Top 10 Alternatives to Wiz in 2023























Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
Top 10 Alternatives to Wiz in 2023
Do you want to find a solution that will strengthen your data security and compliance management techniques?
While Wiz has indeed positioned itself as a trusted choice for addressing compliance, it may not always serve as the best option for every organization’s unique circumstances.
If you’re still working to determine which compliance management software will be the best fit for your organization, it may be helpful to consider some of the Wiz alternatives listed below. We’ve compiled this list based on considerations such as functionality, pricing and customer satisfaction.
In this blog post, we will reveal ten viable replacements for Wiz, each demonstrating its unique edge over their rivals.
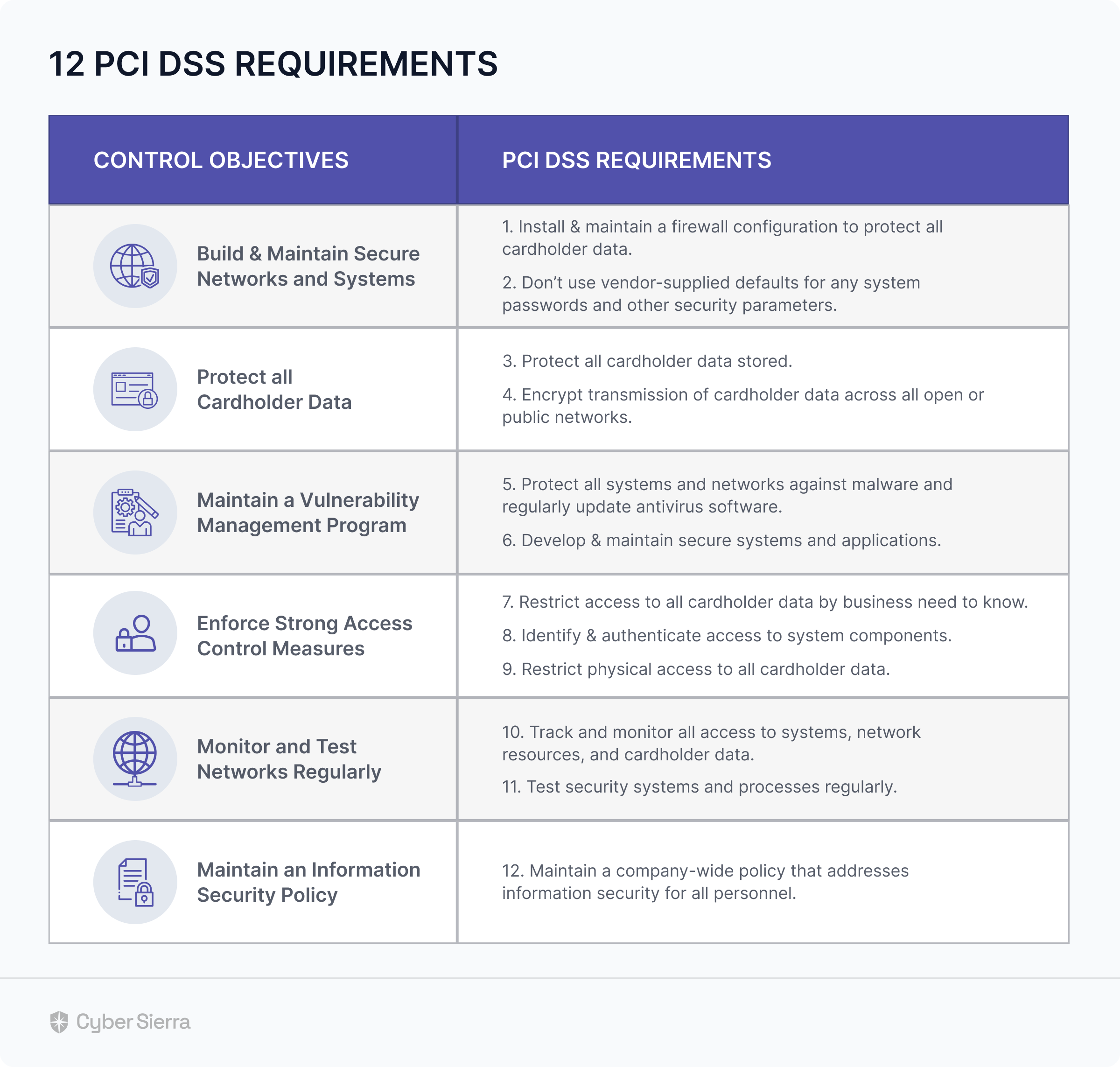
Top 10 Wiz Alternatives: Key Features, Pricing Plans, and More
Here are the top 10 alternatives to Wiz that we have shortlisted for you:
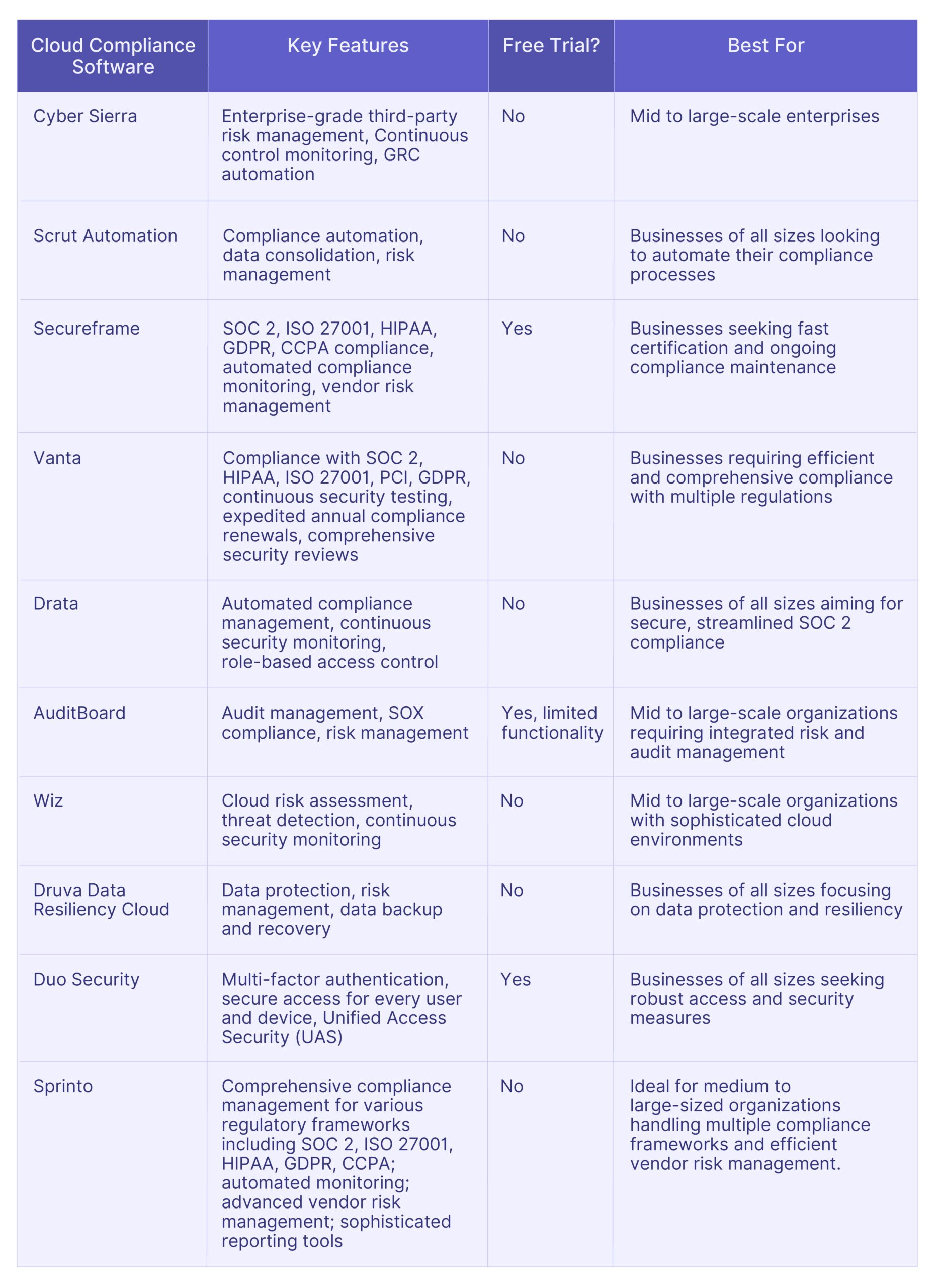
- Cyber Sierra
- Vanta
- Scrut
- Drata
- Sprinto
- AuditBoard
- Secureframe
- Acronis Cyber Protect Cloud
- Druva Data Resiliency Cloud
- Duo Security
Let’s look at them one by one.
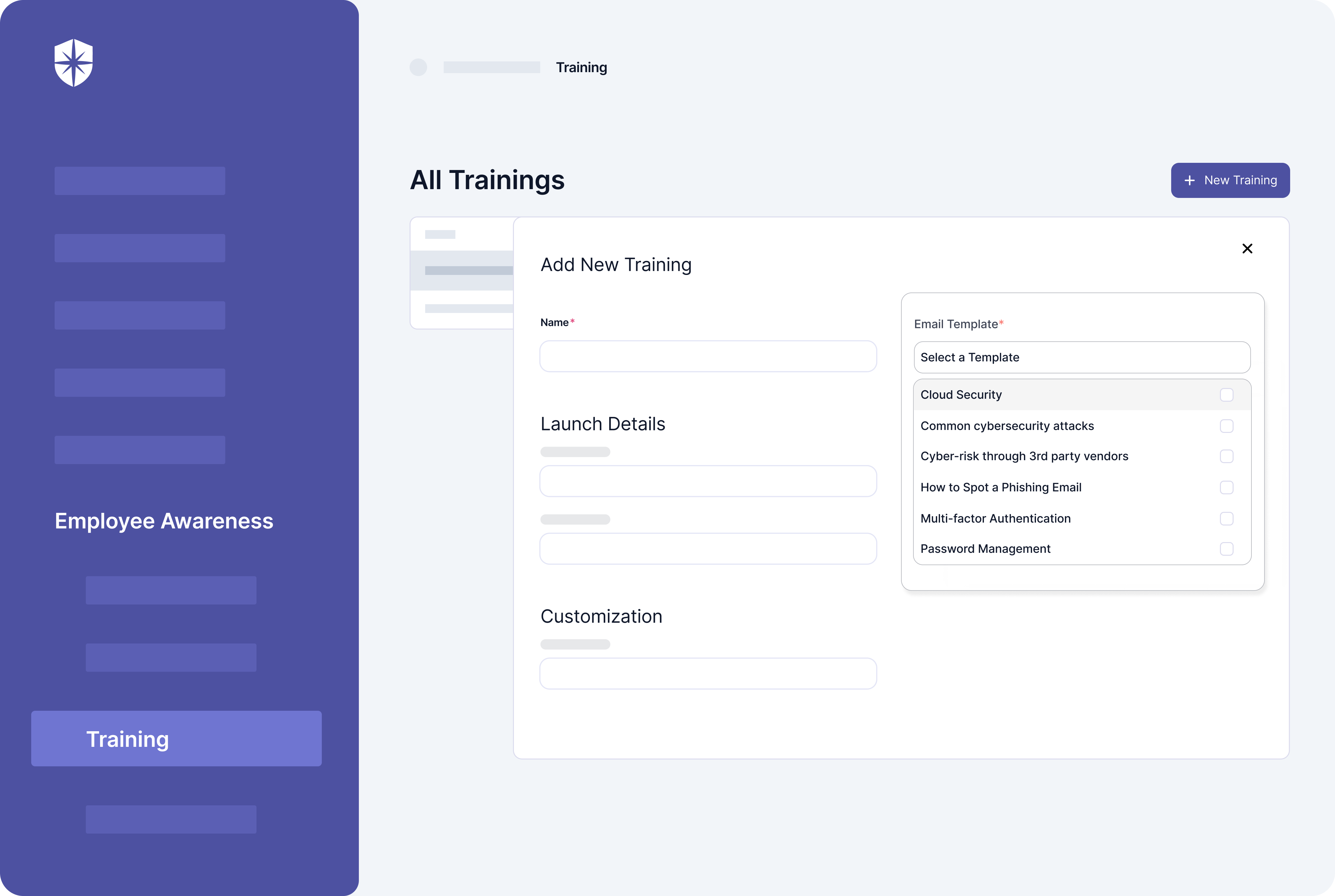
1. Cyber Sierra

Cyber Sierra offers a unique cybersecurity offering and has been made expressly to meet the needs of Chief Information Security Officers (CISOs), tech leaders, and others working in data protection.
