Cybersecurity Continuous Control Monitoring Process Steps Simplified for Enterprise CISOs





Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
Work-related stress has long been the bane of enterprise security execs, mainly chief information security officers (CISOs). For instance, in Nominet’s 2020 research, 90% of CISOs said work-related stress affected their wellbeing and personal lives.
Years after, the situation isn’t getting better.
Threat actors are becoming more advanced by the day. As a result, securing a company’s IT assets, employees, IP, and so on, will only get harder. This has led to higher stress levels, as this recent study found:

Realistically, you can’t wave a magic wand and remove all work-related stress. It is built into the fabric of leading an enterprise security team. However, you can drastically reduce it by simplifying the cybersecurity continuous control monitoring (CCM) process steps.
That’s what we’re delving into today. But first, let’s establish…
What Enterprise Continuous Control Monitoring Process Is
A cybersecurity continuous control monitoring (CCM) process is a collective of the action steps taken to stay one level above cybercriminals. The whole idea is to achieve the golden rule: Prevention is better than cure.
Says SANS Institute Director, John Davis:


John couldn’t say it better.
And that’s because with an effective CCM process:
- You can keep an ongoing watch on security controls across company assets with less stress.
- Your enterprise security team can remediate vulnerabilities before threat actors exploit them.
To achieve these benefits, follow the steps discussed below. But if you’re new to this, I recommend you also get this cybersecurity continuous control monitoring checklist:
Continuous Security Monitoring Process Steps
Four steps enable the cybersecurity CCM process:
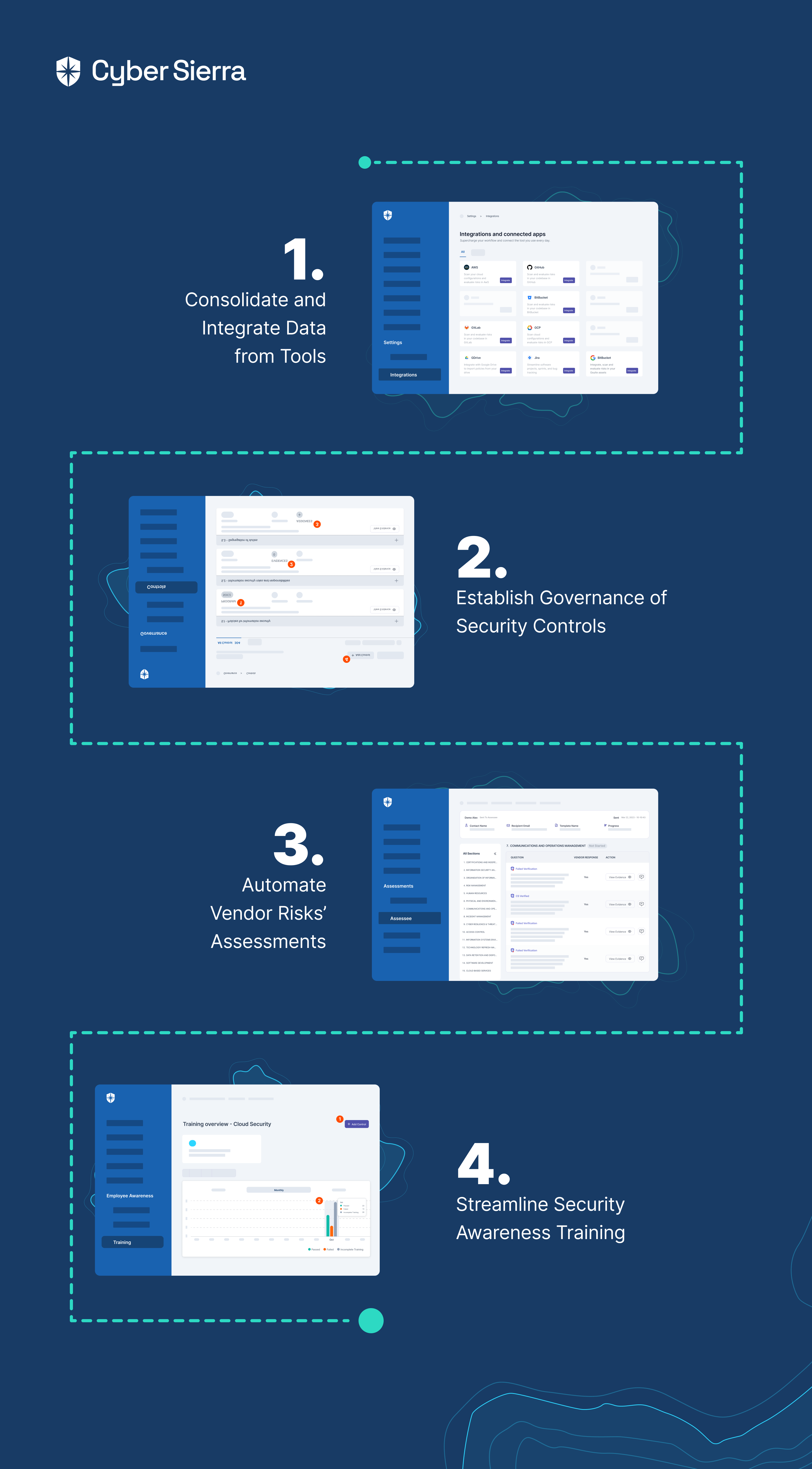

1. Consolidate and Integrate Data from Tools
The first step towards achieving CCM is to integrate data from all tools prone to misconfigurations and vulnerabilities into a single platform. This includes critical cloud assets and business tools used across your organization:

