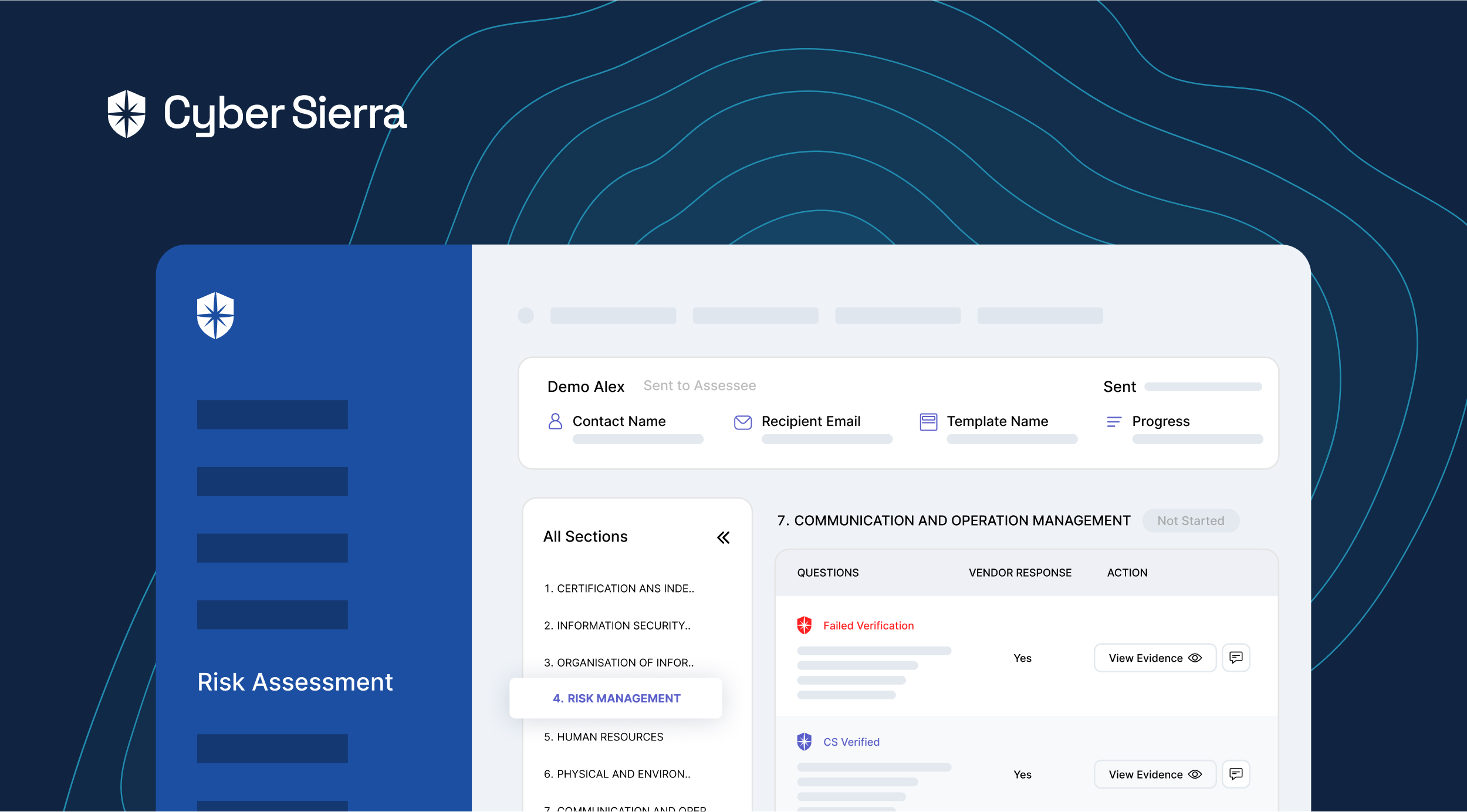
Best Practices to Create a Third-Party Risk Management (TPRM) Program





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
All businesses involve finance, sales, marketing, and other operations. And outsourcing some of these functions is the easiest way for large enterprises to grow. However, it’s imperative to recognize that these business relationships can also expose your enterprise to significant threats in the form of data breaches.
According to a survey by IBM, nearly 83% of the organizations they studied have had more than one data breach. And it caused an average loss of $4.35 million!
The smart way to circumvent these third-party risks is to mitigate and manage them proactively. Enter Third-Party Risk Management.
Read on to uncover everything you need to know about Third-party risk management and its best practices.
