HIPAA Compliance Checklist Guide for Automating the Process





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
US$25 billion with a ‘b:’


The healthcare sector lost all that to cyberattacks from 2020 to 2022 alone. To curb such losses, the Health Insurance Portability and Accountability Act (HIPAA) emerged in 1996. Unfortunately, almost two decades later, cybercriminals have only gotten smarter.
So responding to the growing threat landscape, the Office for Civil Rights (OCR) continues to tighten enforcement with heftier fines. As a result, it no longer ends at attaining initial HIPAA compliance.
Security officers must now also automate the gruesome post-HIPAA compliance process to stay compliant and avoid fines.
And a good starting point is to…
Know the HIPAA Compliance Requirements
Being a US federal law, the HIPAA regulation has many requirements grouped under five main components or HIPAA rules.
As illustrated below:
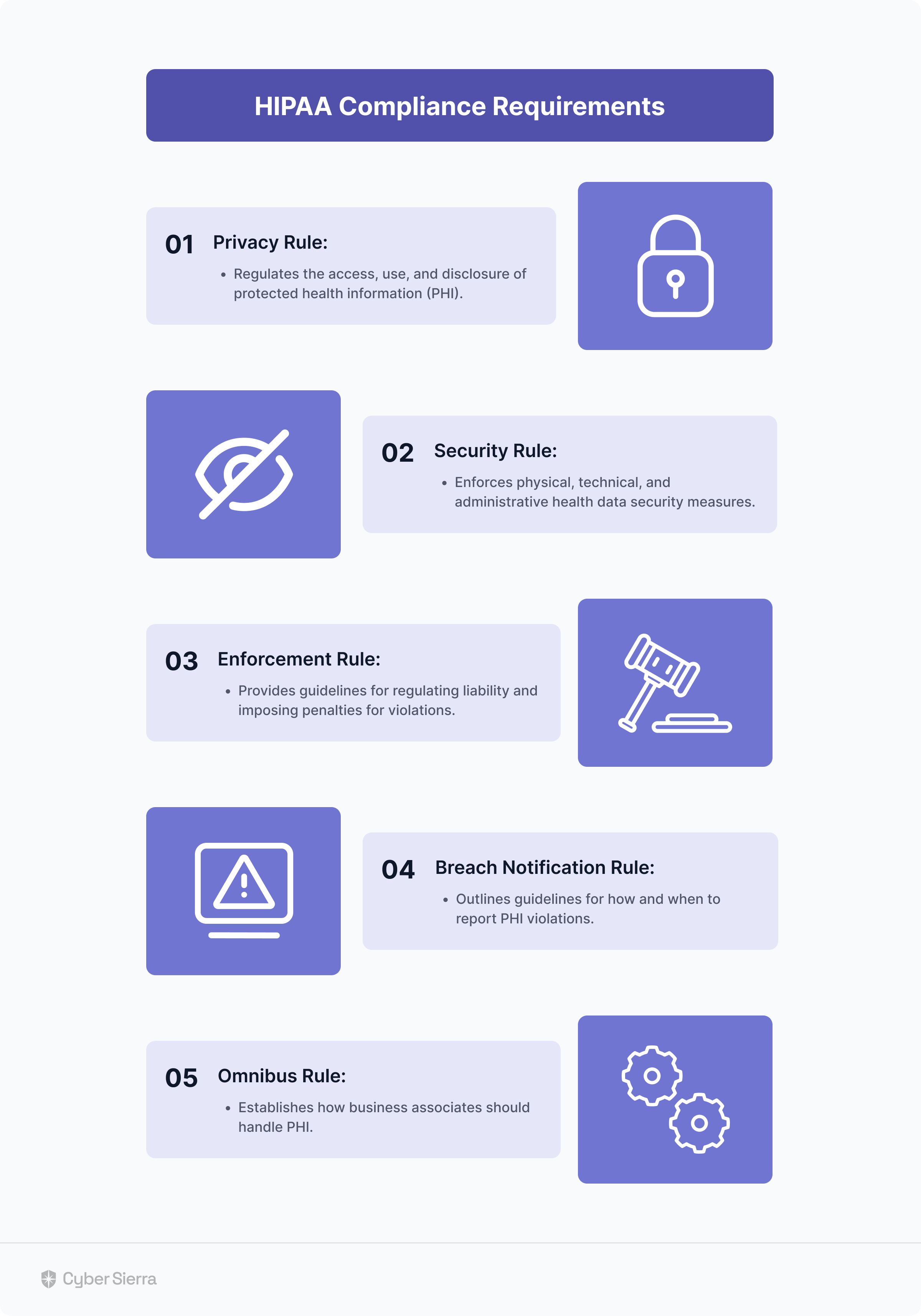

Correct implementation of requirements under each rule demonstrates that a company directly or indirectly accessing protected health information (PHI) is keeping it safe and secure. However, as earlier noted, you must continuously implement them to (1) become and (2) stay HIPAA-compliant.