Integrating and connecting apps will enable your team to maintain an undated cloud asset inventory. Done with an intelligent, interoperable cybersecurity platform like Cyber Sierra, you get:
- Granular data segmentation of integrated assets.
- Continuous monitoring of misconfigurations.
More on Cyber Sierra as we proceed.
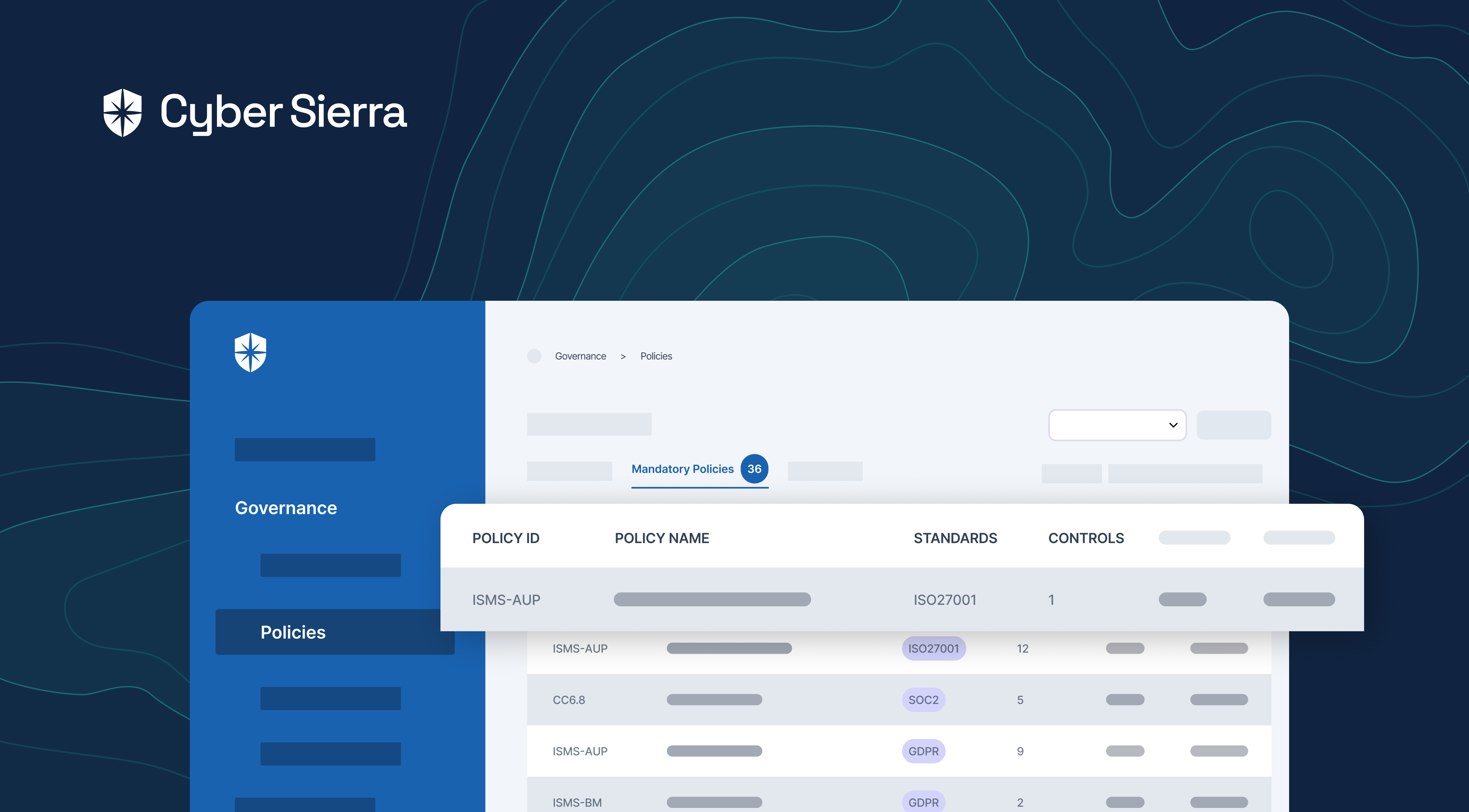
2. Establish Governance of Security Controls
All risk management compliance programs have security controls that must be in place for an organization to attain and remain compliant. This is true for SOC2, ISO27001, GDPR, and others.
So establishing governance enables your team to know what security controls to prioritize and continuously monitor across programs.
And doing this is easy with Cyber Sierra:

