your organization. This could include online shopping carts, over-the-phone orders, in-store payment terminals via credit/debit cards, etc.
- Pinpoint the various ways cardholder data is handled across your company’s business units. Importantly, outline where the data is stored and everyone in your organization with access to it.
- Identify internal systems and technologies involved in payments and transactions processing. This should include your cloud assets, network systems, data centers, and others.
These three to-dos above are crucial.
And that’s because it creates a comprehensive map of network systems, connections, and applications interacting with all credit card data across your organization.
3. Perform Internal Security Assessment
Once you’ve mapped all organization-wide network systems interacting with credit card data, assess them to spot vulnerabilities not aligned with the PCI DSS security controls.
You can do this with Cyber Sierra.
Initiate a scan of all technologies and network systems mapped to be interacting with cardholder data. For instance, you scan your Kubernetes, Repository, Networks, and Cloud environments:
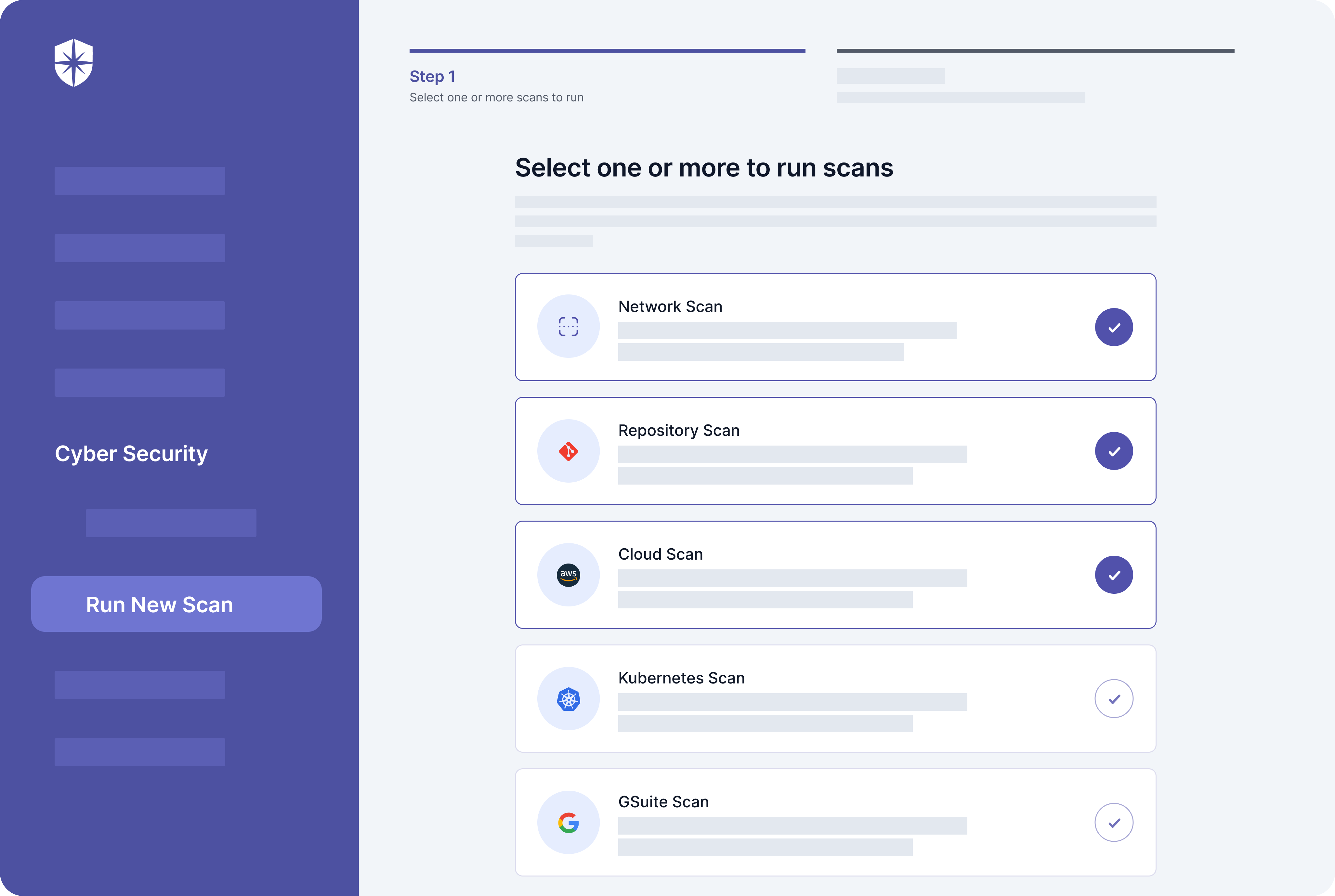

Once you initiate a scan, Cyber Sierra will:
- Continuously monitor all network systems and cloud assets interacting with credit card payment transactions
- Automatically assess and detect critical risks you should prioritize to stay aligned with PCI DSS security controls
- Highlight tips guiding your team to remediate detected risks and vulnerabilities as they emerge.
