CISOs Are Using This To Automate Third-Party Vendor Assessments





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
Gartner polled enterprise compliance and legal execs.
As you may guess, due to growing concerns, one of the survey questions was to uncover risks from 3rd-party vendors. What the study found? Rethinking vendor assessments has become increasingly crucial.
According to the report:
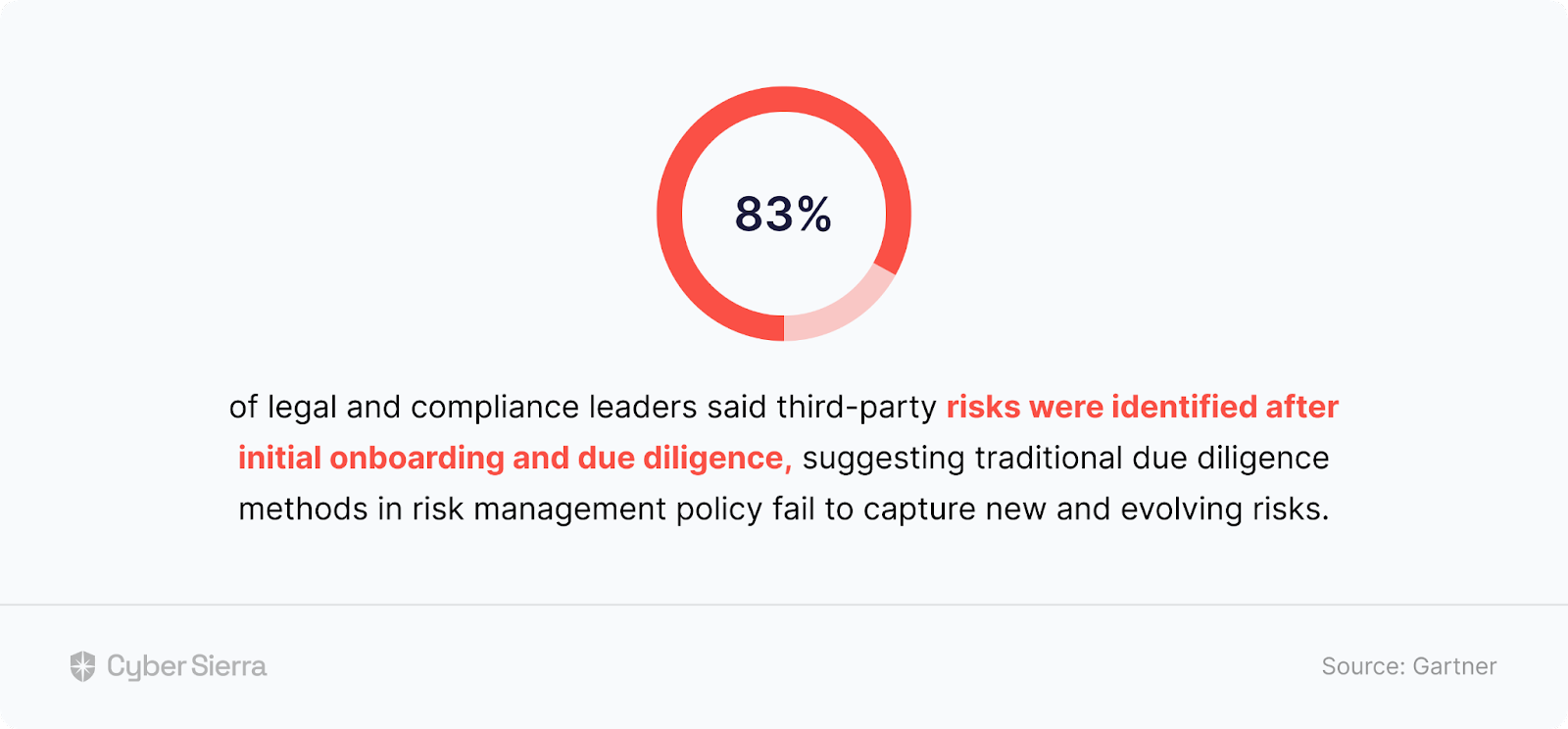

CISOs and enterprise security managers must take this finding seriously as it tells a crucial story. What story does it tell, relative to third-party vendor risk management (TPRM), you ask?
Well, the answer is straightforward:
One-Time Assessments Don’t Mitigate Vendor Risks
And it makes sense.
You can create a well-detailed security questionnaire that properly assesses vendors before joining your organization’s supply chain network. But detailed as your questionnaire might be, they don’t guarantee the detection and prompt mitigation of new risks after vendors get the nod.
In short, they don’t guarantee that vendors who went the extra mile to pass your initial checks and win your company’s business are honest. Dustin Bailey, Fmr. Security Lead at Twilio, hammered on this.
In his words:


This poses an apt question: How should proactive enterprise security executives like yourself approach vendor risk assessments today?
I’ll answer this question by showing you how to go beyond one-time questionnaires for vendor assessments. Disclaimer: Our interoperable cybersecurity and compliance automation platform, Cyber Sierra, makes it possible and also streamlines the process.
Before we dive in…
How Should Vendor Risk Assessments Be Done?
It should be ongoing.