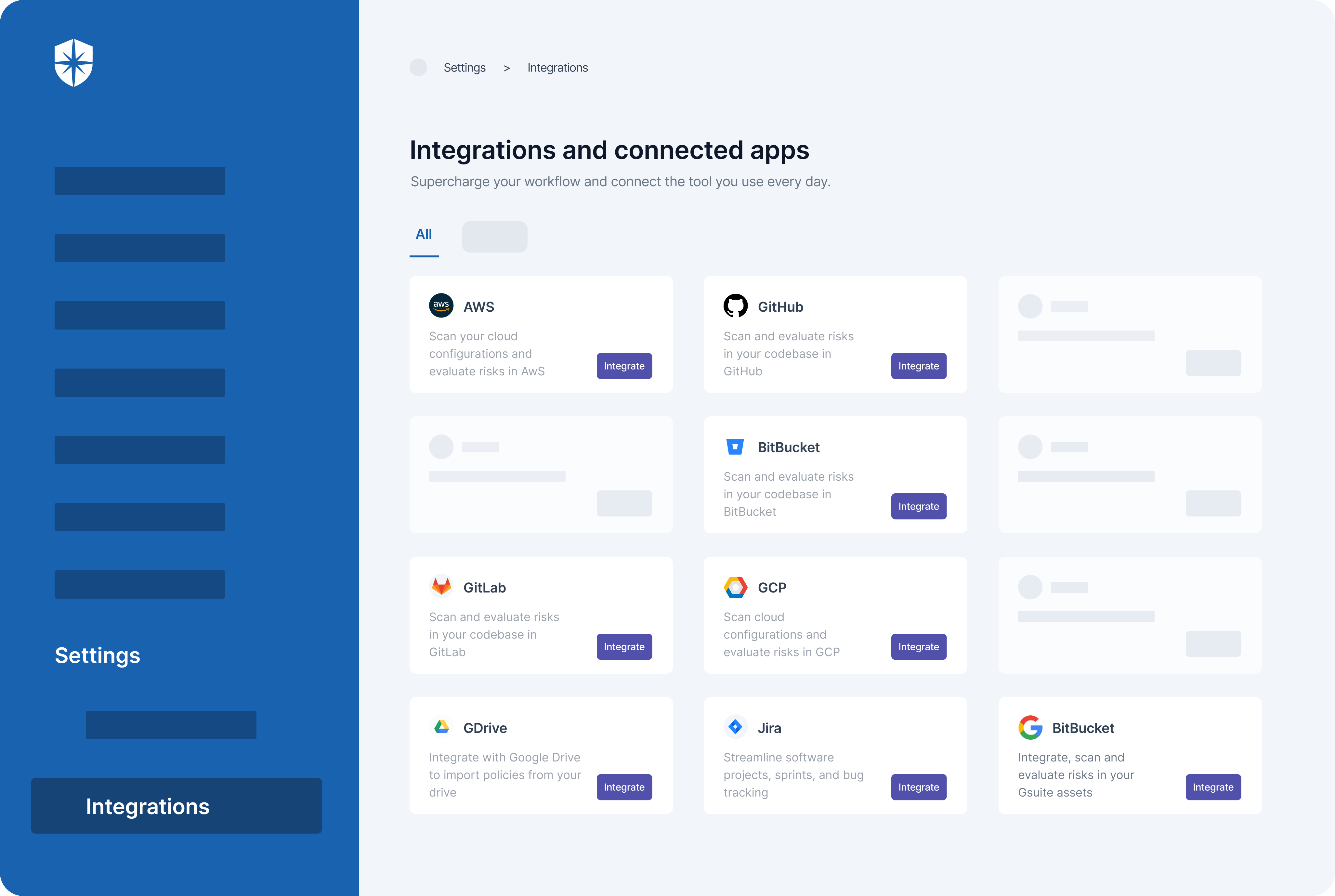
As shown, our intelligent cybersecurity platform automatically aggregates security controls from all implemented compliance programs into one view. From this holistic view, you can:
- See programs a security control is attached to.
- View evidences of having that control in place.
- Assign critical controls to key members of your security team.
- Easily create and add new controls to your cybersecurity governance.
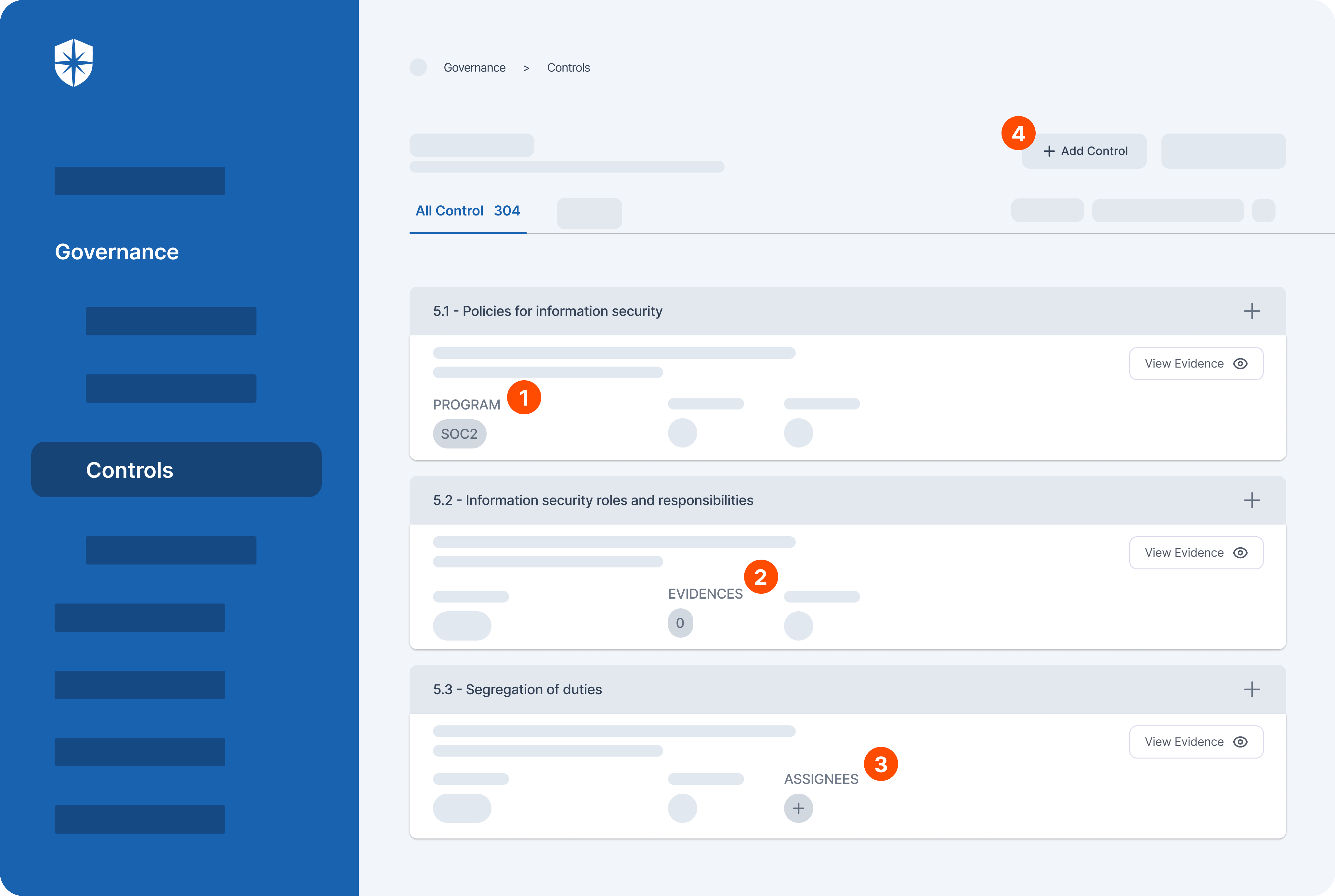
3. Automate Vendor Risks’ Assessments
Third-party vendors can introduce risks that undermine your cybersecurity continuous control monitoring efforts. To buttress, research by Verizon revealed that:


Worse, it can take up to 277 days for organizations to detect risks from 3rd-parties, according to IBM. One way to mitigate this as part of the cybersecurity continuous control monitoring process is to automate vendor risks’ assessments.
Cyber Sierra enables your team to do this. For instance, our platform auto-assess evidence of security controls uploaded by 3rd-parties. It also consolidates everything into a single view, where your team can track evidence that failed verifications.
Here’s a sneak peek:

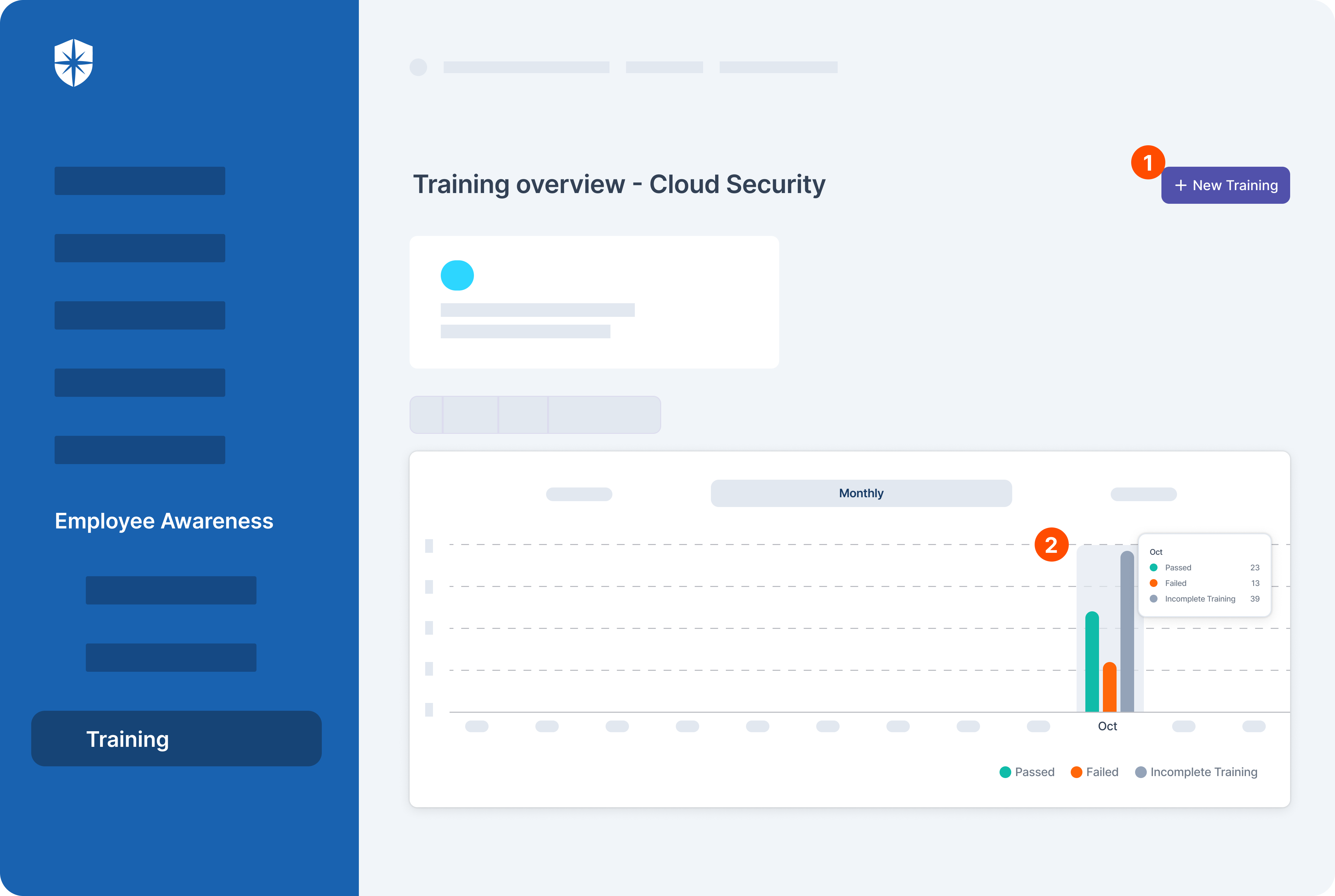
4. Streamline Security Awareness Training
Employees across an entire organization form an important, if not the most important, component of all cybersecurity processes. And continuous control monitoring is no exception.
Ongoing security awareness training is therefore essential for educating employees on the steps outlined above. It is also crucial for equipping them on implementing the ever-changing CCM process.
Kevin Turner corroborates:


Cyber Sierra streamlines this in a way that makes sense for enterprise security execs. On the same platform, you can:
- Launch new regular cybersecurity training
- Monitor ongoing training to ensure employees complete them and stay informed on their responsibilities in achieving continuous control monitoring:

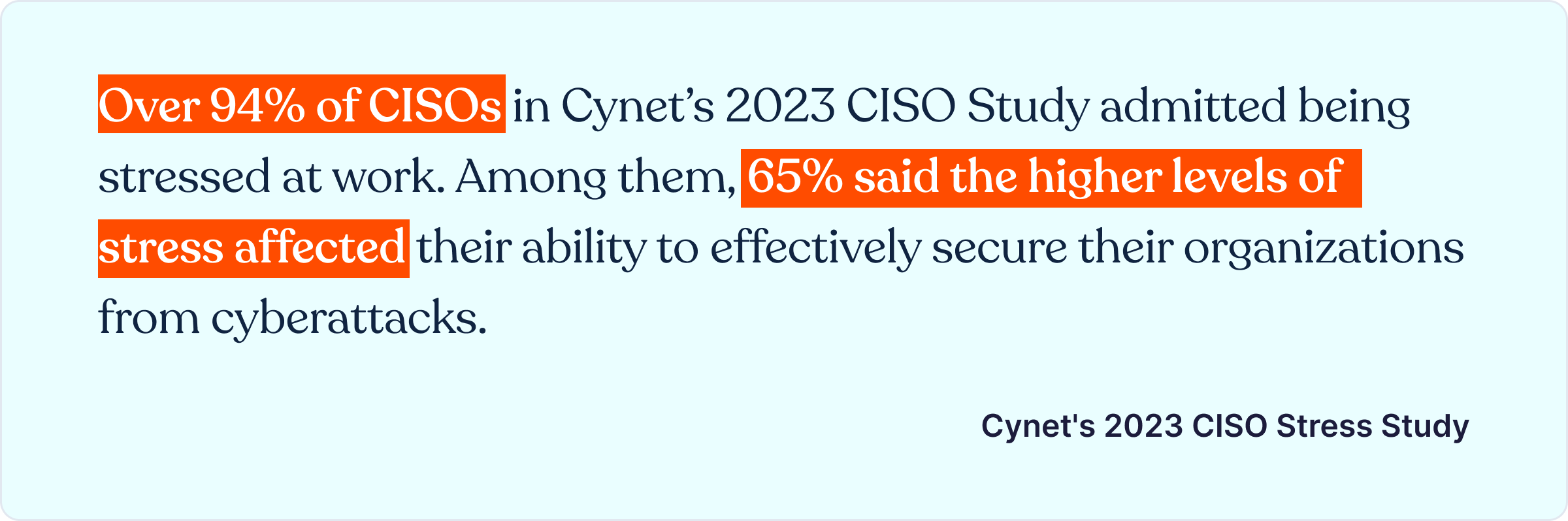
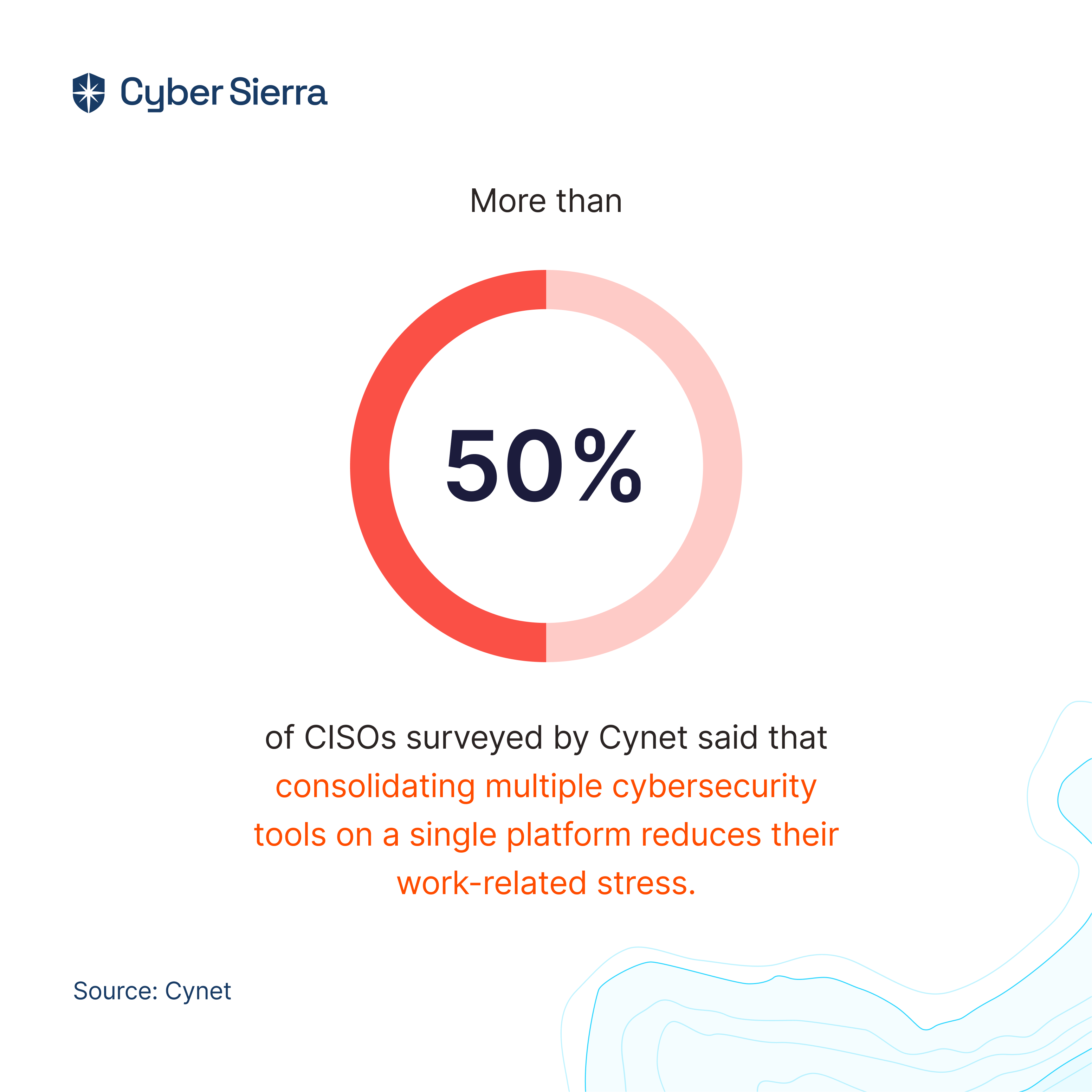
All through the four cybersecurity continuous control monitoring process steps, I showed how our platform helps. Consolidating multiple security tools on a single platform like Cyber Sierra reduces stress for CISOs and enterprise security execs.
Cynet’s CISO Study confirmed this:

Using an enterprise cybersecurity CCM system such as Cyber Sierra has other benefits, apart from just reducing stress for CISOs.
Before we get to those advantages:
The Advantages of Enterprise Cybersecurity Continuous Control Monitoring System
According to Narendra Sahoo:


Sahoo’s take highlights the first advantage of using a cybersecurity continuous control monitoring system like Cyber Sierra.
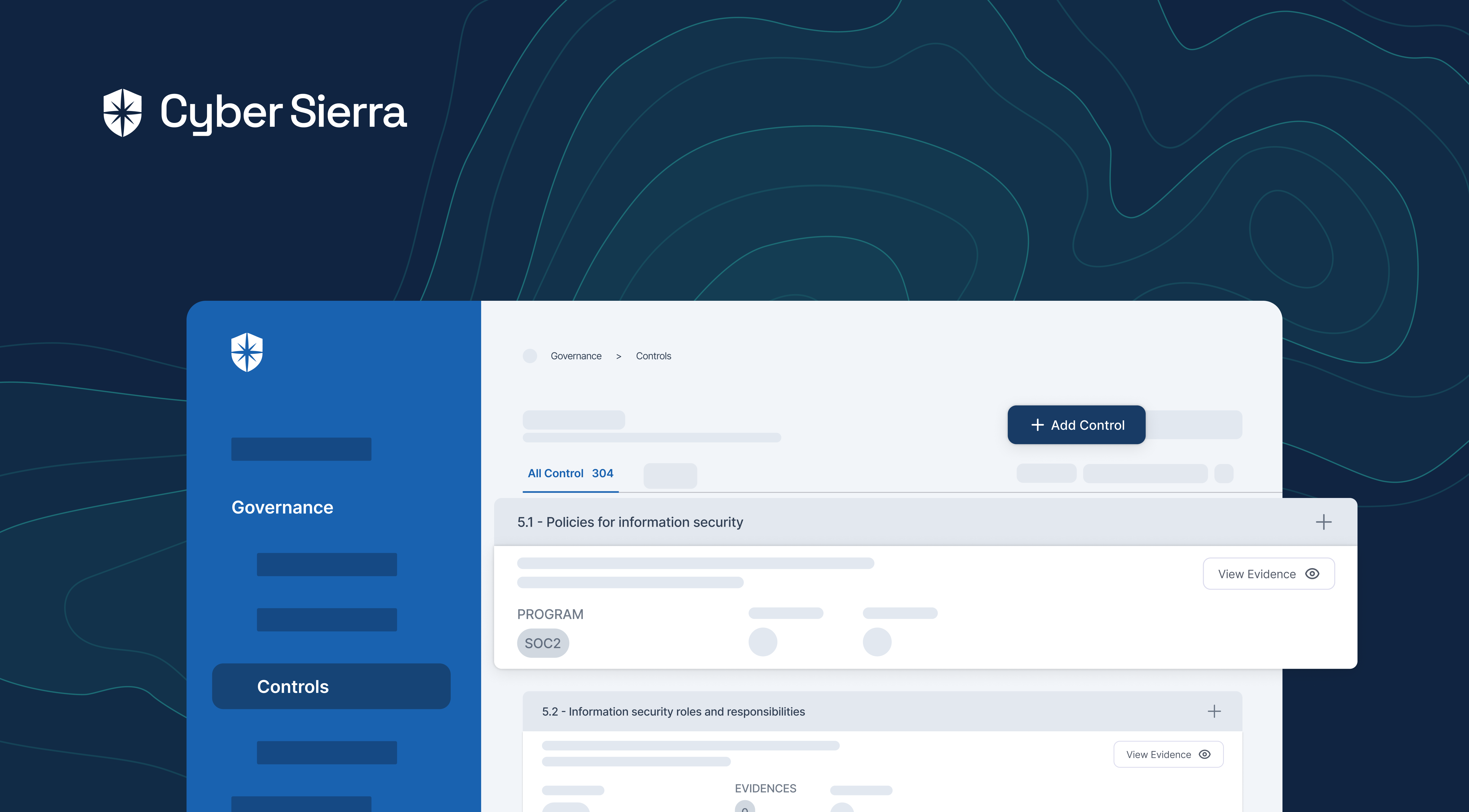
1. Near Real-Time Risk Monitoring
Being a pure-play cybersecurity CCM platform, Cyber Sierra has built-in, enterprise-grade capabilities. For instance, the holistic ‘Controls Dashboard’ enable your enterprise security team to continuously monitor controls in near real-time by:
- Integrated cloud asset categories or asset types
- Custom or standard compliance programs implemented:
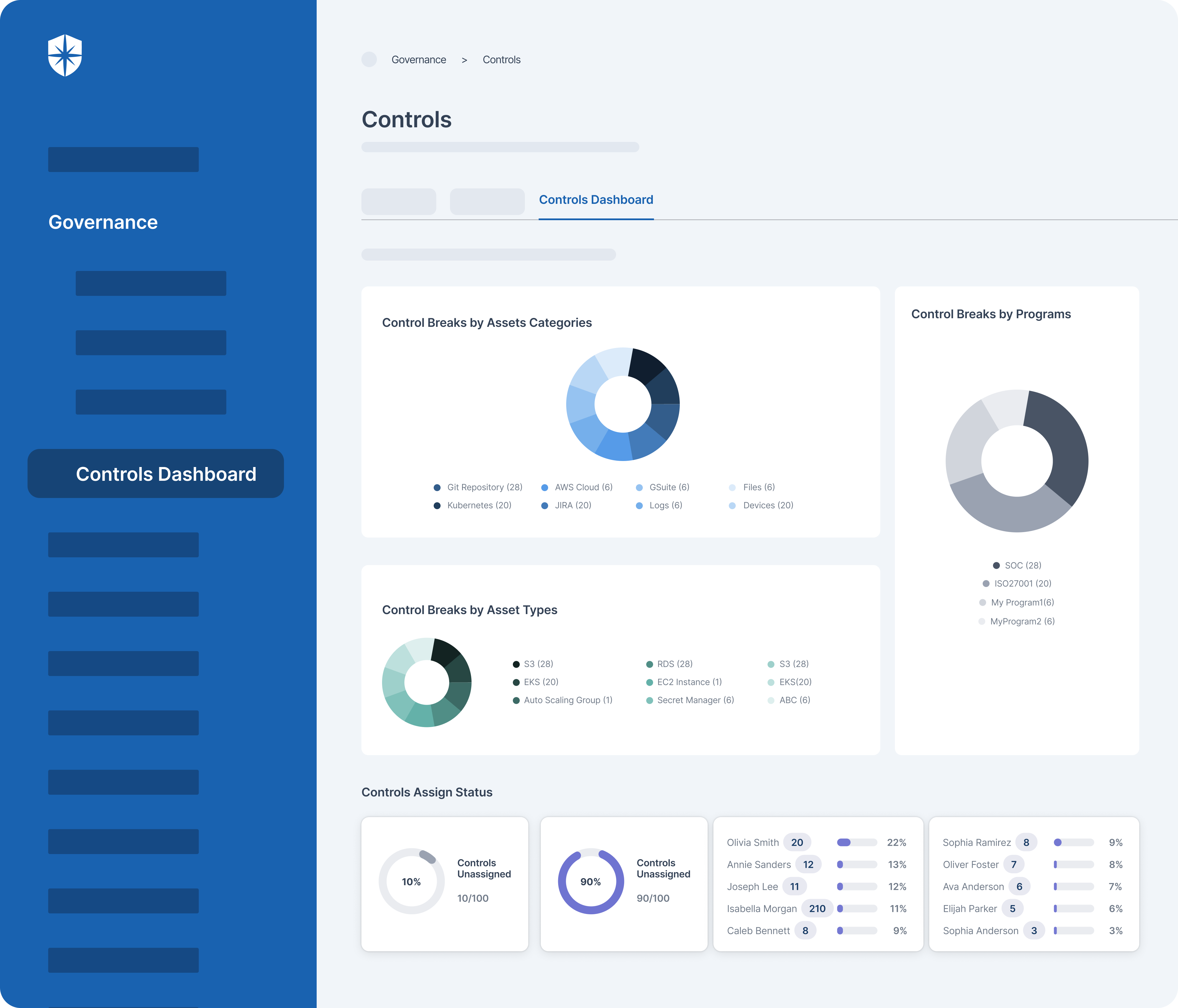