This checklist guide walks you through how to achieve both. As we proceed, you’ll also see how Cyber Sierra automates implementation of crucial HIPAA rules and requirements.
Download your copy to follow along:
The 8-Step HIPAA Compliance Checklist
From determining HIPAA rules to developing policies and implementing safeguards, HIPAA compliance can be overwhelming. To help, we’ve broken the many moving parts into eight actionable steps in this checklist.
But before diving in, there are two company types —Covered Entities and Business Associates— that must comply with HIPAA regulations.
This infographic illustrates:


As you’ll see throughout this checklist guide, where you fall into is crucial for gauging your company’s HIPAA compliance readiness.
Let’s dive in.
1. Determine What HIPAA Rules Applies to You
HIPAA’s Privacy Rule and Security Rule details what companies must do to protect PHI and electronic protected health information (ePHI). The Breach Notification Rule, on the other hand, details remediation steps organizations must take in response to a breach.
But not all companies must comply with them.
Covered Entities, for instance, must implement all safeguards dictated by the Privacy Rule and Security Rule. They are also mandated to protect both PHI and ePHI. This isn’t the case for Business Associates, even though some Privacy Rule requirements apply to them.
So the first step towards HIPAA compliance readiness is knowing what HIPAA rules apply to your organization.
Three things you should do are:
- Understand the intention of each rule’s requirements.
- Review the technical specifications required for each rule.
- Outline the correct procedures, safeguards, and policies you should create and implement for your organization.
2. Appoint a HIPAA Compliance Officer