And the reasons are simple. First, CISOs can no longer afford to assess vendors once, no matter how detailed the security questionnaires used are, and go to sleep. Second, a BlueVoyant survey of top executives globally responsible for cybersecurity in their organizations supports this.
The study saw a whopping 93% of respondents say they suffered breaches due to weaknesses in their supply chains. Considering breaches in supply chains are usually from third-party vendors, the study uncovered even more troubling data.
These breaches are getting worse:
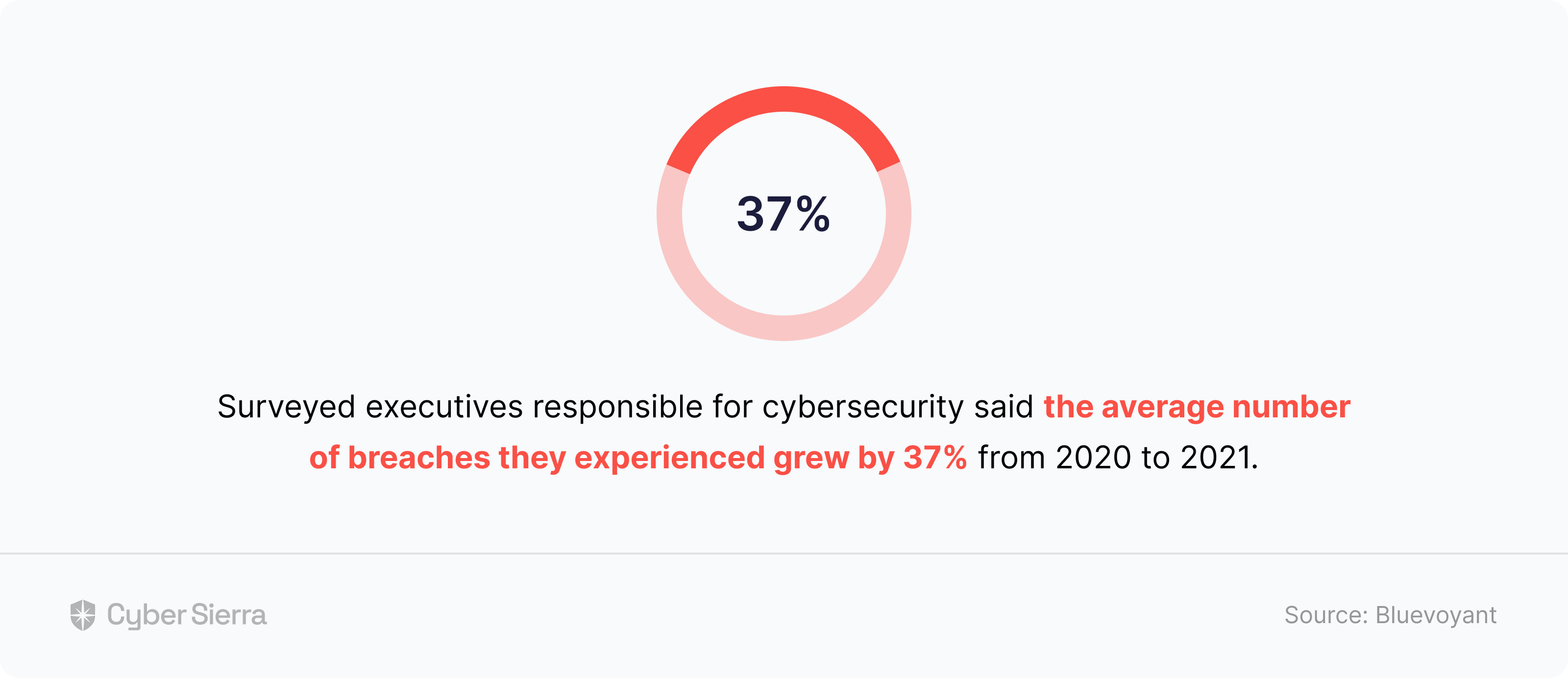

Based on this trend, here’s how we recommend going beyond one-time assessments to mitigate as much vendor risk as possible.
1. Categorize Vendors Based On Risk Level
The more access to your organization’s critical cloud and network environments a vendor has, the more they are likely to increase your risk surface area. The same goes for vendors who will rely on other vendors (4th parties) to fulfill their duties to your company.
But it doesn’t end there.
The type of solution a 3rd party brings to your company and their geographic location also matters. For instance, companies located in jurisdictions with weak compliance regulations are less likely to have security measures in place. All this creates the need to categorize and prioritize vendors your team must pay constant attention to.
Our recommendation?
Do this the moment you want to start assessing them.
