Here’s How to Automate Ongoing Vendor Risk Monitoring





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
First impressions matter.
You wouldn’t approve a third-party vendor if they posed a single cybersecurity threat at first sight. They know this. It’s why they all come prepared with a good first impression to pass even the most rigid third-party vendor assessment questionnaires.
So while having a strict security questionnaire to score and clear 3rd parties of bringing zero risk to your organization is crucial, it’s never enough. You also need to know the risks that arise from using vendors —something positive first impressions can never detect.
Says Andy Ellis, Advisory CISO at Orca Security:


Here’s what CISOs and security executives must draw from this: Strict security assessment questionnaires have their place, but to make your third-party risk management (TPRM) processes more effective…
You Need Ongoing Vendor Risk Monitoring
Consider this stat:


And this one, too:
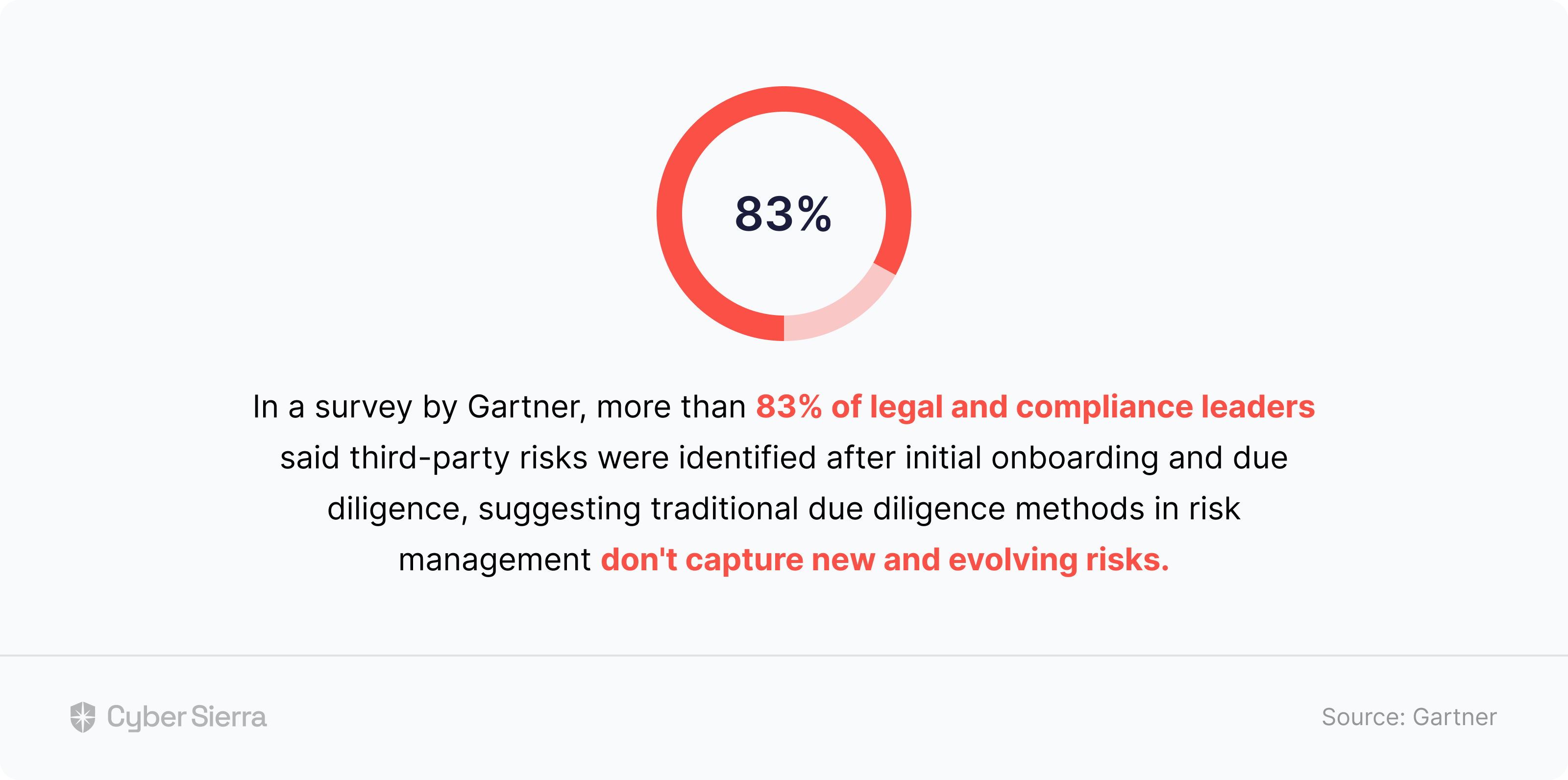

As these alarming data points clearly indicate, ignoring ongoing vendor risk monitoring can have serious consequences. First, about 98% of risk suffered by companies in recent years came from 3rd parties in their vendor ecosystem. Worse, a whopping 83% of those risks aren’t discovered during initial security assessments.
