Different Cybersecurity Controls and How to Implement Them




Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
The frequency at which cybercriminals are launching new —and more sophisticated— attacks will only increase. To buttress, imagine it takes you 5–7 mins to skim this article. In that short time, hackers would’ve targeted the cybersecurity infrastructures of over 33 enterprises.
And that’s by 2021 estimates:
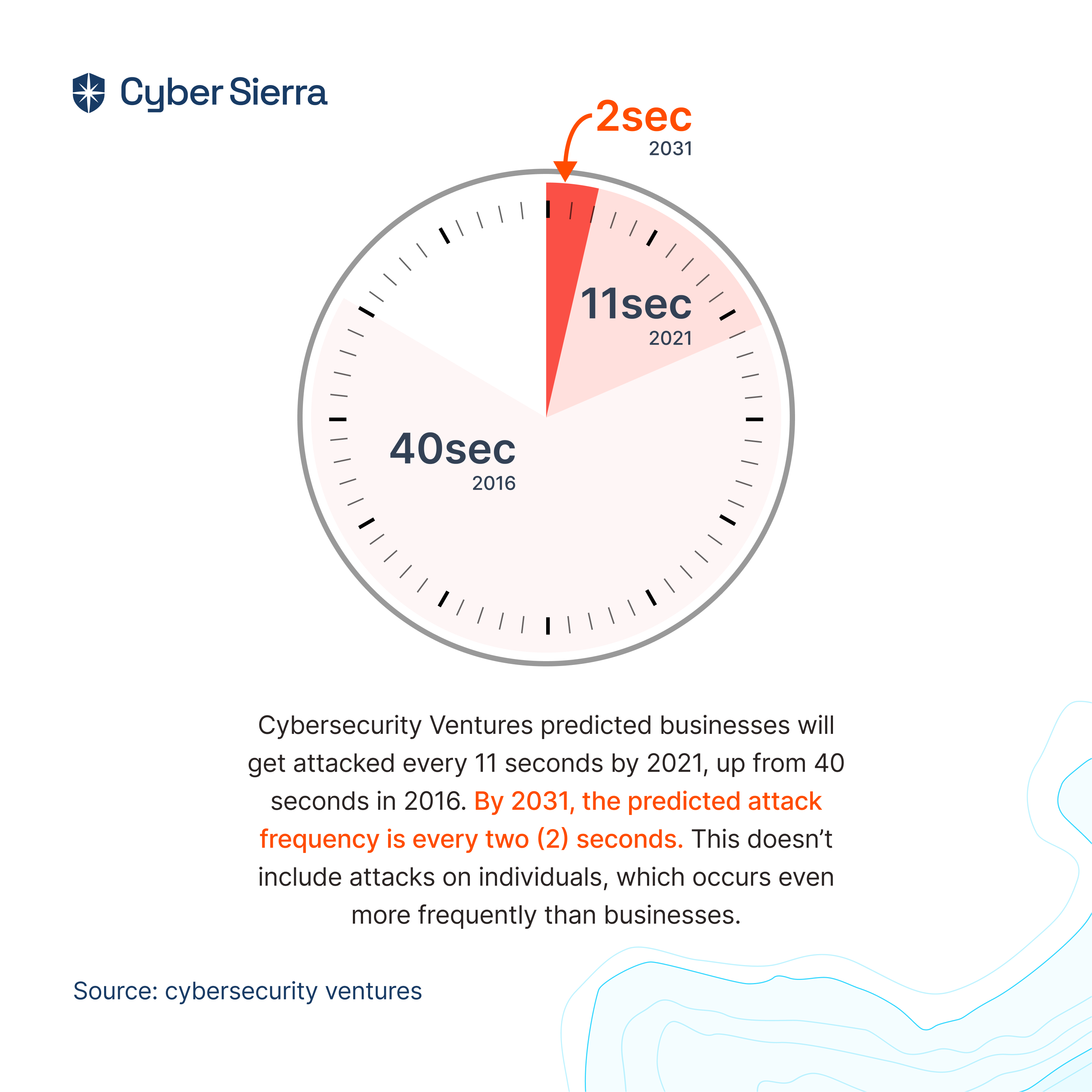

As the predictions reveal, by 2031, enterprise organizations would be cyberattacked every two seconds. Given this alarming frequency, how can enterprise security teams identify, investigate, and counter-attacks at the pace of cyber thieves?
Joseph MacMillan; CISSP, CCSP, CISA, gave a clue:


I wrote this article to help proactive CISOs and Enterprise Security Leaders like you heed this crucial advice. We’d evaluate cybersecurity control types and go through how your security team can implement the right ones with Cyber Sierra.
But first:
What are Cybersecurity Controls?