What is Third-Party Risk Management?
The third-party risk management is a structured approach to mitigate any third-party risks associated with your business. Enterprises create a TPRM framework, which includes vendor risk assessment, monitoring, and mitigation to protect their data.
Vendors, suppliers, contractors, distributors, service providers, manufacturers, affiliates, and other third-party organizations expose your enterprise to a multitude of risks. Third-party risk include:
- Operational risks
- Financial risks
- Reputational risk
- Compliance risk
- Cyberattack risk
- Data protection risks
Third-party risk refers to the various types of risk that a business faces from its relationships with other parties and organizations that it works with.
6 critical components of the TPRM Framework
There are six components of a typical third-party risk management framework including:


The process involved in each element is different and goes through a lifecycle. Let’s dive into each of them.
1. Risk assessment and categorization
The company assesses the risk associated with each third-party vendor. A TPRM framework identifies and evaluates the risks stemming from any third-party relationship. This may encompass operational, financial, compliance, and other aspects.
This step is crucial for identifying potential threats to the business. The TPRM framework incorporates risk matrices or scoring systems to categorize these risks
2. Due diligence
Due diligence is a process that involves assessing qualifications, conducting background checks, and verifying documents before engaging in a third-party relationship. This process serves to diminish the likelihood of potential threats posed by third-party vendors and fosters trust between your company and these vendors.
Organizations should establish specific criteria for selecting vendors, which may include evaluating their financial stability, ensuring compliance with regulations, and assessing alignment with corporate values.
3. Contractual agreements
Contractual agreements entail the creation of precise contracts that outline responsibilities, obligations, expectations, scope, and other essential terms. These contracts incorporate legal clauses designed to safeguard data against breaches and ensure compliance with regulations.
They also include conditions and indemnifications to address various scenarios. It’s important to note that contracts may need to be modified in response to new regulations or significant changes in circumstances.
4. Continuous monitoring
Continuous monitoring is an automated process in which companies routinely assess networks, organizations, IT systems, and other third parties to ensure they adhere to legal contracts and obligations.
This component detects security, performance, or noncompliance issues and prevents/ warns them! Companies use metrics and Key Performance Indicators (KPIs) to measure performance and legal obligations.
5. Risk mitigation
Now that you have identified the risks, it’s time to take action. This phase involves the development and implementation of strategies to mitigate or manage the risks associated with third parties. Risk mitigation strategies may include contingency plans, security controls, insurance coverage, and other measures.
6. Incident response
Incident response plans delineate the steps to be taken in the event of an incident, encompassing the involvement of third parties and the risks associated with them, such as data breaches or compliance violations.
This step is essential to ensure a coordinated response whenever an incident occurs. These plans typically include the identification of the incident, notification of stakeholders, containment of the incident, investigation of its root causes, and the implementation of corrective actions.
Each of these components is crucial for a proactive and successful third-party risk management lifecycle.
10 steps to create a strong Third-Party Risk Management Framework
Any cybersecurity-conscious enterprise must adopt a robust TPRM framework to identify, avoid, and mitigate any third-party risks in its business operations.
Here are the 10 steps to create a third-party risk management framework that manages all your business risks.


1. List all the third-party affairs
No matter the number or size of the third-party vendors you are affiliated with, you must document every vendor information in your system. It includes the vendor information, their service type, the risks they can make, and their roles.
2. Identify and categorize the third parties.
Create a separate list of categories to quantify the risks based on the third-party affairs and based on their potential impact on the business.
Make an intuitive category, either ABC or high, medium, or low, depending on the risk rating. Then, put each of them in the class according to the seriousness of the risks.
For instance, the TPRM program in Cyber Sierra allows enterprises to maintain a central repository of all their vendors on a single platform and helps score them in terms of the risks. But more on that later.
3. Vendor risk assessment
Identify and assess every risk associated with third-party vendors. Document and categorize each of them into the different types of risks. You can table them as operational, financial, legal or reputational.
This helps to assess the potential risks that the third-party relationship in the future might cause. With Cyber Sierra, you can do a continuous risk assessment for your third-party vendors and identify all the potential risks associated with them and proactively take mitigating actions to reduce their impact.
4. Risk mitigation and control
It might cost you a good governance team to handle your TPRM framework- but it’s worth it. Appoint a TPRM team in your organization, or get yourself a professional TPRM platform such as Cyber Sierra’s that can manage it all for you. Cyber Sierra can seamlessly bridge the gap between your TPRM requirements and your vendors, and make the process effortless, efficient, and most importantly, effective.