A distinct feature of Cyber Sierra is its smooth integration of myriad security elements, resulting in a total cybersecurity security solution.
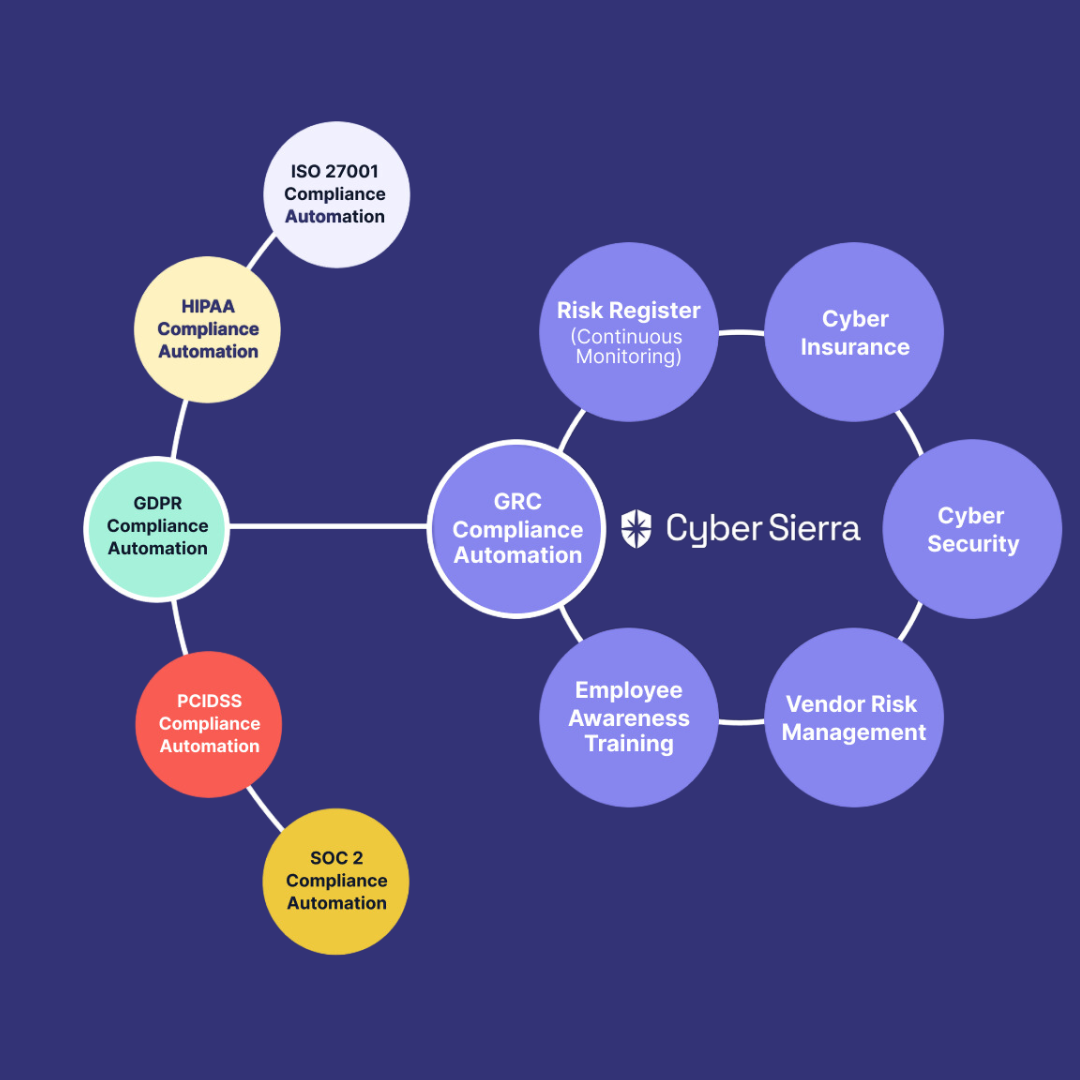
It combines governance, risk handling, cybersecurity compliance, cyber insurance offerings, threat analysis, and employee training modules into a single platform, considerably reducing