As shown, consolidating all security controls into this dashboard enables near real-time risk monitoring. You can also track controls assigned to teammates from the same pane, making it way easier to fix control breaks.
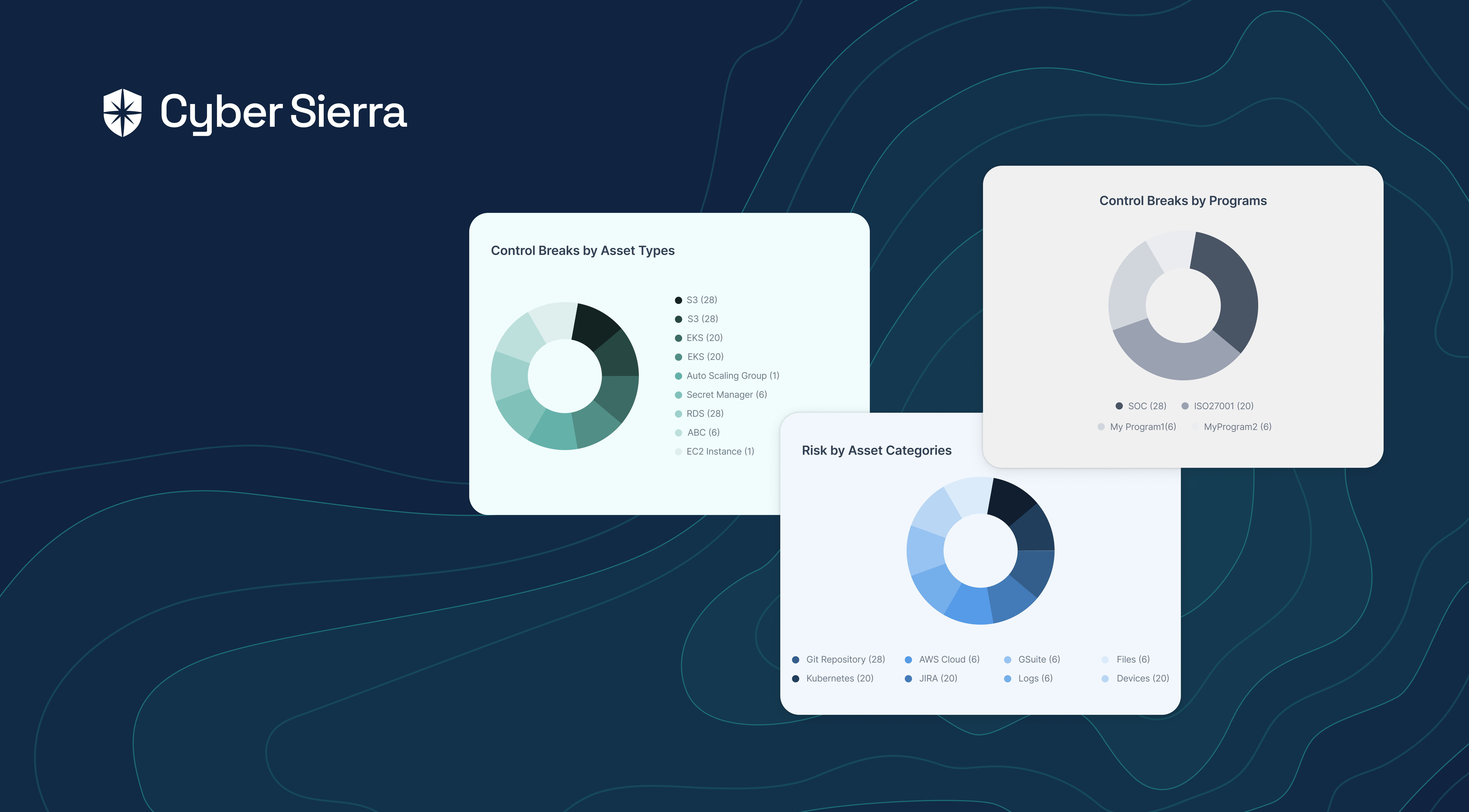
2. Seamless Risk Remediation
An effective cybersecurity continuous control monitoring process should detect threats, control breaks, and promptly remediate them. Achieving this is seamless with Cyber Sierra.
From all controls in your security governance, our platform automatically detects and pulls control breaks into a separate view:
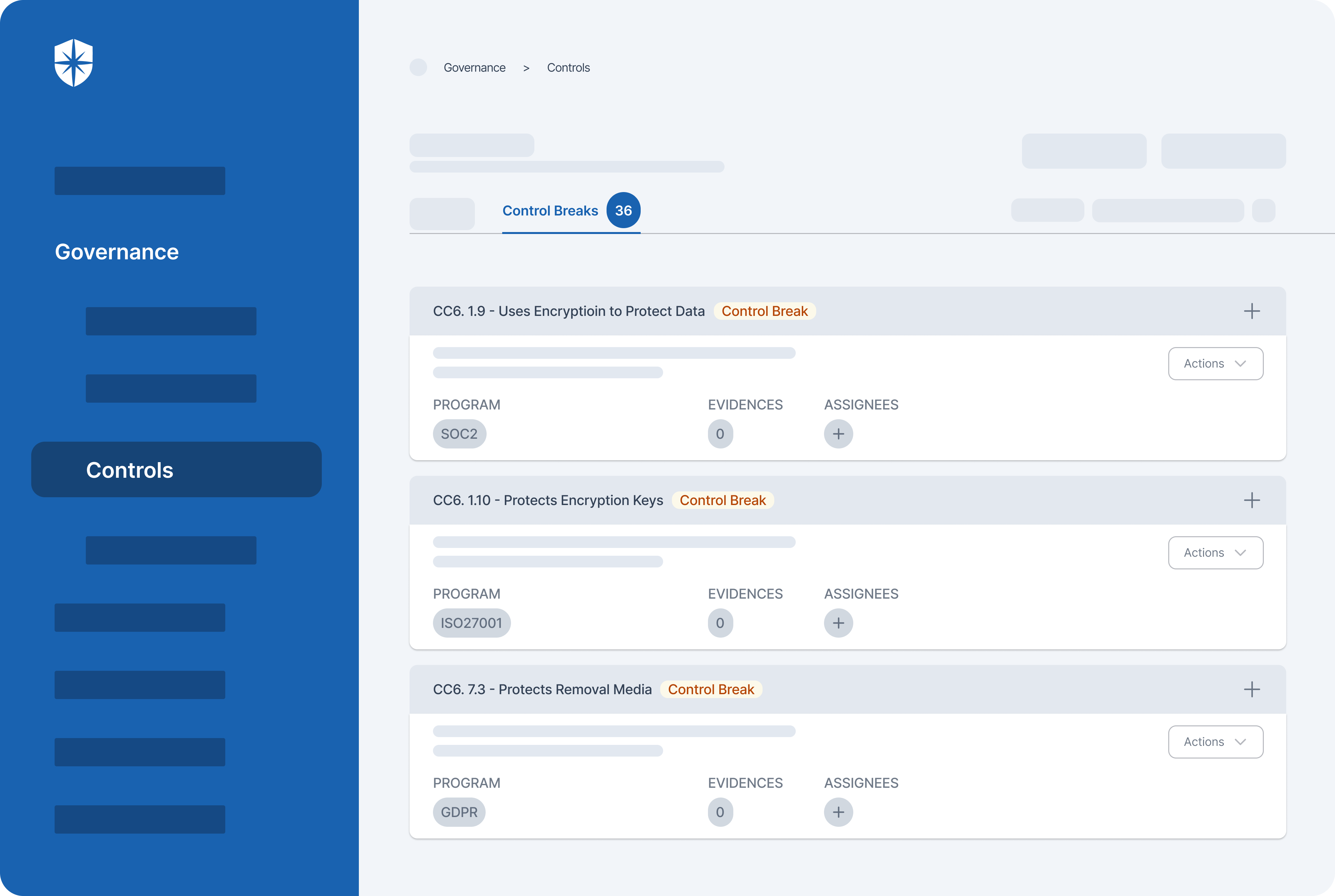