If that first step looks complex, it’s because it is.
Hence, the need to appoint someone on your security team to spearhead your company’s HIPAA compliance process. Some things this appointed officer (or consultant) will oversee include:
- Determining applicable HIPAA rules and regulations
- Ensuring the right controls and policies are in place
- Conducting risk assessment to detect vulnerabilities
- Training employees on HIPAA implementation
- Enforcing the implementation of security controls and policies
- Investigating incidents and data breaches
- Developing action plans for remediating breaches
- Implementing continuous monitoring to ensure that your organization stays HIPAA-compliant always.
Before we proceed…
Imagine your appointed HIPAA compliance officer (or maybe, you) could do most things highlighted above from one place. Imagine you had an interoperable cybersecurity platform that brings all the features for achieving the things above from one platform.
That’s where software like Cyber Sierra comes in:
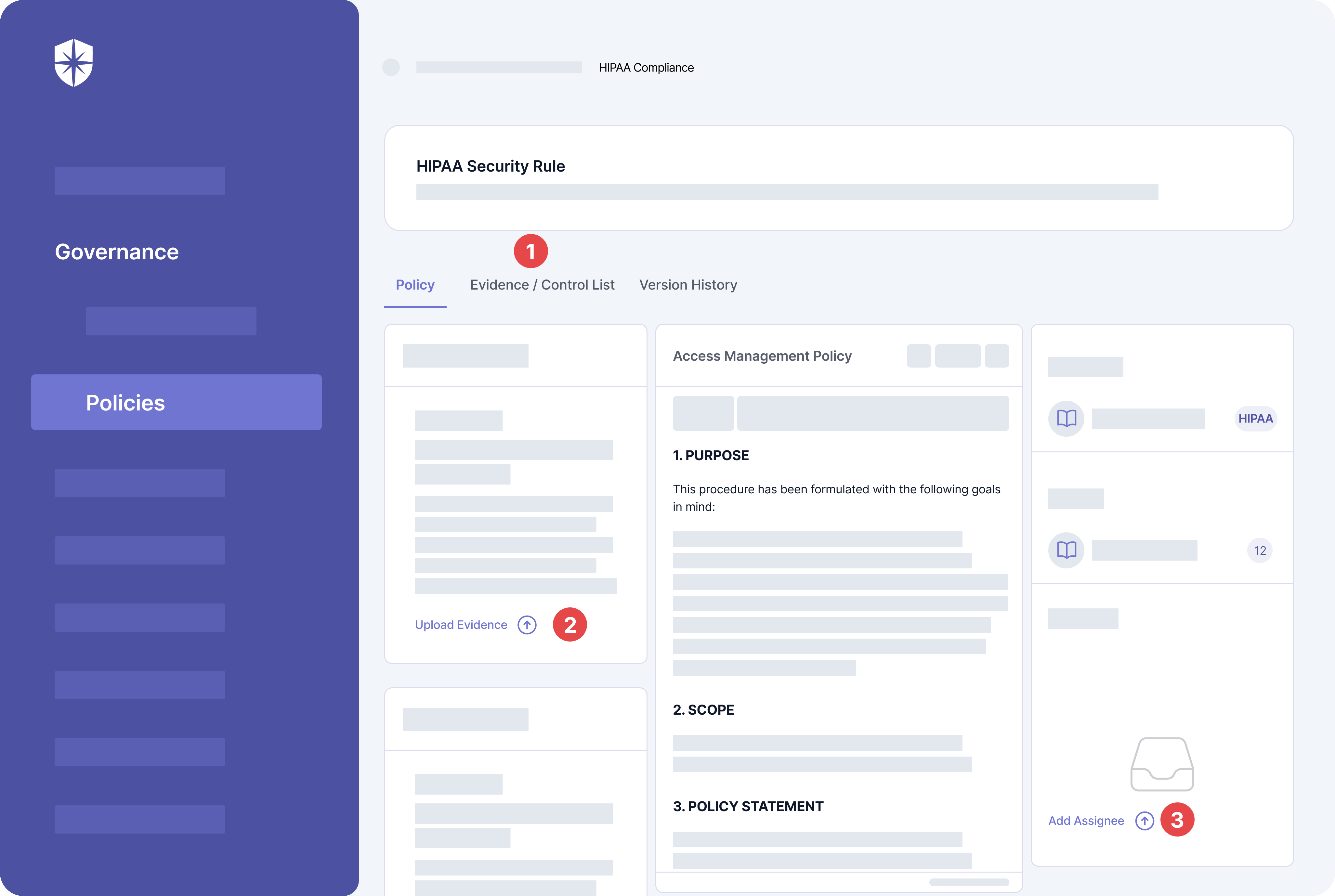
3. Develop Your HIPAA Compliance Policies
All HIPAA rules have mandatory requirements.
So for each rule that applies to your company, you need policies and procedures to show you meet those requirements. In other words, you must develop documentation that will prove your employees are handling PHI and ePHI data safely.
Across the three main HIPAA rules, some compulsory policies are:
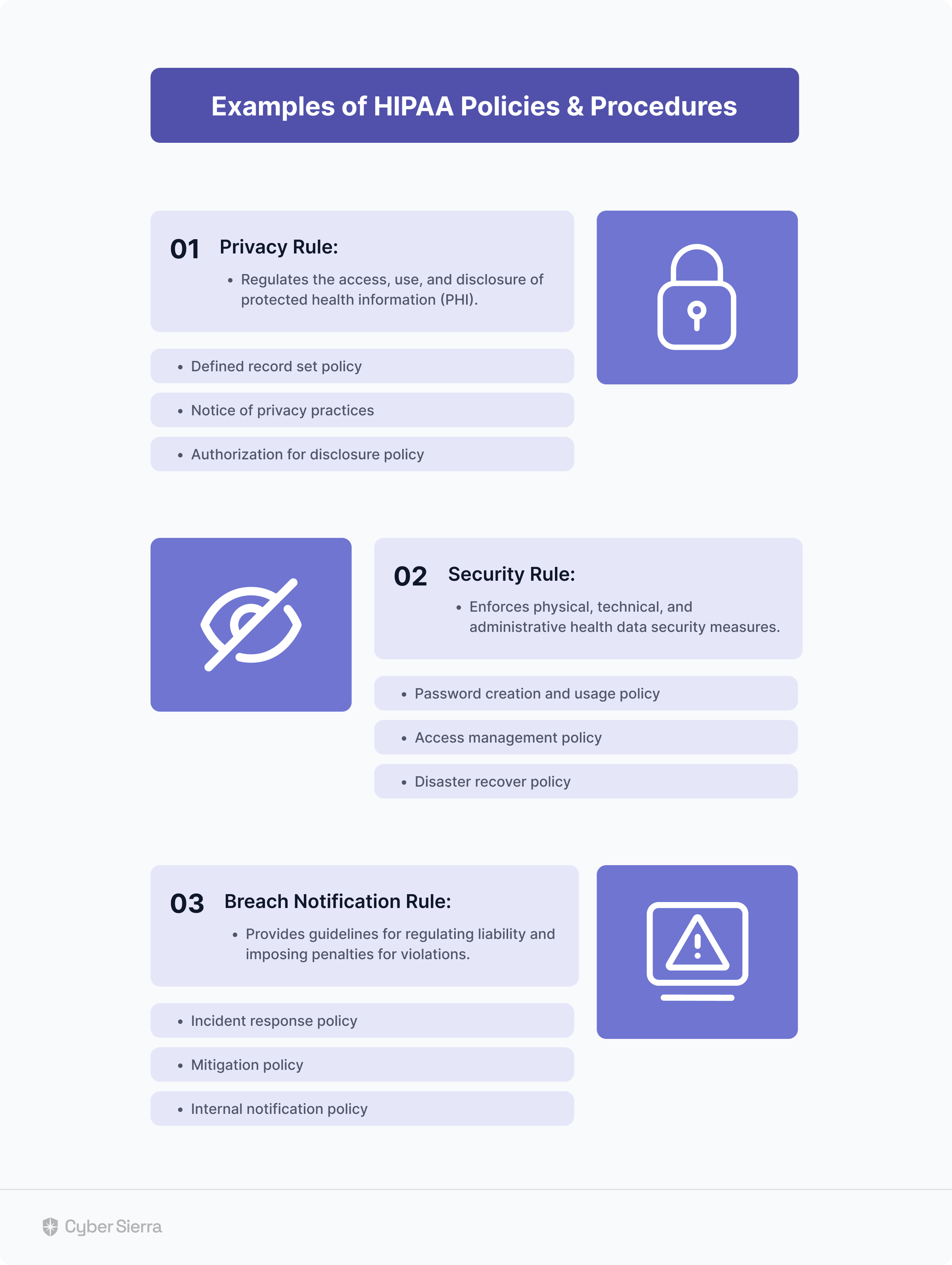

Managing all these policy documents through email threads or spreadsheets can be draining.
But imagine a central place where you can:
- Create policy documents
- Upload evidence easily, and
- Assign the implementation of each policy.
You can do all three things and more to automate most HIPAA compliance processes with Cyber Sierra:

4. Manage Business Associates with Access to PHI
The HIPAA Security Rule mandates that Covered Entities working with a Business Associate or vice versa have a legally binding agreement. Known as a business associate agreement (BAA), this is to ensure the protection of PHI and ePHI accessed by both parties.
A BAA should cover all relevant topics. Examples of topics include permitted uses of PHI and ePHI, reporting unauthorized disclosures and uses, processes to return or remove PHI when terminating, etc.
We created a template to help with this.
Download (and customize) it to start creating your own BAA below:
5. Implement HIPAA Security Rule Safeguards
Only the HIPAA Security Rule has over 50 implementation specifications. This makes complying with the rule a complex hurdle, requiring necessary safeguards. And the HIPAA groups these safeguards into three —administrative, physical, and technical.
Implementing them is a must. Without this, you can’t demonstrate your company protects PHI properly or become HIPAA-compliant.
So let’s briefly discuss each.
Administrative safeguards
These safeguards are needed to:
- Train employees about PHI protections.
- Resolve security incidents that may threaten PHI.
- Protect PHI or ePHI during emergency situations.
Physical safeguards
These are safeguards to protect physical points of access to PHI. They outline how employees should manage their devices and workstations to keep sensitive health info secured. Company-wide, this safeguard enforces the use of surveillance technology and other measures for protecting physical access to PHI.
Technical safeguards
These are safeguards mandated to protect against unauthorized access or alteration to stored PHI or ePHI. Antivirus, data encryption, and multifactor authentication software are some common technical safeguard enforcement tools.