You can also assign the remediation of these risks as tasks to relevant members of your security team on the same pane:
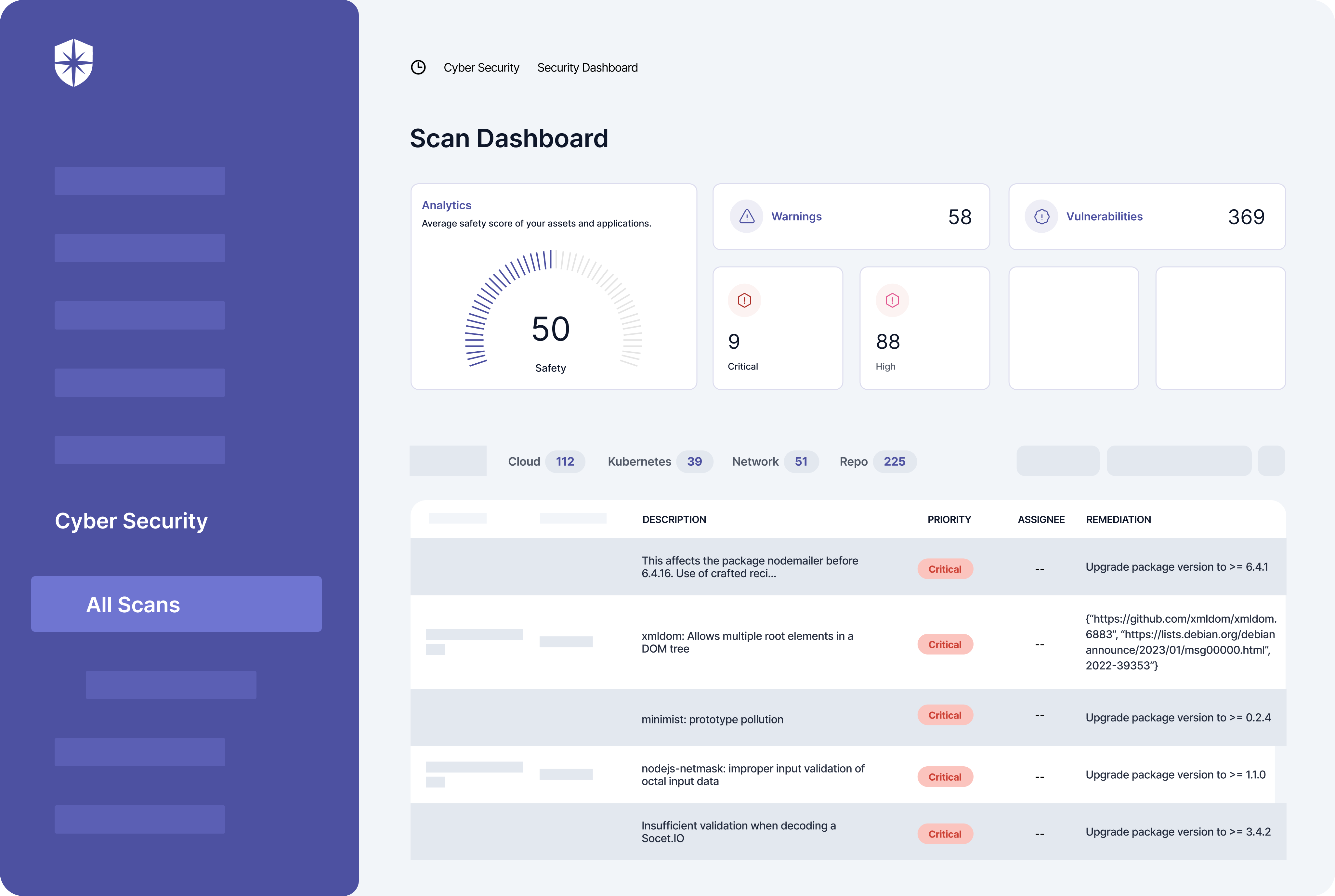

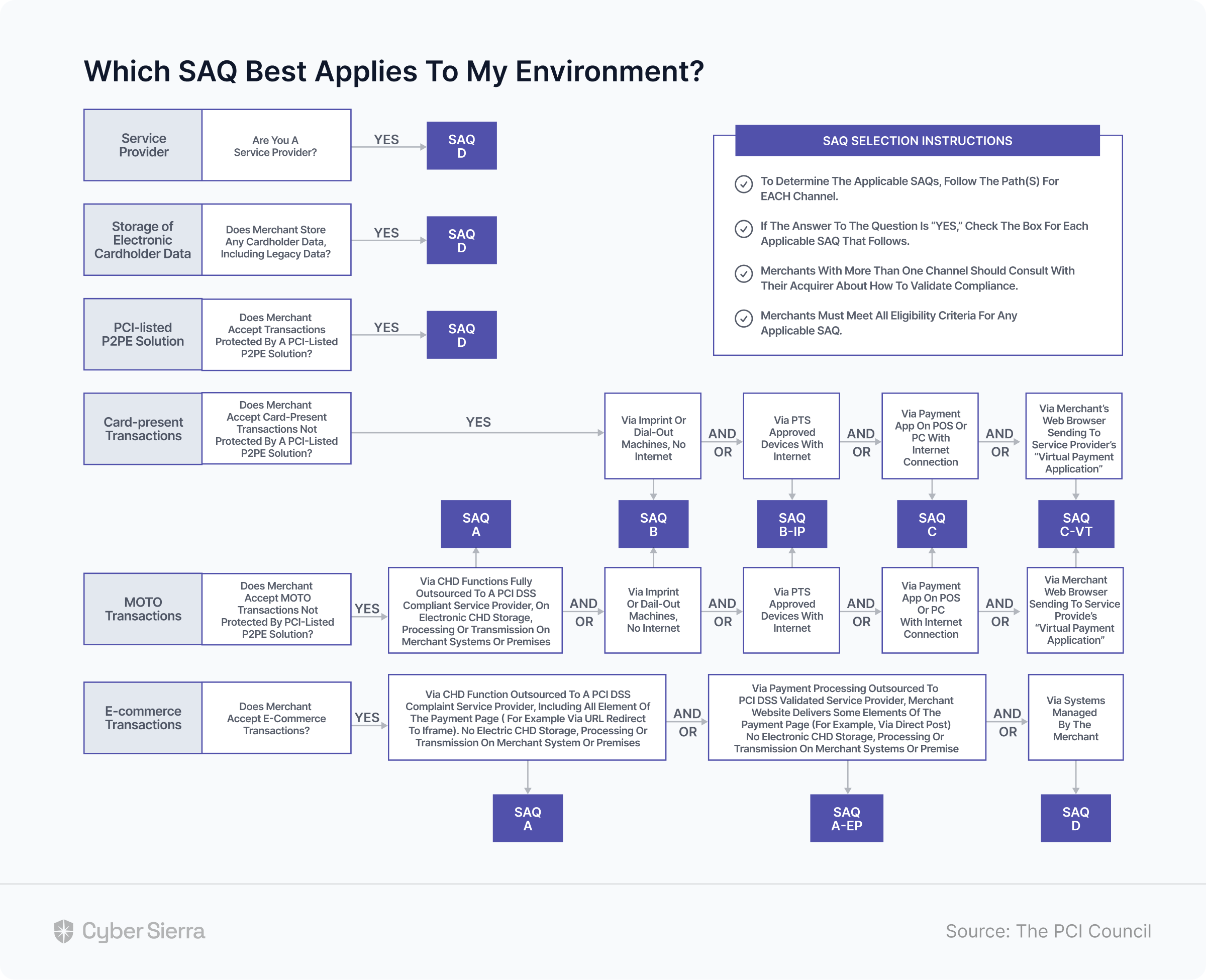
4. Fill Out Self-Assessment Questionnaire (SAQ)
The SAQ records the result of the internal security assessment performed to gauge your company’s compliance with PCI DSS. The particular SAQ to fill out depends on your organization’s PCI Level transaction types relevant to your business environment.
As captured in this chart by the PCI Council:

5. Conduct External Vulnerability Scans
This step prepares you for compliance.