the scatter often associated with cybersecurity management.
Key Features
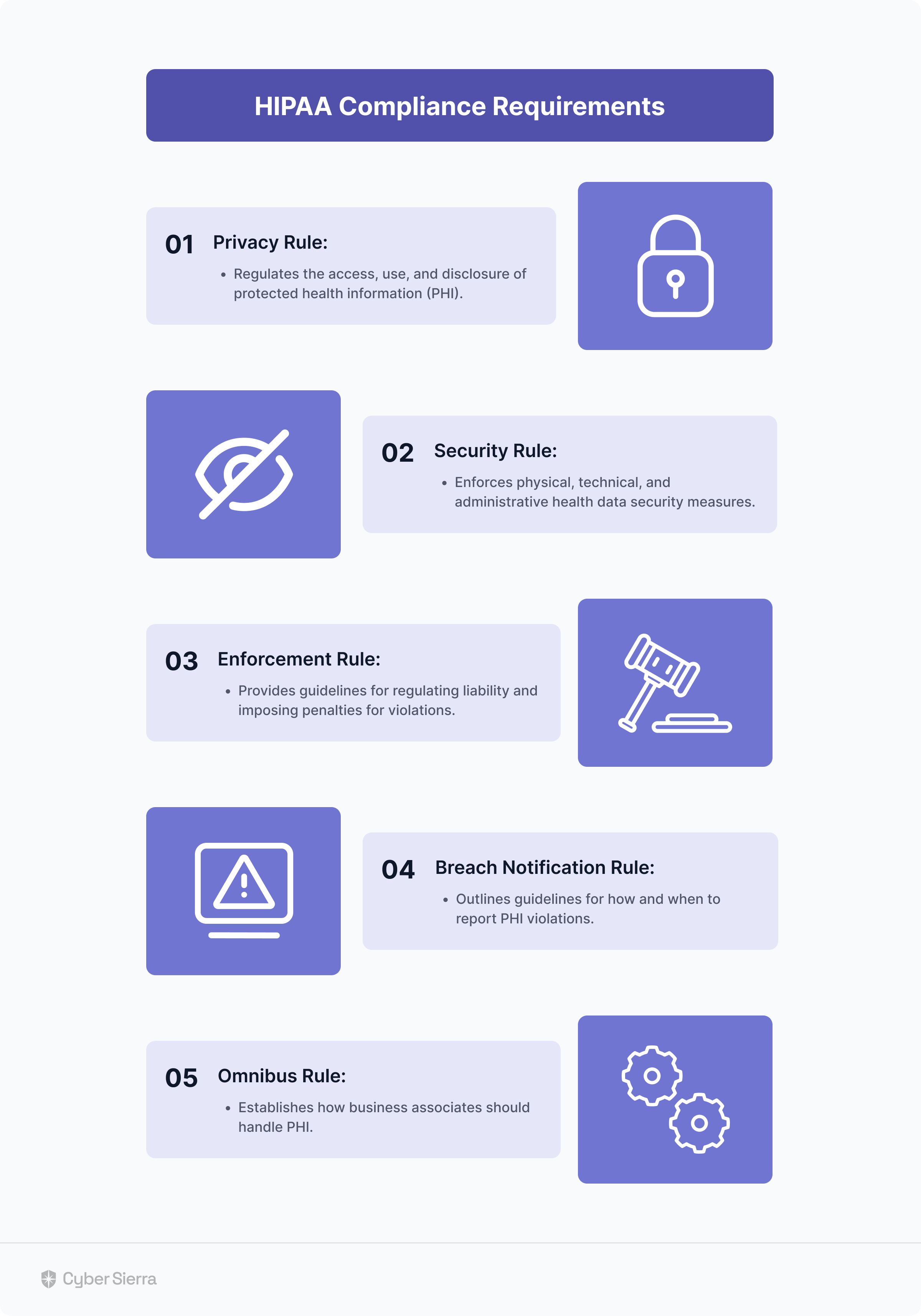
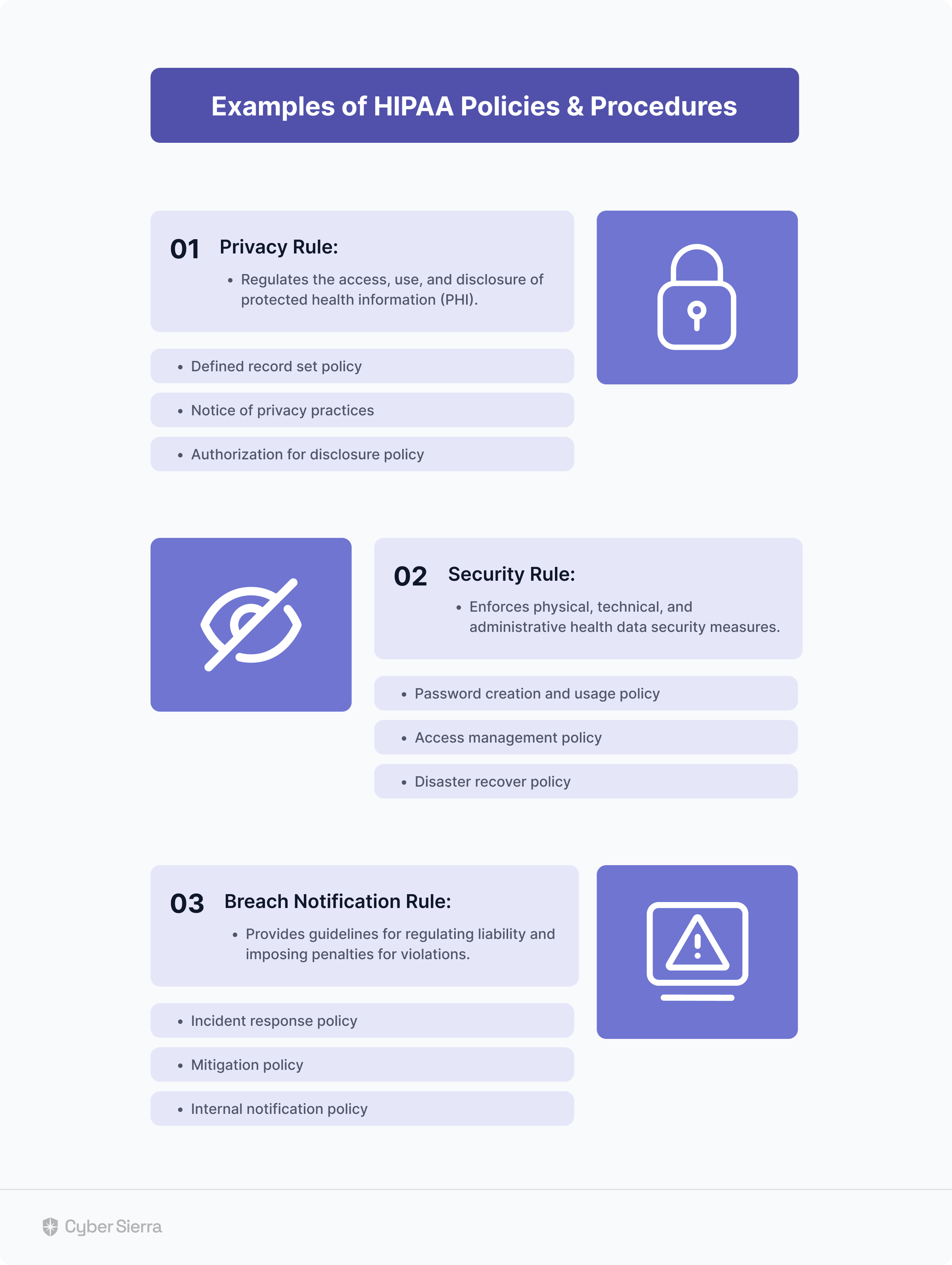
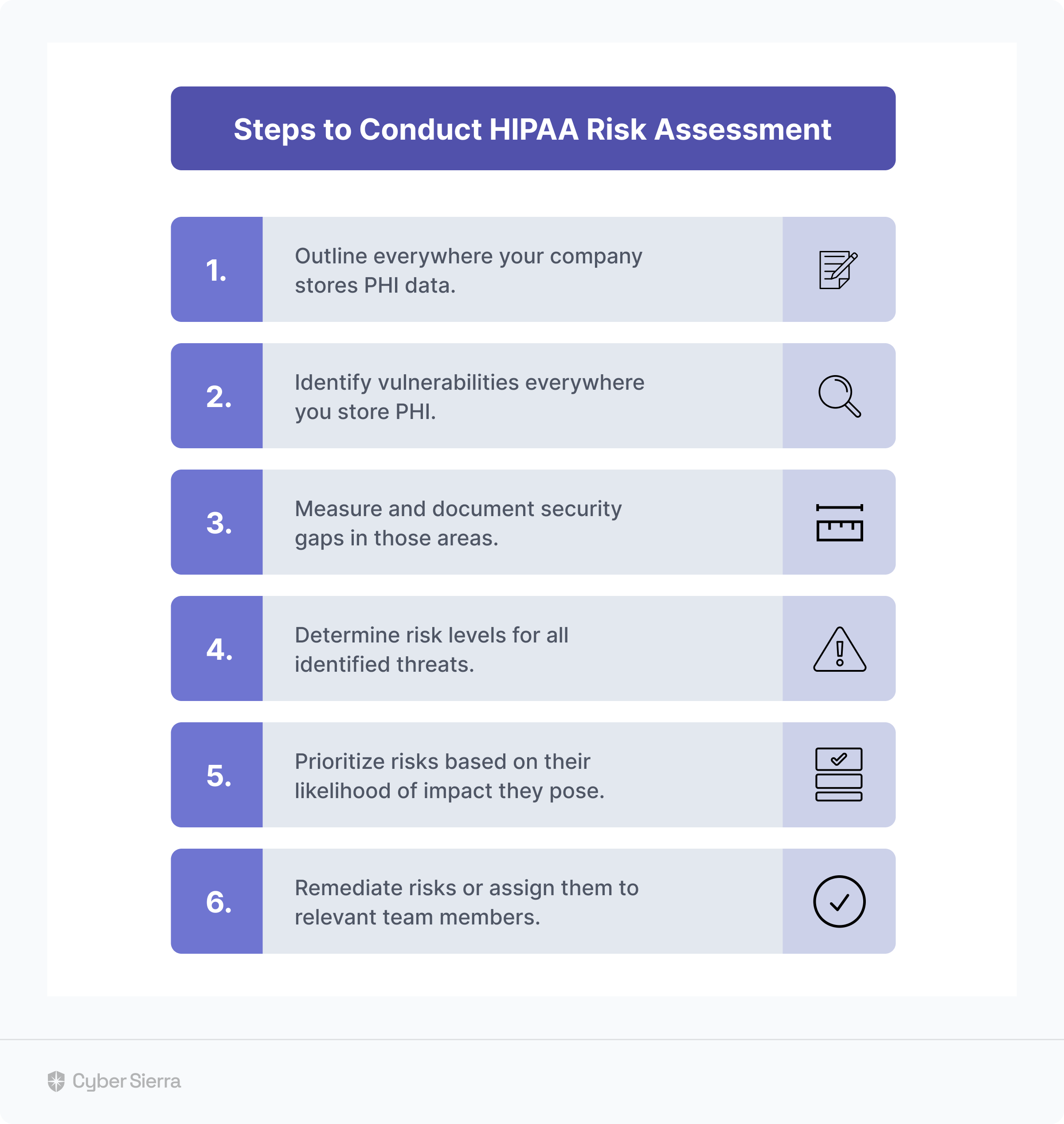
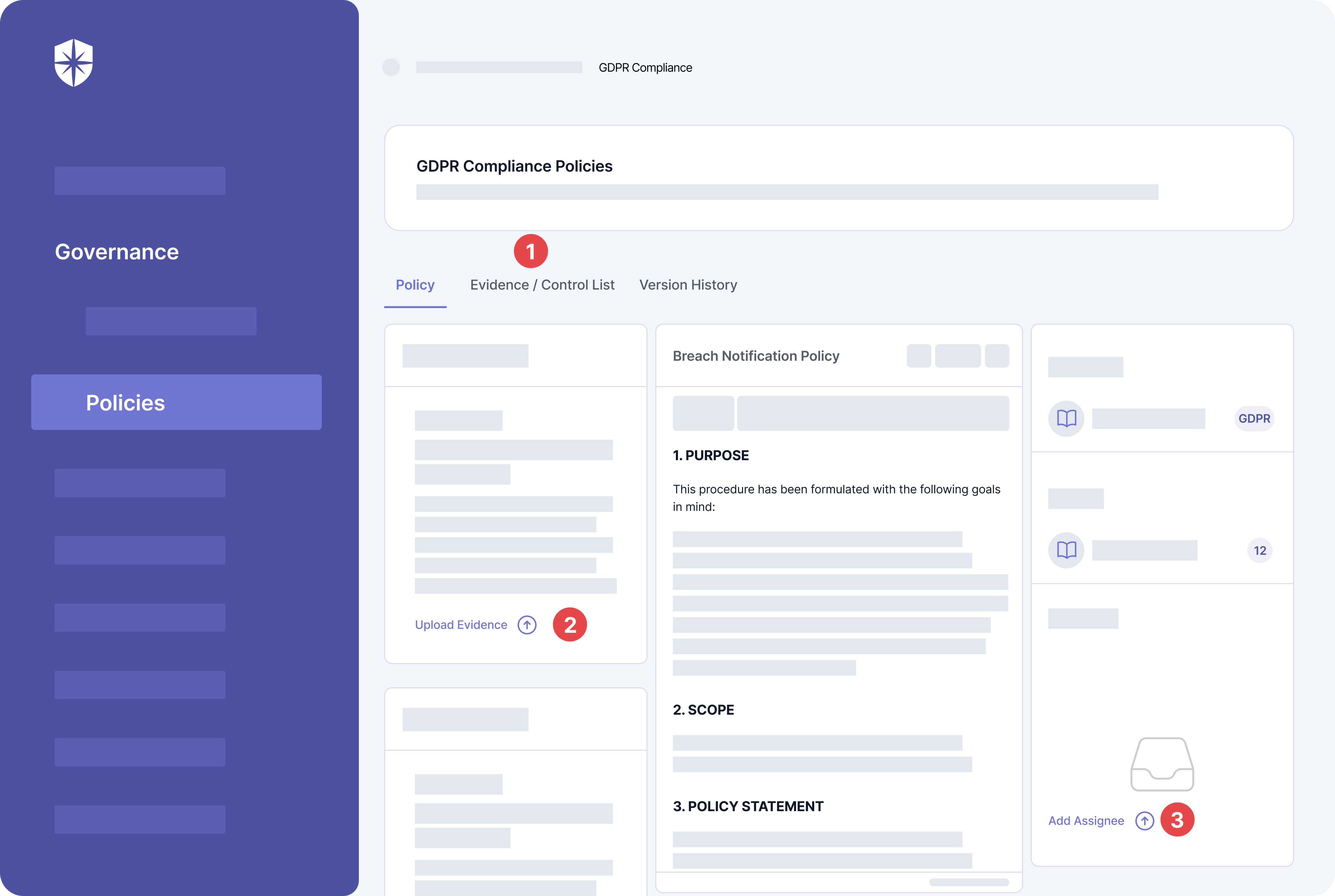
- Universal Governance: Helps companies meet widely recognized compliance standards such as ISO 27001, SOC 2, HIPAA, GDPR, and PDPA.