Cybersecurity controls are measures used by security teams to detect, prevent, and remediate cyber threats. Creating, implementing, and enforcing them ensures the cybersecurity CIA triad —confidentiality, integrity, and availability)— of your company’s IT assets:
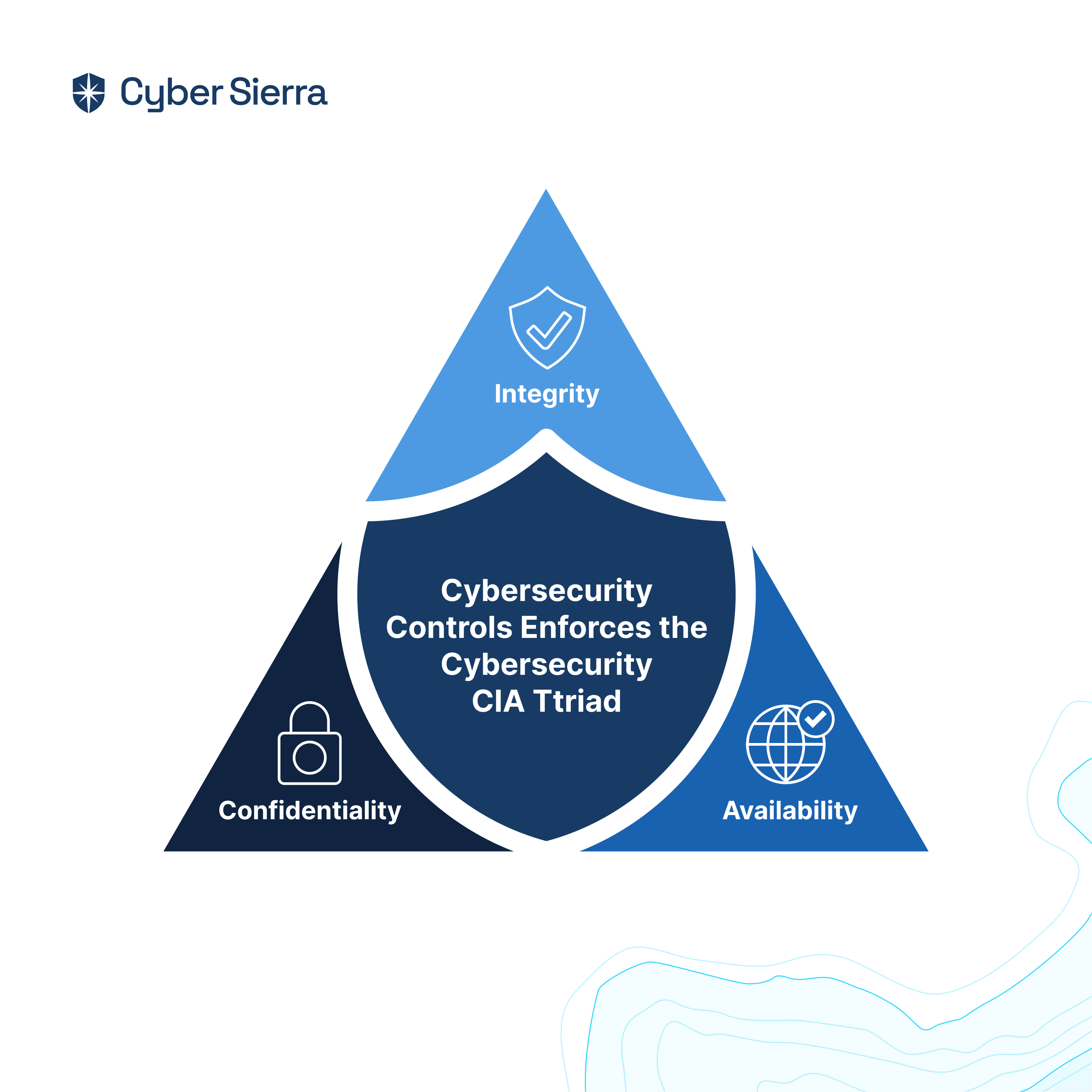

As illustrated, without the proper controls, achieving the cybersecurity CIA triad is difficult, if not impossible. The rise of cybersecurity continuous control monitoring (CCM) is as a result of this. Today, enterprises mustn’t just strive to have the right cybersecurity controls, but you must monitor them continuously to always ensure proper implementation.
So for the rest of this article, we’d:
- Evaluate types of cybersecurity controls
- Go through how to implement and monitor them.
Before that:
Types of Cybersecurity Controls for Enterprises
All cybersecurity controls revolve around four essentials: People, technology, processes, and strategy. This means you must:
- Have the right people on your security team
- Empower them with the right technology
- Institute the right security processes, and
- Have a strategy that tracks the right security metrics.