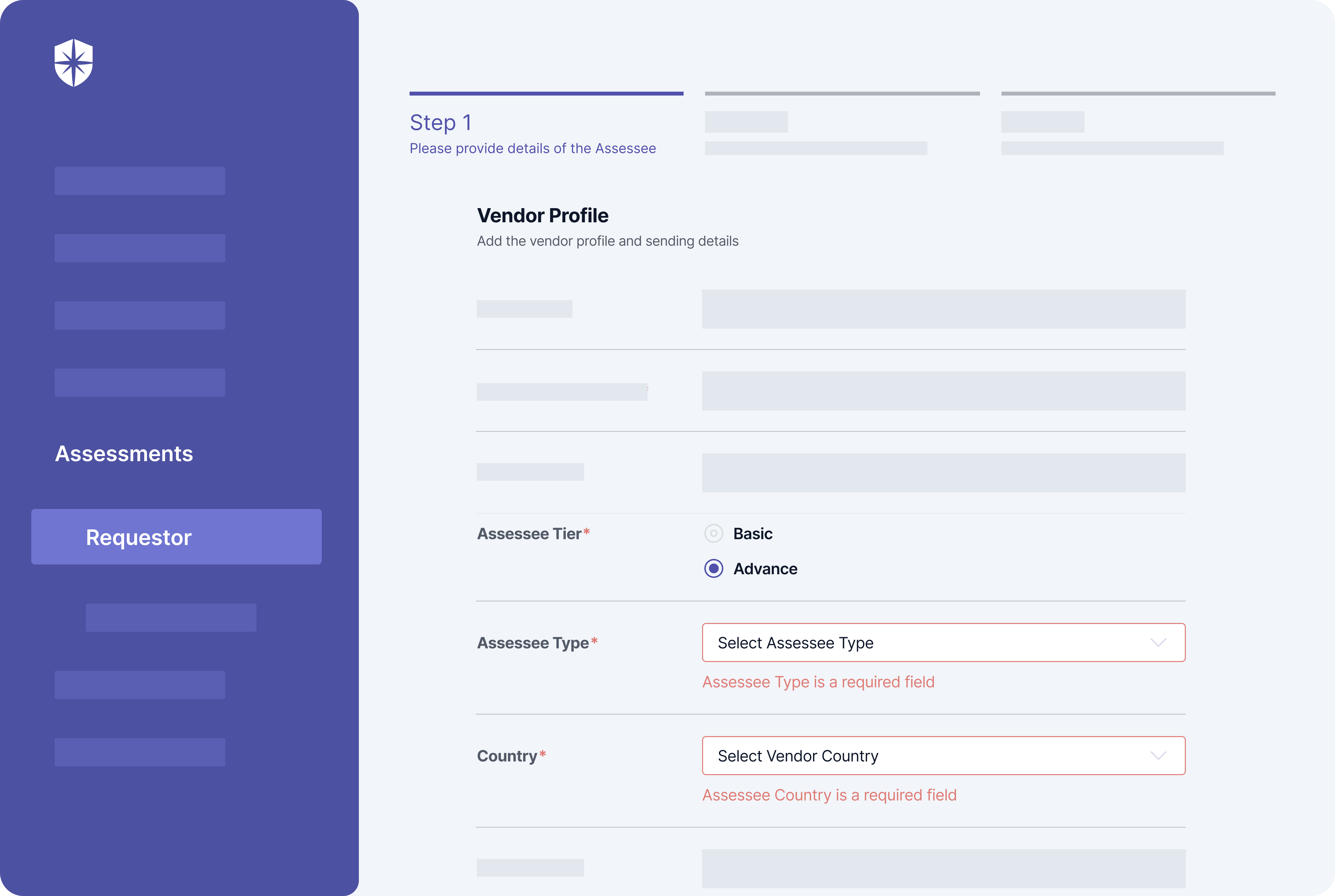
With Cyber Sierra, for instance, your security team is prompted to categorize vendors based on the criteria above from the get-go. You can easily profile vendors when initiating an assessment by:
- Indicating if an advanced assessment is needed
- Choosing an assessee type (service, software, etc.)
- Selecting the third-party vendor’s country of location:

2. Automate Uncovering Vendors Who Fail Assessments
Does this look familiar?
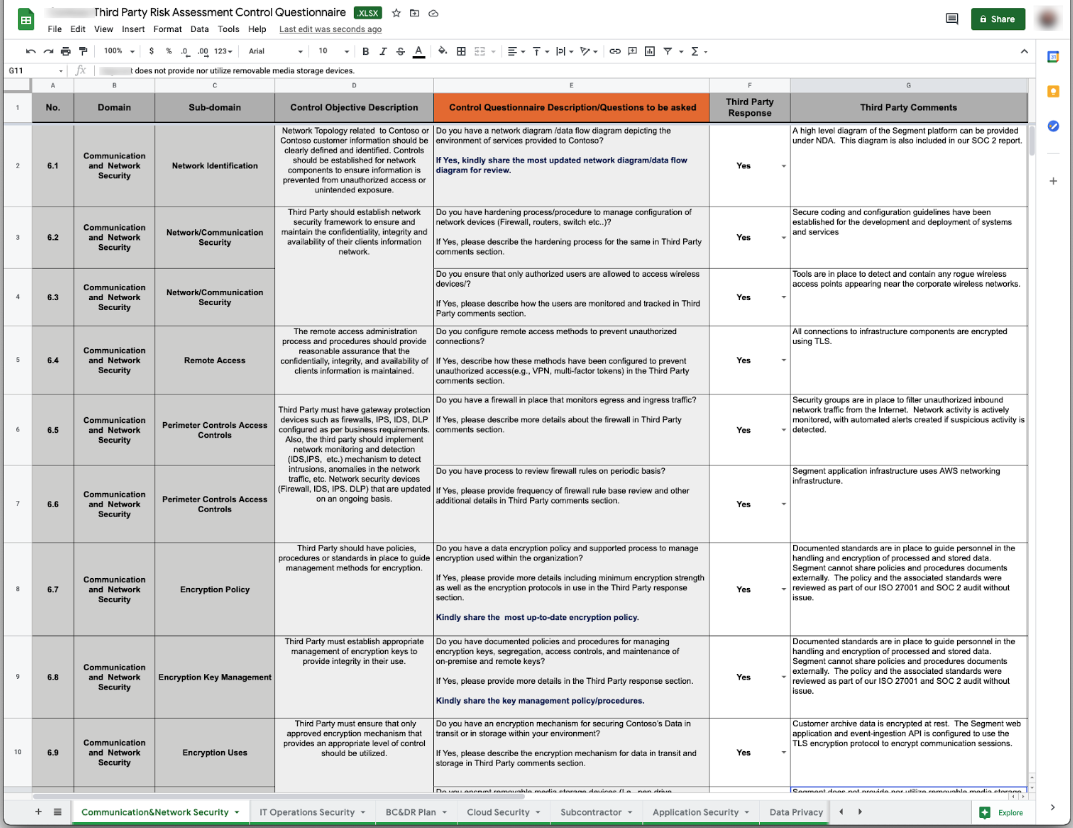

You know the drill. Send assessment questionnaires to vendors in spreadsheets, have a yes/no answer column, yet still go back and forth, chasing them to send evidence of controls.