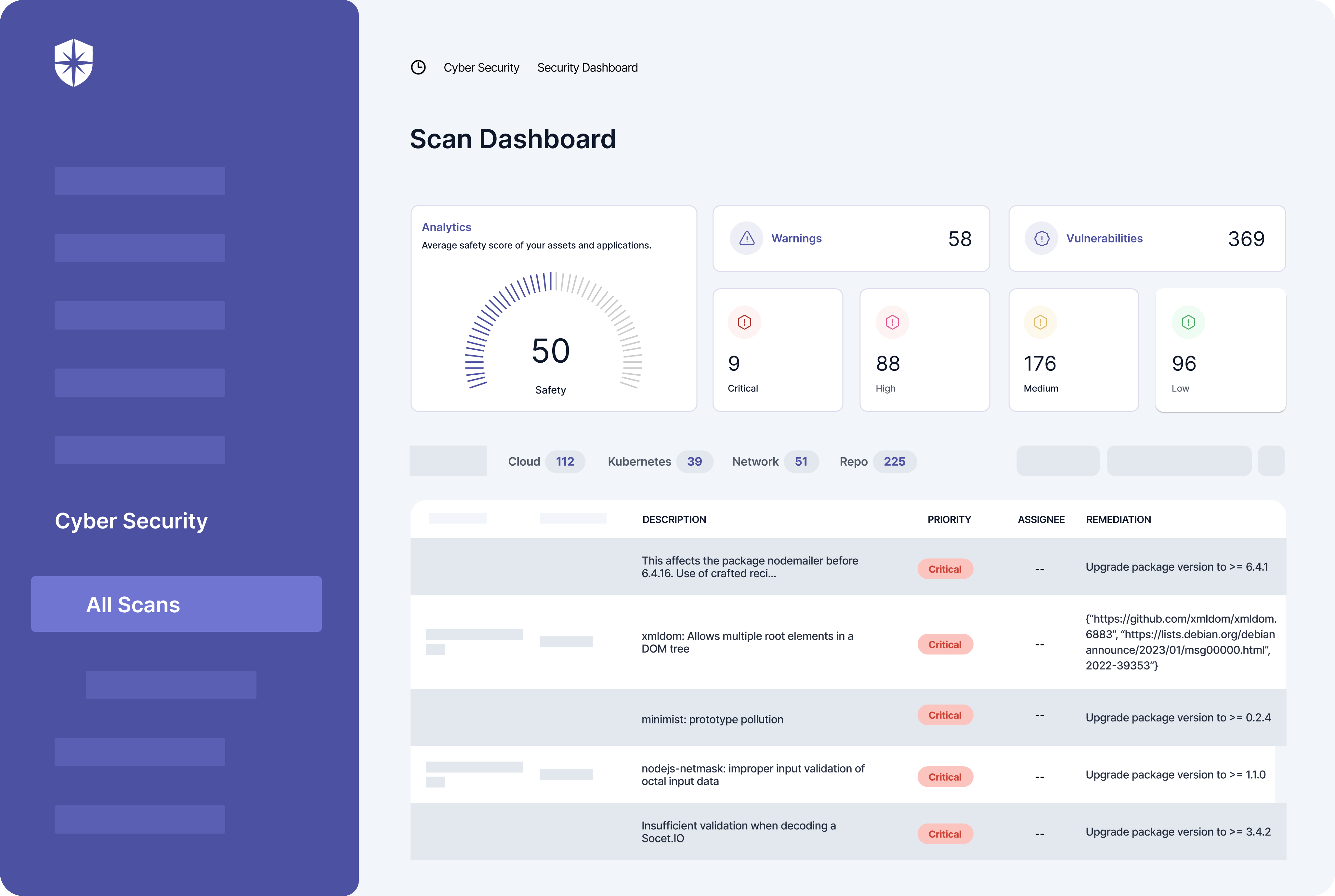
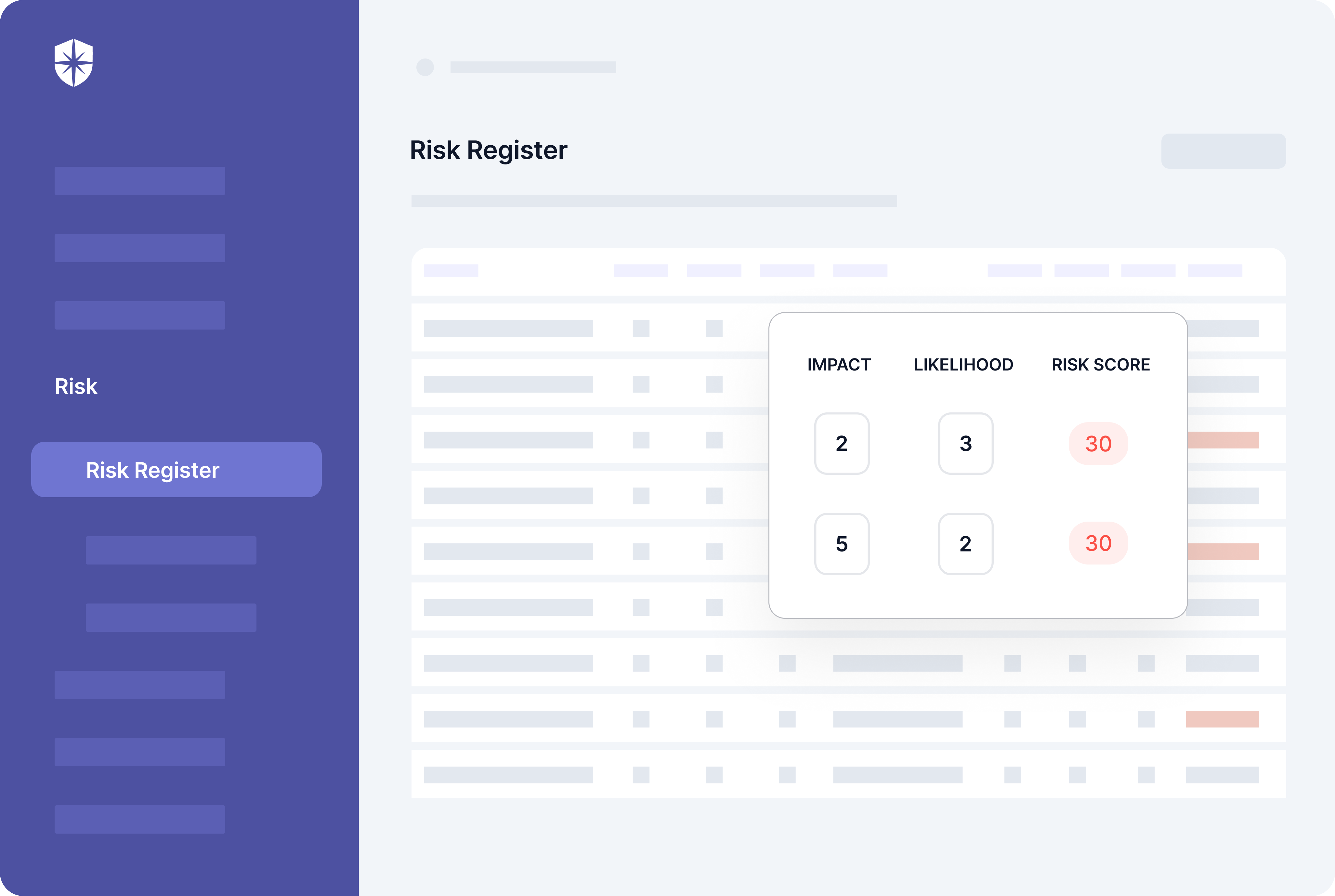
- Cybersecurity Health Examination: Carries out in-depth reviews and identification of threats connected to your digital assets.
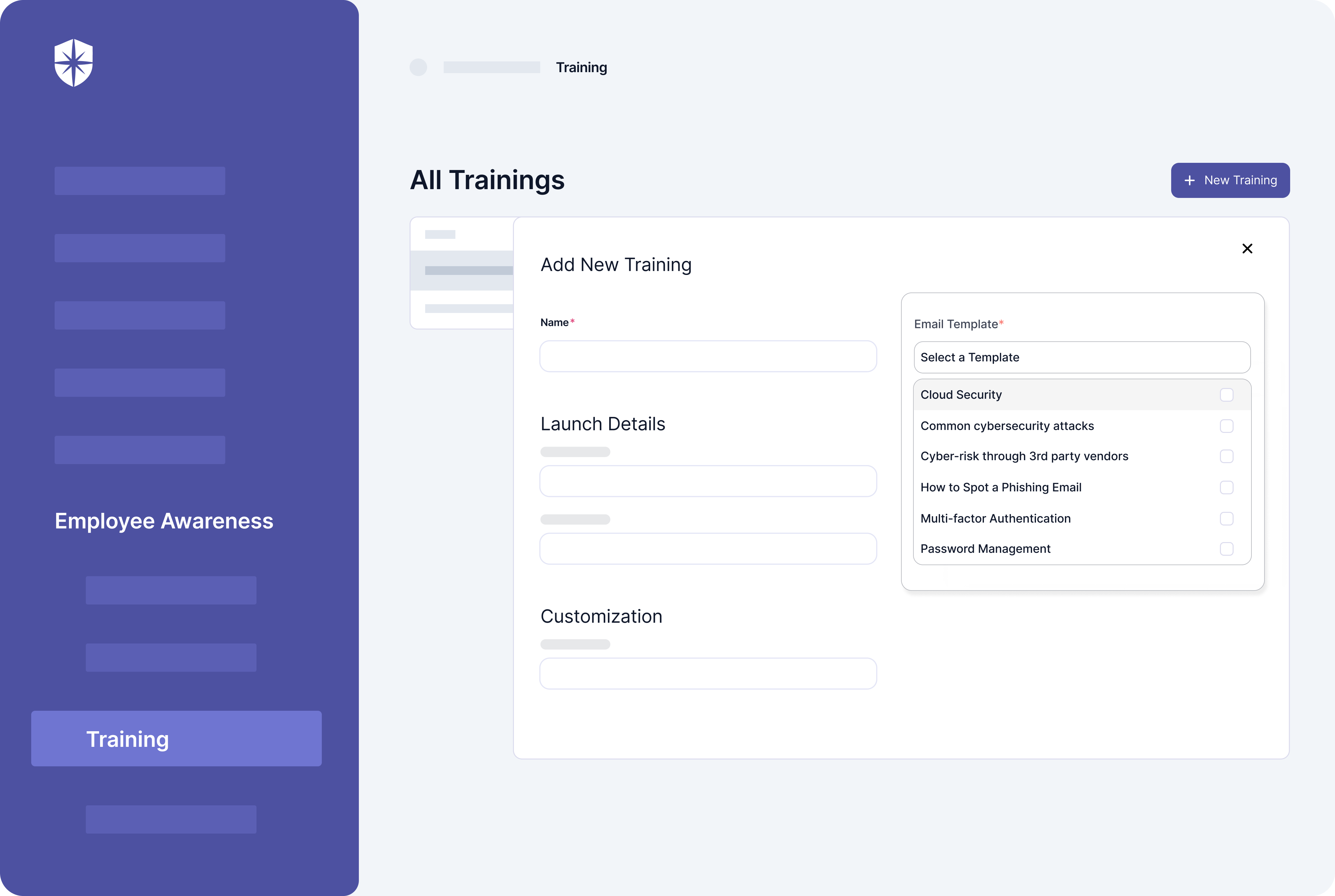
- Employee Security Instruction: Offers learning materials that help employees recognize and ward off phishing attempts.
