A Quick Guide for CISOs to Automate Third Party Risk Management





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
After its Sep. 2022 data breach, Uber wrote:


The response was swift, as you’d expect from an enterprise company. Latha Maripuri, Uber’s CISO, in a New York Times’ report, confirmed the move to tighten internal security, so such attacks don’t happen again.
But just two months later in December, it happened again. Despite tightening internal cybersecurity measures, Uber suffered another cyberattack. This time through a third-party vendor, Teqtivity.
Their case has a crucial lesson for CISOs.
Tightening internal data security measures is a must, but it’s not enough. In trying to breach companies’ data, going through 3rd-party vendors has become a hot shot window for cybercriminals:
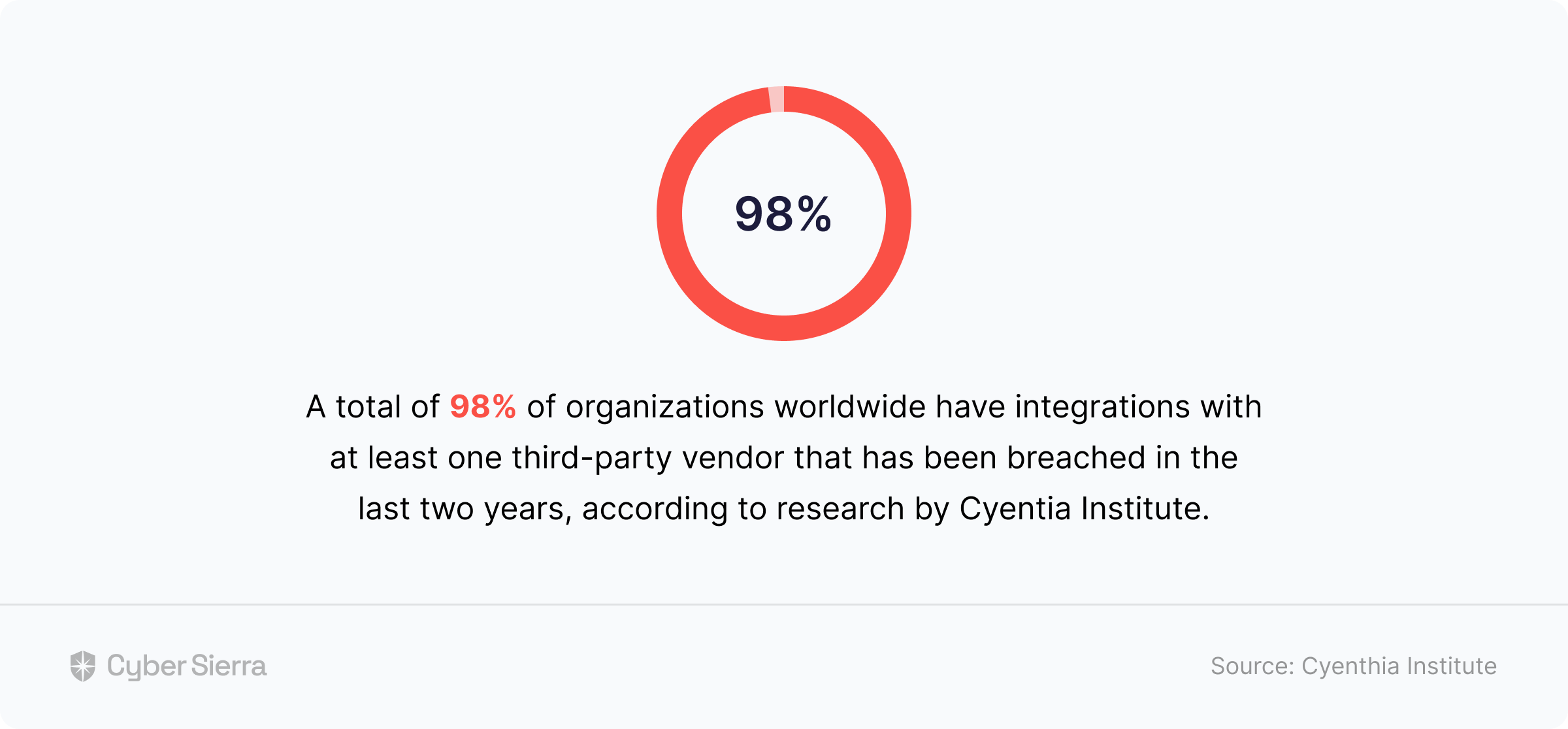

Unfortunately, the reality is that your company needs third-party vendors to expand capabilities. So since they can’t be cut off, CISOs must rise to the occasion of managing third-party vendor risks.
And it starts with understanding your role.
The Role of CISOs in Vendor Risk Management
The CISO role is evolving.
In the past, operating as tactical manager per the CXO’s direction was enough. It was enough because being reactive —dealing with minor threats when they emerged or implementing a few security needs —was enough.
As Uber’s case showed, being reactive isn’t enough.
Modern CISOs have evolved from reactive —constantly playing defense —to strategic. They are getting more involved in the overall operation of the business. And this involves ensuring internal security awareness while managing possible external vendor threats.
Joao Correia corroborates:


The need to also evolve your role to a more strategic focus on managing vendor risks cannot be overstretched.
That’s because doing otherwise can lead to significant financial losses for your company and organizations connected to you. To give you a clue, when SolarWinds witnessed a cyberattack, all third-party companies affected lost up to USD12 million on average:


Talking about being more strategic to curb such losses…
It’s crucial that you know:
- Common third-party vendor risks to prioritize, and
- How to manage them without increasing your workload.
We’ll cover both in this guide, but before we dive in:
Common Third-Party Vendor Risks CISOs Should Prioritize
Here’s why the onus is on you, the CISO.
You can’t rely on third-party vendors to notify you when they get breached, let alone possible ways they could be attacked. For context, out of more than 1,000 IT security professionals surveyed, only 34% were confident a 3rd party vendor would notify them of a data breach:
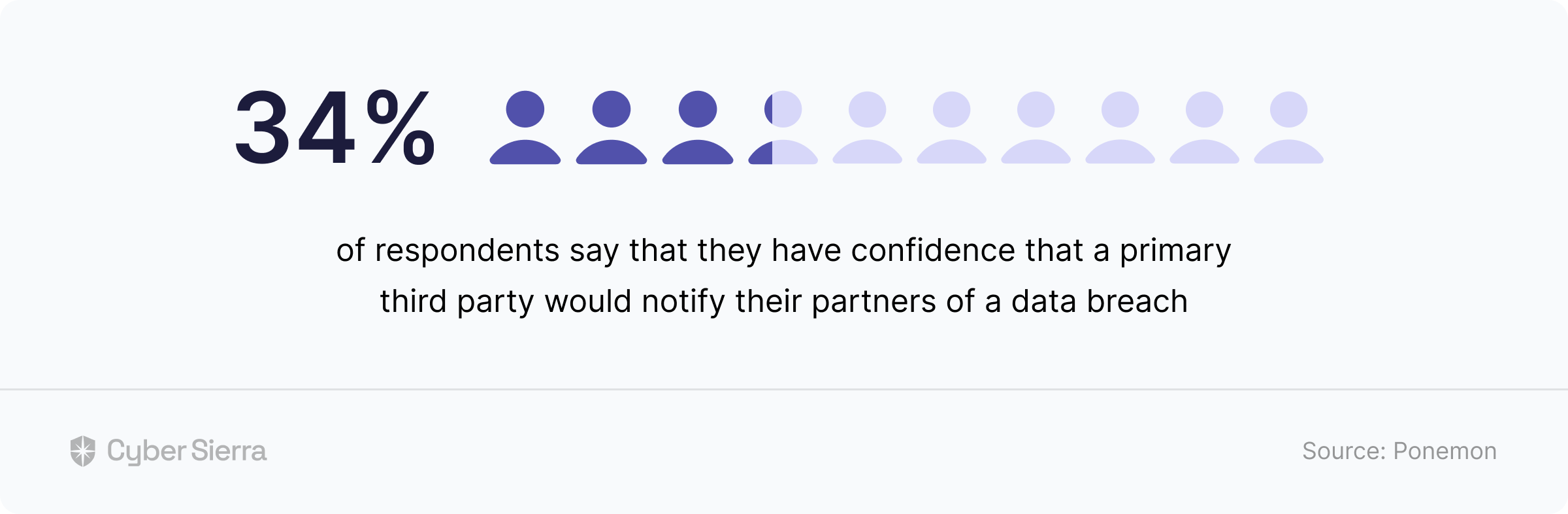