After the internal security assessment performed and self-assessment questionnaire filled out, hire PCI DSS approved scanning vendors (ASVs) to conduct another round of scans. These experts ensure that you’ve met all required PCI DSS standards before proceeding.
Noah Stahl shared why this is crucial:


6. Complete the Attestation of Compliance (AoC)
The Attestation of Compliance (AoC) declares your company’s compliance with PCI DSS. As a mandatory step toward PCI DSS compliance certification, this document must be completed by a Qualified Security Assessor (QSA).
Because it serves as evidence that your organization’s security posture, network systems, and practices can effectively protect against cardholder data threats.
Preview a sample of the document here.
7. Submit Filled Out PCI DSS Documents
Submit filled out forms in the previous steps, including:
- Approved Scanning Vendors (ASVs) report
- Self-Assessment Questionnaire (SAQ), and
- Attestation of Compliance (AoC).
Once submitted, a PCI DSS accredited auditor reviews, vets them, and finalizes the PCI DSS compliance certification process for your company.
But it doesn’t end there.
8. Implement Continuous Monitoring
PCI DSS compliance is no one-time affair.
To understand why, recall this guide’s introduction. I cited data showing that about 60.5% of organizations didn’t meet PCI DSS requirements when they suffered a data breach.
Here’s how you avoid that.