- Third-Party Risk Supervision: Streamlines the security clearance process for suppliers and ensures regular tracking of potential dangers.
- Continuous controls monitoring: Monitors in near real-time the security controls, flagging off controls breaks and risk mitigation strategies.
Strengths
- Comprehensive Security Solution: Integrates governance, risk management, cybersecurity compliance, cyber insurance offerings, threat context, and staff training modules within one neat platform.
- Continuous Surveillance: Active, always-on risk monitoring, threat projection, and risk grading.
- Third-party risk management: Handles the complexity of managing third-party relations and diminishes the linked risks.
Weaknesses
- The platform is relatively new in the market.
Optimal For
Cyber Sierra perfectly aligns with both established companies and startups facing regulatory compliance, data safety, and such like challenges.
Additionally, it favors companies seeking to coordinate their cybersecurity, governing, and insurance policies, thereby transitioning from multiple vendors to one integrated, smart platform.
2. Vanta



Vanta distinguishes itself as a platform devoted to security and compliance management, with explicit expertise in simplifying processes for SOC 2 compliance. It highlights the fundamental importance of security in a company’s technical environment by promoting continual monitoring and automation of compliance procedures. This strategic approach drastically minimizes the time and expenses required for SOC 2 certification readiness.
Key Features
- Continuous Monitoring: By delivering constant security surveillance, Vanta guarantees real-time compliance, which allows companies to keep their security status current and robust at all instances.
- Automation: Vanta speeds up the SOC 2 certification process by automating compliance duties, which streamlines workflows and significantly cuts down manual work.
- Integration: Vanta offers smooth integration with well-known services and platforms, including AWS, GCP, Azure, and more. Such broad integration possibilities ensure flexibility across different technological environments.
Strengths
- Time Efficiency: Vanta considerably slashes the time and effort spent on SOC 2 compliance, liberating valuable resources for businesses.
- Integration: Its competency to link effortlessly with multiple popular platforms makes it highly adaptable to diverse tech environments.
Weaknesses
- Limited Scope: As Vanta shines in its SOC 2 compliance specialty, it may not fully serve other security frameworks or standards essential to certain businesses.
- Customization: Limited customization options may make Vanta less versatile for businesses with distinctive compliance needs or those craving bespoke experiences.
Ideal For:
Vanta is a favored choice for medium to large enterprises, especially those belonging to sectors with strict security compliance norms. This includes sectors like technology, healthcare, and finance, where adherence to strict security standards such as SOC 2, ISO 27001, HIPAA, PCI, and GDPR is a fundamental requirement.
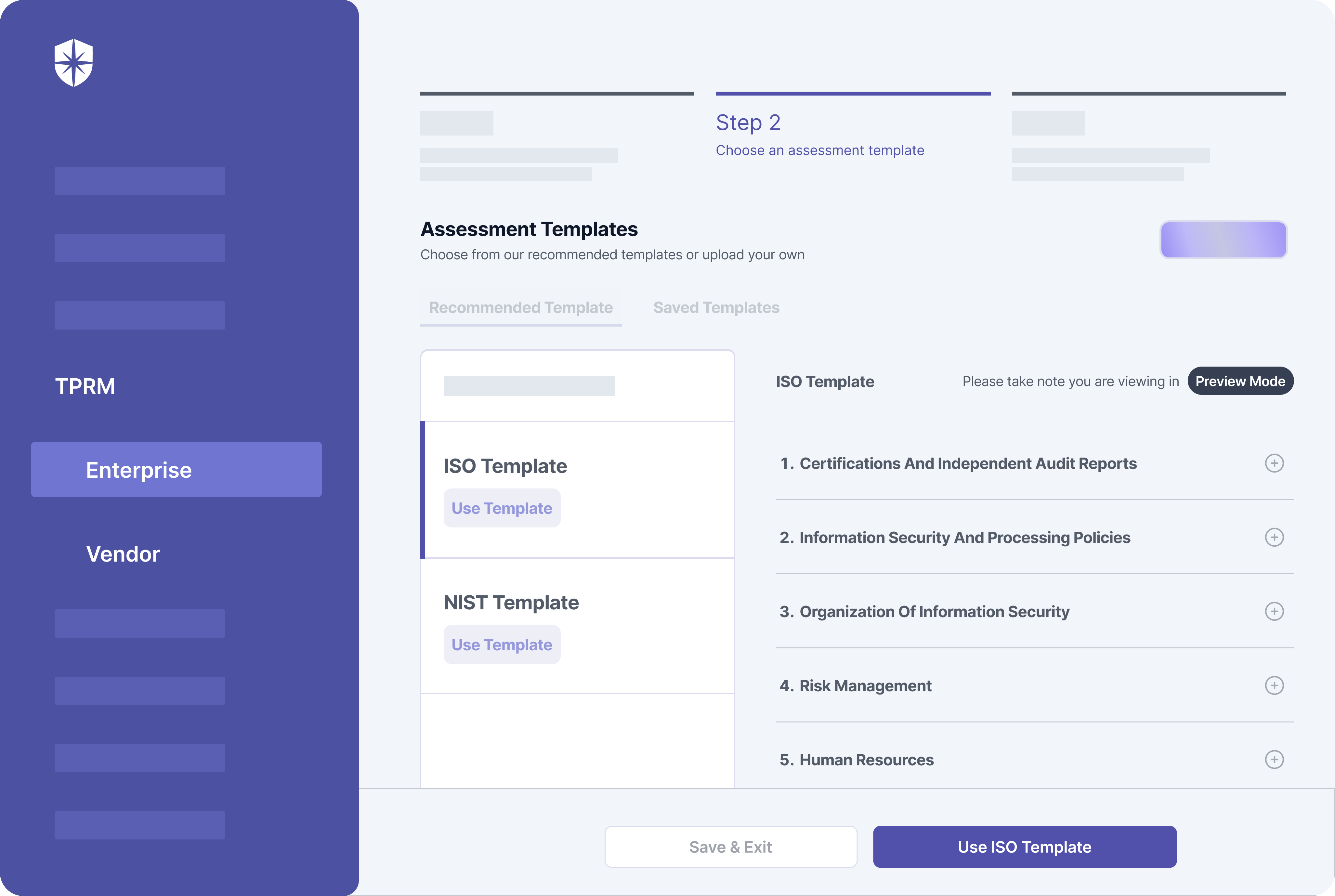
3. Scrut Automation






As a cloud security platform with a strong emphasis on cloud configuration testing automation, Scrut Automation offers sturdy cloud-native defenses for AWS, Azure, GCP, and more.
Key features
- Automated cloud configurations testing: Scrut Automation persistently tests your cloud configurations against an extensive list of 150+ CIS benchmarks.
- Historical records: The platform builds a historical overview of your security state, enabling you to track progress over time.
- Integration: Effortless integration is facilitated with leading cloud platforms like AWS, Azure, and Google Cloud.
Strengths
- In-depth security coverage: Equipped to secure your cloud environment using over 150 CIS benchmarks.
- Time-efficient: Speeding up information security progression, it automates demanding tasks and prioritizes remediations.
Weaknesses
- Learning curve: Especially for users new to cloud security configurations, understanding and using certain features might take time.
- Limited customization: Customization and personalization options can be limited, based on unique user requirements.
Best for
Organizations relying on cloud services from AWS, Azure, GCP, and similar providers will find Scrut Automation an ideal choice. Its wide-ranging security and compliance coverage make it well-suited for large enterprises requiring solid cloud security. However, medium and small businesses aiming to bolster their cloud security while favoring automation will also benefit greatly.
4. Drata





Drata operates as a security and compliance management platform, offering exhaustive support for companies aiming to attain and preserve SOC 2 compliance. Its audit management software systematizes the process of tracking, managing, and overseeing essential technical and operational controls for SOC 2 certification.
Key Features
- Asset management: Companies can identify and oversee assets like servers, devices, and applications seamlessly with Drata’s asset management feature.
- Policy & procedure templates: Ready-to-use templates on the platform facilitate the swift generation of internal compliance paperwork.
- User access reviews: Drata performs frequent user access evaluations to enforce appropriate access governance.
- Security training: The platform supplies continuous workforce training and phishing simulations to increase awareness of current security threats and practices.
Strengths
- Automated evidence collection: By automating the evidence collection process, Drata cuts down on manual effort and the likelihood of human errors.
- Exceptional customer support: Clients benefit from the platform’s highly responsive and well-versed support team at every step of the compliance process.
Weaknesses
- Onboarding process: Users may experience a longer and more complicated onboarding process, potentially leading to a slow initial setup.
- Complex functionality: Drata’s broad functionality suite may prove problematic for non-technical users.
- Scalability: As a relatively new market player, Drata may struggle to address the more complex compliance requirements of larger organizations.
- Pricing: Limited-budget businesses, especially smaller ones, might find Drata’s pricing model challenging.
Best Suited For
Drata is especially beneficial for companies working towards attaining and maintaining SOC 2 compliance with minimized manual intervention. With its superior automation features, Drata is a favorable option for businesses desiring a more streamlined audit experience.
5. Sprinto






Sprinto is a comprehensive security and compliance automation platform. Its main purpose is to aid businesses in adhering to various compliance frameworks, such as SOC 2, ISO 27001, GDPR, HIPAA, and PCI-DSS. The platform’s customization options and real-time monitoring capabilities enable companies to perpetually assess and adeptly manage their security and compliance position.
Key Features
- Asset Management: Sprinto’s security compliance component allows businesses to combine risk elements, systematize entity-level controls, and run fully automated checks.
- Policy Implementation: The platform’s automated workflows, policy templates, and training modules are designed to meet various security compliance needs smoothly.
- Exceptional Support: Sprinto’s team of experts guide companies through each phase of the compliance process, from risk assessment to the execution of audit requirements.
- Cloud Compatibility: Sprinto seamlessly integrates with numerous modern business cloud services, allowing for extensive risk assessment and control mapping.
Strengths
- Automation: Sprinto’s robust automation features considerably streamline the effort required to achieve compliance.