This insight is instructive: Know the common risks to manage based on their likely impact on your business, without relying on third-party disclosures.
Some of them are as follows.
1. Information Security Risks
NIST defines information security or infosec as:


As the definition highlights, infosec risks arise when 3rd-parities’ can’t provide confidentiality, integrity, and availability of data your company grants them access to.
In other words, can the management of a third-party vendor secure your company’s data in their possession from unauthorized access?
If they answer no, that’s a loophole for cybercriminals.
Unauthorized network access, to give you a perspective, caused over 40% of third-party vendor attacks that had a cascading effect on companies:
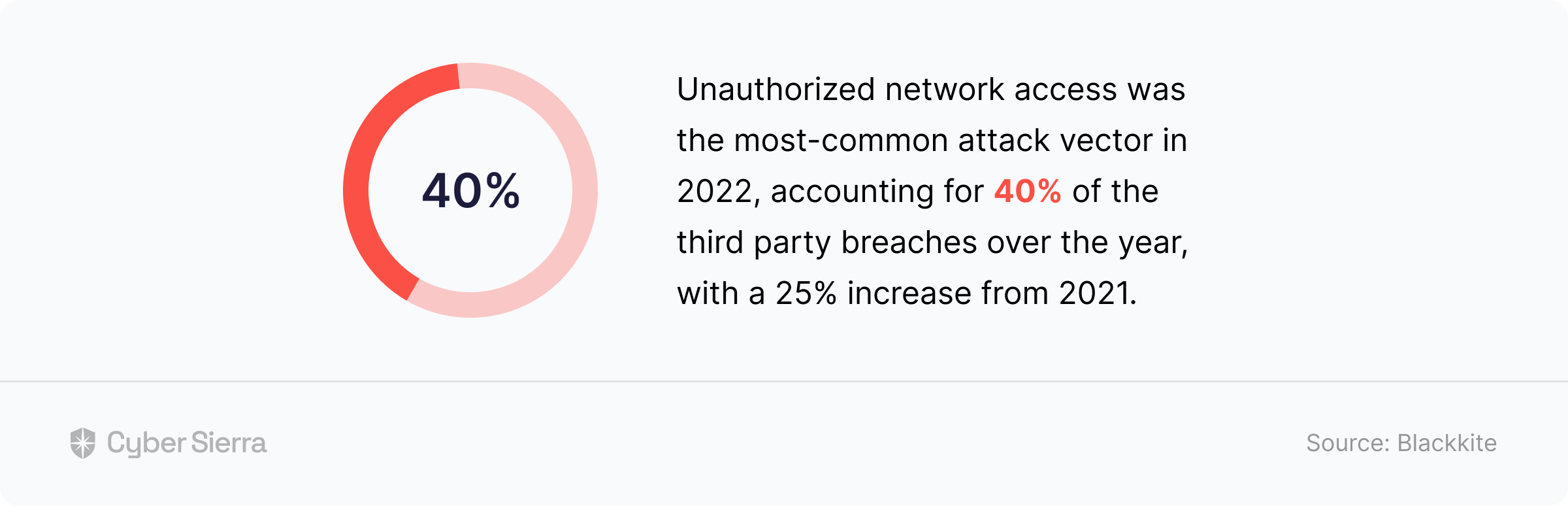

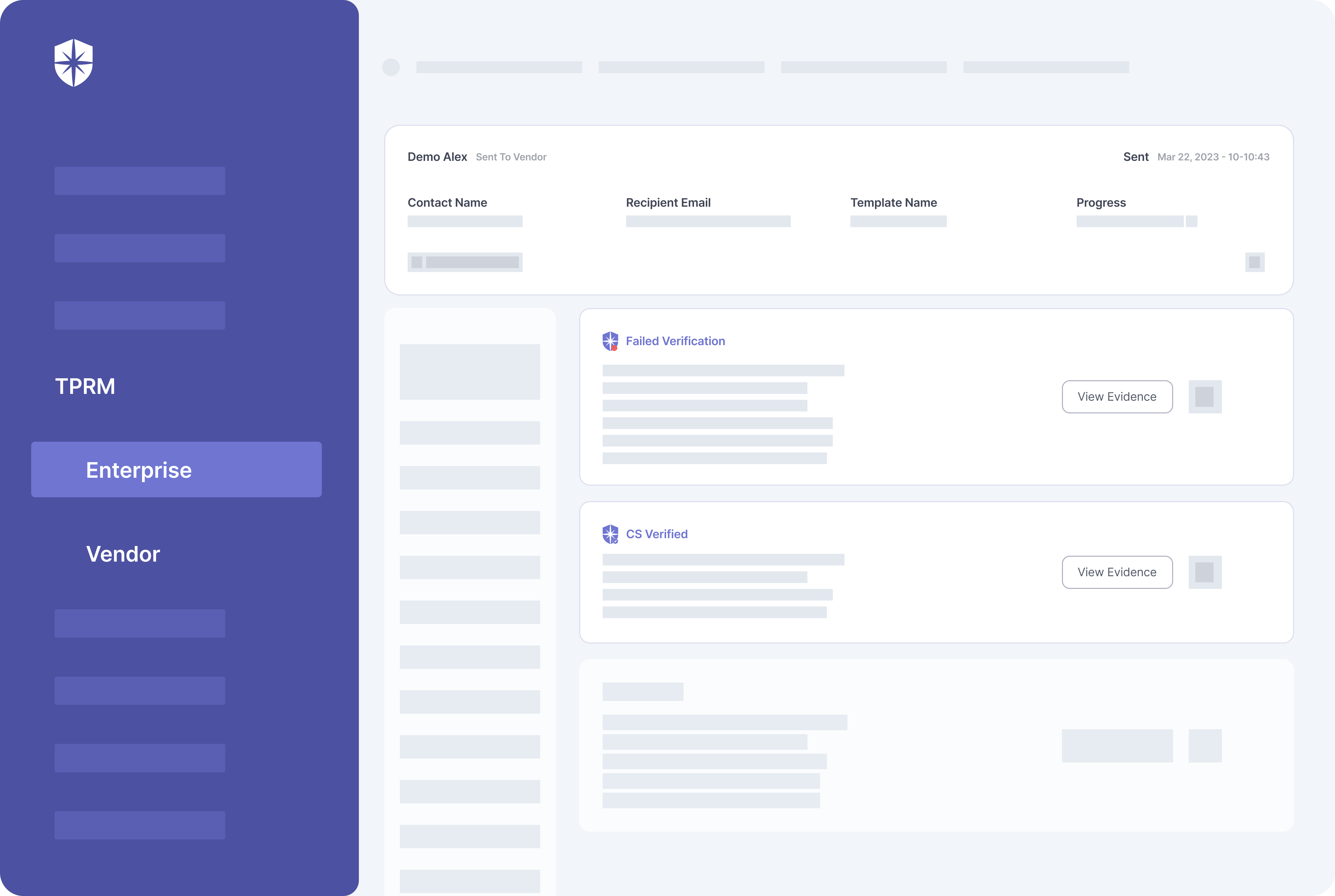
The issue, as noted earlier, is vendors won’t point out this weakness. Not when they’re eager to win your company’s business. So to manage and curtail infosec threats, collect and verify as much evidence as necessary before approving the onboarding of a vendor.
Better if you can do this from one platform:

2. Cybersecurity Risks
Consider this scenario.
A third-party vendor with access to your company’s data witnesses a malware or ransomware cyberattack. Assume also that you’d verified them on the information security front, and they actually protected your data.
If they safeguard your data from breaches, but cannot secure themselves from cyberattacks, your company is still at risk. That’s how cybersecurity risks differ a bit from information security, infosec:
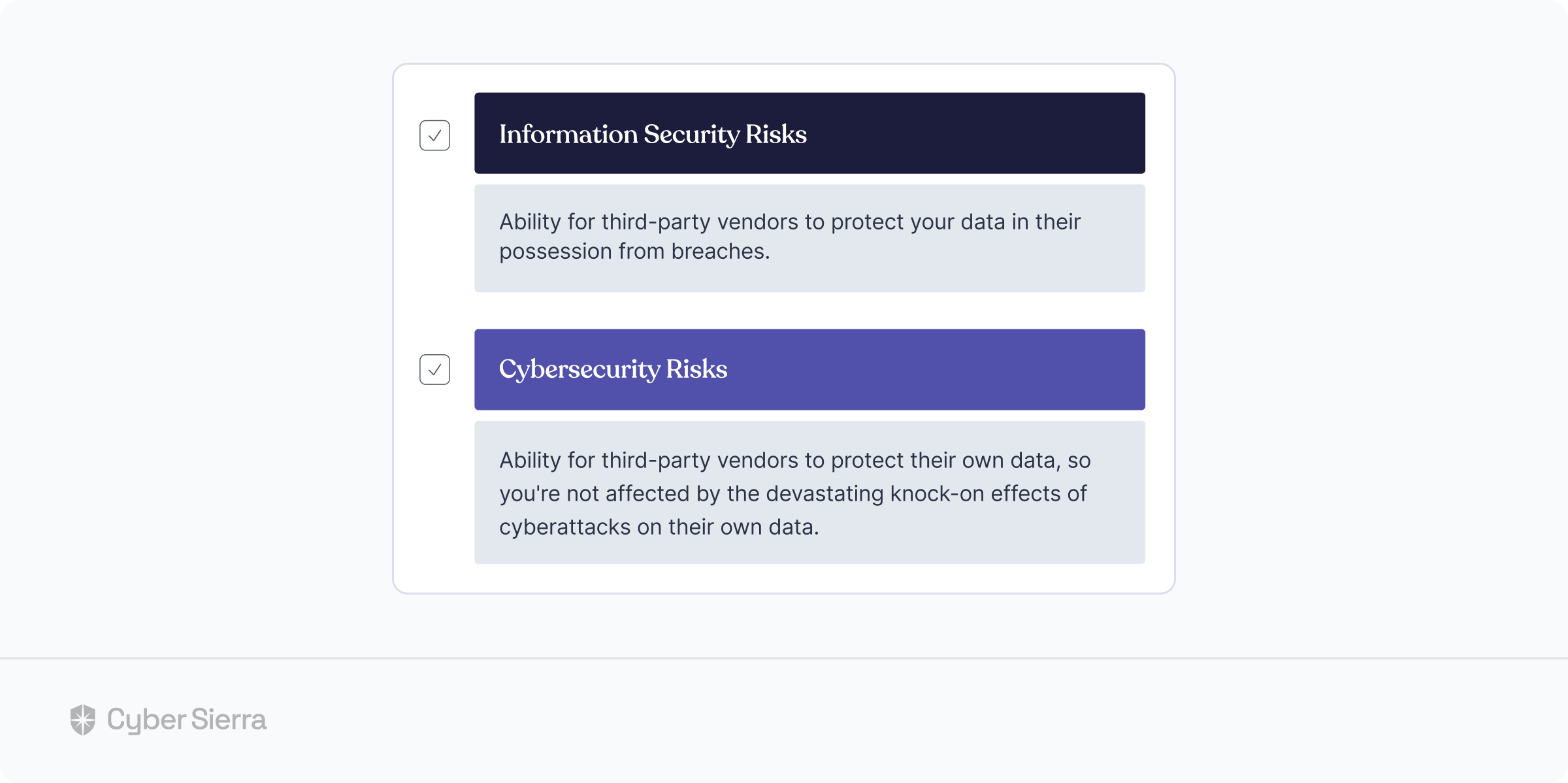

A third-party vendor’s inability to protect themselves poses serious threats —cybersecurity risks— to your company, too. In short, the knock-on effect can also be devastating as infosec risks.
Cyenthia Institute’s study highlights:
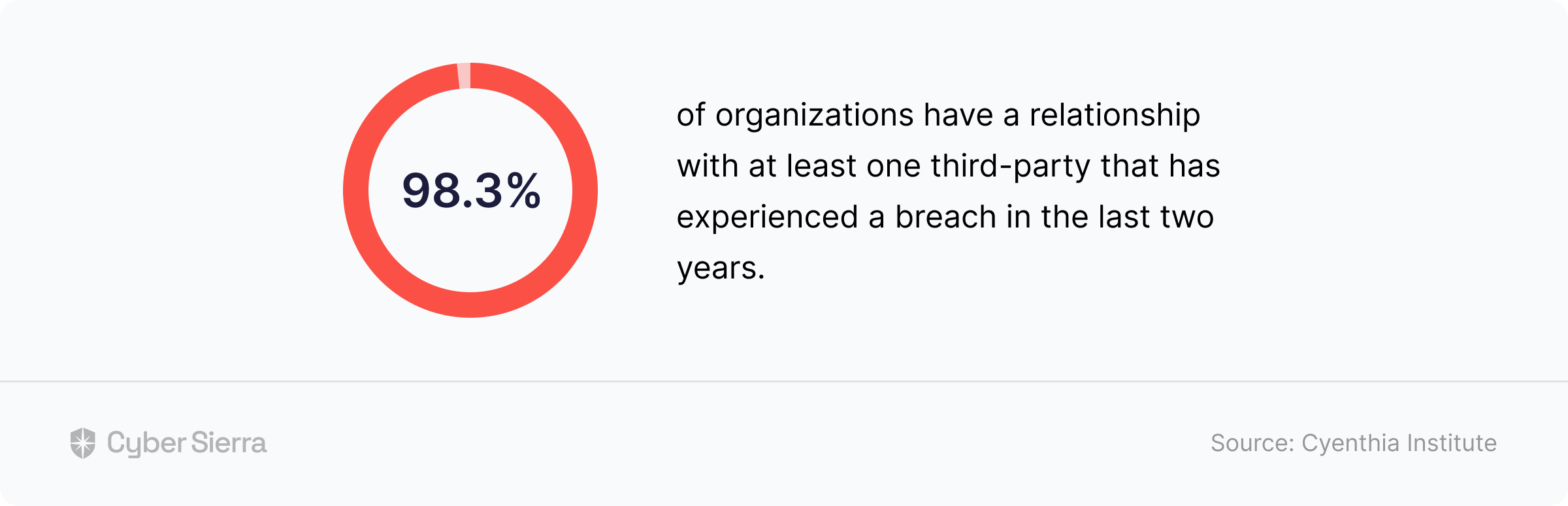