Do it for just a couple dozens of vendors, and you risk:
- Delaying the approval of compliant vendors who could be driving the business forward
- Losing important files in the maze of too much back and forth
- Approving vendors mistakenly whose security controls evidence aren’t verified.
Automating vendor assessments with Cyber Sierra helps mitigate these risks effectively. Our platform streamlines the entire process by allowing vendors to answer security questions and upload evidence for the same in one place, instead of using spreadsheets.
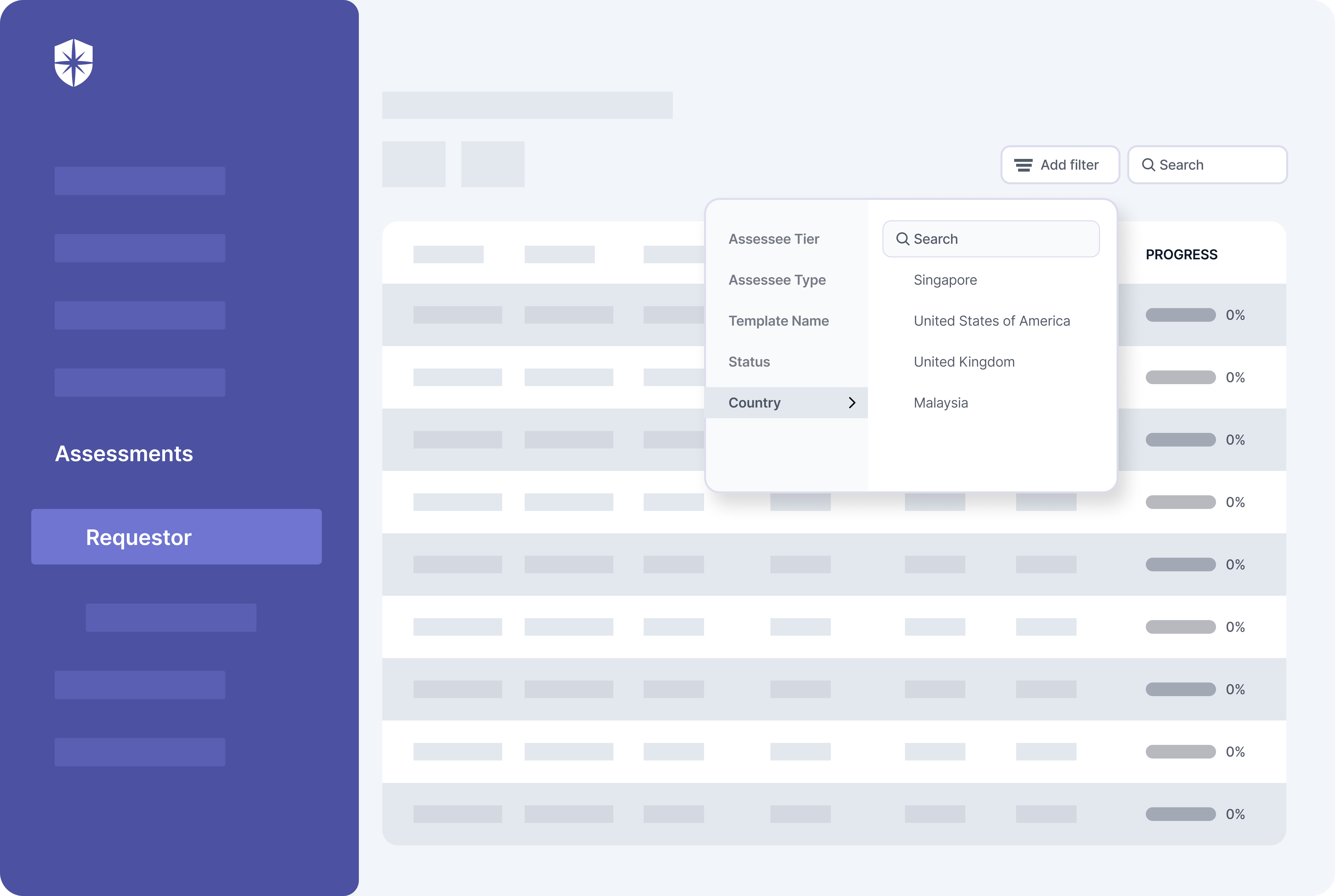
Your security team can filter or search vendors based on various criteria used to profile them. And you can see their progress in uploading evidence for assessment questionnaires in one view:

3. Enforce Ongoing Vendor Risk Assessments
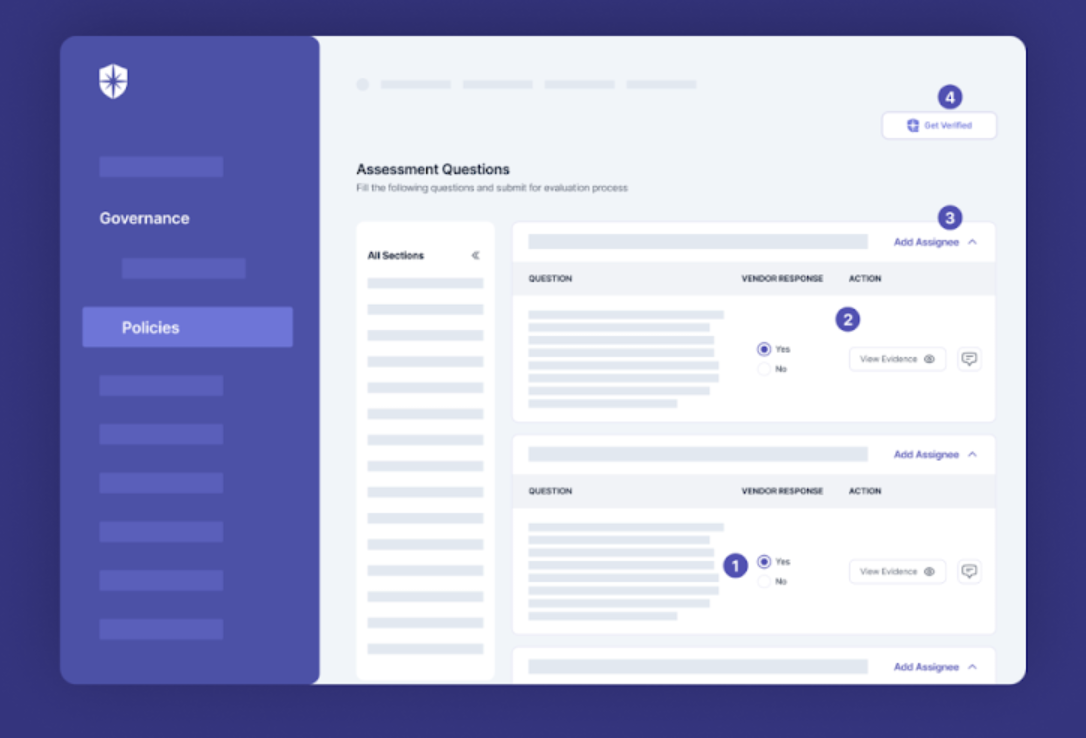
Send assessments to 3rd parties with Cyber Sierra, and they’ll receive an email with instructions on how to complete your questionnaires. But