5. Due diligence
Even though the due diligence method is quite traditional, it pours many benefits into the TPRM framework. Develop a strategy that involves a series of diligent inspections. It includes a thorough background check, document verifications, checking the reputation, financial audits, and security of the third-party organization.
This is a process that requires time and effort, but it can be very effective in protecting your business from fraud and other risks. A thorough due diligence will help you avoid the hard costs associated with doing business with an unreliable vendor.
6. Contractual agreements
Inform your third-party vendors of the significance of the boundaries maintained in case of regulatory compliance.
Create a concise and explicit contract that states the scope, parties’ roles, data protection clauses, regulatory compliance, and termination conditions. This way, any third-party company that causes risk is subjected to legal obligations.
7. Continuous monitoring
Establish a system for continuous monitoring of third-party activities and risk exposure to prevent any risks ahead.
Set the frequency for assessments, which may vary based on the nature of the relationship. Companies also use metrics and key performance indicators (KPIs) to measure performance and adherence to contract terms.
Cyber Sierra’s intelligent platform allows you to monitor the security posture of your vendors continuously instead of simply relying on a one-off filling up of security questionnaires with no means to follow up and ensure all the security practices are always put to practice.
8. Reporting and communication
Create mechanisms for reporting and communicating third-party risks to relevant stakeholders. Ensure executives and regulatory authorities are informed to prevent any leading miscommunications between the stakeholders and the company.
9. Continuous improvement
Review and update your TPRM program regularly based on lessons learned, changes in third-party relationships, and evolving risks. To manage the risks better, adapt to new regulatory requirements, industry best practices, and technologies that give new insights into the TPRM framework.
With Cyber Sierra, you can incorporate regulatory as well as custom requirements into your TPRM framework.
10. Exit strategies
Vendor offboarding is also a critical step and needs meticulous planning and best practices such as data retrieval and contingency plans.
Benefits of Third-Party Risk Management