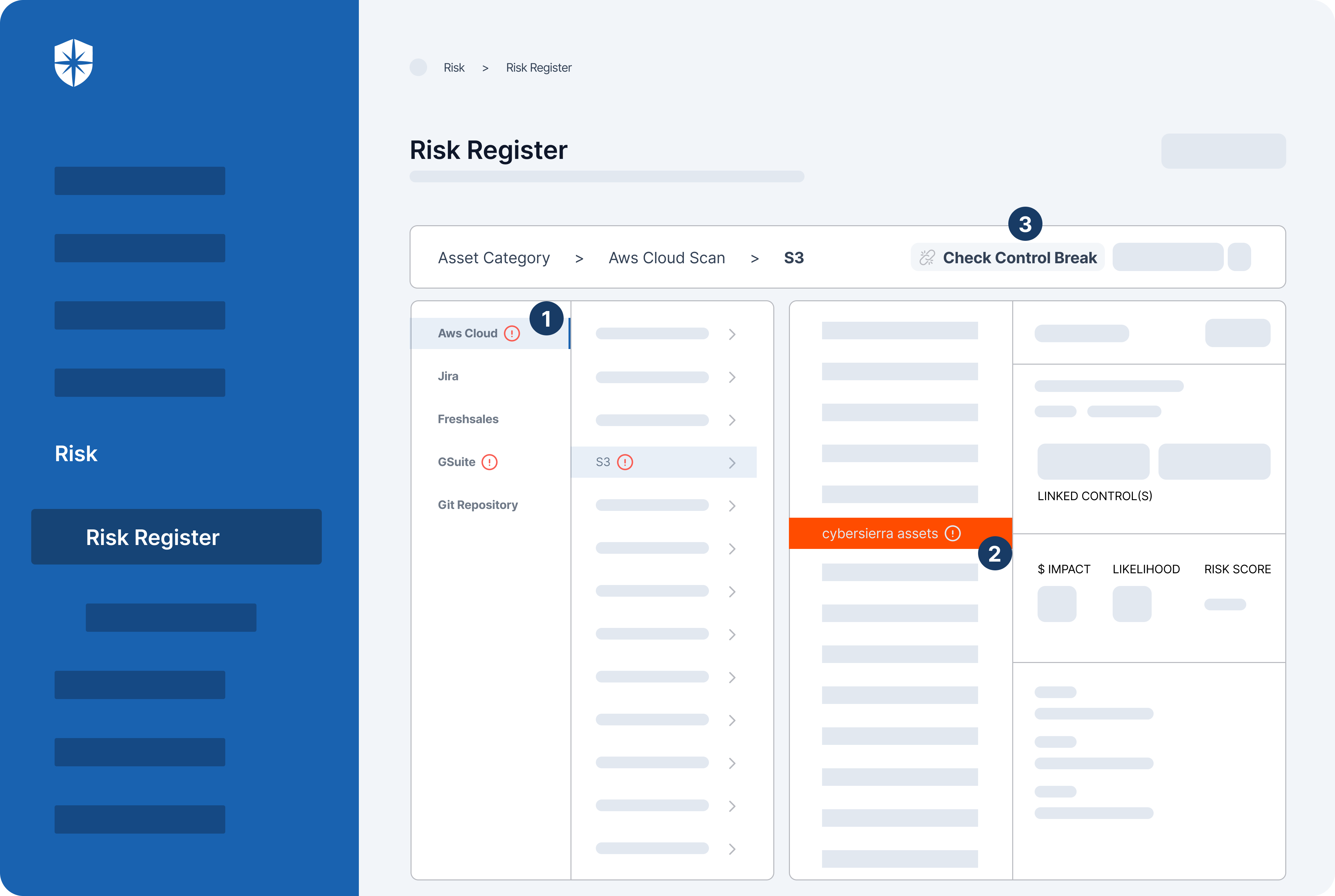
From this view, you can easily assign control breaks for prompt remediation and tracking. Another way Cyber Sierra enables seamless risk management and remediation is through its Risk Register.
Enterprise security teams use it to continuously:
- Detect IT assets with misconfigurations and vulnerabilities.
- Examine all security controls linked to such assets.
- Check the control breaks and assign remediation:

Enterprise tech executives trust Cyber Sierra for simplifying their cybersecurity processes due to the advantages mentioned above. One, out of many examples, is Aditya Anand, the CTO of Hybr1d.
In his testimony, Aditya raved:
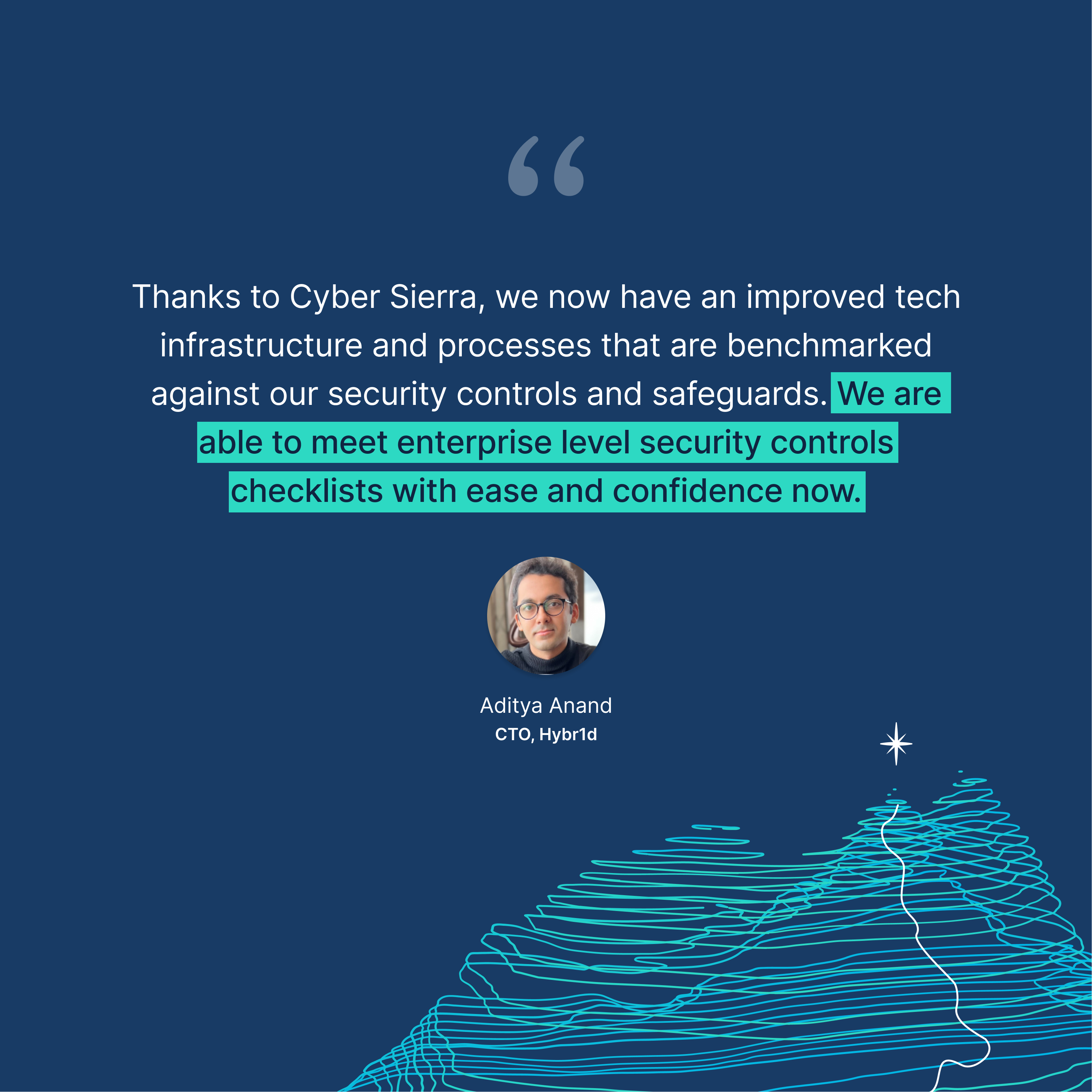

Read Hybr1d’s case study.
Simplify Cybersecurity CCM Process Steps
To recap, our recommended cybersecurity CCM process steps are:
- Consolidate and integrate data from tools.
- Establish governance of security controls.
- Automate vendor risks’ assessments, and
- Streamline security awareness training.
Typically, each of these steps required a different software product. But most tools often don’t work well together, making the process more complex and stressful for enterprise security leaders.
To solve this, our platform consolidates the core capabilities required into an intelligent, interoperable cybersecurity platform. This way, you can simplify the entire cybersecurity continuous control monitoring process steps from one place:



A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.