instead of just ticking yes/no to security questions, your team can enforce uploading evidence for their answers.
Here’s a peek into a vendor’s view:
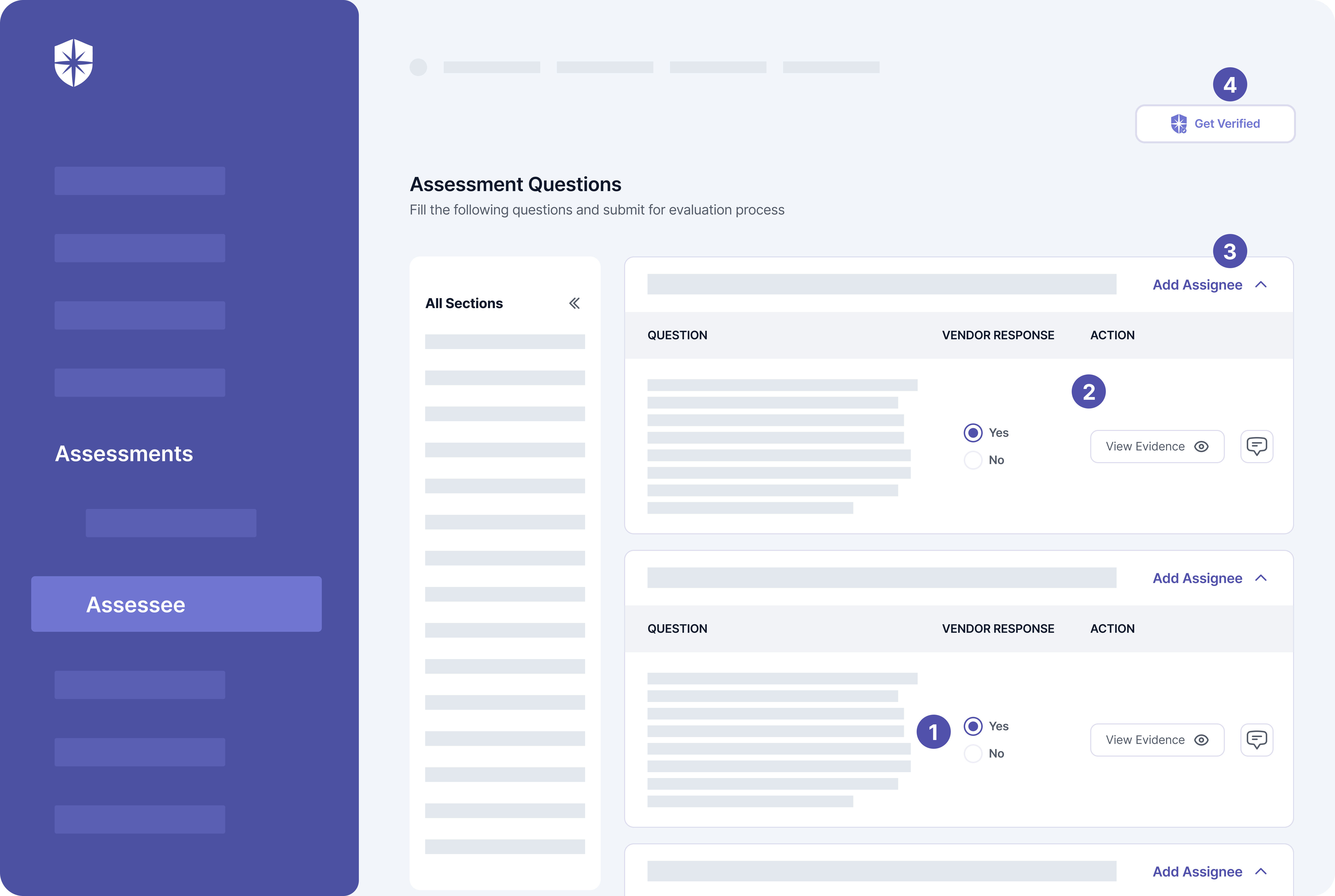

As shown above, they can:
- Answer security questions in one click.
- Upload evidence for each question answered and leave comments for your security team (your team can respond, too).
- Assign their teammates to answer questions or upload evidence.
- And more importantly, get uploaded evidence auto-verified by clicking on “Get Verified.”