Implementing a Third-Party Risk Management (TPRM) program offers numerous benefits to organizations across various industries. Here are some of the key advantages:
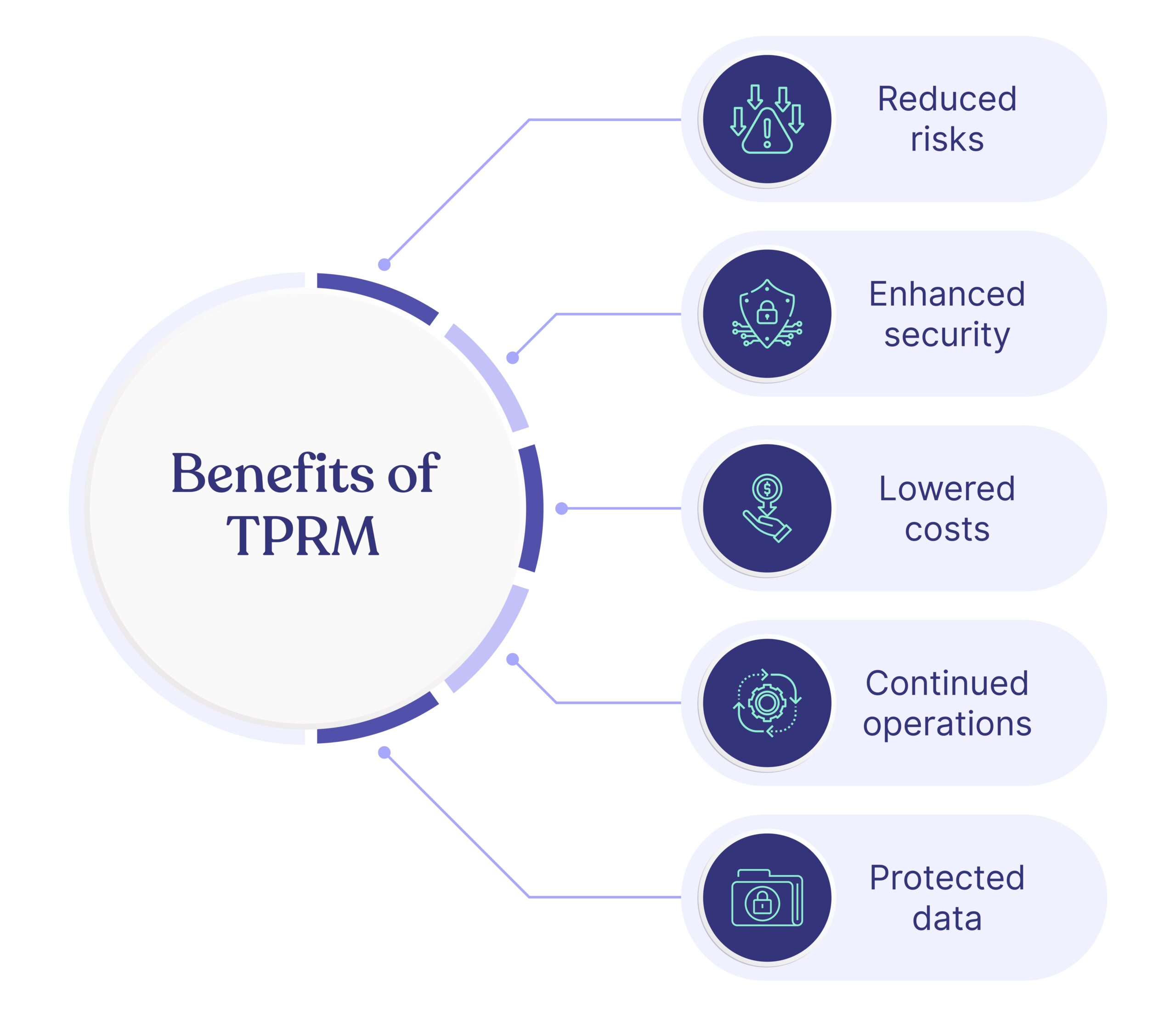

Let’s look at them one by one.
1. Reduced risks
TPRM helps organizations identify, assess, and mitigate risks associated with their third-party relationships. This approach minimizes the likelihood of unexpected issues, such as data breaches, compliance violations, or supply chain disruptions.
2. Enhanced security
It also helps protect sensitive data and intellectual property. The TPRM program assesses the third-party cybersecurity practices and requires security controls. This eliminates the primary source of stress in the age of cyber-attacks.
3. Lowered costs
TPRM programs are excellent in detecting the risks. Therefore, they prevent costly incidents or disruptions resulting from third-party failures. As aforementioned, data breaches can cause millions of financial losses, leading to reputational damage.
4. Continued operations
Effective TPRM programs include contingency planning for potential disruptions caused by third parties. This ensures that operations can continue smoothly even when third-party issues arise.
5. Protected data
Protecting customer data and sensitive information is a top priority for many organizations. TPRM ensures that third parties handle data appropriately, reducing the risk of data breaches.
Best Practices for Maintaining an Effective Third-Party Risk Management Framework
Managing risk is a vital aspect of any business endeavor. Consequently, the need for an effective third-party risk management framework is both pressing and complex.
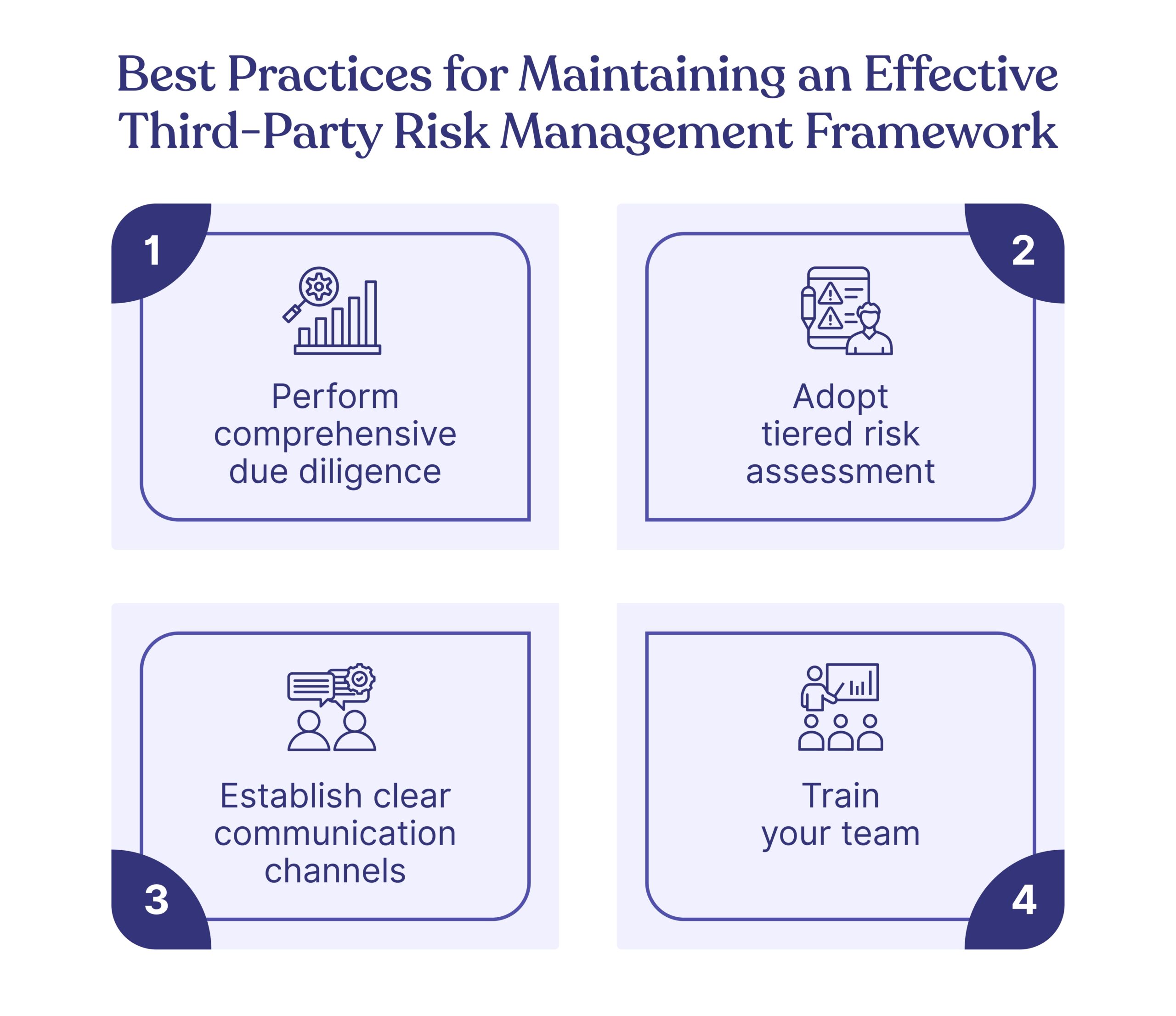
Here are some best practices to ensure that your third-party risk management framework is not only robust but can adapt to an ever-evolving risk landscape.

-
Perform comprehensive due diligence
Due diligence is more than checking a box; it’s about understanding a potential third-party’s operations, controls, reputation, and financial health. Your risk management, therefore, must start before a partnership or engagement begins.
It’s crucial that you delve into their past dealings to spot any red flags regarding their business conduct, legal or regulatory issues.
-
Adopt tiered risk assessment
Not every third-party will pose the same level of risk to your organization. Some may have a minimal impact, while others can have significant business implications.