Continuous monitoring is therefore no longer a nice thing to have, but a core necessity. If you’re like me when I first realized this, you may be thinking: So how do CISOs and IT executives achieve continuous third-party risk monitoring?
The rest of this article will explore how. Specifically, you’ll also see how our interoperable cybersecurity and compliance automation platform, Cyber Sierra, streamlines the entire process.
But before we proceed…
Categorize Vendors; Ease Continuous Risk Monitoring
When Uber suffered a breach in September 2022 through a third party vendor, they moved quickly to block security loopholes. In their press release on the attack, the enterprise company wrote:


But just two months later, it happened again.
In December of the same year, cybercriminals stole sensitive data from Uber through another 3rd-party vendor, Teqtivity. This attack revealed that Uber may have improved their vendor risk policies, but it still wasn’t enough to detect imminent breaches.
And the reason isn’t far-fetched. Growing startups and large enterprises like Uber work with a lot of outside vendors. According to a Gartner report, over 1,000. This can make it hard for security teams to know which ones pose the most risks and need constant attention.
Vendor Categorization Solves this Problem
For instance, imagine Uber’s security team categorized third-parties in their vendor ecosystem on criteria such as:
- Confidentiality of company info they can access
- Sensitivity of customer information they need to work
- The number of mission-critical assets they can access
- Likelihood to be breached based on their operating location:
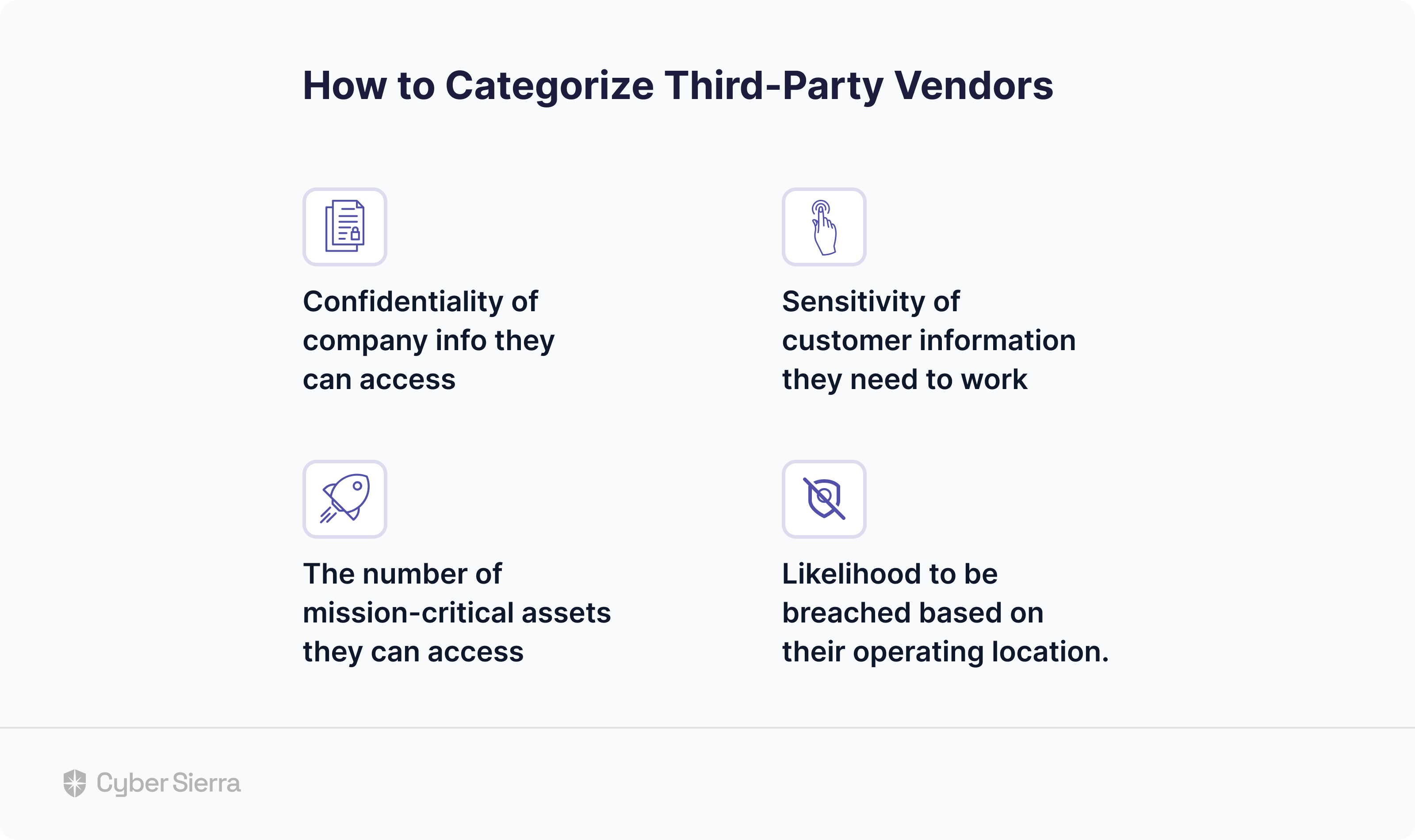

Categorizing 3rd parties in this way simplifies ongoing monitoring of vendor risks. That’s because your security team can laser-focus on those that must be tracked 24/7, as Uber should have.
And the best place to start?
When sending assessment questionnaires.
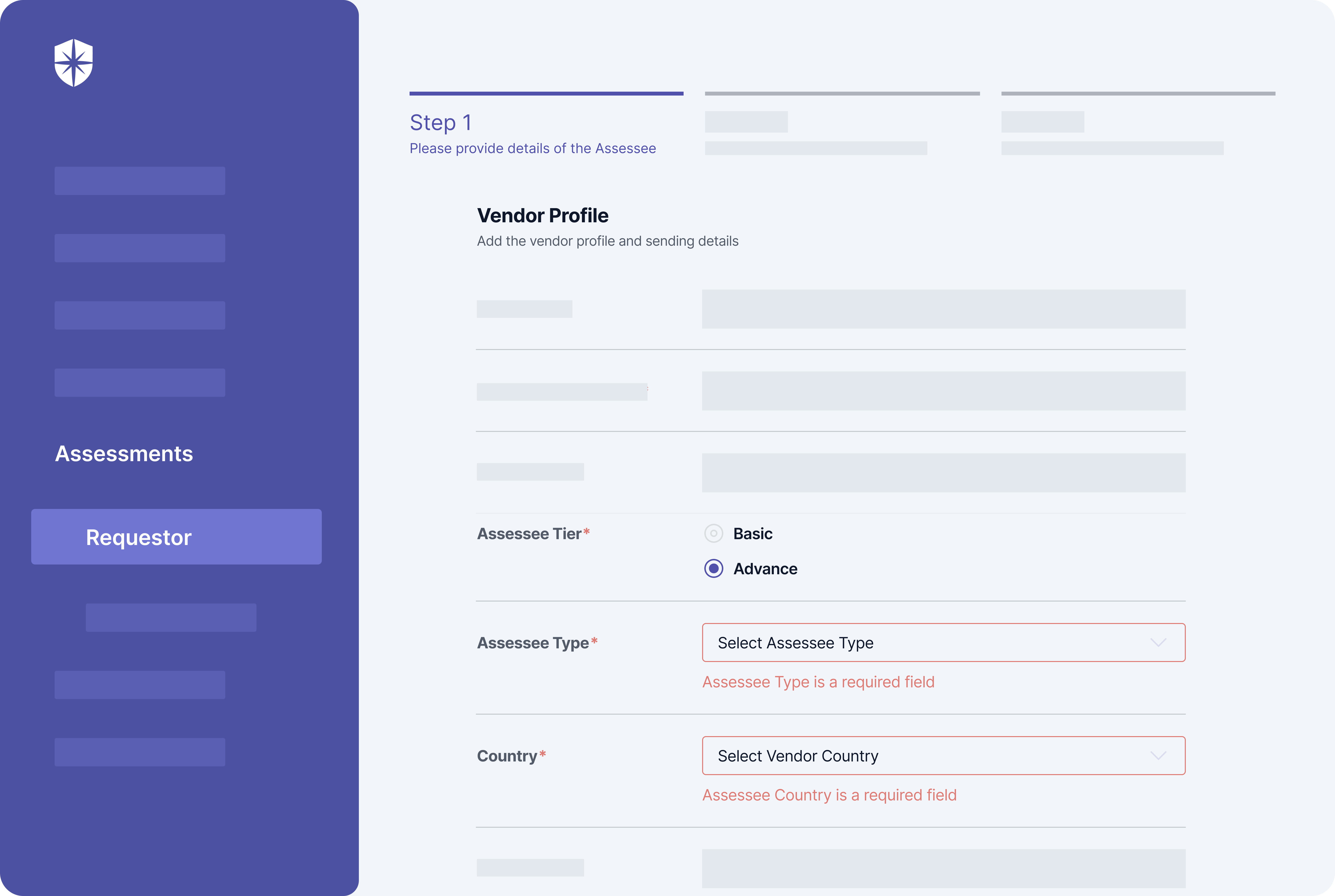
By enforcing the categorization of vendors when sending security assessment questionnaires, your team can easily profile those that:
- Require advanced assessments (based on the confidentiality of your company info they’ll access)
- Can access sensitive customer info or mission-critical assets (based on their assessee type –service, software, etc.)
- Are more likely to get breached (based on the vendor’s country of operation):
Achieving this level of categorization is automated with Cyber Sierra’s cybersecurity and compliance automation platform assessment suite:

And it doesn’t end there.
Once categorized with our software, your security team gets a central dashboard to search and continuously monitor specific vendors for risks.
Third-Party Risk Management Challenges Solved By Ongoing Monitoring
Typical third-party risk management is complex.