As you would when trying to manage infosec risks, don’t expect 3rd parties to willingly disclose they can’t protect themselves from cyberattacks. Collect and verify as much evidence as possible.
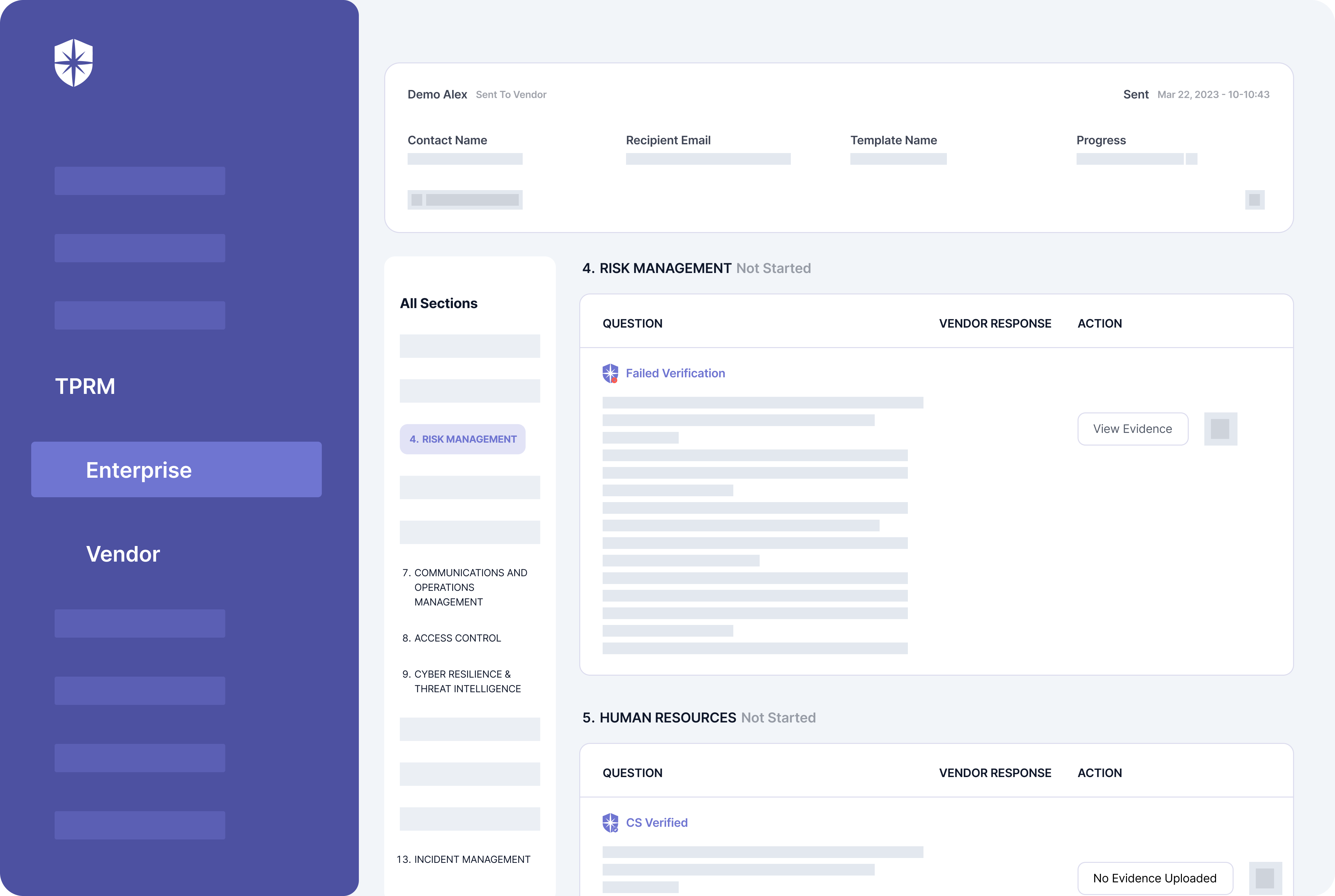
Specifically, request evidence for things like:
- Risk management
- Communications and operations management
- Cyber resilience & threat intelligence
- Access control
- And others.
Again, better to request and verify these in one place:

3. Operational Risks
Imagine a third-party vendor shuts down.
- How much will it affect your company’s operations?
- Can you trust them to correctly dispose of your data?
- What levels of risk will it expose your organization to?
It’s crucial to ensure that 3rd-party operations won’t expose your company to risks, per the concerns above. More so in today’s digitally-driven business climate of cloud-based software and API integrations.
Talking about security threats from the operations of third-party vendor software or APIs integrated into yours, a Gartner study advised:
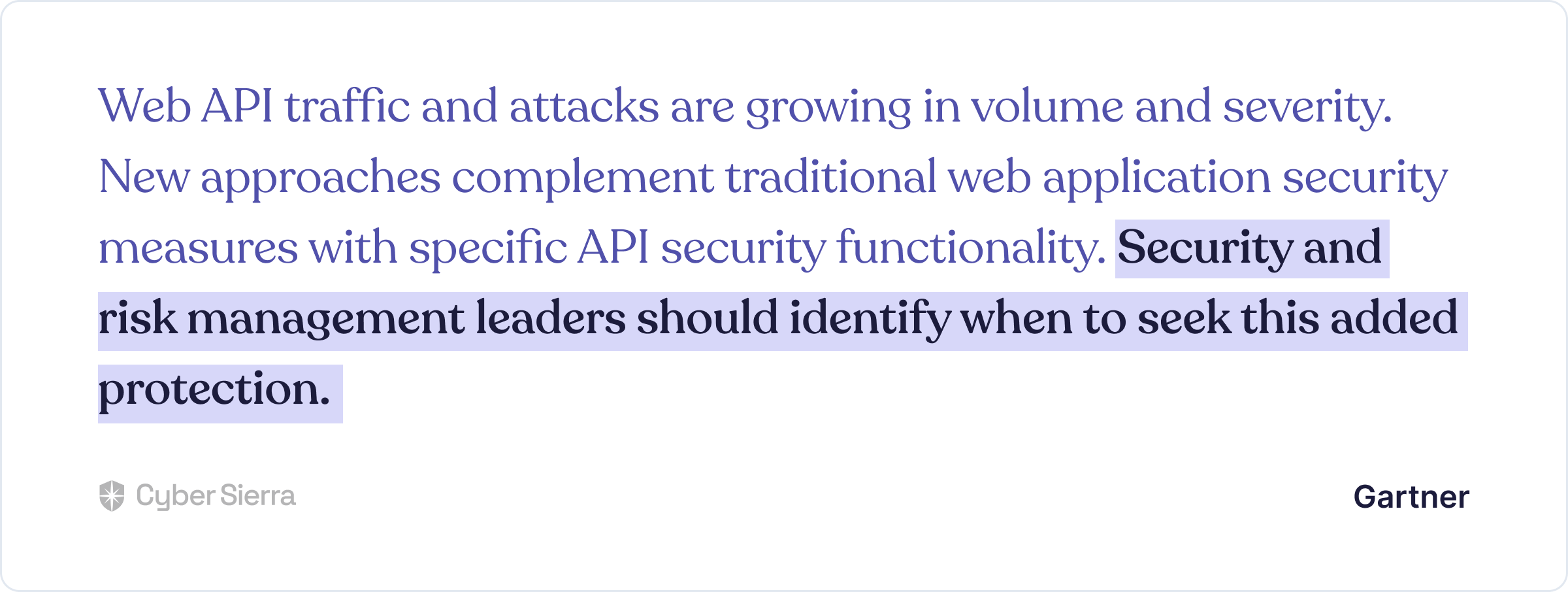

The challenge:
How do you know which vendors to seek such added protection from?
By requesting and verifying things like:
- Software development lifecycle
- Cloud based services information
- Technology refreshment management
- And others.

