The Busy CTOs Checklist Guide to Automating GDPR Compliance





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
Look at this:
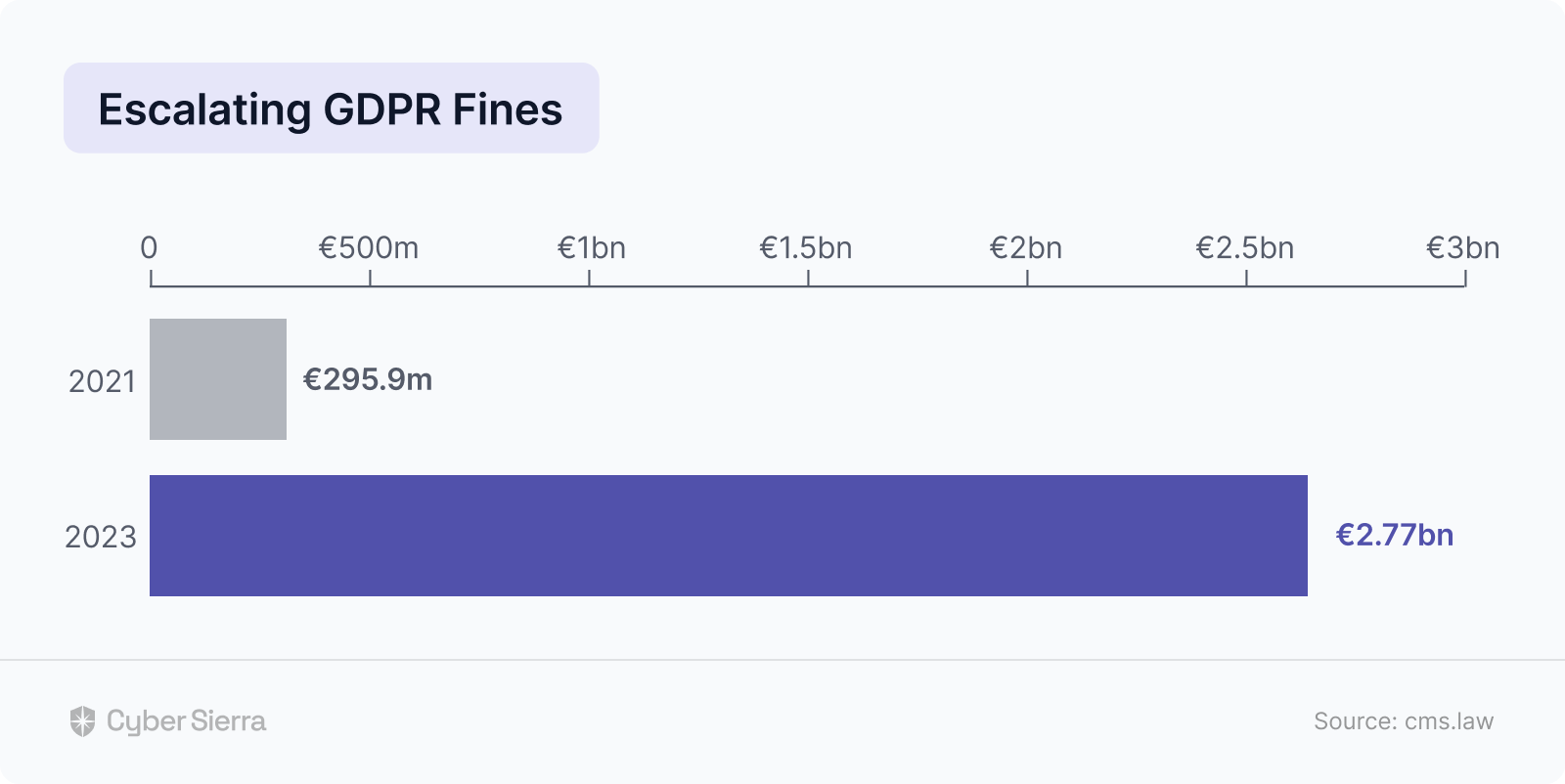