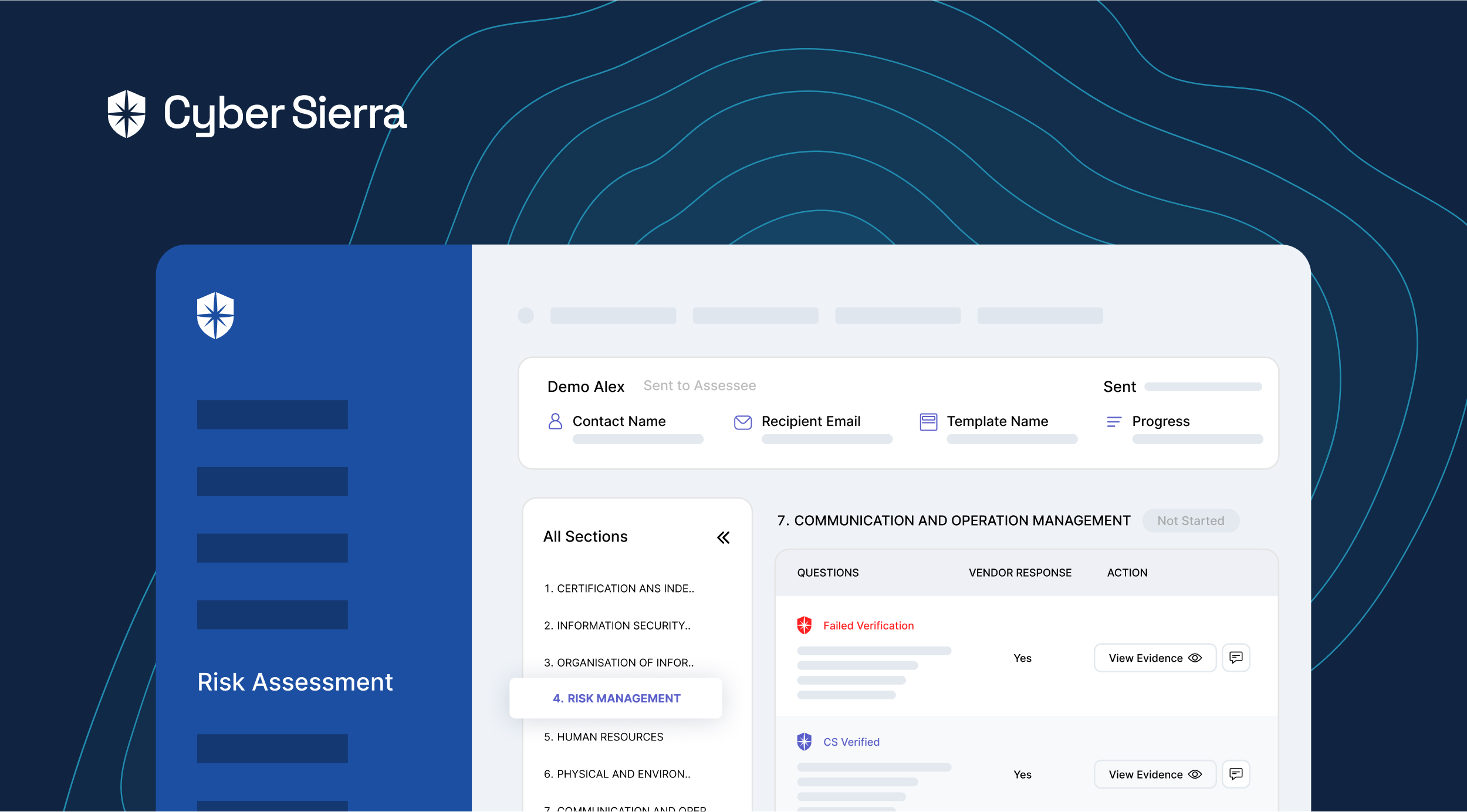
On your team’s side, Cyber Sierra enables continuous risk assessments through two effective approaches. First, our platform automatically verifies uploaded evidence and flags unverified ones:
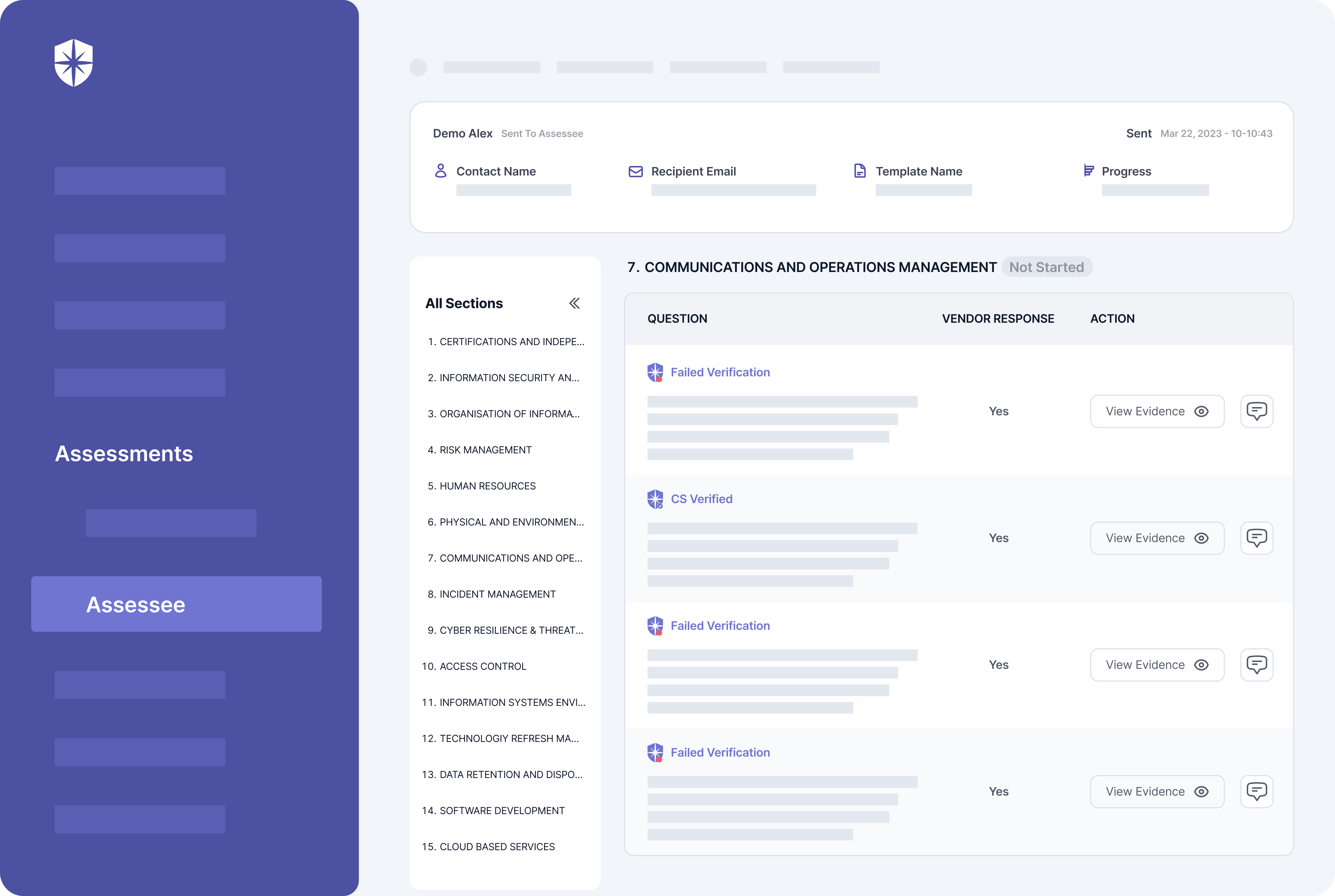

Second, you can mandate vendors to click on the “Get Verified” button, say monthly, and it triggers an auto-verification process in the background. This way, you can even enforce ongoing assessments.