- Broad Compliance Coverage: Sprinto supports an extensive array of compliance frameworks, giving businesses the capability to manage multiple compliances in parallel.
- Expert Support: Sprinto commits to providing expert-led implementation support from the get-go, assuring that suitable controls and practices are in place.
- Integration Capability: Sprinto’s ability to integrate smoothly with various business cloud services facilitates proficient mapping of controls and wide-ranging risk assessments.
Weaknesses
- Adaptive Requirements: To make the most of automated checks and continuous monitoring, businesses may need to adapt to the workings of the Sprinto platform.
- Customer Support: As per some user reports, Sprinto could enhance its customer service, particularly in the area of response times.
Best For
Sprinto is an ideal choice for rapidly scaling cloud businesses keen on making their security compliance processes more streamlined. With its potent automation capabilities and vast compliance coverage, it becomes a prime option for businesses seeking a more effortless and less hands-on method of preserving security compliance.
6. AuditBoard




AuditBoard is a versatile audit, risk, and compliance management platform designed to make complex tasks easy for businesses. It facilitates the management of intricate audits, compliance, and risk management operations while fostering accessibility and collaboration.
Key Features
- Integrated Control Management: AuditBoard enables full management of audit, risk evaluation, control testing, issue tracking, and reporting features.
- Operational Auditing: With AuditBoard, businesses have access to integrated tools that make performing internal and operational audits a seamless process.
- Risk Assessment: AuditBoard aids in effortlessly identifying and managing risks throughout the organization.
- Real-Time Reporting: The platform ensures users have access to real-time insights and customized reports, aiding in audit progress tracking and issue resolution.
Strengths
- Ease of Use: AuditBoard is commended for its easy-to-navigate system, simplifying complex audit and risk assessment procedures.
- Collaboration: The platform’s collaboration tools improve communication between internal teams and external auditors.
Weaknesses
- Customer Support: There’s room for improvement in AuditBoard’s customer support efficiency and response times, as reported by some users.
- Less Intuitive Navigation: Some users have found the system’s navigation less intuitive, particularly when managing multiple projects.
- Expensive: The platform presents a broad suite of features accompanied by a high price tag, which may be unviable for small to medium-sized businesses.
Best for
Large corporations looking for a holistic audit and risk management solution will find AuditBoard optimal. It’s an unmatched tool for businesses conducting regular internal and operational audits and needing real-time insights into their audit and risk progression.
7. Secureframe






Secureframe is an effective compliance management solution that streamlines processes involved in achieving SOC 2 and ISO 27001 compliances. It offers ongoing and efficient monitoring for a wide range of services like AWS, GCP, and Azure.
Key Features
- Continuous Compliance Monitoring: Enables unceasing compliance adherence for a multitude of services.
- Automation: Optimizes security compliance responsibilities effectively, saving ample time and resources.
- Integration Features: Collaborates effortlessly with prevalent cloud services such as AWS, GCP, and Azure.
Strengths
- Significant Time Saver: Drastically slashes the time customarily needed for documenting and managing compliance practices that can span weeks.
- Integrated Solution: Melds seamlessly with beloved cloud services, presenting distinct advantages for companies utilizing these infrastructures.
Weaknesses
- Limited Customization: As per certain user feedback, Secureframe could improve customization flexibility to cater better to businesses’ unique needs.
Best for
Secureframe is a stellar platform for companies of all sizes looking to streamline their SOC 2 and ISO 27001 compliances. Companies using AWS, GCP, and Azure for their cloud services stand to gain significantly from its robust integration capacities.
8. Acronis Cyber Protect Cloud



Acronis Cyber Protect Cloud is a thorough cybersecurity solution that unifies backup, disaster recovery, AI-enhanced malware, ransomware protection, remote support, and security in one platform. It’s devised to furnish a multi-layered approach to safeguard data across numerous devices and surroundings.
Key Features
- Backup and disaster recovery: Acronis pledges to keep your data safe with its backup capacities, providing disaster recovery avenues when major complications arise.
- Cyber security: Leverages artificial intelligence and machine learning methodologies to detect and react to novel threats.
- Patch management: Discerns and instantly updates obsolete software editions, diminishing vulnerability dangers.
- Remote assistance: Acronis includes remote help, granting users and administrators the ability to rapidly tackle issues from any place.
Strengths
- Full-scale Protection: Delivers multi-tiered protection by integrating backup, security, and disaster recovery options.
- Ease of Use: The system has an accessible interface and user-friendly navigation that users appreciate.
- Reliable Backup and Recovery: Acronis demonstrates reliability in data backup and recovery, satisfying numerous users with its performance in this scope.
Weaknesses
- Performance Issues: Some users detected occasional sluggishness in the application, particularly during heavy backup procedures.
- Technical Support: A segment of users reported less satisfactory experiences and delays when dealing with the support team.
- Scarce Reporting Details: A few clients noted that the reporting aspect could be more comprehensive with added details for thorough analysis.
Best for
Acronis Cyber Protect Cloud is highly recommended for businesses placing emphasis on a robust and all-embracing cybersecurity stance. With its comprehensive approach, the solution proves advantageous for organizations operating in industries such as IT, retail, healthcare, finance, and other sectors where data protection is vital.
9. Druva Data Resiliency Cloud





Druva Data Resiliency Cloud is a cloud-oriented data protection and management tool using the SaaS methodology. It provides secure backup, disaster recovery, and information governance across a range of environments, including endpoints, data centers, and SaaS applications.
Key Features
- Unified Data Safeguarding: Druva offers reliable, consolidated backup and recovery solutions for endpoints, data centers, and SaaS applications.
- Disaster Bounceback: It equips businesses with a straightforward, quick, and cost-efficient model for on-call disaster recovery.
- Global Deduplication: Druva’s deduplication capability enhances storage and bandwidth efficiency, reducing costs, and boosting backup speeds.
- Security and Compliance: The solution adheres to a variety of regulations such as GDPR, providing encryption, access controls, and audit trails.
Strengths
- SaaS Utilization: As a cloud-based solution, Druva eases deployment, management, and scalability burdens on IT teams.
- Streamlined Data Management: Druva possesses a centralized hub for handling data protection activities across diverse settings, simplifying data management procedures.
- Economical: By eliminating hardware and infrastructure-associated costs, Druva proves cost-effective.
- Customer Assistance: Clients value Druva’s responsive and helpful customer support team.
Weaknesses
- Dealing with Large Data Sets: There are indications of performance decline when managing colossal data sets.
- Pricing Complexity: Users have indicated that Druva’s pricing structure can be convoluted and less than clear.
Best for
Druva Data Resiliency Cloud is a practical choice for businesses of all scales looking for a SaaS-focused, cost-convenient, and easy-to-use data protection service. It is particularly helpful for businesses with distributed infrastructures, including endpoints and a variety of data center applications.
However, businesses with large data processing needs might want to consider other options or evaluate Druva’s performance before making a commitment.
10. Duo Security





Duo Security, now a part of the Cisco ecosystem, is a cloud-anchored access security platform dedicated to shielding users, data, and applications from prospective security threats. By ensuring the identities of users and the security of their devices, it aligns access privileges with business safety and compliance needs.
Key Features
- Two-factor Authentication (2FA): Duo’s 2FA adds a layer of security for network and application access by mandating a secondary form of authentication along with the primary password.
- Device Trust: Duo delivers comprehensive visibility into all devices trying to access your applications, granting access only after verifying security standard compliance.
- Adaptive Authentication: Duo leverages adaptive policies and machine learning for secure access, which is predicated on user behavior and device insights.
- Secure Single Sign-On (SSO): Duo provides users with secure, seamless access to all enterprise applications via its SSO feature.
Strengths
- Ease of Deployment and Use: Duo’s implementation is straightforward and it comes with an easily navigable interface.
- Powerful Security: By employing two-factor authentication, Duo greatly decreases the likelihood of unauthorized access.
- Wide Integration: Duo demonstrates easy compatibility with various existing VPNs, cloud applications, and network infrastructure.
- Quality Customer Support: Duo’s excellent customer service is known for being reactive and providing effective solutions.
Weaknesses
- Limited Control Granularity: Users wanting specific controls or advanced customization options may find Duo Security lacking, especially when setting policies.
- Software Update Issues: Sporadic difficulties or interruptions have been reported by users following software updates.
- Pricing: The cost of Duo’s solution might be considered high for small businesses or startups.
- Interface Appeal: Despite being easy to use, the interface could be more visually engaging and contemporary.
Best for
Given its wide-ranging compatibility with various applications and devices, Duo is a valuable solution for organizations with a diverse range of software applications.