Because everywhere you turn, there are third parties potentially involved. From network servers to operating systems, to software installed on workstations, to the service-based vendors that make the business and software work. The list goes on, up to the vendors delivering office supplies. Without ongoing vendor risk monitoring, it’s almost impossible for security teams to overcome the challenge of identifying threat-carrying or at-risk vendors.
But that’s not the only challenge it solves.
1. It Reduces Wasted Costs
After the data breaches on Uber in September and December 2022, both Uber and the affected third-party vendors hired digital forensic firms to investigate. They also incurred costs, launching massive PR campaigns to communicate both incidents and save the cost of losing brand reputation and customer trust.
How much do all such costs come to?
A lot.
On average, a data breach costs companies a whopping US$4.35 million, according to IBM’s 2022 research. This amount almost doubled for US-based organizations, the study revealed. But here’s what the same study found of companies using automated tools to monitor and identify risks beforehand across the board:
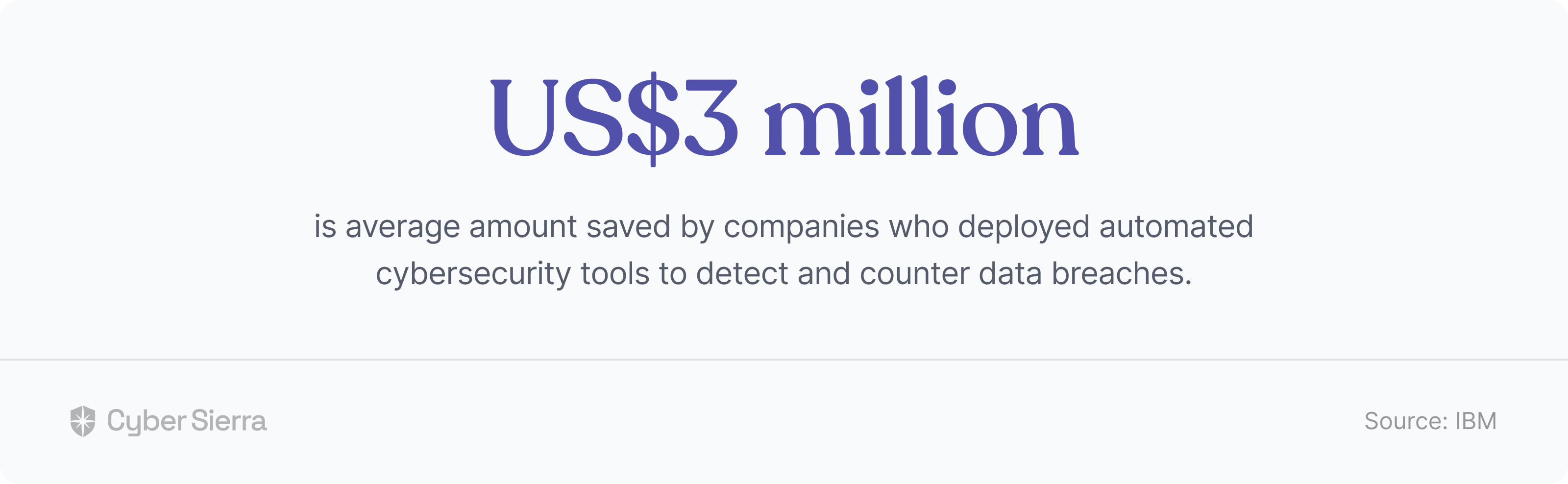

Ongoing vendor risk monitoring helps your team reduce costs from third-party data breaches. As IBM’s study found, this is because your security team would be more likely to identify and mitigate them.