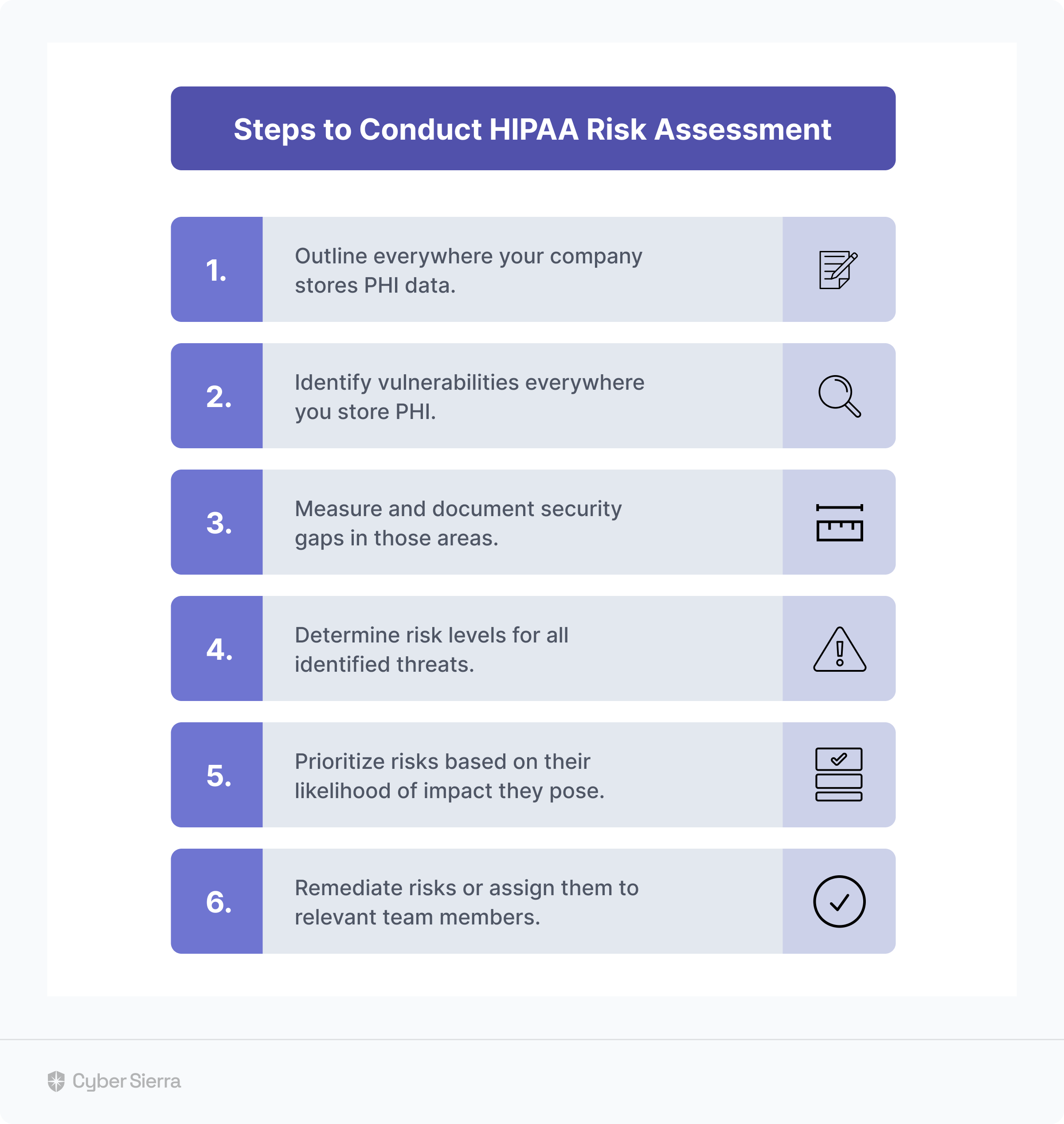
6. Conduct HIPAA Risk Assessments
This step of the HIPAA compliance process ensures the proper implementation of the HIPAA Security Rule safeguards —administrative, physical, and technical. It’s also how to identify vulnerabilities across your cloud and network environments.
Follow these steps to conduct a HIPAA risk assessment:

Again, doing all these manually can be daunting, if not impossible. But with an interoperable cybersecurity platform like Cyber Sierra, you can breeze through the steps above from one place.