4. Compliance Risks
Are 3rd-party vendors your company works with compliant with standards, laws, policies, and regulations in a given industry or jurisdiction?
IT security executives must ask this crucial question.
That’s because if they aren’t, they could expose your organization to legal and regulatory compliance penalties. According to Deloitte, this is a common 3rd-party risk enterprise organizations face:


Compliance with standard frameworks like SOC 2, ISO27001, HIPAA, GDPR, PCI DSS, etc., are all necessary. Also, confirm a third-party vendor is compliant with regulations specific to their industry and exact location.
Here’s an excellent way to do that.
When onboarding a third-party vendor:
- Choose the right vendor type: This will help you know the industry-specific regulatory compliance to request and verify.
- Select their location: This will help you know the local laws and regulations they must be compliant with to avoid risks.
Both are some crucial TPRM workflows built into our platform:
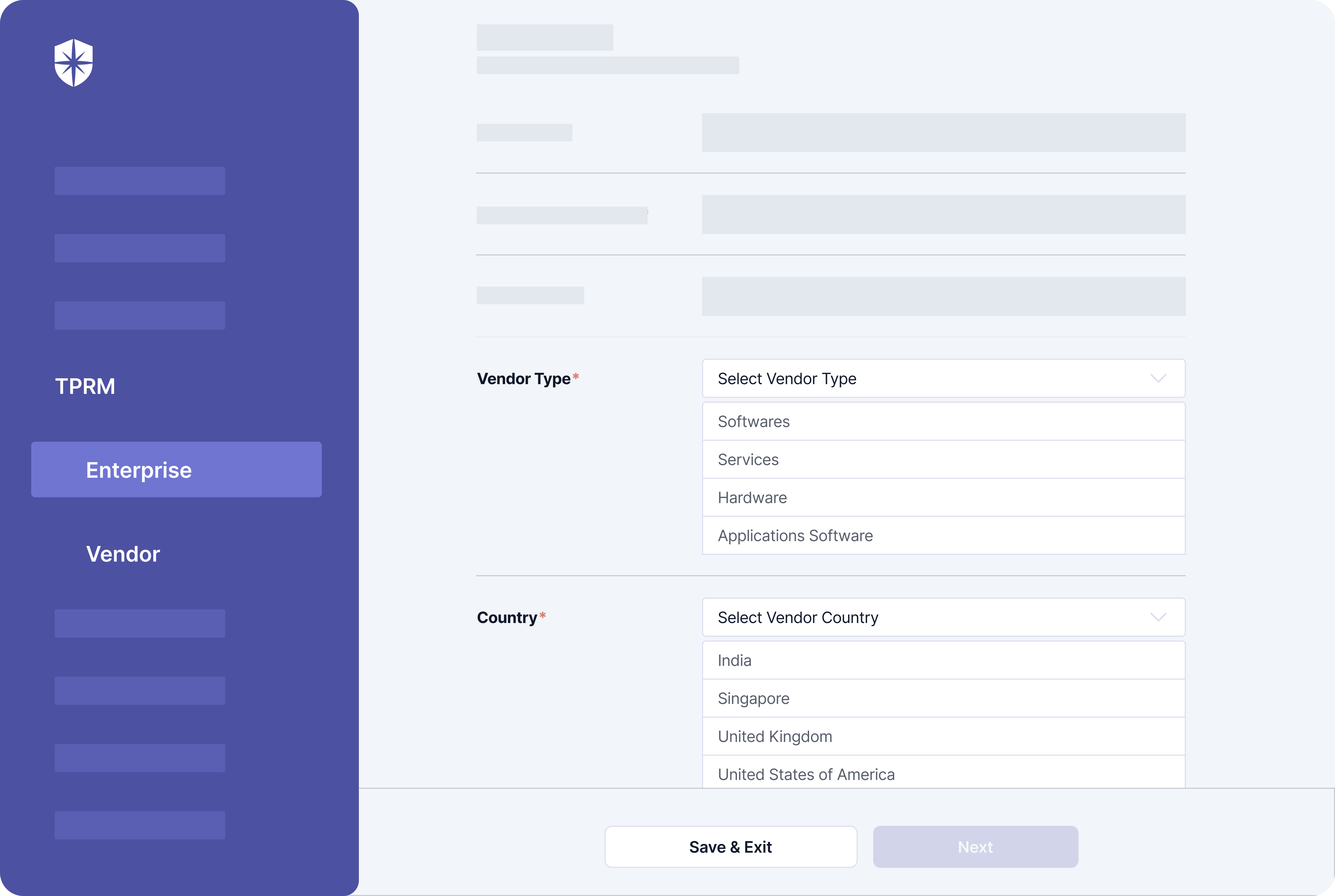

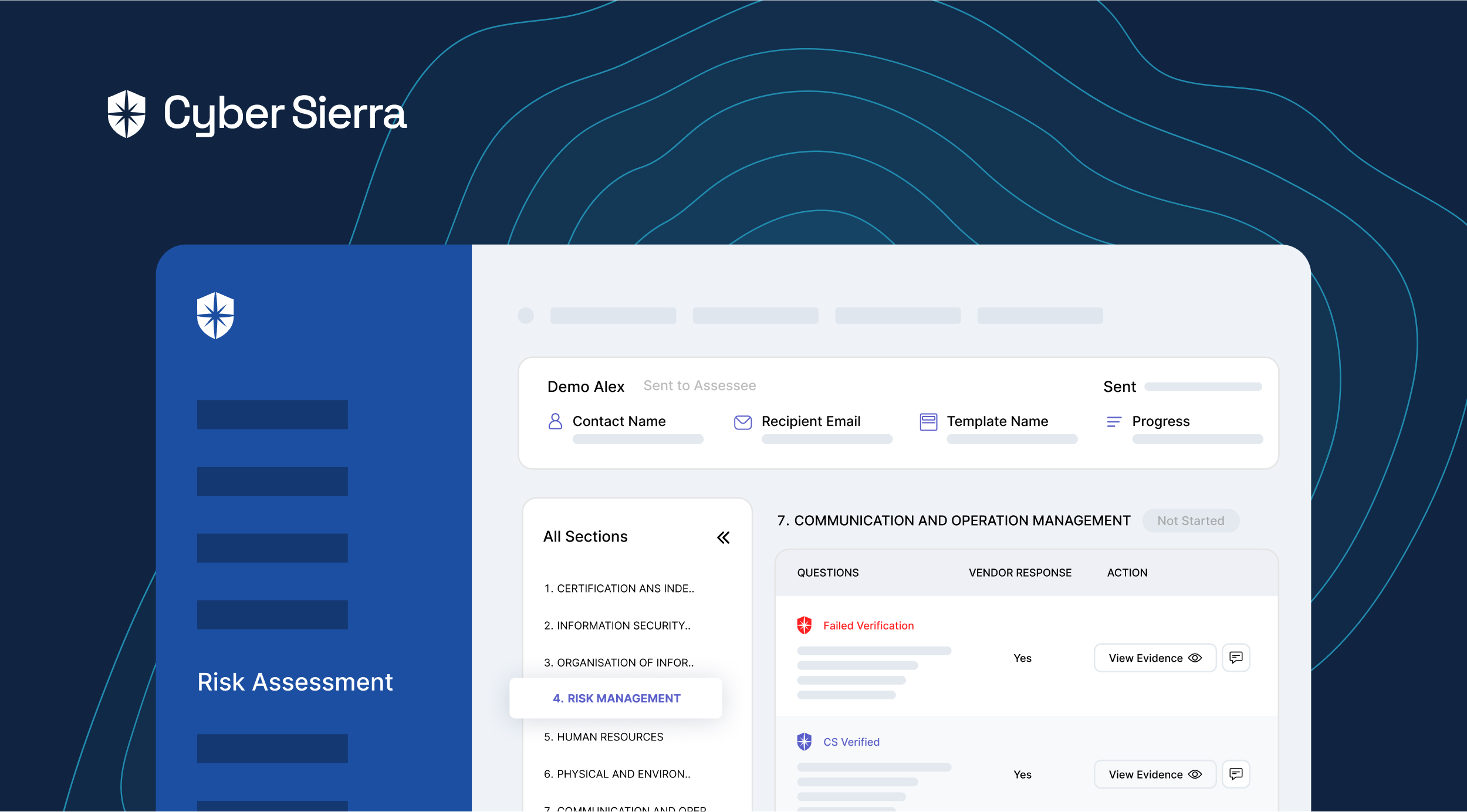
As shown above, Cyber Sierra simplifies vendor categorization, so you can assess them seamlessly from the get-go. Our software also automates most processes involved with third-party vendor risk management.
How CISOs Automate Vendor Risk Management
UIC’s CISO, Shefali Mookencherry, once said:


Unpack that, and you’ll notice categories of assessments to be carried out on third-party vendors before CISOs should give the greenlight:
- Information security profile
- Possible cybersecurity threats
- Operational and regulatory risks
All three categories involve a lot of standard and custom security questionnaires and ongoing risk assessments. Each must be sent to vendors with due dates, received back, resent to them for failing to meet requirements, sent back to you, and so-on-and-so forth.
This manual back-and-forth isn’t optimal, and that’s where automation comes in. With the right platform, you can automate TPRM in three steps:
1. Streamlining Vendor Risk Assessments
In the US, for instance, it is required to assess a 3rd-party’s infosec and cybersecurity risks, using policies specific to SOC and NIST.
And there are about 35 standard assessments across both.
If you’ve ever tried to assess just one vendor, manual back and forth can be a real nightmare. Using software to streamline the process allows for quicker and more cost-effective vendor assessments in less time.
Let’s stay with our US-based third-party vendor example.
Cyber Sierra streamlines the entire process to just three steps. Choose the vendor’s industry in the 1st, and in the 2nd step, the policy templates for SOC and NIST are already pre-built (and updated regularly).
All you have to do is select the one you want to use:
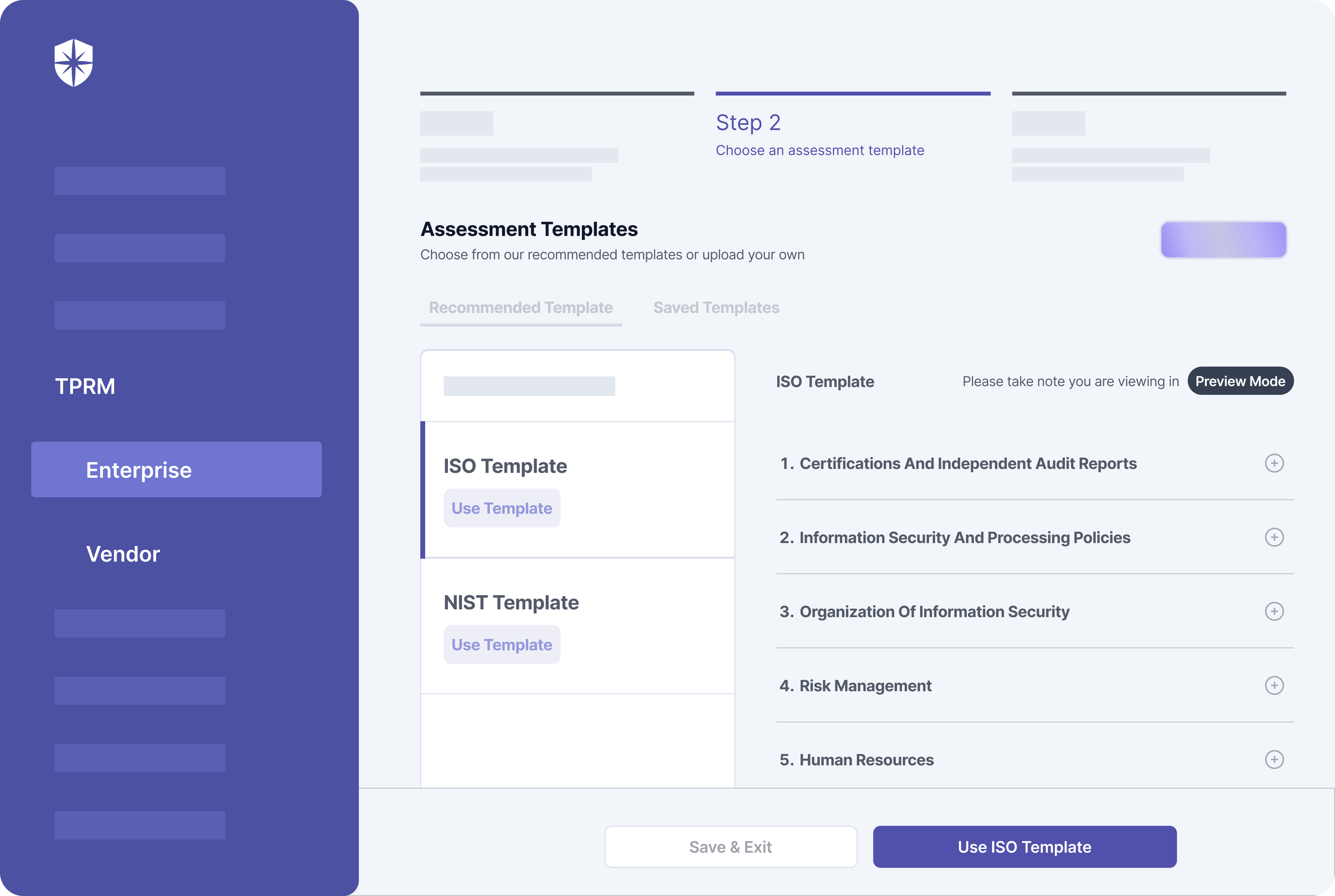