As shown, fines issued by the General Data Privacy Regulation (GDPR) are escalating. Notably, it leaped tenfold from €295.9 million in 2021 to over €2.77 billion as of February 2023.
At this rate, CTOs and IT executives must stay GDPR-compliant (even after initial compliance) to avoid getting fined. But achieving this requires automating the gruesome pre- and post-GDPR compliance processes.
You’ll see how to accomplish both in the ongoing GDPR compliance checklist explored below. Before we get there…
Start by Knowing the 7 GDPR Principles
Article 5.1-2 of the GDPR privacy law outlines seven protection and accountability principles organizations must adhere to when processing personal data.
As captured below:
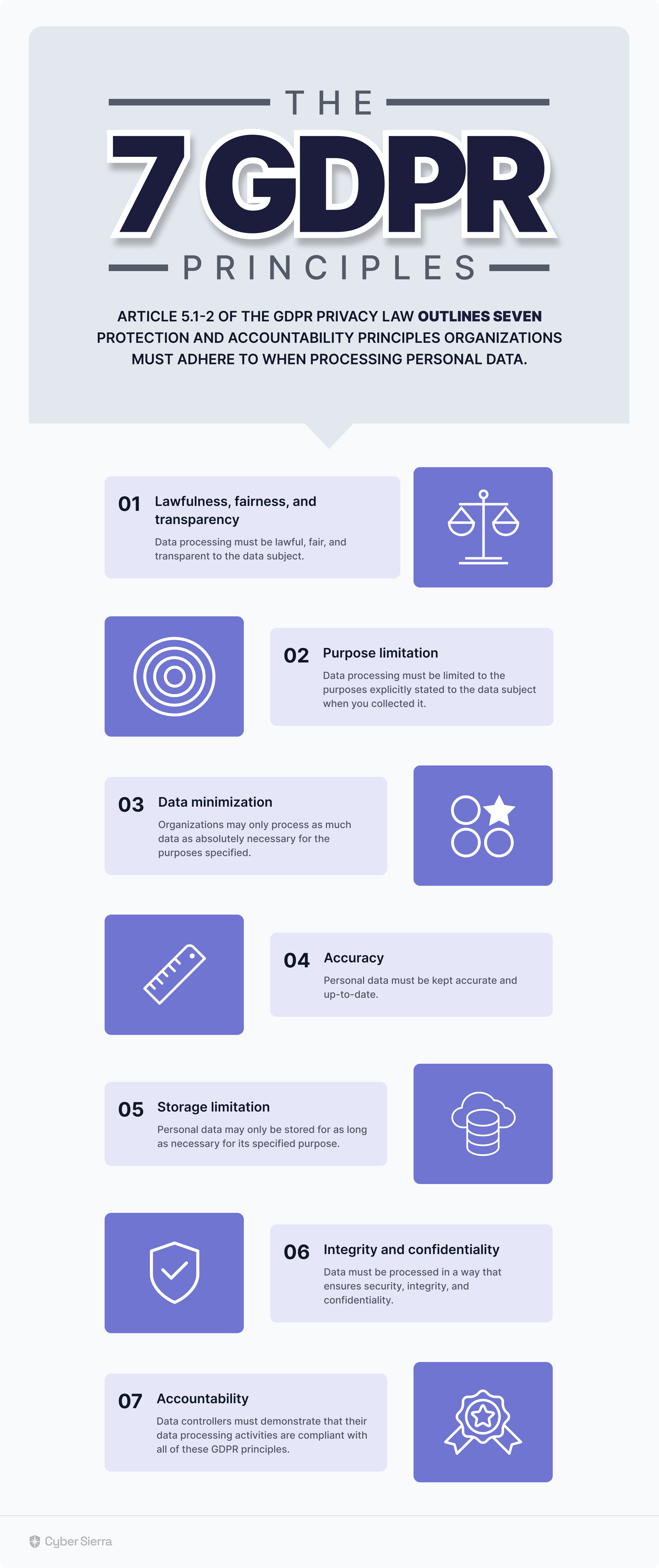

Continuous adherence to all principles outlined above is how you become (and stay) GDPR-compliant. Unfortunately, it’s easier said because implementing their requirements leaves a lot to interpretation.
CSO’s Micheal Nadeau corroborates:


To emphasize, fines for non-compliance could be as high as €20 million or 4% of your company’s global revenue. So to close every leeway that could lead to one, comprehensive and continuous implementation of GDPR principles is crucial.
Our 10-step checklist guide details how to do that. As we proceed, you’ll also see how Cyber Sierra automates crucial processes involved.
Download the checklist to follow along:
The 10-Step Ongoing GDPR Compliance Checklist
Does GDPR, an EU law, even apply to you?
Organizations outside of Europe might ask this question. So before jumping into the checklist, here’s to re-clarify who must comply with the General Data Protection Regulation (GDPR):
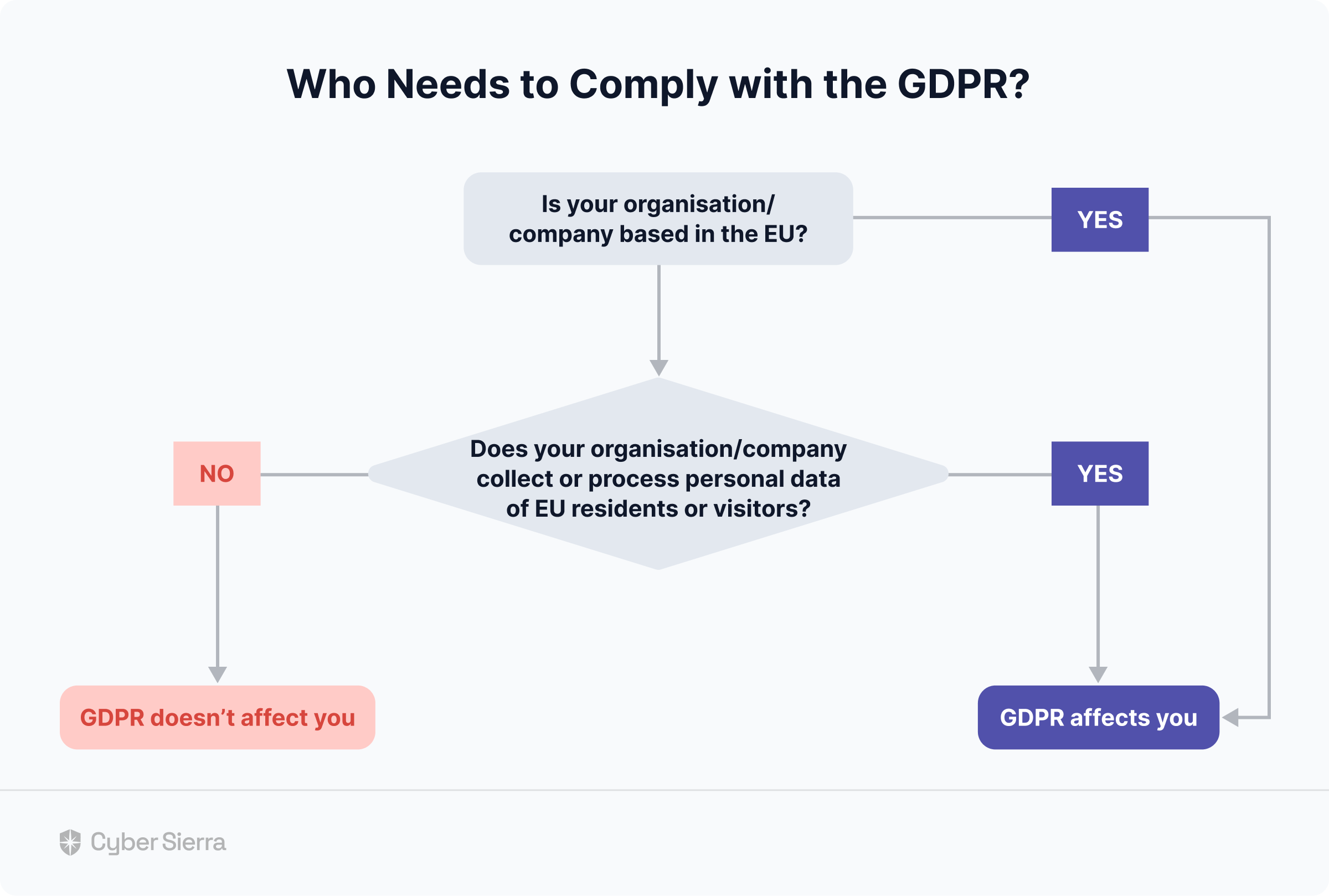

Explaining further, the GDPR’s official site notes:


And now, the GDPR Cyber security checklist guide.
1. Map All Collected & Processed Data
The first step for becoming compliant with GDPR is taking a holistic inventory of all the data your company collects or processes.
Three things you should do here are:
- Identify all databases, applications, networks, etc., within your organization.
- Document all collected, processed, and stored personally identifiable information (PII) in those mapped systems.
- Outline who has access to each mapped data (i.e., employees or third-party vendors, partners, etc.)
These actions create a birds-eye view of all personal data your company collects, stores, or processes. Matt Fisher, an IT thought leader, shared why this first step is crucial for simplifying the entire project of becoming GDPR-compliant.
In his words:


2. Document Justification for Data Processing
Collecting, storing, or processing personal data is illegal under the GDPR law. Therefore, all companies must justify why they are doing so, subject to one or more conditions listed in GDPR’s Article 6.
So as a 2nd step, create a process that documents your company’s justification for processing personal data. This should include a lawful basis for processing data approved by the GDPR such as:
- Consent given by the data subject, where the data subject is the owner of the data.
- Contract entered with the data subject.
- Necessary for fulfilling a legal obligation.
- Necessary for protecting the interests of the data subject or an associated third party.
- Necessary for legitimate purposes pursued by the data controller (i.e., the organization collecting data) or associated third parties.
Next, add a consent box to all forms and switch to double opt-ins to ensure you only collect data with expressed consent. Then, create (or recreate) and publish your company’s privacy policy. In it, provide clear information on how you process data and justify why.
According to the GDPR’s official site:


3. Perform Data Protection Impact Assessment (DPIA)
A data protection impact assessment uncovers how your product could jeopardize the personal data your company collects, stores, or processes. This step also helps you identify risks associated with personal data being processed.
Consider using a cybersecurity suite to effortlessly achieve both. Fortunately, this is one area where the Cyber Sierra interoperable cybersecurity and gdpr compliance automation platform comes in.
For instance, connect your cloud assets, network systems, etc., and our cybersecurity suite will scan everywhere your company collects, stores, or processes data.
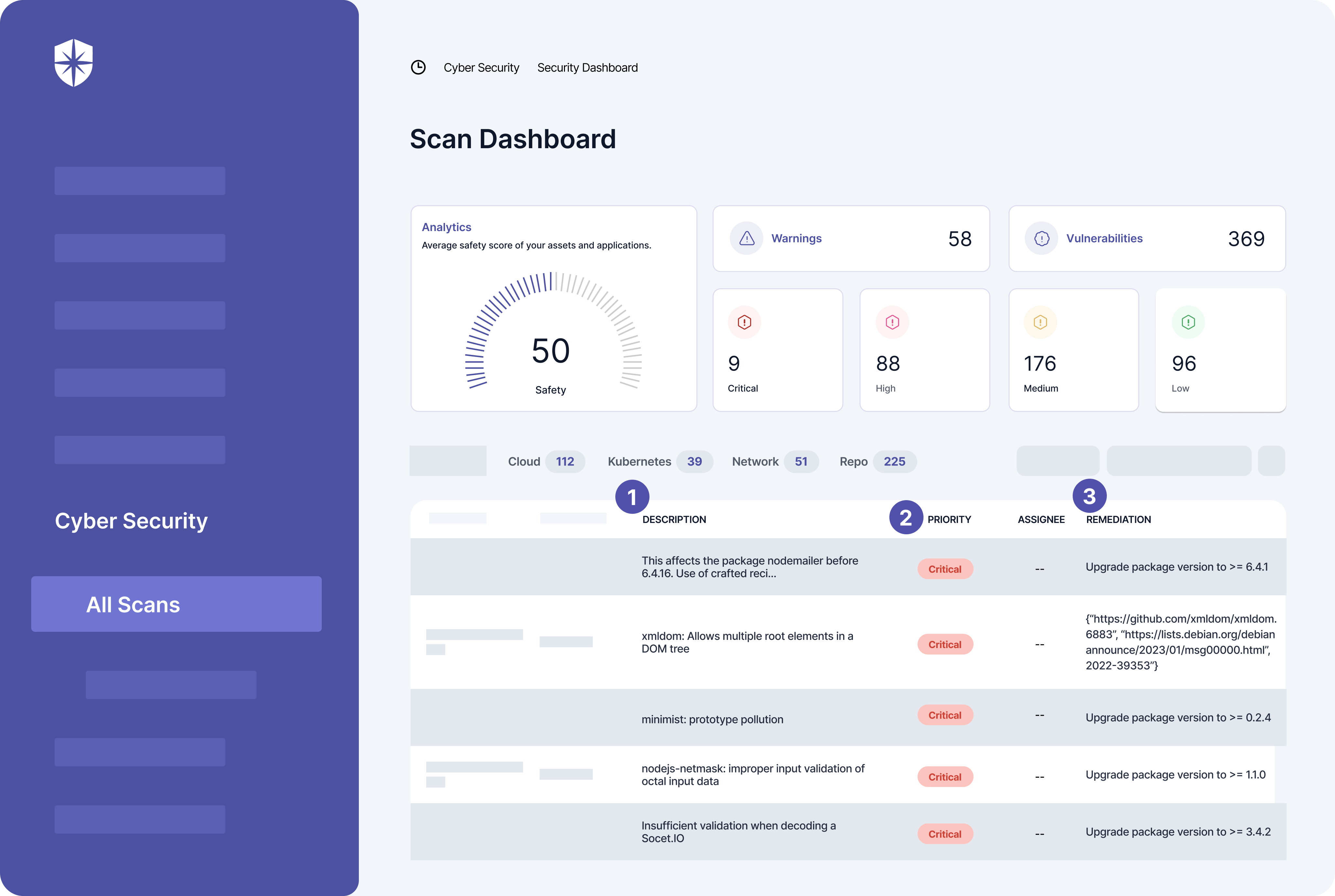
You get a Scan Dashboard with:
- Descriptions of all identified risks and vulnerabilities across everywhere your company collects, stores, or processes data.
- Critical risks to personal data identified and prioritized.
- Ability to assign identified threats to teammates with summarized remediation tips for mitigating risks:

4. Appoint a Data Protection Officer (DPO)
If the steps above look overwhelming, it’s because they are.
Hence, this official statement:


In addition to overseeing the steps up to this point, a DPO eases you of responsibilities outlined by the GDPR law.
Some crucial ones are:
- Respond to comments and questions from data subjects related to how your company processes their personal data.
- Cooperate with the data protection supervisory authority and inform executives and employees of their GDPR obligations.
- Continuously monitor your organization’s GDPR processes and maintain documentation to prove compliance.
- Train employees on compliance and perform ongoing audits.
Before we proceed…
Imagine your appointed data protection officer (or maybe, you) could continuously monitor your company’s GDPR compliance and train employees from one place. As you’ll soon see, you can do both with Cyber Sierra’s cybersecurity and compliance automation platform.
5. Launch Ongoing Employee Awareness Training
Punit Bhatia, author of ‘Be Ready for GDPR,’ advised:


Punit is spot on because, as you can imagine, implementing and maintaining the GDPR law is complex. Therefore, regular data privacy training is needed to help employees handle personal data securely.
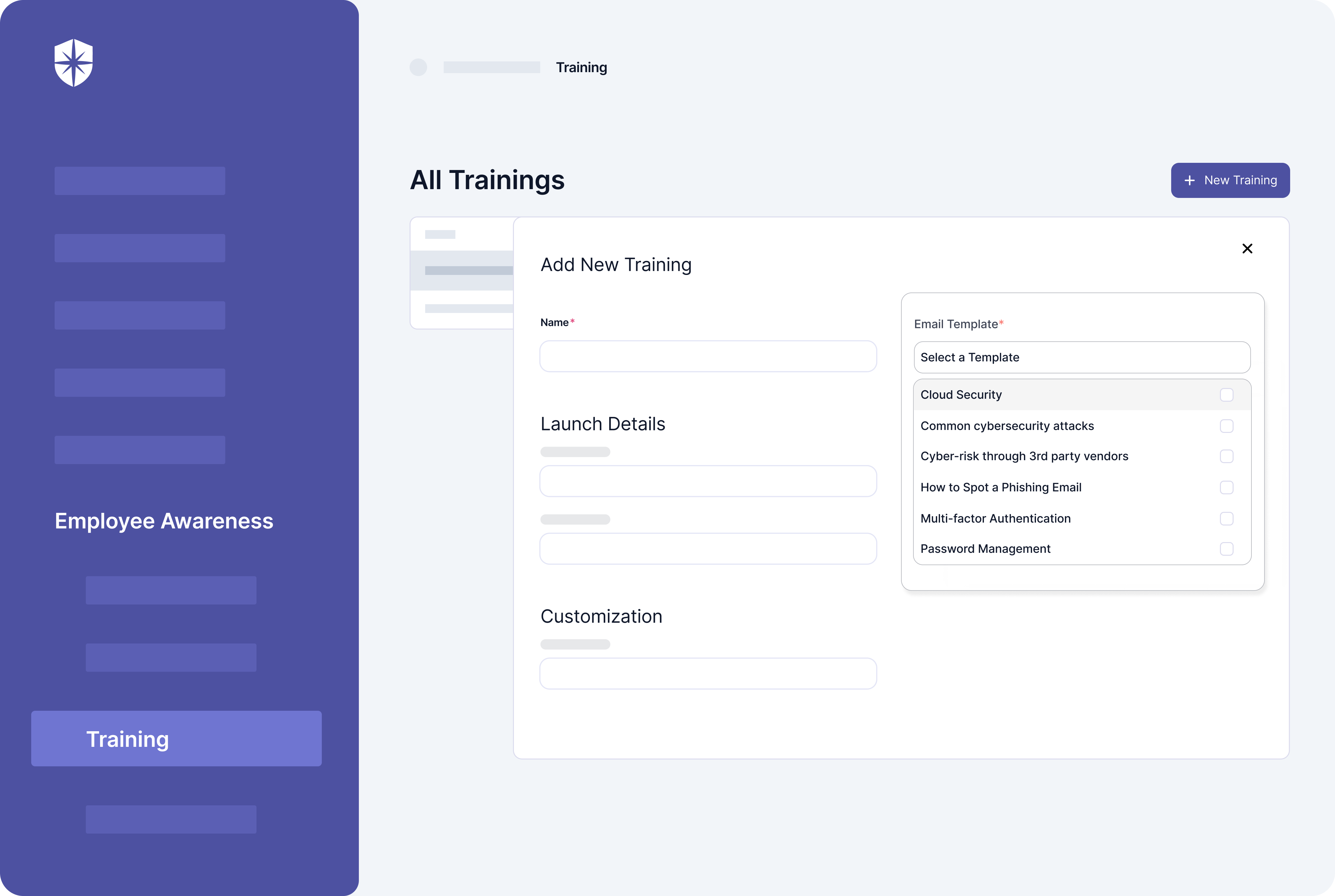
Ticking off this crucial step of the GDPR compliance process is easy with Cyber Sierra. You can launch, track completion, and manage ongoing employee security training necessary for implementing GDPR procedures and staying compliant from the same place.
Here’s a peek:

6. Implement Company-wide Safeguards
Companies are mandated to establish ‘appropriate technical and organizational measures,’ ensuring all processed customer data is properly secured. The GDPR doesn’t specify what safeguards must be implemented, allowing organizations to implement those relevant to their business needs.
However, crucial safeguards to consider are:
- Multifactor authentication for employees and customers
- Data encryption for all processed data
- User access controls to monitor unauthorized accesses.
7. Enforce the Security of Data Transfers
To become compliant with GDPR, ensure that all personal data shared between your company, partners, and third parties is adequately transferred and secured.
Enforcing this requires:
- Putting unavoidable technical controls (i.e., implementing data security measures) in place.
- Having company-wide controls (i.e., implementing data governance measures) to guide employees handling data.
- Creating Data Processing Agreements (DPA) with contractual clauses mandating third-party vendors to secure shared data.
8. Assess and Manage Third-Party Vendor Risks
Risks to personal data from third-party vendors aren’t left out of the GDPR compliance equation. In short, it is mandated for organizations to regularly assess and manage 3rd-party vendor risks.
So to ensure third-parties don’t sabotage your efforts toward becoming (and staying) GDPR-compliant, you must:
- Conduct a thorough evaluation of the risk associated with every vendor within your organization’s ecosystem.
- Have standard security questionnaires 3rd-party vendors must complete to prove compliance with data handling.
- Implement measures for identifying and remediating third-party vendor risks swiftly.
Our tool makes these processes more efficient.
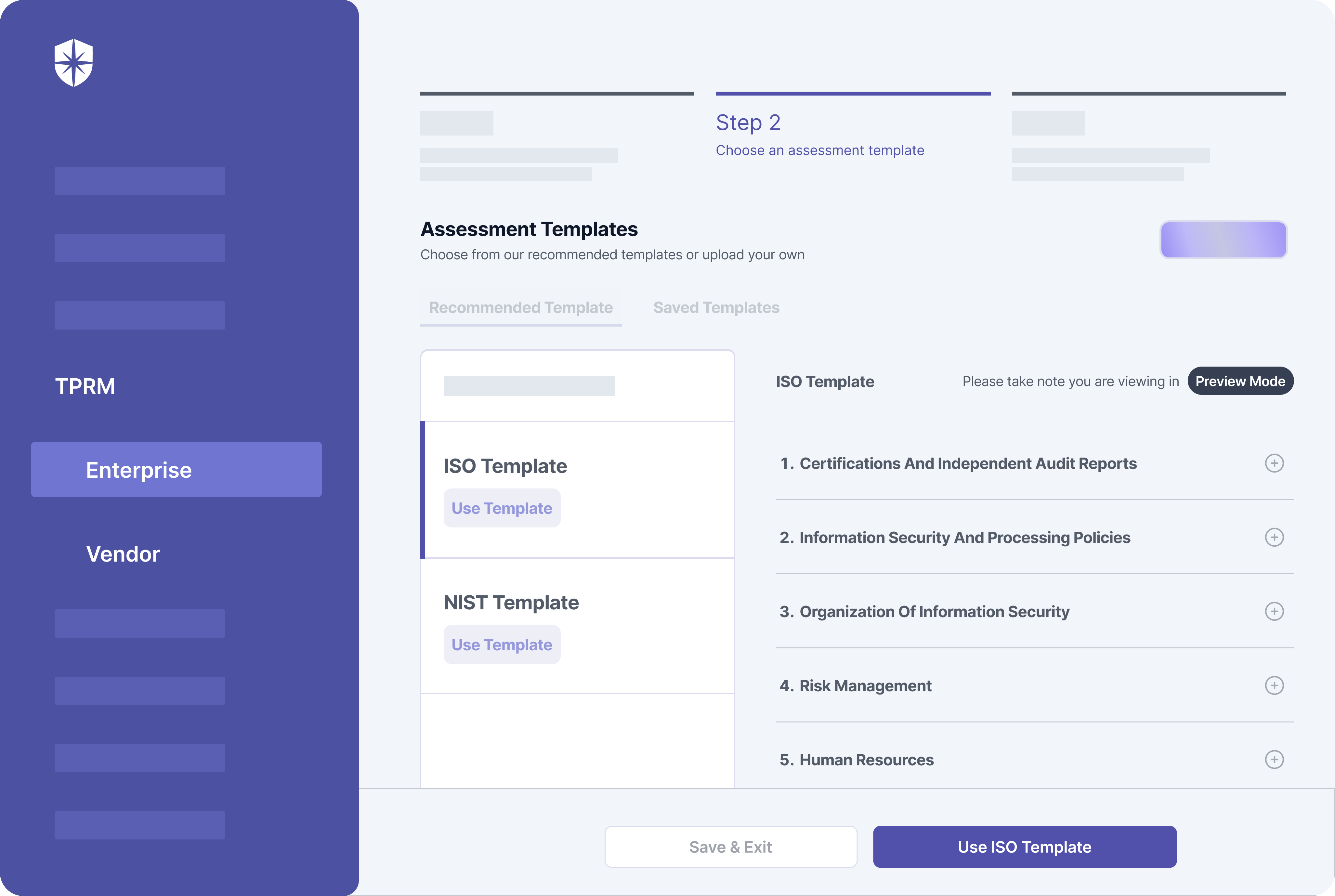
For instance, you can easily add vendors to our Assessments suite. And when doing so, choose from our prebuilt risk assessment templates and share it with your vendors to prove their compliance with handling personal data.
You can manage everything from one dashboard:

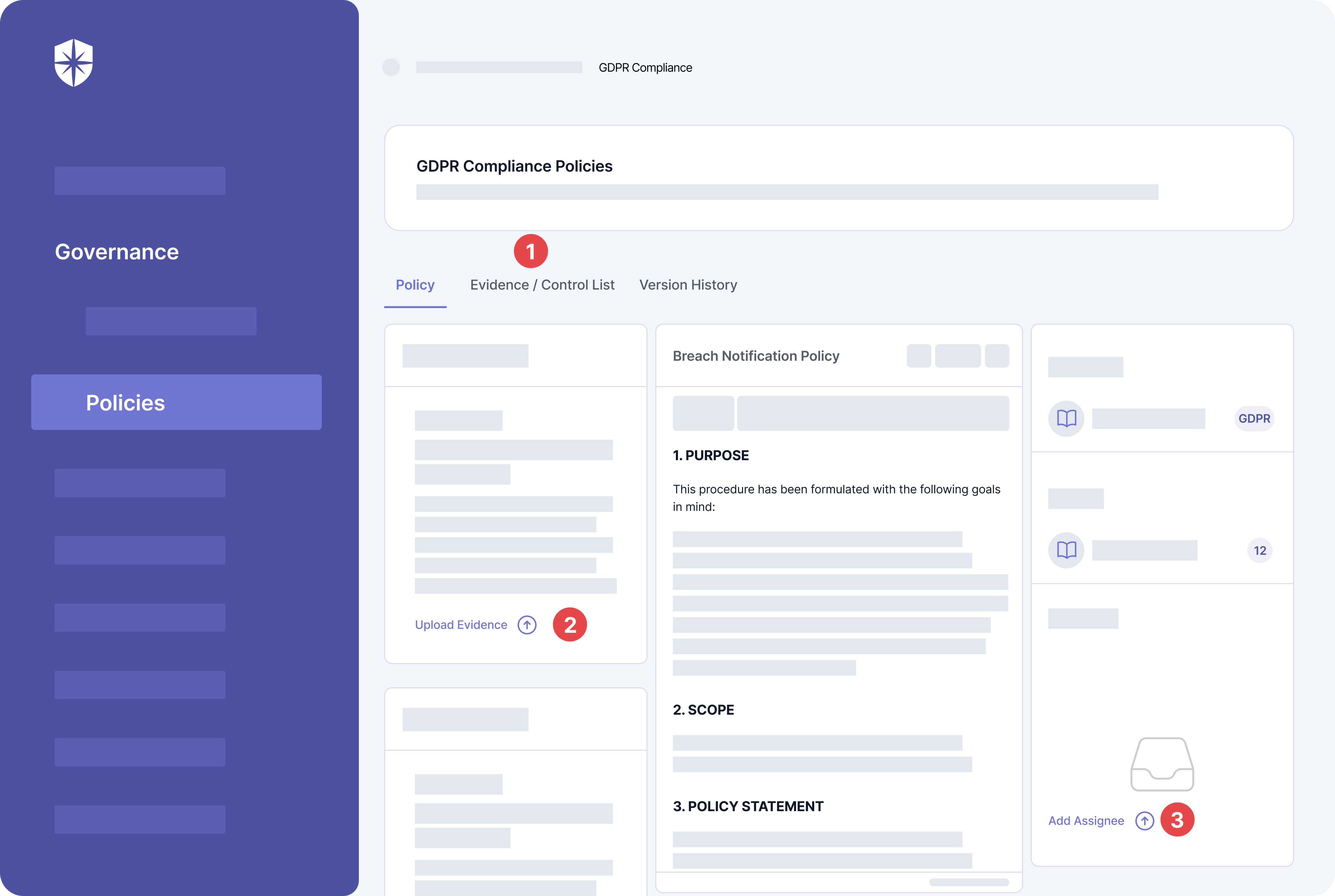
9. Create Breach Notification Policies
As cybercrime evolves, unauthorized access to personal data you control or process can still happen despite your company’s best effort.
In case it does:
- How will your company’s security team handle it?
- Specifically, who on the security team will handle it?
- How will you monitor against such events and swiftly remediate them when they happen?
Creating and implementing breach notification procedures and policies addresses these concerns. And they are a mandatory requirement for becoming (and staying) GDPR-compliant.
Specifically, the EU GDPR mandates that all breaches be reported less than 72 hours after they occur. Data processors must report to data controllers. Data controllers, in turn, must report to a supervisory authority, often called the Data Protection Association.
You can also create, assign, and manage these essential GDPR policies and procedures with the Cyber Sierra compliance automation suite:

10. Implement Continuous Monitoring of GDPR Controls
Becoming GDPR-compliant is tough.
But staying compliant is even tougher.
And that’s because the process isn’t a one-time affair. Cybercriminals are endlessly on the hunt for new ways to breach the personal data you control or process. This explains why non-compliance fines continue to escalate, jumping tenfold from two years ago:



To avoid this, continuously:
- Monitor GDPR safeguards, controls and policy implementations
- Train employees on emerging risks relevant to GDPR compliance
- Track if employees and third-party vendors are monitoring safeguards and properly securing personal data they handle
- Detect, score, prioritize, and remediate emerging data risks.
You can do all these with Cyber Sierra.
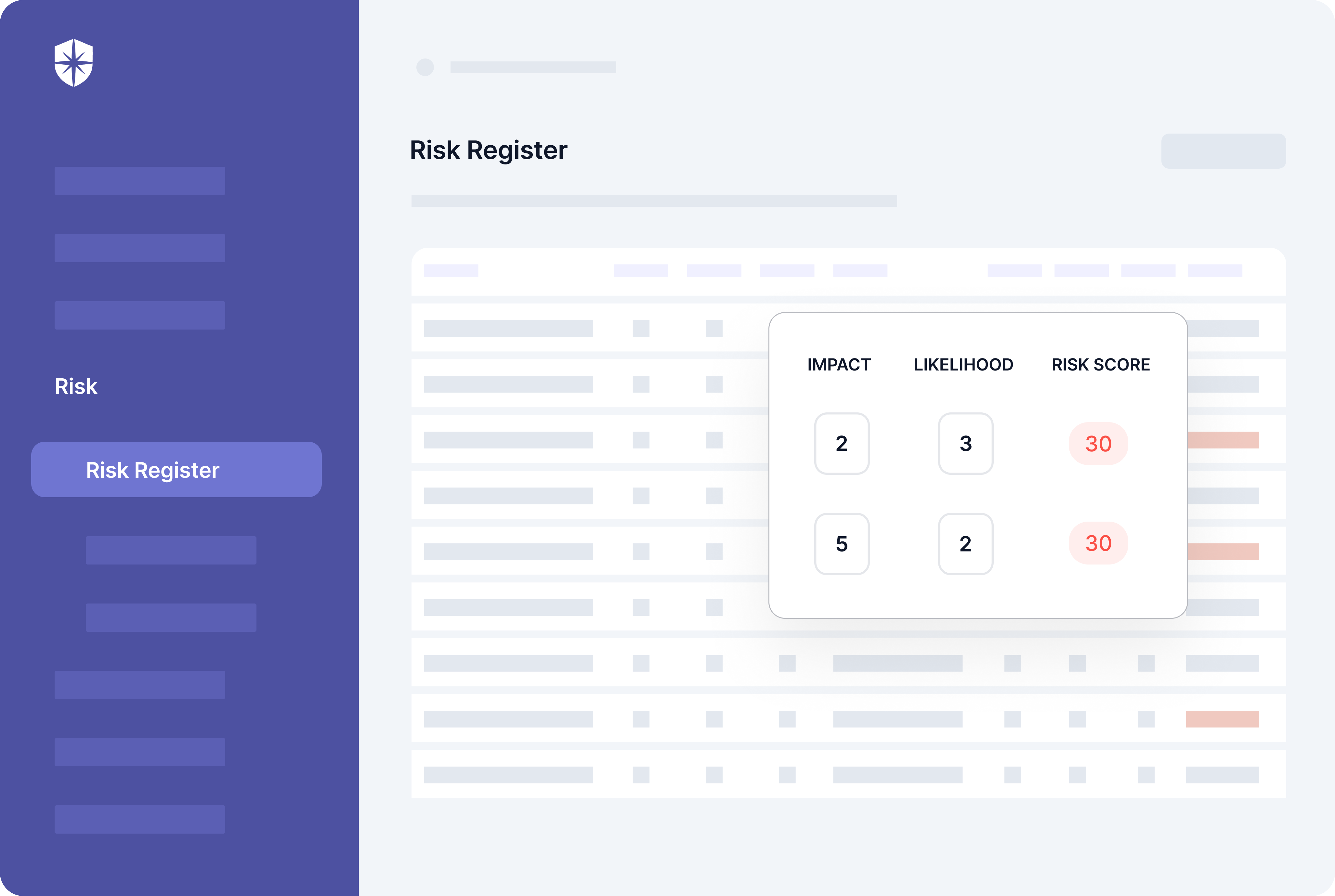
Take detecting and remediating risks as they emerge. Our Risk Register feature handles both effectively and efficiently. It can continuously scan and monitor all your connected cloud systems.
You get an always-updated dashboard with detected risks scored and prioritized based on likelihood to cause a data breach:




A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.