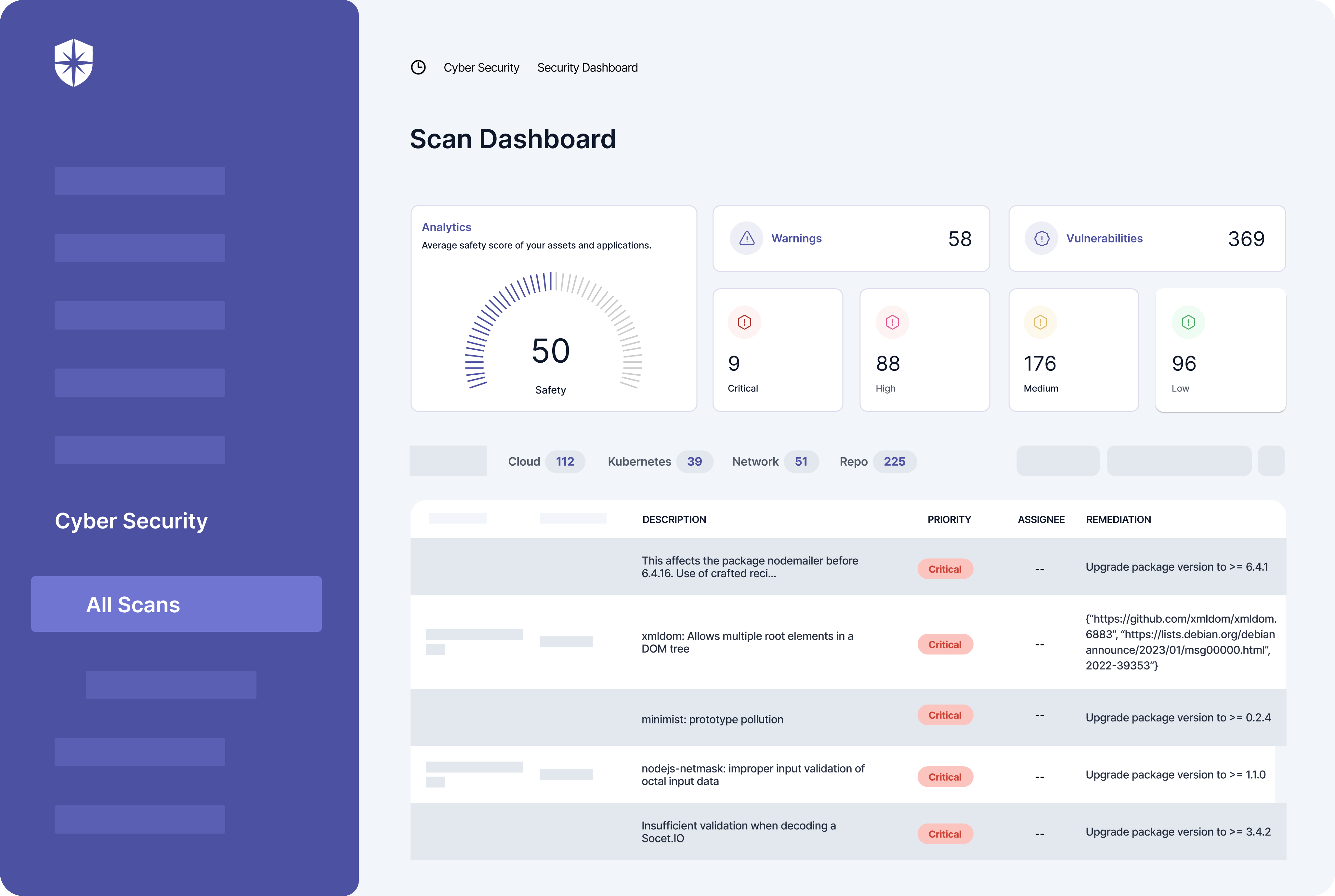
Connect your cloud assets, Kubernetes, repository, and network systems to Cyber Sierra, and our software will:
- Automatically scan all connected tools and assets.
- Detect risks and vulnerabilities to PHI data in real-time
- Prioritize critical risks based on their likely threat levels.
- Enable you to assign remediation tasks to members of your security team with tips on how they are to remediate risks:

7. Train Employees on HIPAA Risk Mitigation & Procedures
It takes a team to become HIPAA-compliant.