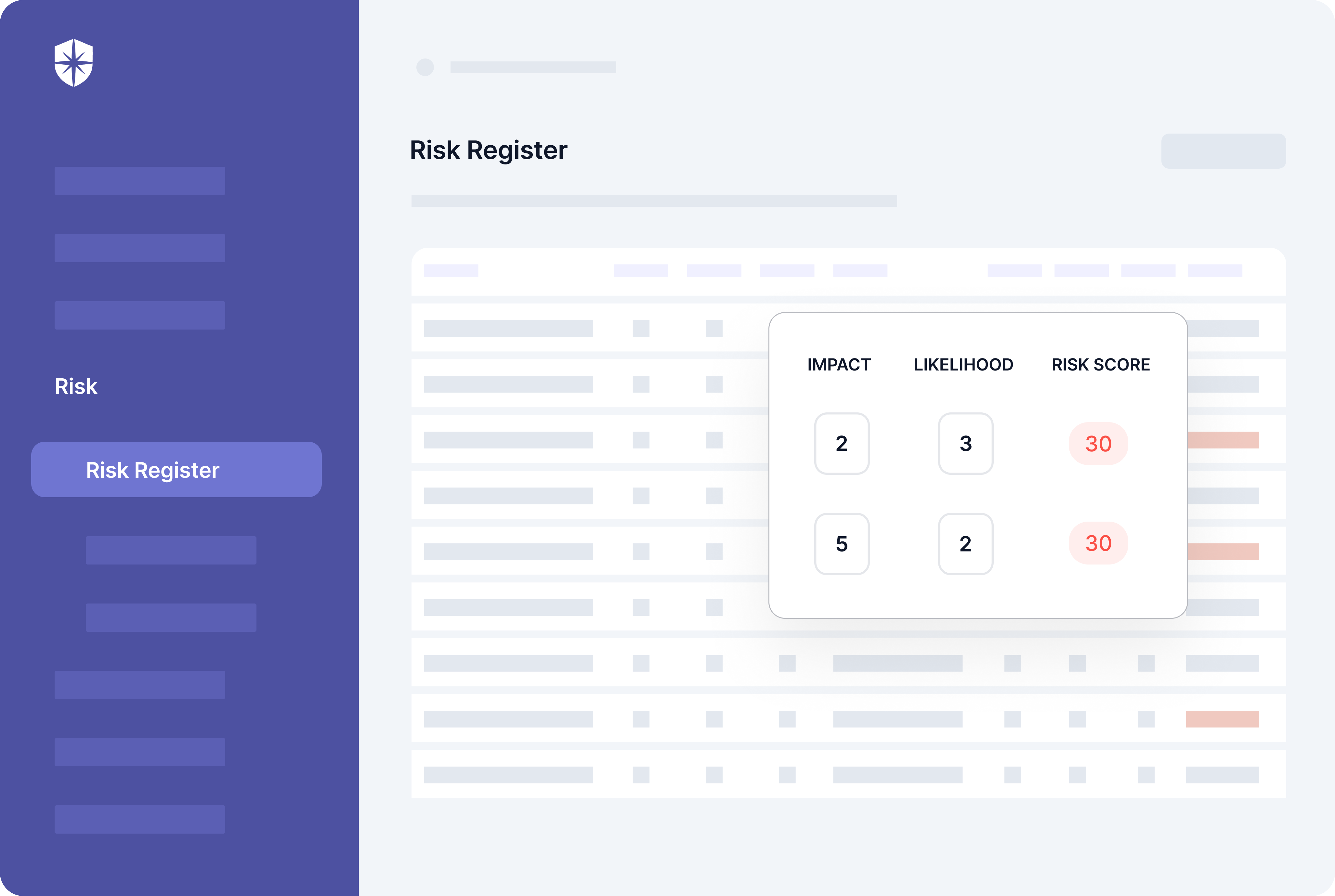
Continuously monitor your organizations’ adherence to the PCI DSS security controls, even after achieving initial compliance. Cyber Sierra’s continuous control monitoring suite automates this.
Our platform streamlines identifying and rating risks, automating the process of maintaining compliance with PCI DSS. Our prebuilt, auto-updated Risk Register, for instance, will help your team identify and know what risks to prioritize.
…all at a glance from one dashboard:

Automate Becoming PCI DSS Compliant
Becoming PCI DSS compliant, as this checklist shows, can be overwhelming and time-consuming. First, knowing what to implement from the 300+ controls to meet the 12 PCI requirements is hard, and depends on accurate internal security assessment.
Continuously monitoring your company’s cybersecurity posture to detect and remediate threats can also be daunting. But this is crucial to avoid getting penalized even after meeting initial compliance.
And it doesn’t end there.
The back and forth of sharing compliance documents between teams and external auditors can be a thorn in the flesh if done manually. But with a centralized platform, you can automate these processes, achieve compliance faster, and remain compliant.
This is where Cyber Sierra comes in:




A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.