2. It Removes TPRM Vendor Threat Blind spots
When you’re dealing with hundreds of vendors, as is the case with most organizations today, identifying threats is hard. This leads to blind spots, which, when accumulated, make your TPRM process a threat black box waiting to be data-breached.
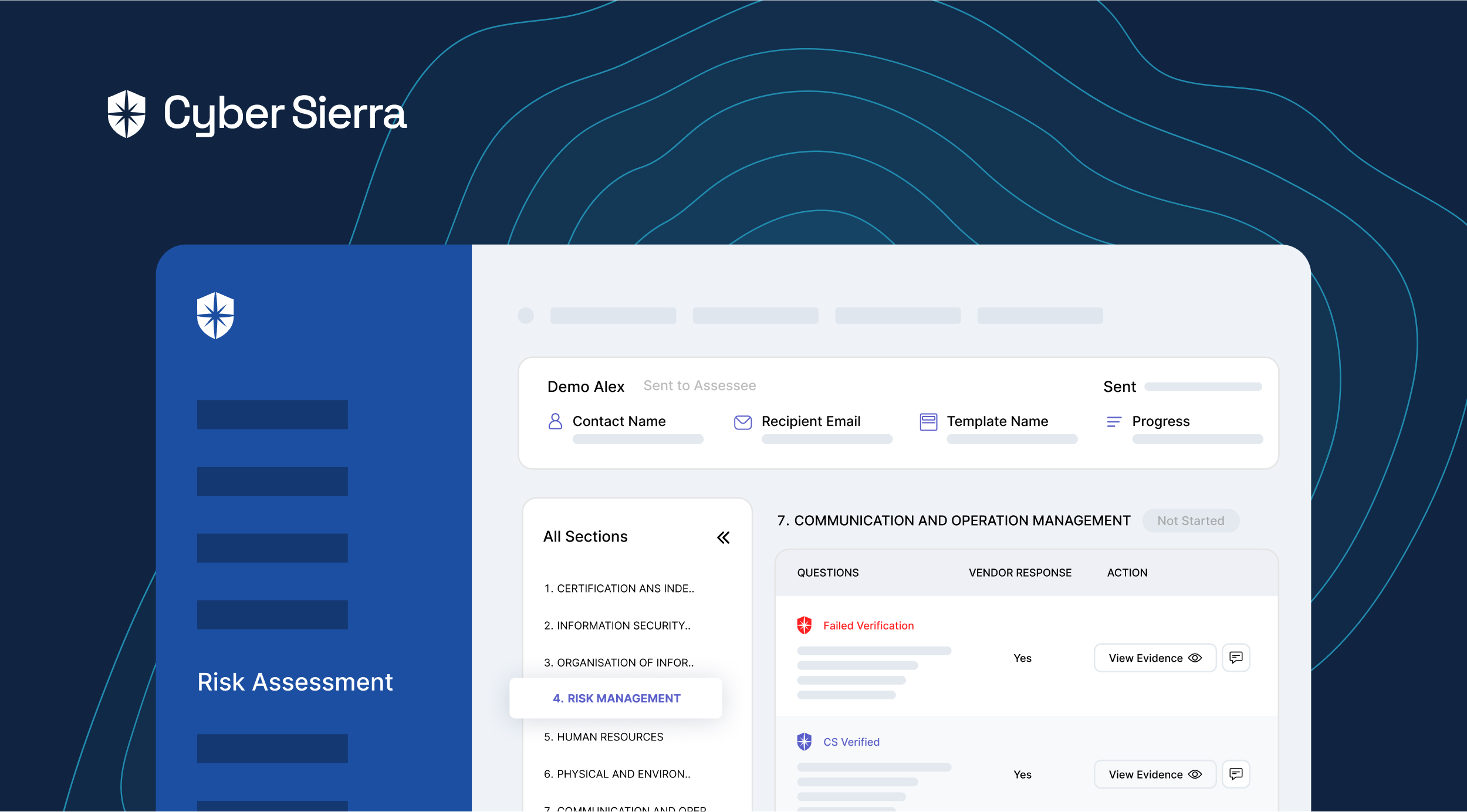