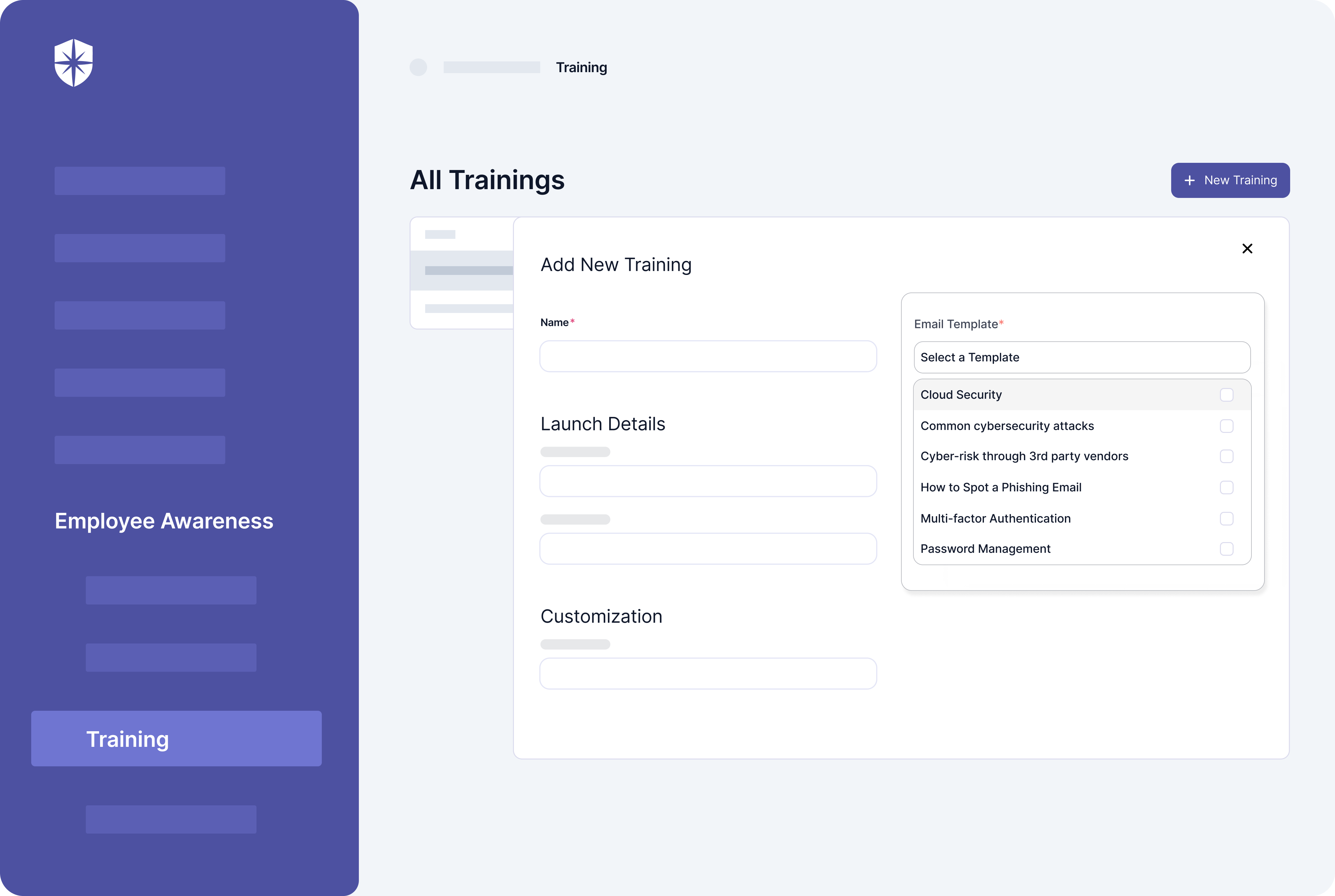
First, from implementing procedures to mitigating and remediating risks, you’re better off collaborating with a team of specialists. Also, any employee who accesses or handles PHI or ePHI is mandated to complete HIPAA compliance training. Both scenarios make training employees on HIPAA risk mitigation and procedures a necessity.
In short, the Department of Health and Human Services (HHS) recommends ongoing refresher training for all employees.
With other compliance automation software, ticking off this crucial step of the HIPAA process requires investing in a separate tool. But with Cyber Sierra, you can launch ongoing employee security training on HIPAA risk mitigation and procedures from the same place.
Here’s a peek:

8. Implement Continuous Monitoring of HIPAA Controls
If you think becoming HIPAA-compliant is tough, you’re right. However, staying HIPAA-compliant is even tougher.
That’s because the process doesn’t stop when you pass audit reviews and become HIPAA-compliant. Cybercriminals don’t care that you’re compliant. They are always devising new tricks to breach your systems and steal PHI data in your company’s possession.
And you’ll face violation penalties from the OCR and pay fines should they succeed, despite being HIPAA-compliant in the past.
To avoid this, continuously:
- Monitor HIPAA safeguards, controls and policy implementations
- Track if employees and business associates are monitoring safeguards and completing refresher risk-mitigation training.
- Detect, score, prioritize, and remediate emerging threats.
You can do all these with Cyber Sierra.
Take detecting and remediating threats as they emerge. Our Risk Register feature works round the clock to help you achieve this. It continuously scans and monitors all your connected cloud systems.