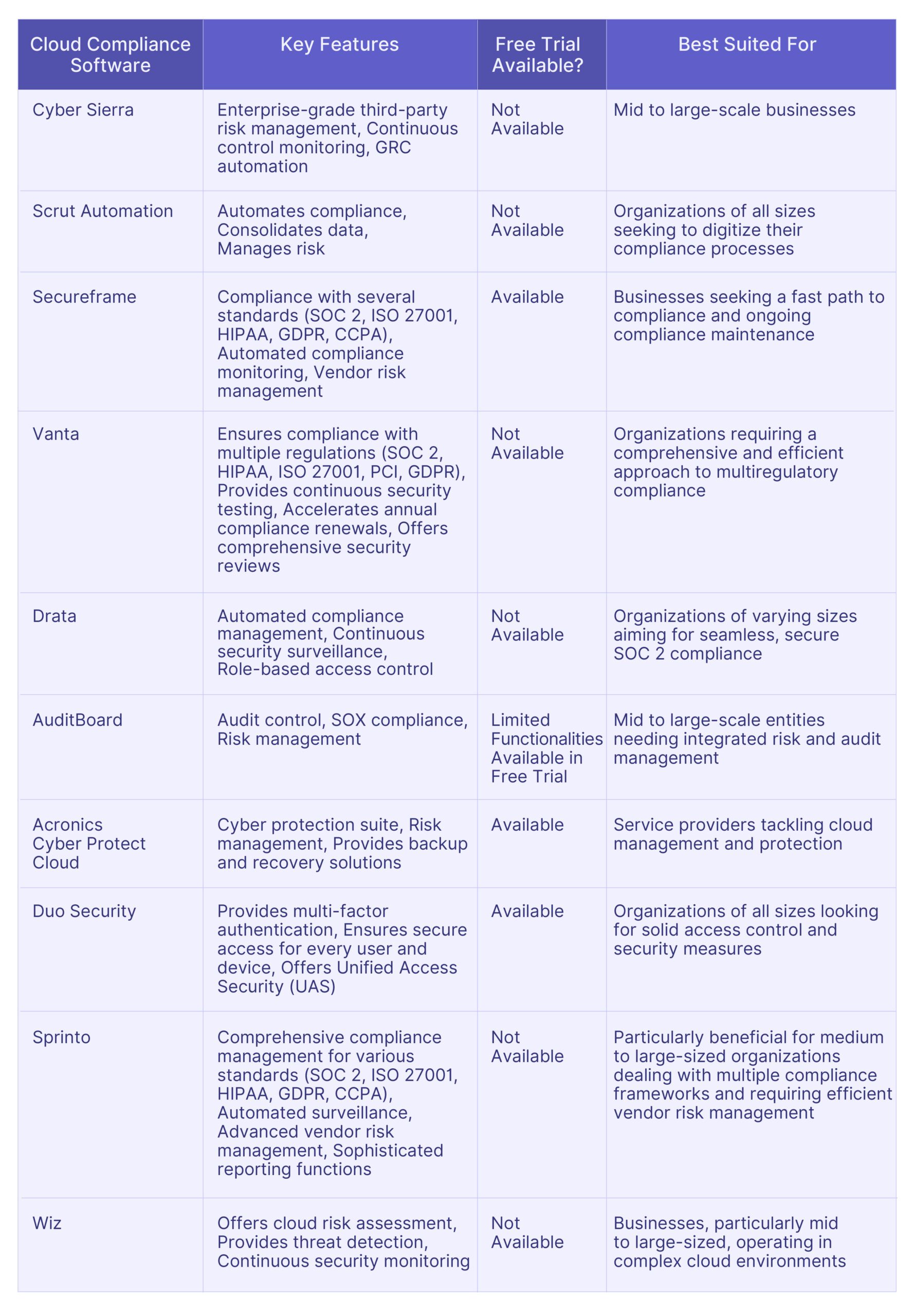
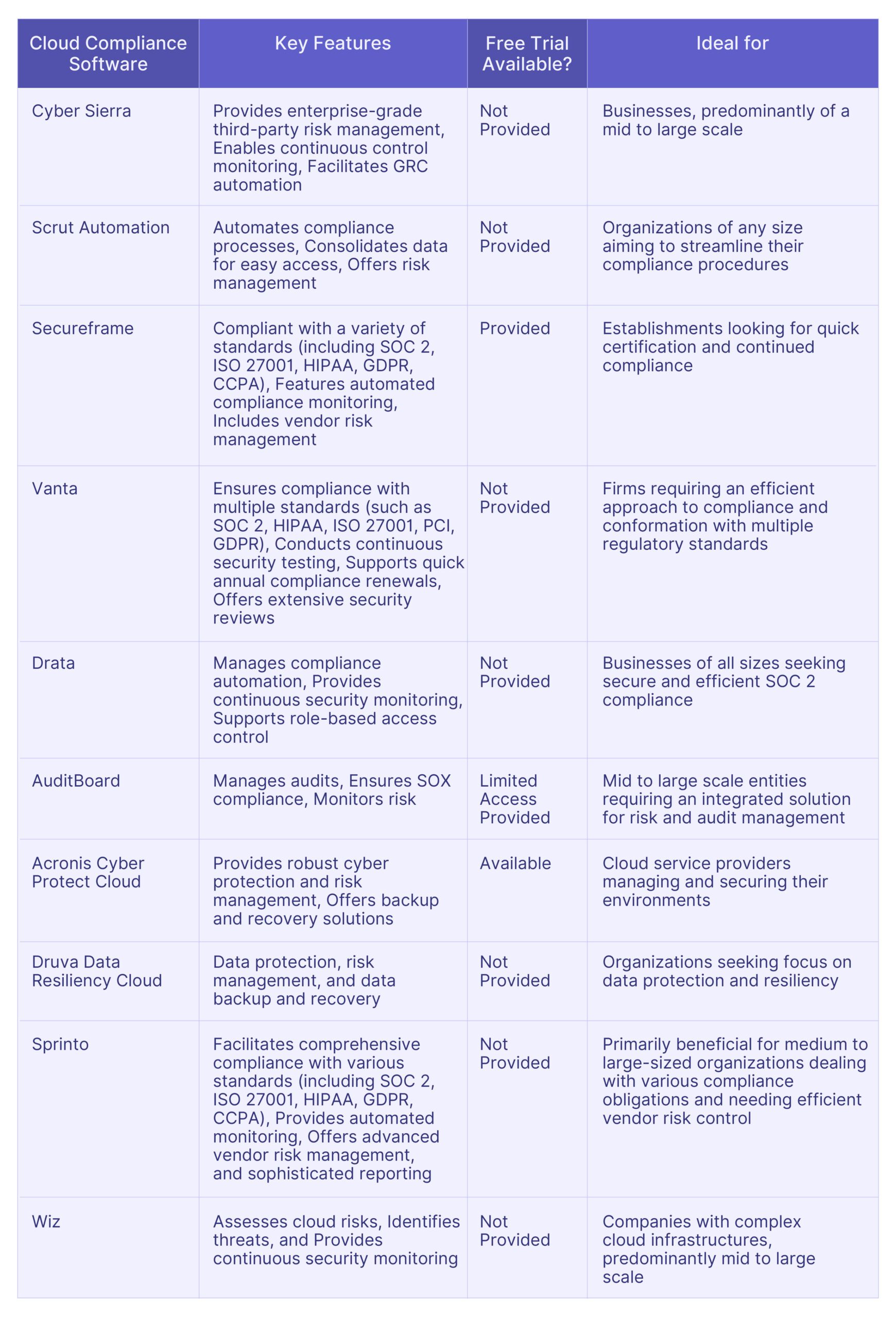
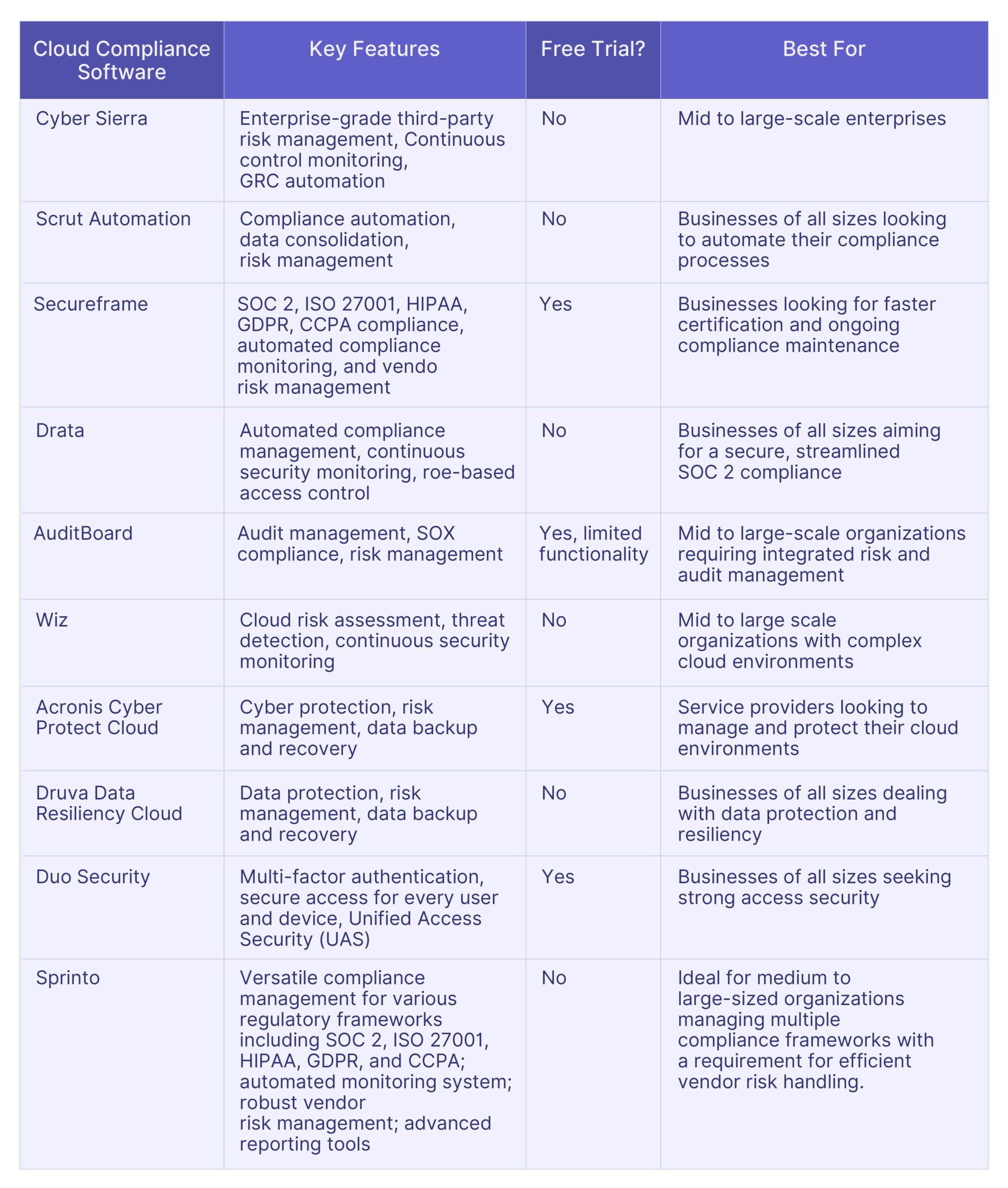
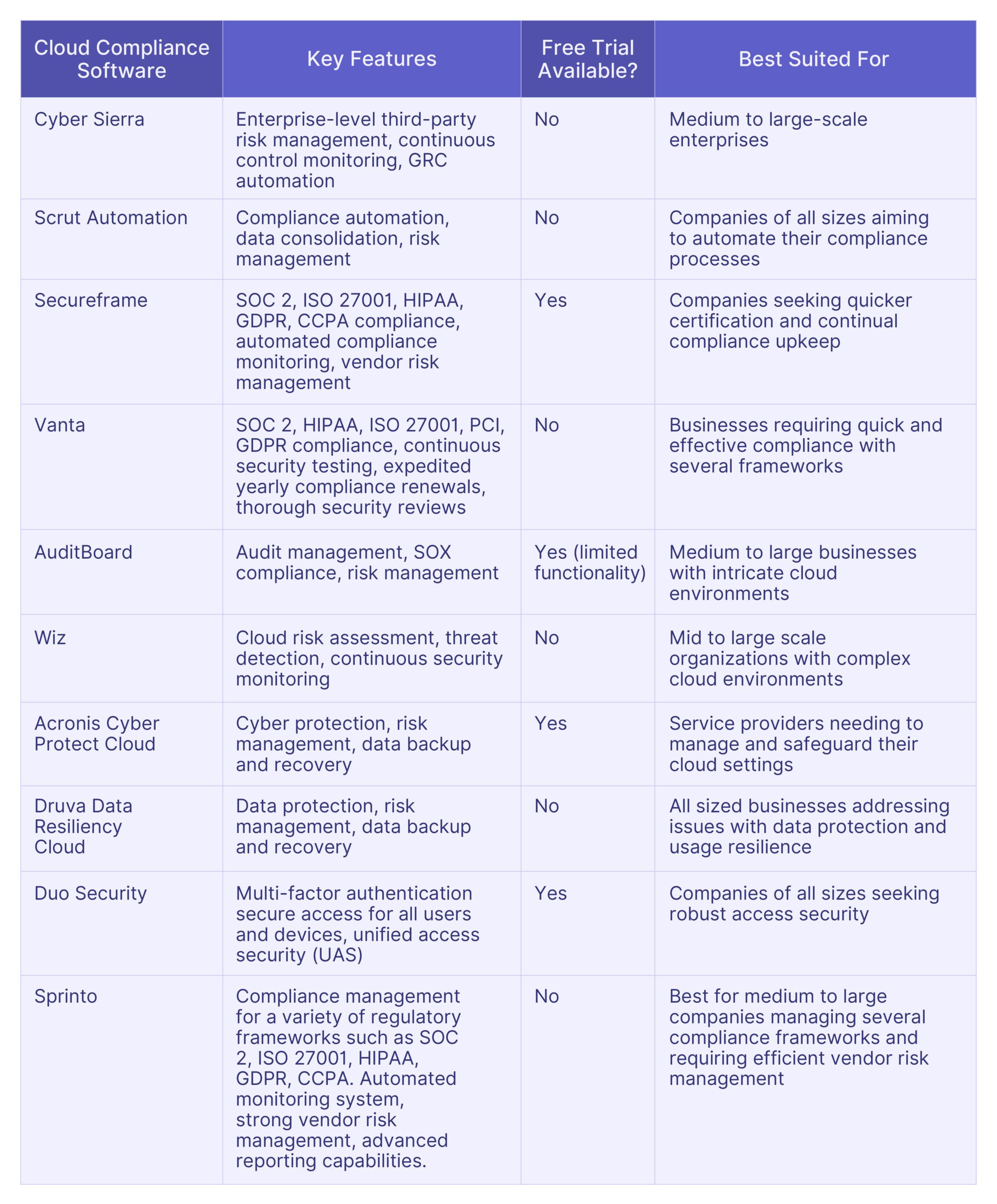
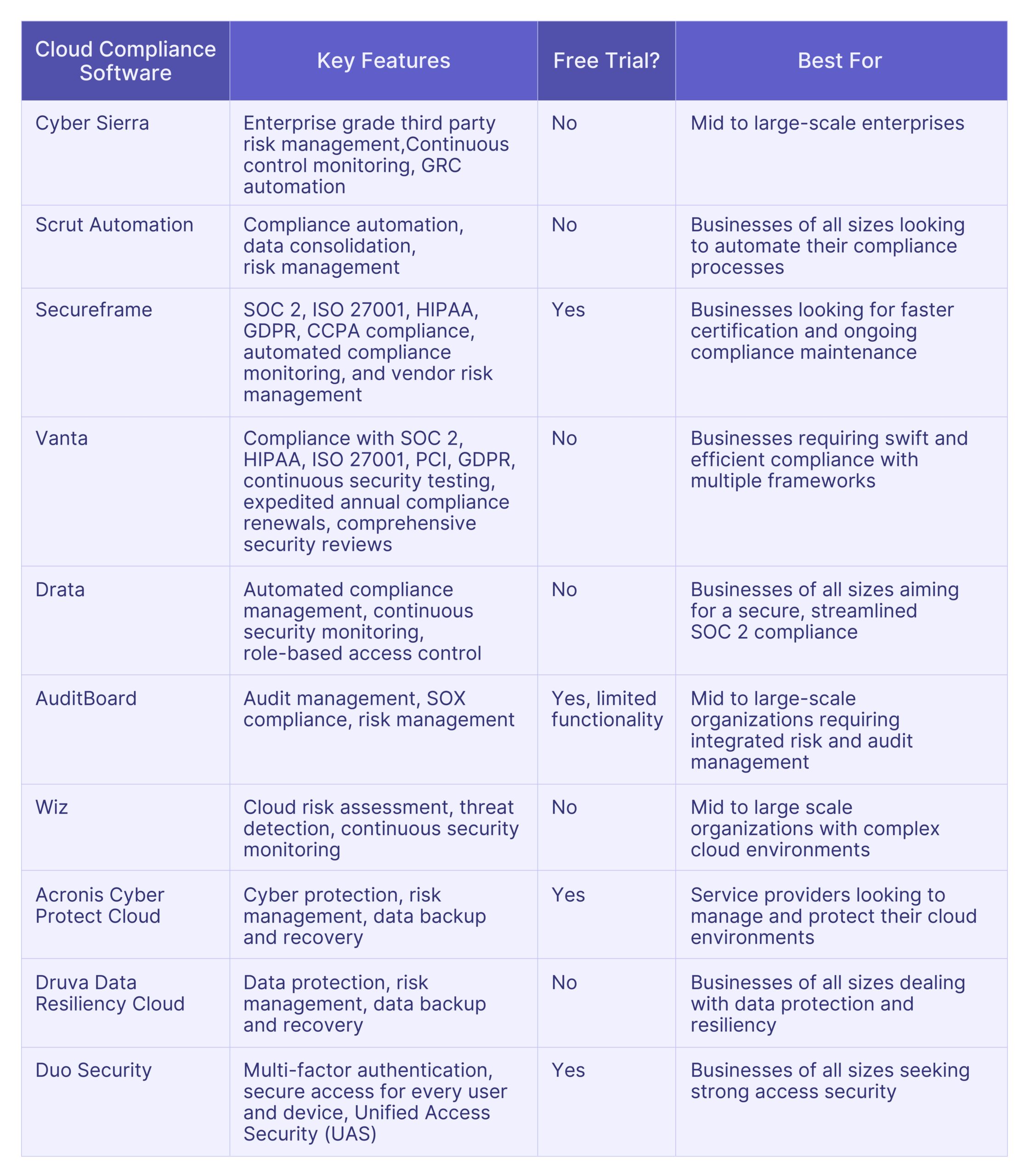
Top 10 Wiz Alternatives: Comparative Analysis
Here is the comparative analysis of the top 10 Wiz alternatives, helping you to choose the most suitable software for your specific needs.
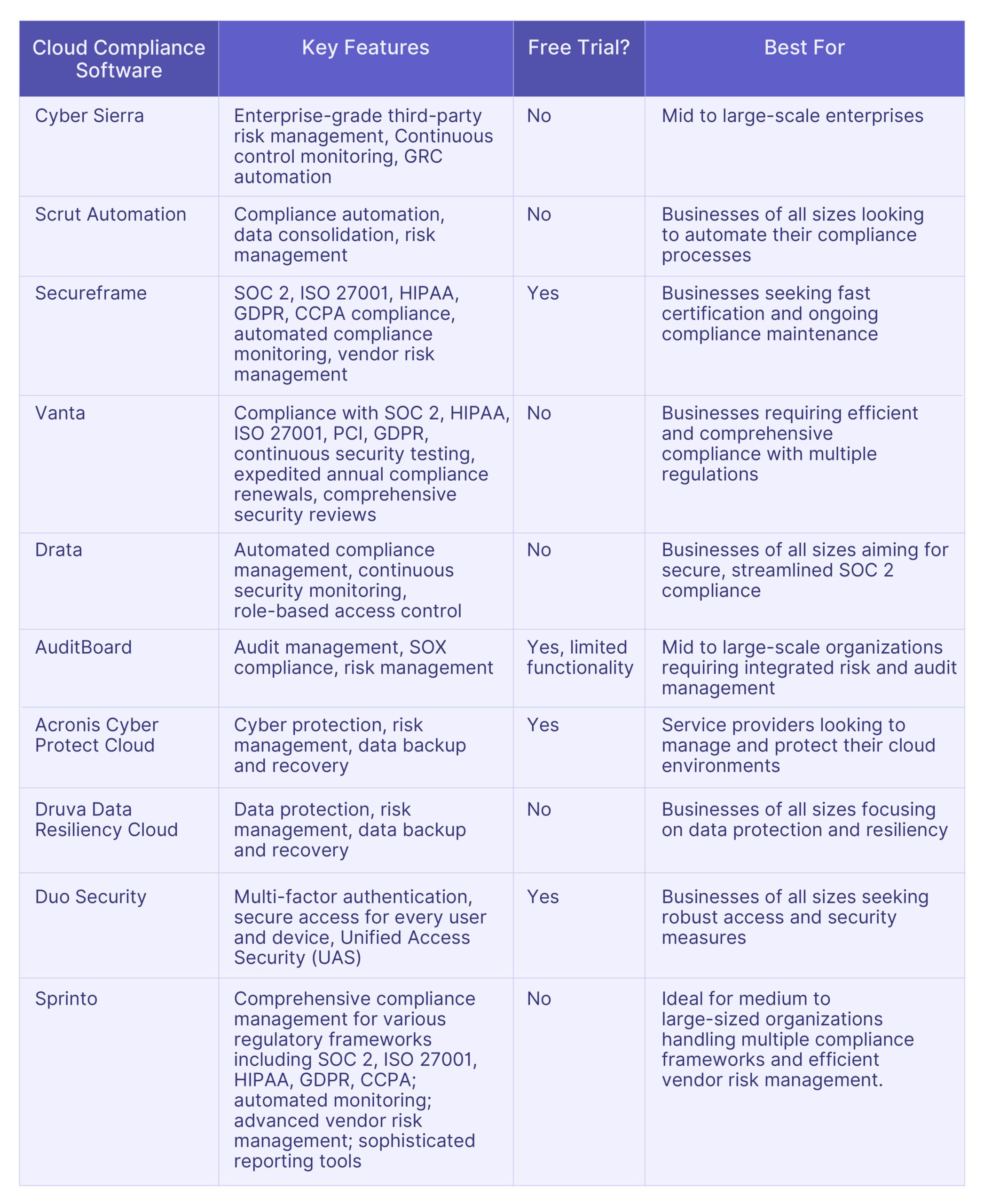

Selecting the Best Software
Selecting the right software necessitates a careful study of specific features, cost implications, and user experiences, to make the decision-making process smoother.
Despite there being numerous software options designed to facilitate your organization’s management tasks, it’s vitally important to select one that best fits your requirements.
Cyber Sierra clearly differentiates itself from other security platforms through its combination of comprehensive functionalities and robust protection.
Its easy-to-use design allows you to implement security protocols in no time at all and provides an extra layer of protection against cyber risks.
Schedule a demo today and learn how Cyber Sierra can optimally secure your business.





















A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.