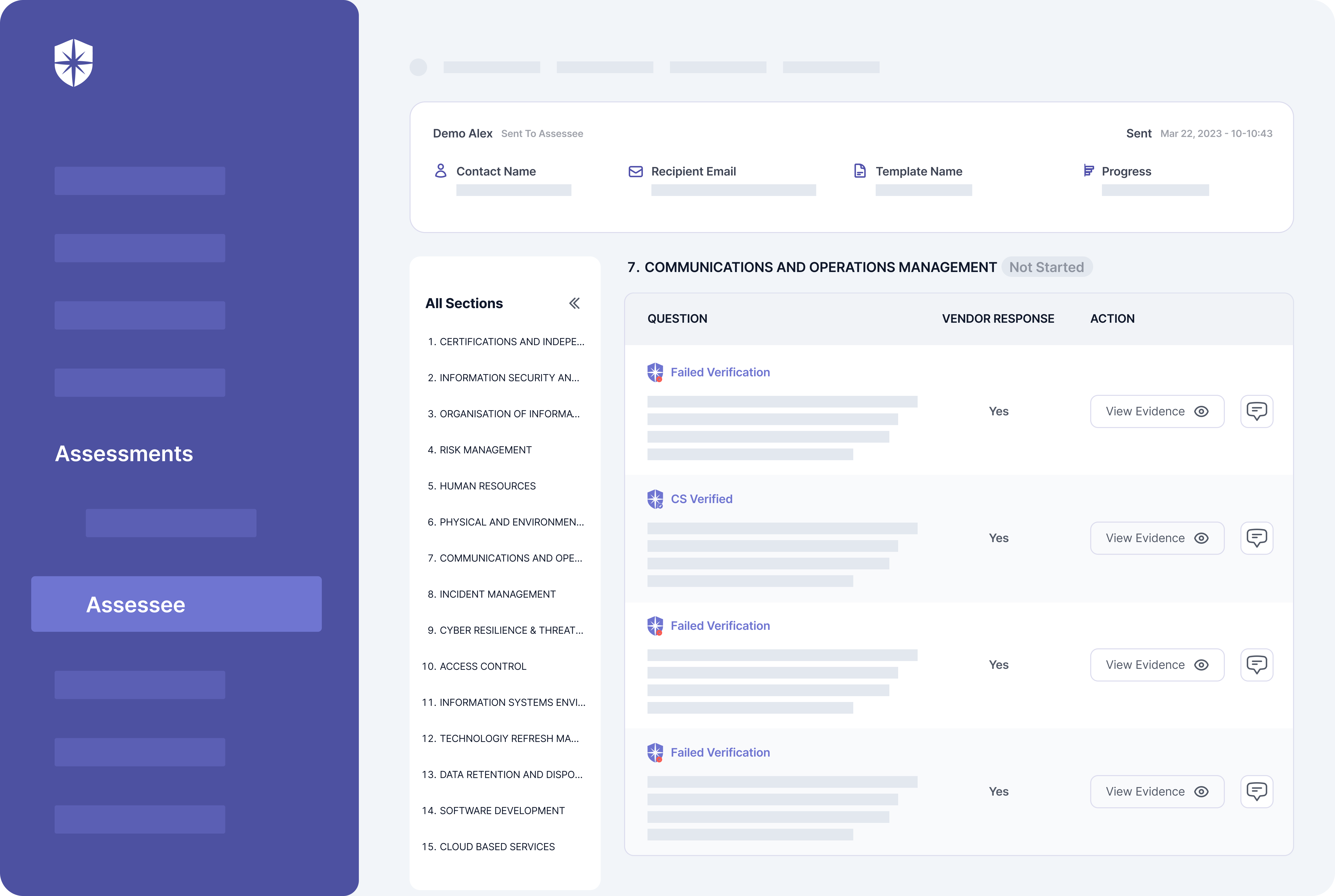
But with ongoing vendor risk monitoring, especially when done with an automated tool, your security team can remove such threat blind spots with prompt alerts. For instance, with Cyber Sierra, you can achieve continuous monitoring by auto-verifying all evidence uploaded during the vendor security assessment phase.