You get an always-updated dashboard with detected threats that have also been scored, and prioritized based on likelihood to cause havoc:
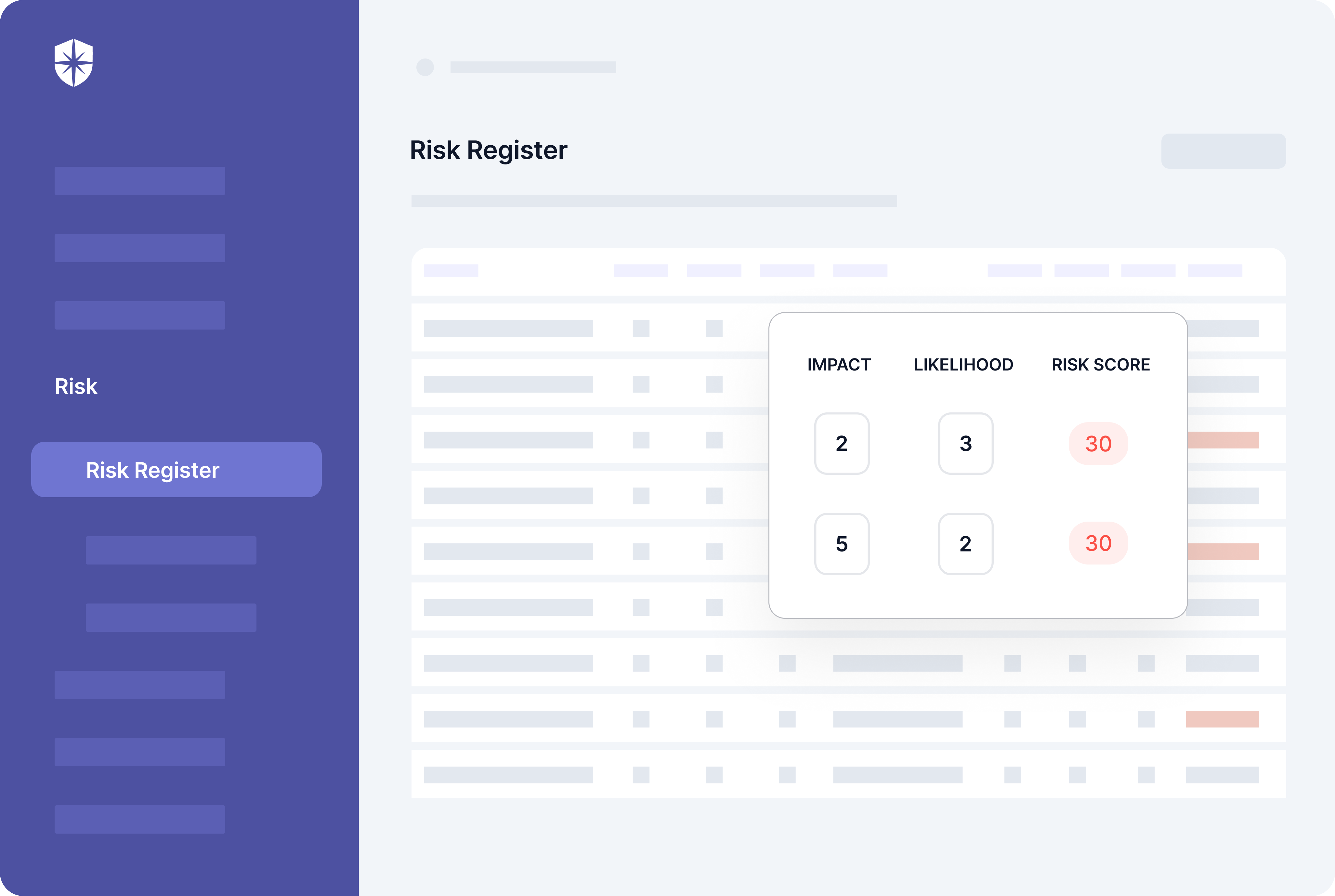

You also get steps for remediating each risk or assigning a remediation task to teammates. This way, you can continuously monitor HIPAA controls, mitigate risks, and stay HIPAA-compliant.
Automate HIPAA Compliance
HIPAA compliance can be overwhelming.
So if you end up with more unchecked boxes than checked ones, don’t panic. From creating policies, implementing HIPAA safeguards and controls, to conducting risk assessments, training employees, and continuous monitoring, there’s a lot to be managed.
Still, it goes beyond managing them to achieve initial compliance. HIPAA also requires organizations to maintain logs of their risk assessments, employee training, and other controls and compliance for a minimum of 6 years.
All of that is easier with an interoperable cybersecurity and compliance automation platform. By automating most processes needed, you can become (and stay) HIPAA-compliant.
That’s where software like Cyber Sierra comes in:



A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.