As indicated above, you can also upload and send custom assessment policies. Either way, the entire assessment processes are streamlined.
2. Facilitating Due Diligence & Verifications
Vendor risk management doesn’t end with sending security questionnaires and risk assessments. After that, security executives must perform:
- Due diligence on uploaded documentation, and
- Verify that they have the correct security controls.
Both processes can also be hectic.
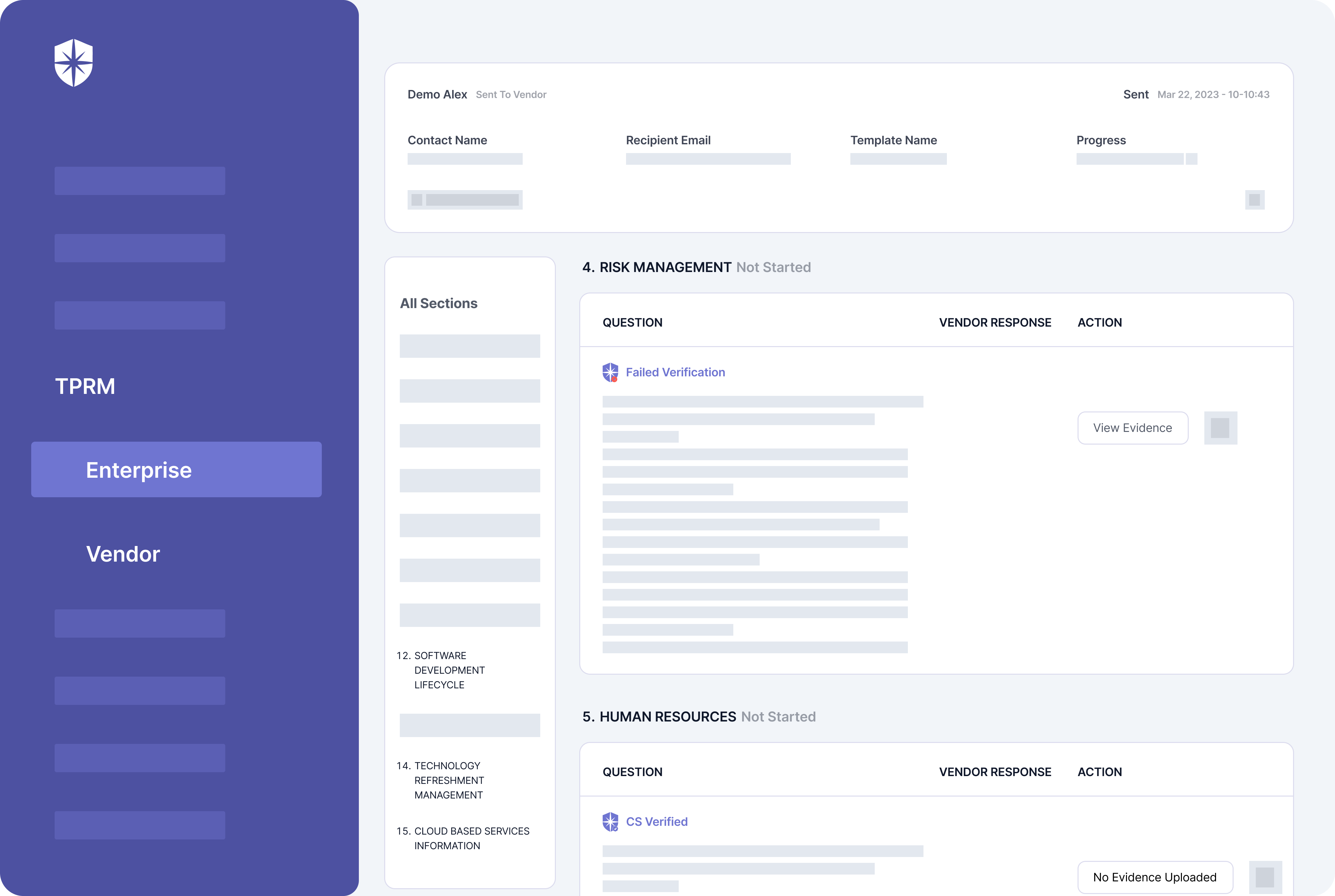
But with the right software, you can automate this crucial step by facilitating due diligence and verifying controls. Cyber Sierra, for instance, autoverifies vendor-uploaded documentation that meets due diligence thresholds. Our software can also flag those that fail verification.
It doesn’t end there.
You can chat with a third-party vendor, flagging unacceptable security controls and why a document they uploaded failed verification:
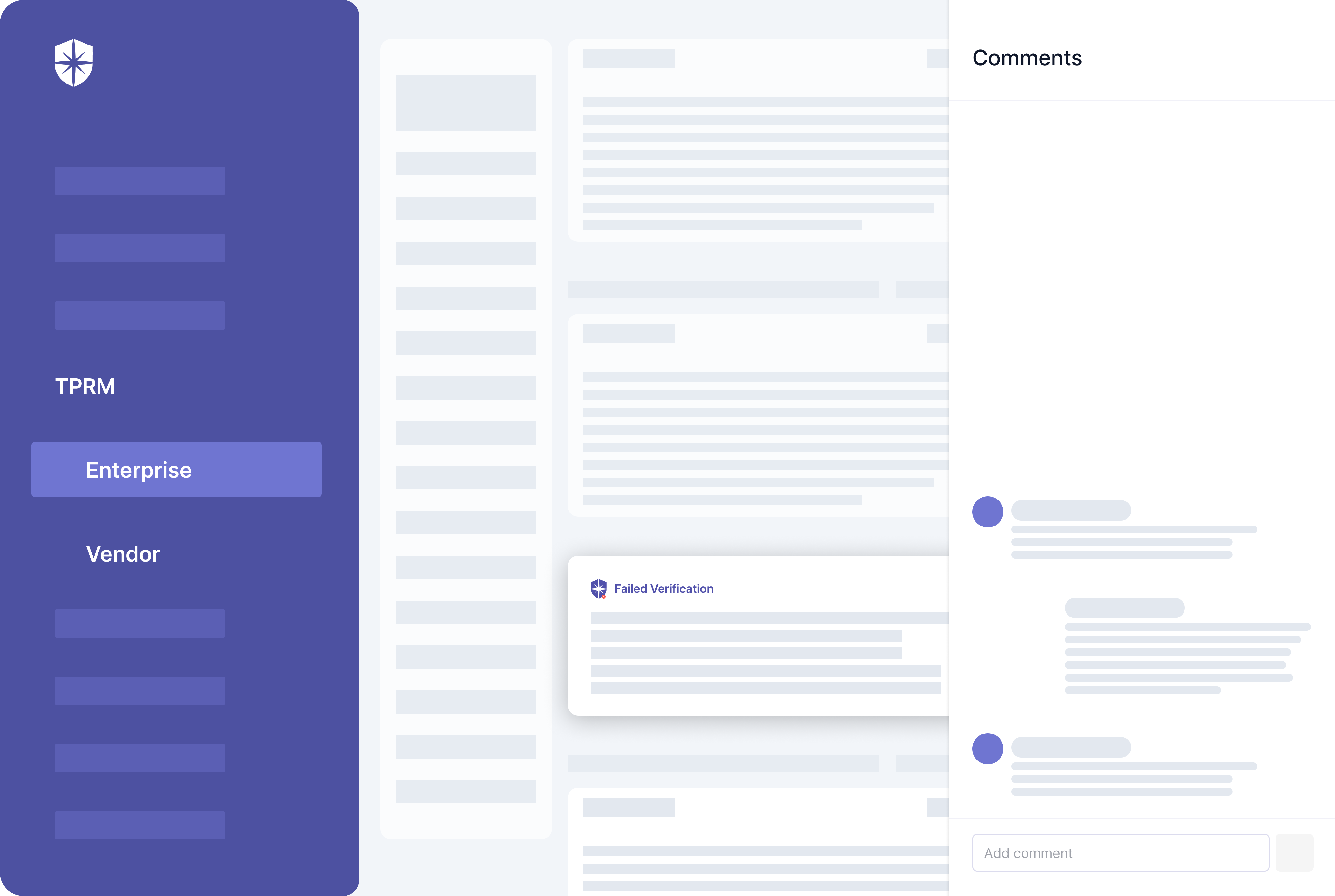