Our system runs continuously in the background to identify vendors with weak, outdated, or no security controls in place, based on uploaded evidence. Your security team gets alerted on controls that fail verification and can follow up with vendors to fix them on the same dashboard:

3. It Removes the Need for Sample-based Analysis
Consider this research finding by ThoughtLab:
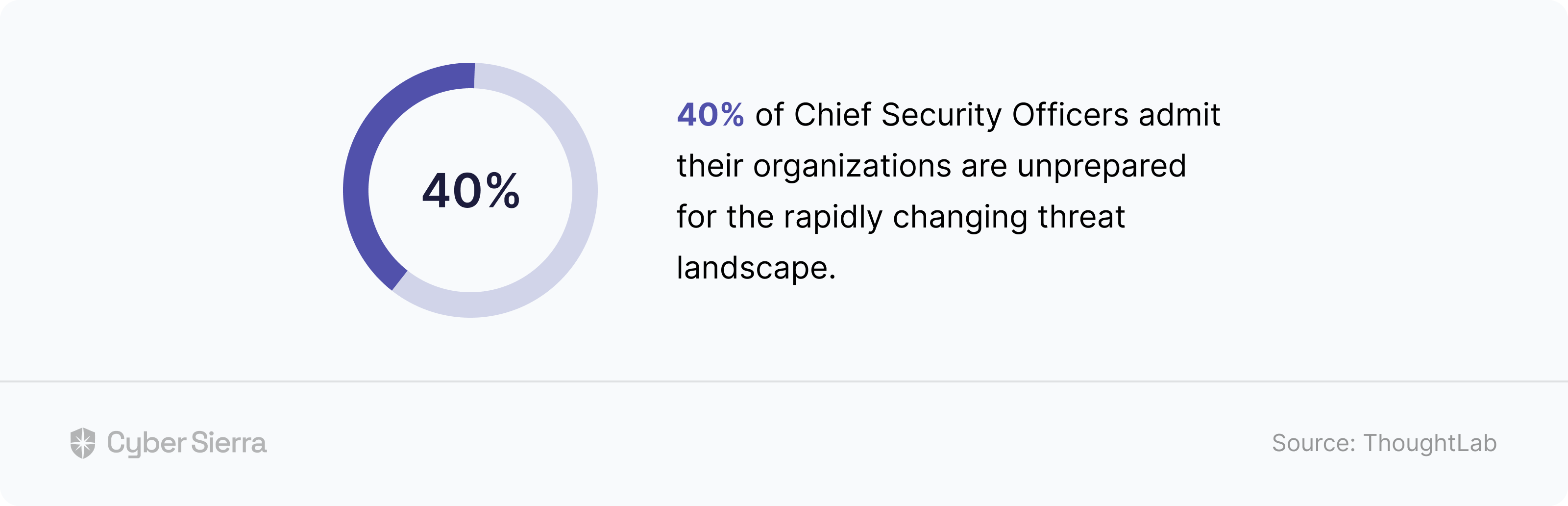

The top two reasons given for this include:
- Complexity of supply chains (44%),
- Fast pace of digital innovation (41%).
It’s a different story on the side of cybercriminals. While security executives are grappling with emerging risks in their supply chains and vendor ecosystems, threat actors are getting even more equipped to strike. Chuck Brooks, a cybersecurity expert, observed this in a Forbes’ article.
He wrote:


At this pace, identifying vendor risks through periodic, sample-based analysis just can’t keep up. Imagine waiting for external analyst firms, which are usually expensive, to sample a segment of your vendors, say yearly. With cybercriminals now hacking companies in days and hours, of what use would that be?
Not so much.
Ongoing vendor risk monitoring removes the need for such sample-based analysis. But more importantly, as we’ve stressed so far in this article, your security team can automatically identify and mitigate cybersecurity risks from third-parties in real-time.