To see all this in action:
Do I Still Need Vendor Risk Assessment Questionnaire Templates?
A recent article in CSO Online by Andy Ellis, Advisory CISO at Orca Security, lays the foundation for answering this question.
Andy wrote:


In other words, vendor risk assessment questionnaire templates still have a place. However, simply adding more questions to templates and scoring vendor risks based on their answers is insufficient. As Andy observed, it won’t help your team understand the actual risks 3rd parties pose to your organization.
We recommend the following.
Begin the process by using appropriate security questionnaire templates. But don’t rely on them blindly. Instead, select questions relevant to a specific vendor and focus on getting them to upload verifiable evidence of having crucial security controls.
Cyber Sierra simplifies the process of doing this. Your team can choose from our prebuilt assessment questionnaire templates (or upload any custom one). More importantly, when doing so, you can select specific questions a vendor must answer and upload evidence:
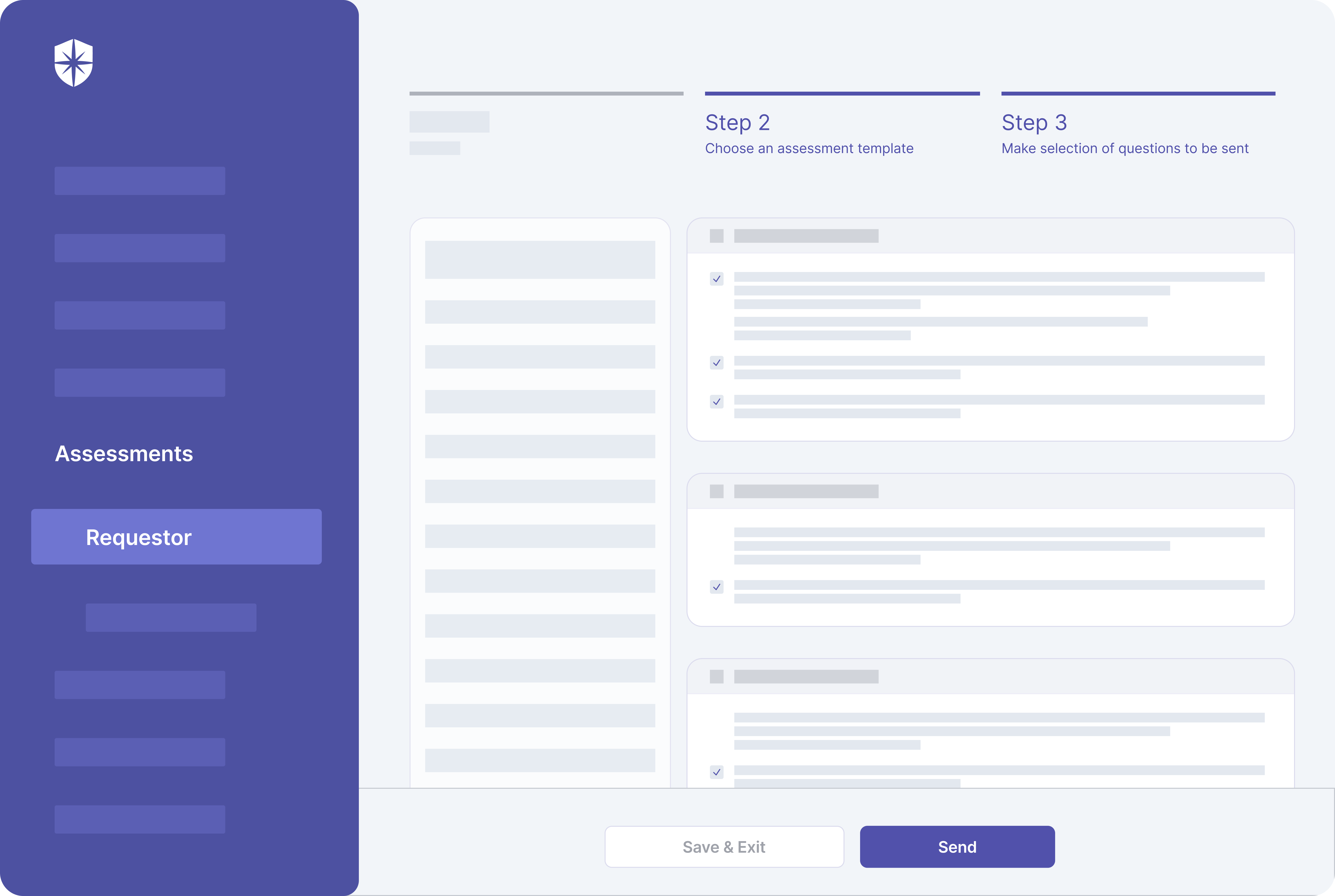

Streamline Vendor Risk Assessments
Managing third-party risks is a necessity.
The only other way around it is to do away with vendors completely. But this isn’t possible, as your organization also needs them to extend its capabilities and stay competitive. In short, effective and efficient third-party vendor management (TPRM) processes can unlock the highest value for the effort expended.
Dustin Bailey corroborates:


The question then is: How do you ensure your organization’s TPRM processes are effective and efficient? Your team can do this by streamlining the process, starting from the vendor assessment step.
And that’s where Cyber Sierra comes in:



A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.