Simplifying due diligence and verifying controls this way has benefits.
Some are:
- Accurate and faster verifications, without context-switching.
- Third-party vendors you’re about to work with will know exactly how to improve their cybersecurity posture, making our entire ecosystem safer.
- Everyone saves time (and money).
3. Monitoring Controls Continuously
Recall Uber’s data breach through Teqtivity.
It’s likely Uber, being a large enterprise, completed necessary third-party infosec and cybersecurity assessments when integrating them into their software. Still, the cyberattack on Teqtivity, which happened after both companies worked for long, affected Uber.
Imagine Uber had regularly monitored Teqtivity’s security controls.
Chances are, they would’ve spotted possible cyber threats that could also affect them and flagged for mitigation. Continuous security controls on third-party vendors are necessary for this.
But it’s not just that.
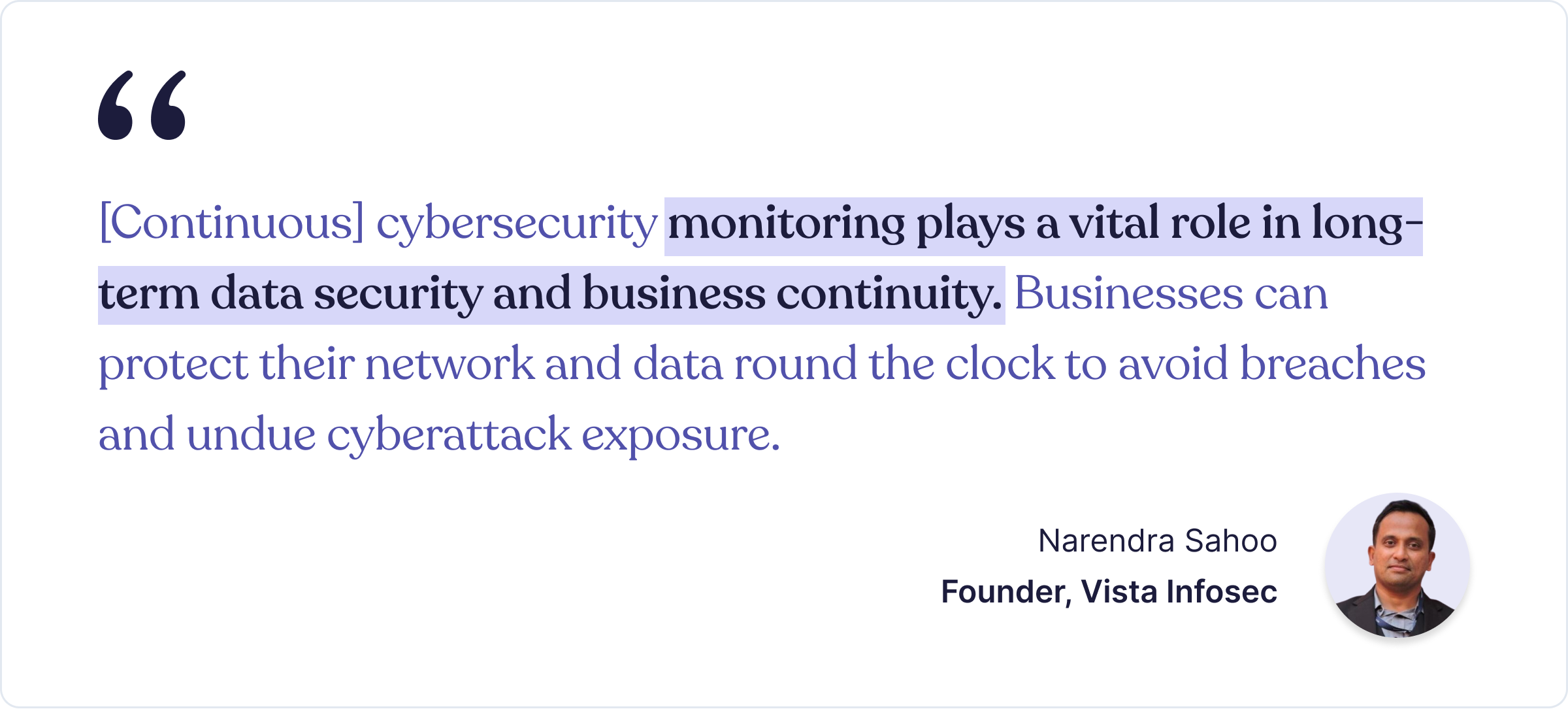
As cybercriminals become more sophisticated, compliance regulations, both standard, industry, and location-specific ones, are also evolving. Continuous monitoring of 3rd-party security controls is therefore also crucial to avoid business operations being stalled by regulatory sanctions.
A veteran infosec and cybersecurity expert corroborates:

Choose More Than a TPRM Platform
An excellent third-party risk management (TPRM) platform automates a chunk of the processes, saving you from manual labor. But in choosing the right one, there are crucial things CISOs must also look out for.
Here’s what Delta Air’s Global CISO looks out for:
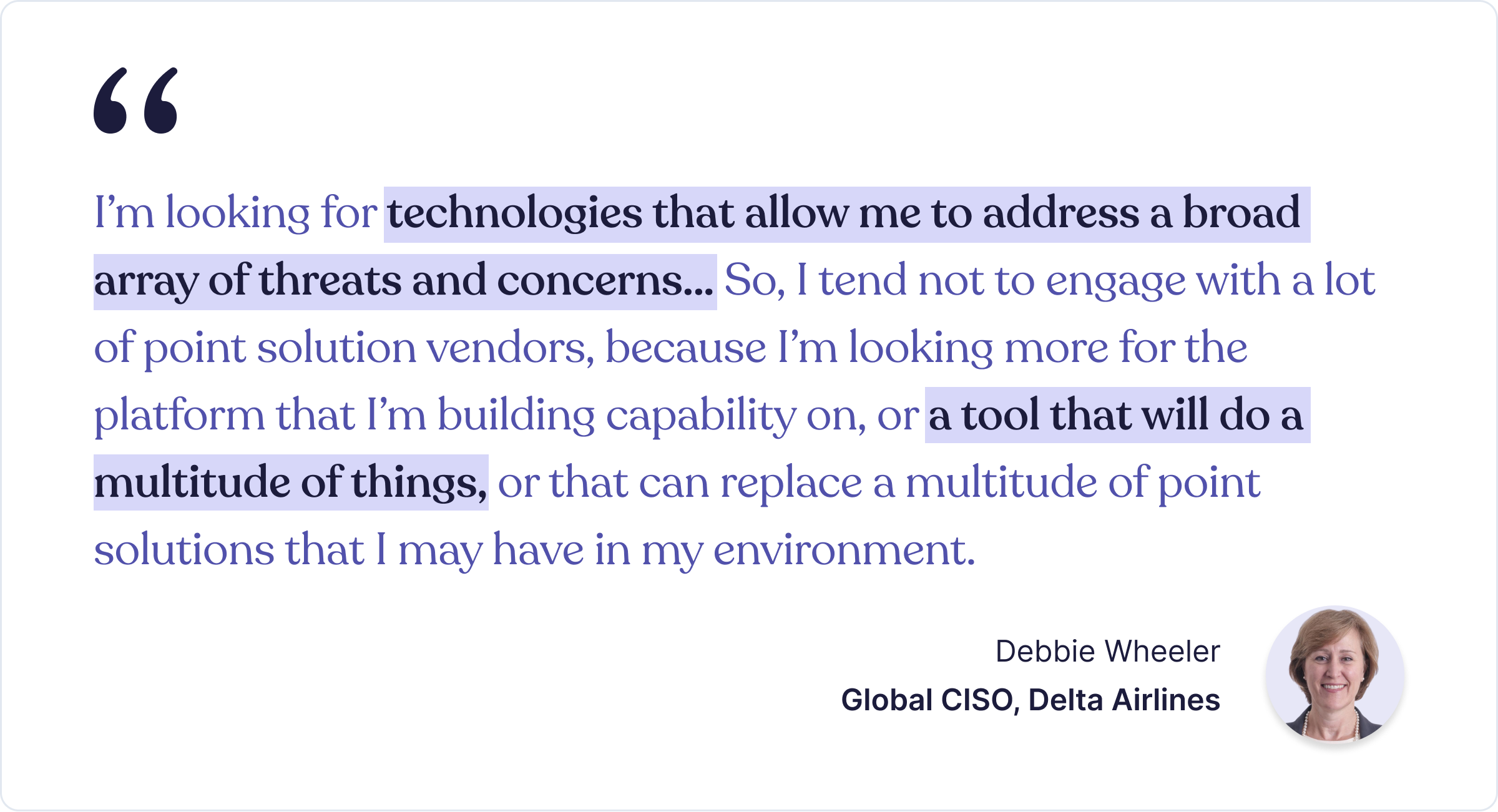

It’s easy to imagine Debbie’s stand.
As we’ve seen, managing 3rd-party vendor risks involves a lot:
- Ascertaining their information security capabilities
- Assessing them for possible cybersecurity threats
- Monitoring their security controls continuously
Ticking all these boxes already takes a lot of back and forth without the right TPRM solution. However, it is just one bit of what CISOs need to proactively implement internal and external security measures.
For instance, you also need to streamline things like:
- Ongoing employee security awareness training
- Staying up to date with regulatory compliance
- Dealing with cloud misconfigurations, and
- Securing and renewing cyber insurance.
Achieving all these in one, interoperable solution is optimal.
And that’s where Cyber Sierra comes in:



A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.