Automate Ongoing 3rd Party Vendor Risk Monitoring
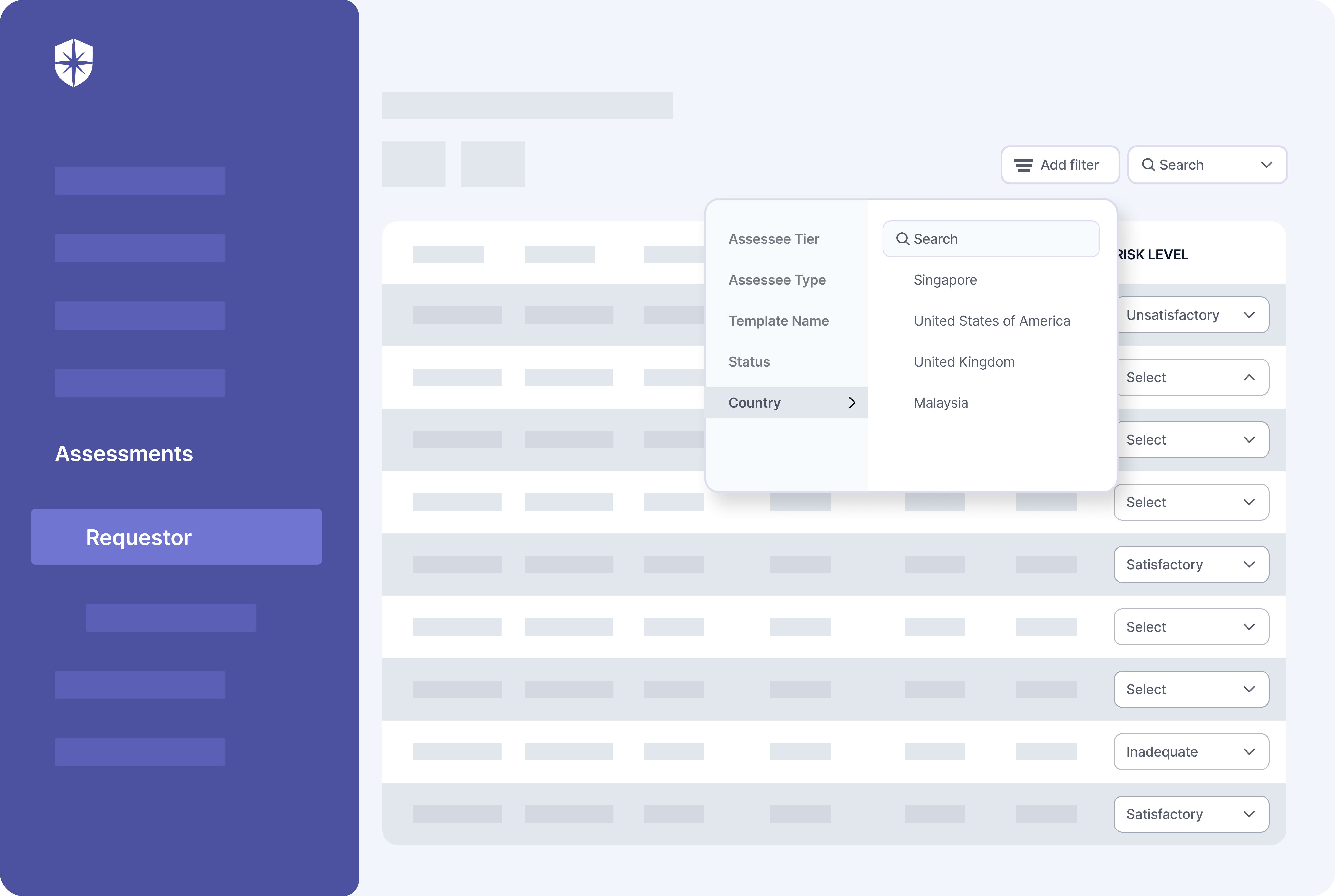
Imagine a central place where you can easily profile vendors when onboarding and sending security assessment questionnaires. From the same dashboard, your security team gets an automatic categorization of vendors they must monitor constantly.
This categorization could be:
- Vendor tier (i.e., level of integration into private/customer information or vitality to your company’s operations).
- Vendor type (i.e., service, software, application software, etc., and the level of mission-critical assets they can access).
- Vendor location (i.e., those based out of location with strict or weak cybersecurity regulation that requires more attention).
Cyber Sierra enables this advanced level of categorization to the third-party risk management process. Most importantly, our platform automates ongoing vendor risk monitoring. This is because your security team can quickly search and track 3rd-parties’s risk level in real-time, and in a few clicks:




A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.