Categorize your third-party partnerships based on the level of risk exposure they bring. This helps focus your resources where they are most needed.
-
Establish clear communication channels
Transparent, unimpeded communication channels form the backbone of effective risk management. From notifying third parties about your policies and expectations to obtaining updates about their activities that may impact your business, communication is key.
Regular dialogues also reaffirm the third-party’s responsibility towards risk management and ensure they remain compliant with your standards.
-
Train your team
The onus of managing third-party risk doesn’t fall on a single department; it is an organizational endeavor.
Therefore, inculcate a culture of risk awareness throughout your organization. Regular training sessions help employees at all levels grasp the significance of third-party risk and their role in mitigating it.

With Cyber Sierra, you can ensure your team is well-informed and trained on how to mitigate third-party risk. Our training sessions can also be customized based on your requirements, so you can be sure they meet all the legal and regulatory standards that apply to your organization.
-
Leverage technology
There are numerous technologies, software, and tools available today that can streamline your risk management processes.
These solutions can automate various steps of the risk assessment process, keep track of documentation, provide real-time analytics, and ensure a consistent approach to risk management across the organization.
Check out our detailed guide on: Best Third-Party Risk Management (TPRM) Tools.
Conclusion
Risk management is a dynamic process that needs to be updated regularly. You need to keep track of the changing business environment, new regulations and legislation, and new threats and vulnerabilities. This is why it’s so important to have a dedicated team in place that can conduct regular risk assessments and make sure your organization has the right policies and procedures in place.
With Cyber Sierra’s third-party risk management program you evaluate, mitigate, and monitor third-party vendor risks.
The TPRM program is customizable to the needs of different industries and ensures compliance with region-specific regulations, such as Singapore’s PDPA, Australia’s CIRMP, Europe’s GDPR, and USA’s CCPA, HIPAA, and PCI DSS, to name a few.
Book a demo to know more.



A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.