TPRM Program Metrics Tracked by Successful CISOs





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
I talk to a lot of CISOs.
Most decry not having enough budget to hire talent and buy every tool needed to implement their desired third-party risk management (TPRM) framework. But even among those who don’t have such challenges, our chats often reveal a common, underlying question:
What metrics do I need to prove my TPRM program is successful? This question is valid to both sides of the spectrum. Because to secure more budget or get approval for next year’s budget, you must establish metrics demonstrating the success of your TPRM program.
Says Chris Gida, Asurion’s Sr. Compliance Manager:


In other words, metrics are useful for more than just getting a TPRM program budget approved. They are also crucial for making decisions relative to securing your company from vendor risks.
But the question remains: How do you choose them?
Criteria for Choosing Vendor Risk Management Metrics
There’s no one-size-fits-all criteria.
However, I like Josh Angert’s recommendation for Chief Information Security Officers (CISOs). He hammered on the need to always start with the end in mind when establishing TPRM program metrics.
In his words:


Based on Josh’s insight, the metrics you choose should cut across key performance indicators (KPIs) and key risk indicators (KRIs). KPIs keep your security team focused on aligning your organization’s TPRM program with business objectives. KRIs, on the other hand, track the prompt identification and mitigation of vendor risks.
So to choose vendor risk management metrics:
- Define business objectives relevant to your TPRM program.
- Outline mission-critical vendor risks that must be mitigated.
- Select enterprise metrics that encompass all of the above:


The rest of this guide explores metrics I see enterprise CISOs using to ascertain the success of their TPRM programs. As we proceed, you’ll also see how our interoperable cybersecurity and compliance automation platform, Cyber Sierra, helps you achieve them.
Before we dive in:
Enterprise Third-Party Risk Management Program Metrics
By knowing what to measure (i.e., the TPRM metrics below), your security team can know what to improve and succeed.
1. Number of Identified Vendor Risks
This metric measures how many 3rd party risks your security team identifies over time. The objective of this metric, relevant to most enterprise TPRM programs, is to identify as many risks as possible.
As organizations add new vendors, they need to identify all risks and security threats brought into their ecosystems. So the more risks identified over time, the more your security team can demonstrate its understanding of 3rd party risks.
2. Number of Reduced Risks
Identifying an appreciable number of risks over time is good. But demonstrating that they are reducing relative to when your program went into effect is more important.
Say your organization hasn’t added new vendors in the last three months. This metric tracks changes in third-party risks within that period. Less risk means your security team is effective.
3. Cost of Managing Third-Party Risks
Security teams should track this in twofold:
- Articulate all direct and indirect costs associated with managing vendor risks before implementing your TPRM program.
- Show how these costs have reduced over time relative to the negative business impact mitigated.
Reporting this metric is critical because it’s a great way for board members to see your TPRM program as a value, and not a cost center.
4. Time to Detect Vendor Risks
As the name suggests, this metric helps you track how long it takes your team to detect vendor risks on average. A shorter risk detection time shows that your security team is efficient.
Board members would want to see risks being detected as soon as possible. This is why third-party security managers track and report on how their team has reduced their average risk detection time.
5. Time to Mitigate Risks
How long does your team take to mitigate vendor risks?
This metric measures the answer to that question. Once your team detects risks, they must immediately mitigate them. The faster they do this, the more financial and reputational damage your vendor risk management program will save your company.
The enterprise security managers I talk to use this metric to visualize how they are mitigating risks within a timeframe. By tracking it, you can set objectives for improving your time to mitigate risks over time.
6. Time to Complete Risk Assessments
Vendors are business entities contracted to help achieve your company’s mission or business goals. Putting them through rigorous third-party risk assessment is critical for mitigating risks.
However, it is also important to track how long it takes to completely assess vendors. Security managers should strive to reduce the time it takes to assess vendors for two reasons:
- Give vendors a smooth assessment experience
- Demonstrate to management how efficiently they are risk-assessing and onboarding 3rd parties into their ecosystem.
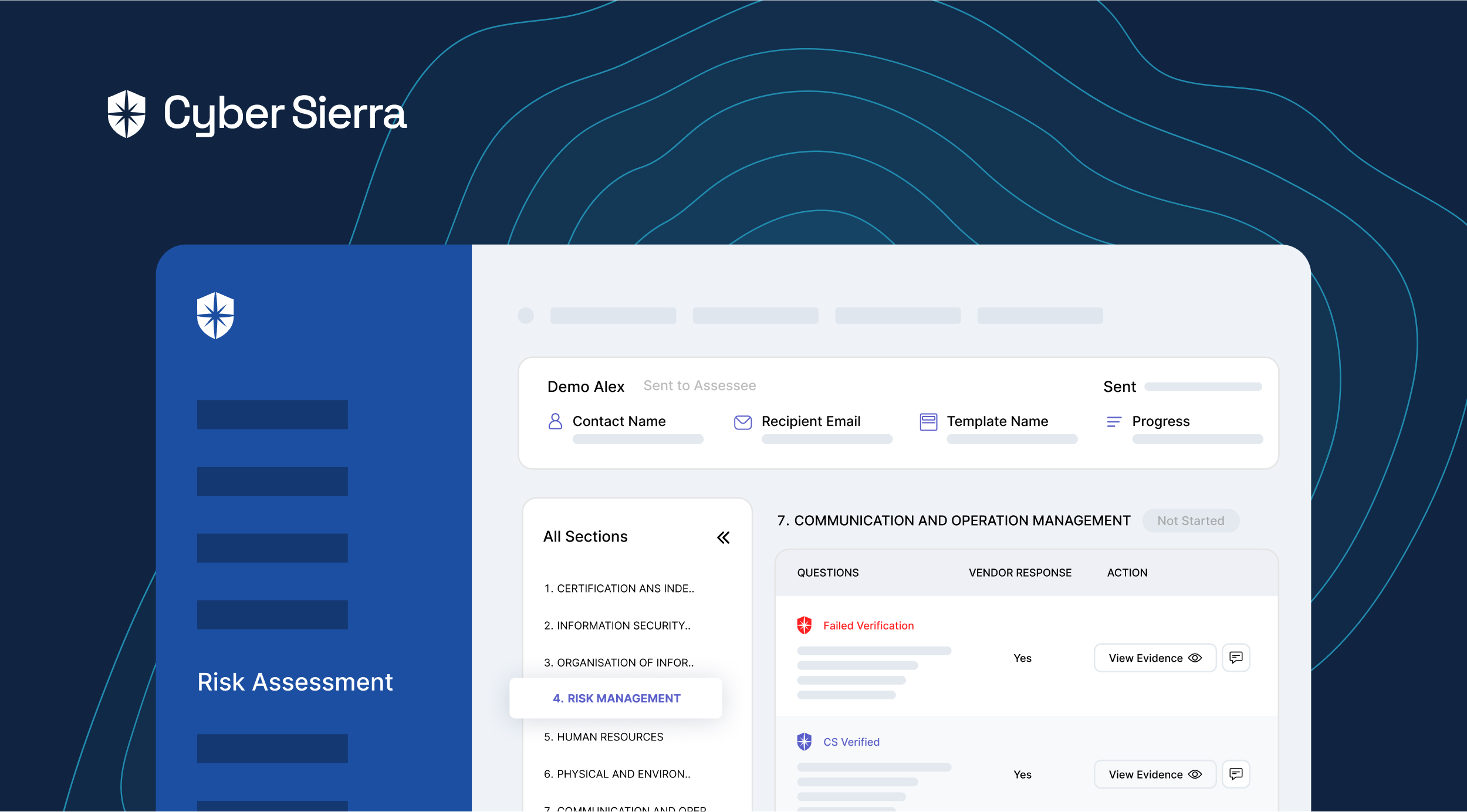
You can achieve these with software that streamlines the process of initiating and completing vendor risk assessments in three steps:

As shown above, this streamlined 3-step workflow is built into Cyber Sierra’s TPRM module. So instead of looping between spreadsheets or exchanging endless email threads, enterprise security teams can profile, assess, and manage vendor risks in one place.
Achieving Vendor Risk Management KPIs & KRIs
Tracking the metrics above is good.
But without context, metrics on a dashboard won’t show how effective your TPRM program is. Worse, they are not so helpful if you can’t tie them to noticeable business objective indicators.
Josh Angert shared why indicators —key performance indicators (KPIs) and key risk indicators (KRIs) —are more important:
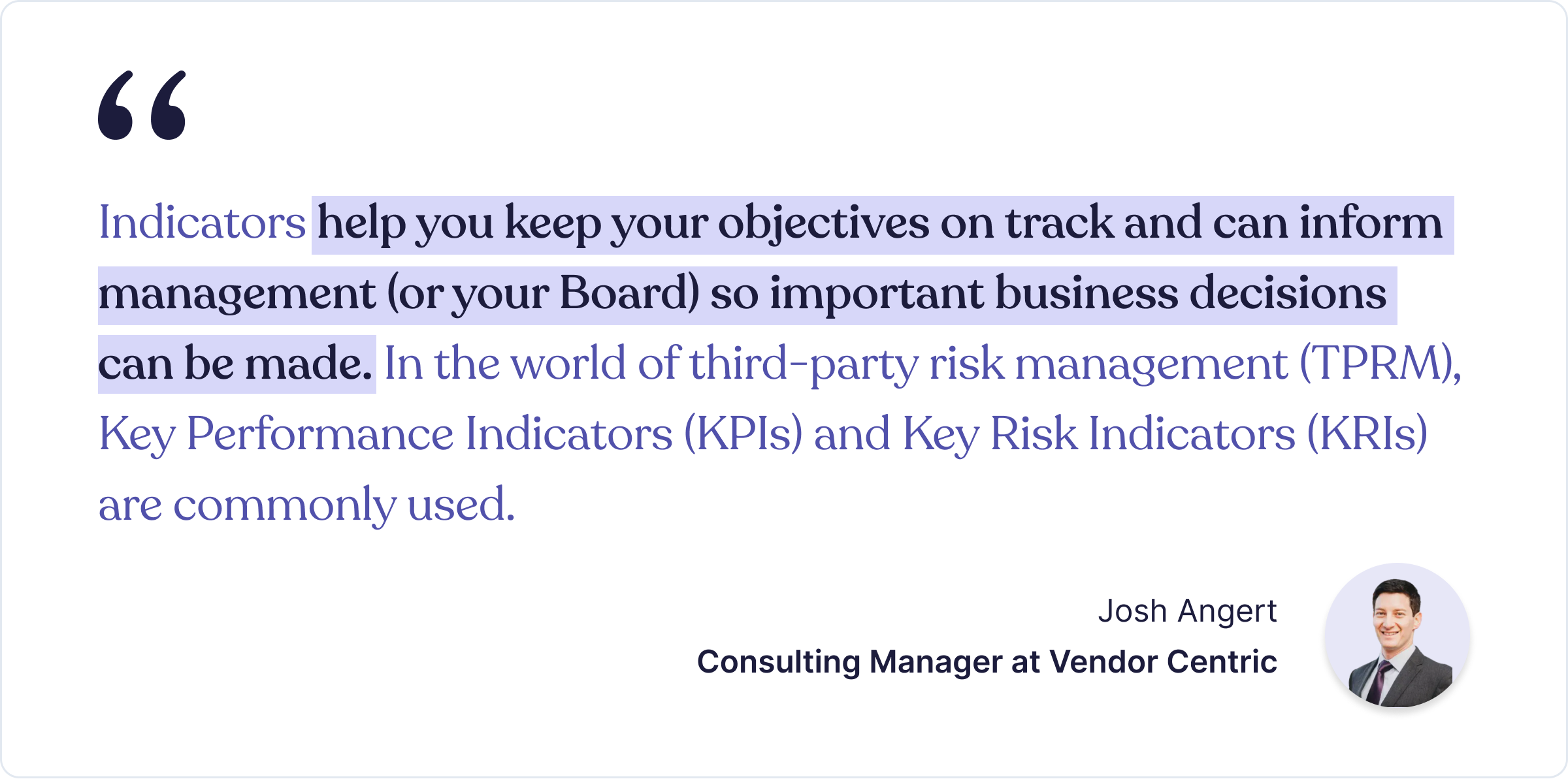

Let me rephrase that.
Choosing TPRM metrics is vital. It guides your security team. Management, on the other hand, concerns itself with indicators —KPIs and KRIs— tied to business objectives they can track and use to make decisions. Below are three you should prioritize.
1. Resource Efficiency
Imagine using the perfect blend of ingredients to bake a batch of cookies without wasting anything. Resource efficiency is similar to that. It means using just the right amount of time, tools, people, and budget to implement an effective TPRM program.
Resource efficiency indicates to management that your security team is doing a great job while saving time and money. According to Bryan Littlefair, the CEO of Cambridge Cyber Advisers, to improve this KPI, start by having a mature vendor risk management strategy.
Bryan advised:

2. Throughput
Say your company must address an average of 300 vendor risks per month. Throughput gives management an overview of how quickly your security team is able to do that over a given time period.
This important KPI helps you identify and minimize bottlenecks in your vendor risk management processes, enabling your team to do more in less time. This is essential for achieving selected TPRM program metrics.
3. Process Efficiency
Think of process efficiency like striking the right balance between operational effectiveness and risk mitigation.
It helps management track the speed at which your security team assesses, manages, and mitigates third-party risks. While the first two required having the right strategy, this one is about streamlining core elements of third-party risk management.
And this is where Cyber Sierra comes in.
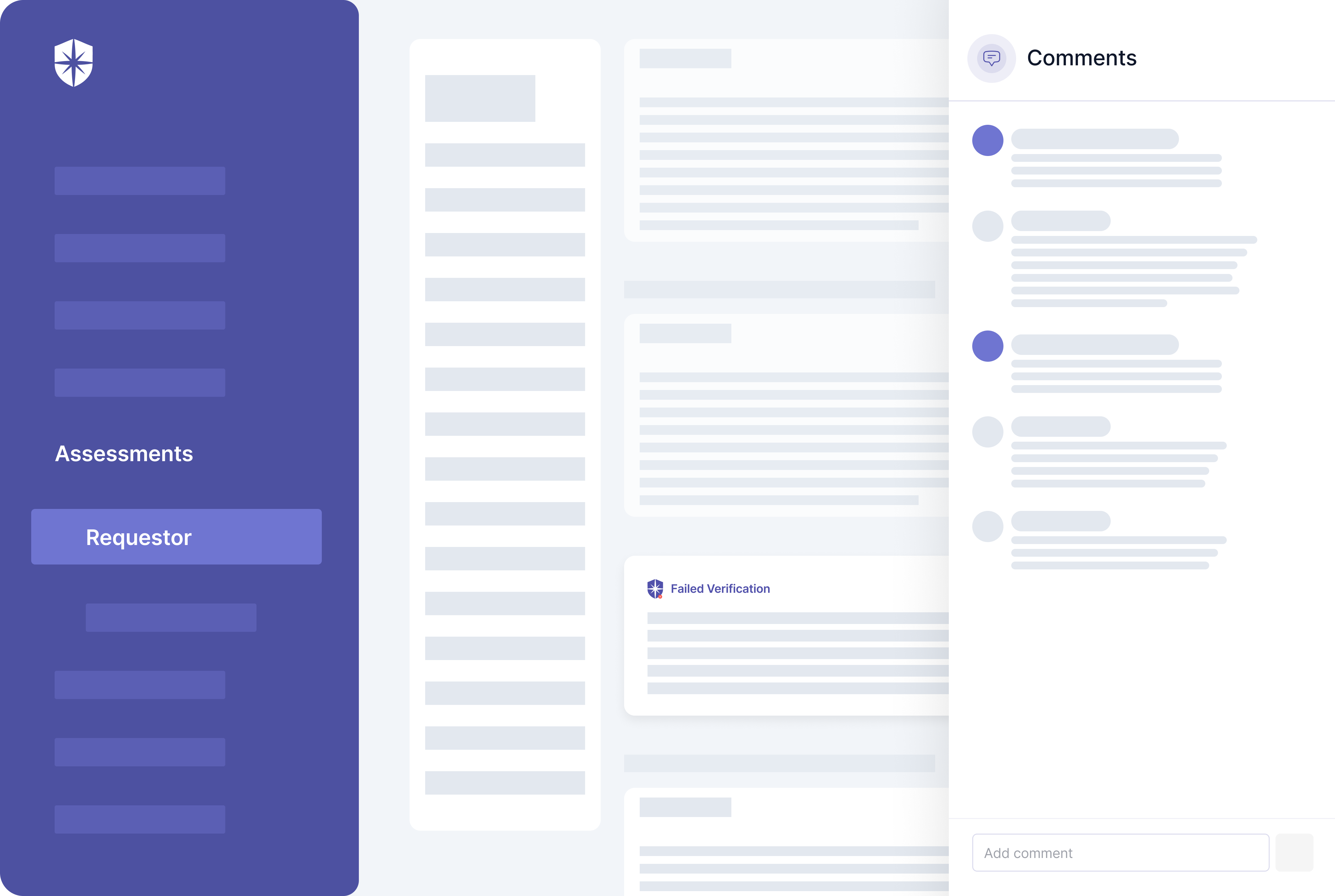
For instance, you can assess, onboard, and manage third-party vendors much faster with our platform. And for prompt risk mitigation, our software auto-verifies all evidence of security controls uploaded by vendors in response to assessment questionnaires.
Unverified evidence indicates a lack of necessary security measures that could lead to data breaches. With Cyber Sierra, your team can follow up with vendors to resolve this on the same pane:

Achieve Key TPRM Program Metrics
As I’ve stressed, knowing what metrics to choose is how you demonstrate that your TPRM program is successful. But as you choose them, it is equally, if not more important to align efforts towards achieving visible KPIs and KRIs.
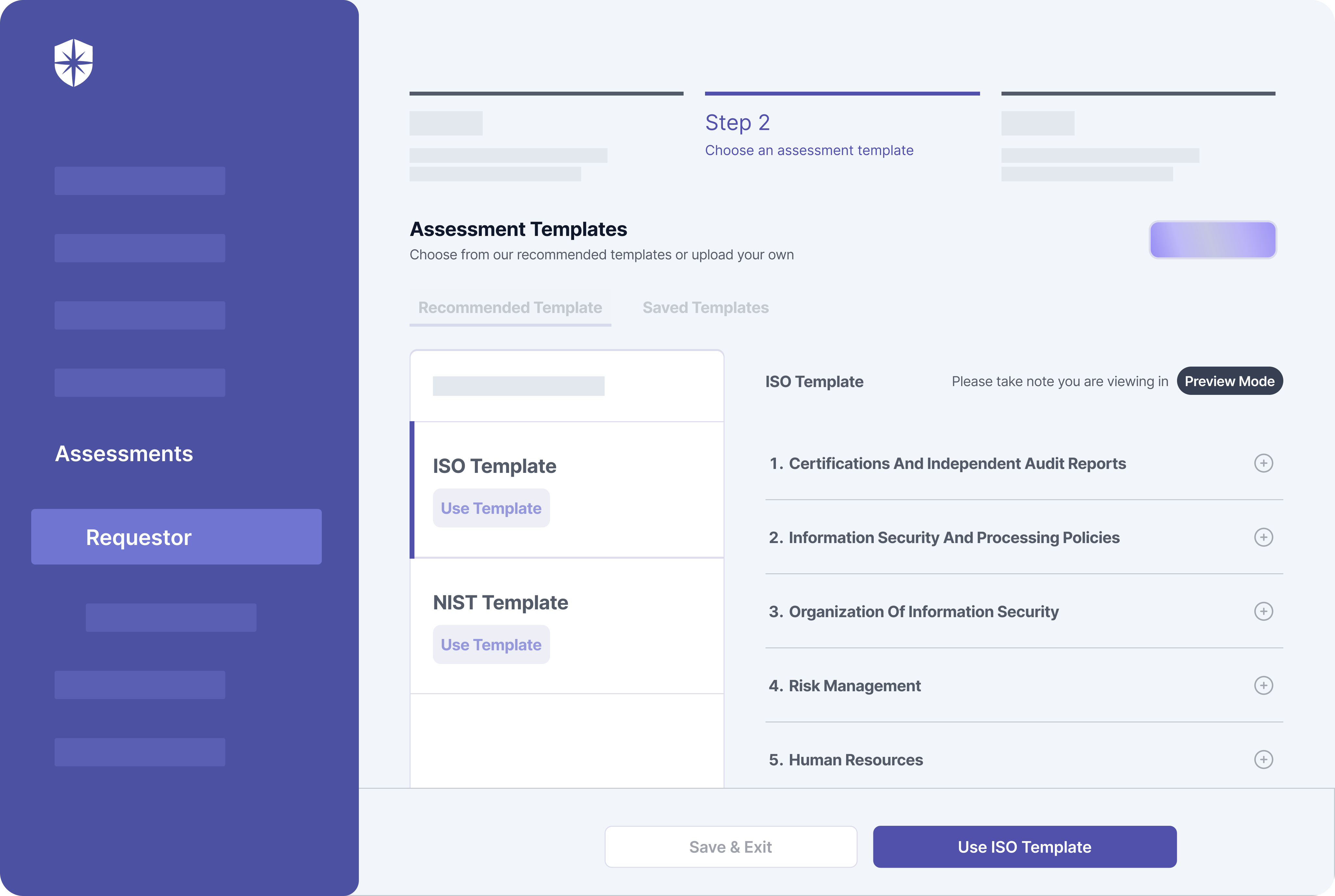
Your team can do this by streamlining critical processes of your vendor risk management program with Cyber Sierra. For instance, you get the NIST and ISO TPRM assessment frameworks built into our interoperable cybersecurity platform.
With these critical assessment frameworks in one place, your team can assess, onboard, manage, and mitigate vendor risks much faster:




A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.