Across the four essentials outlined above, all control types can be categorized under the core pillars of cybersecurity:
- Governance and compliance
- Cyber threat remediation
- Vendor risk management
Governance and compliance controls
Continuously meeting all industry and government regulations is now a prerequisite for gaining customers’ and investors’ trust. To this end, having the required governance and compliance controls does two crucial things for your enterprise organization:
- They help you achieve compliance for highly-sought standards like SOC 2, ISO 27001, GDPR, PCI DSS, and others.
- They also help your company continuously improve those controls to remain compliant as new changes emerge.
But the challenge: How do you know the specific controls required for each compliance standard your company must attain?
Each compliance program has dozens of policies, requiring multiple dozens of security controls to be in place. SOC 2, for instance, has 23 mandatory policies and over 96 cybersecurity controls. Creating, tracking, and implementing each can be a stretch, especially when you add those from other programs like ISO 27001, GDPR, and so on.
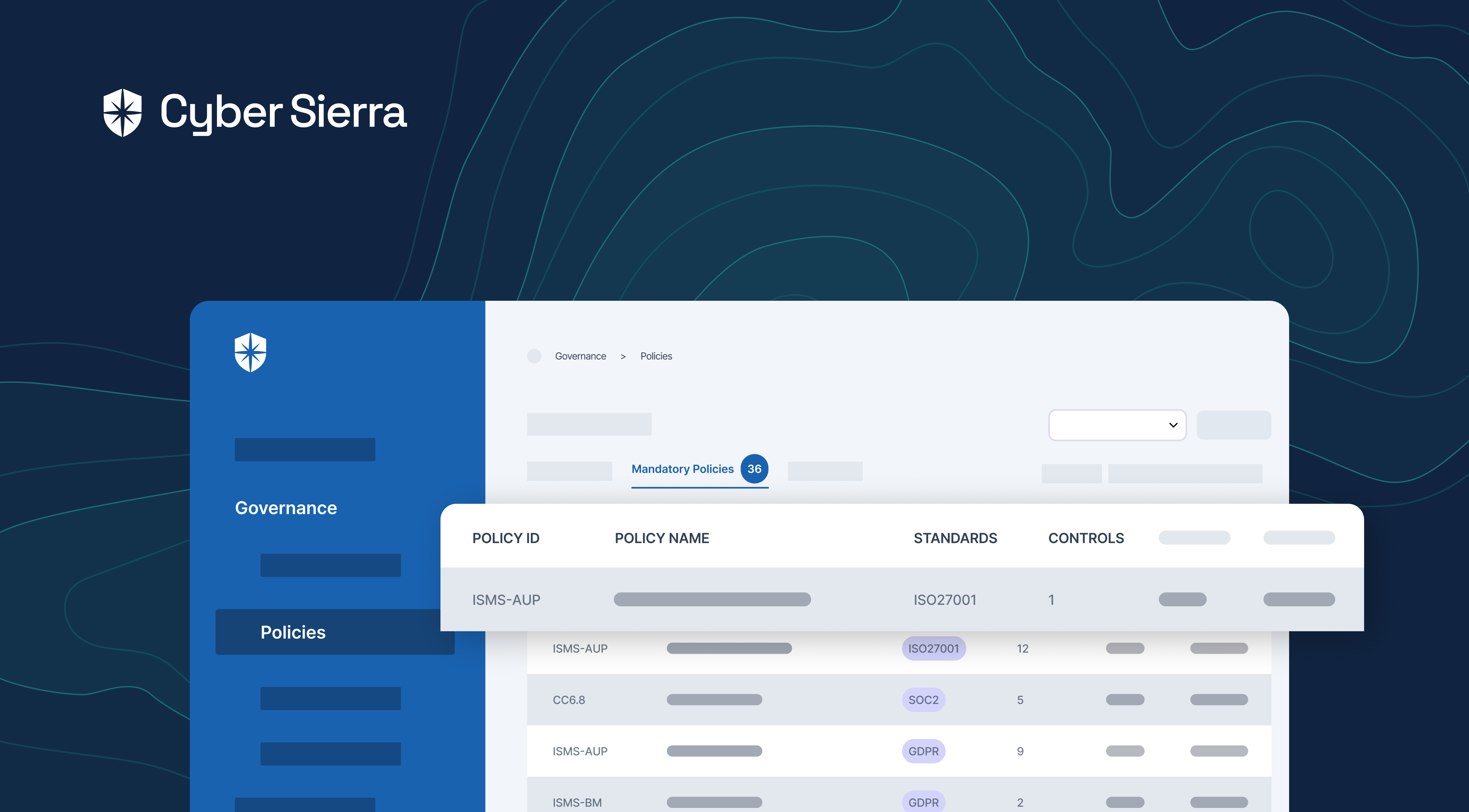
But with Cyber Sierra, your security team gets a centralized view of all compliance program policies and their corresponding controls:
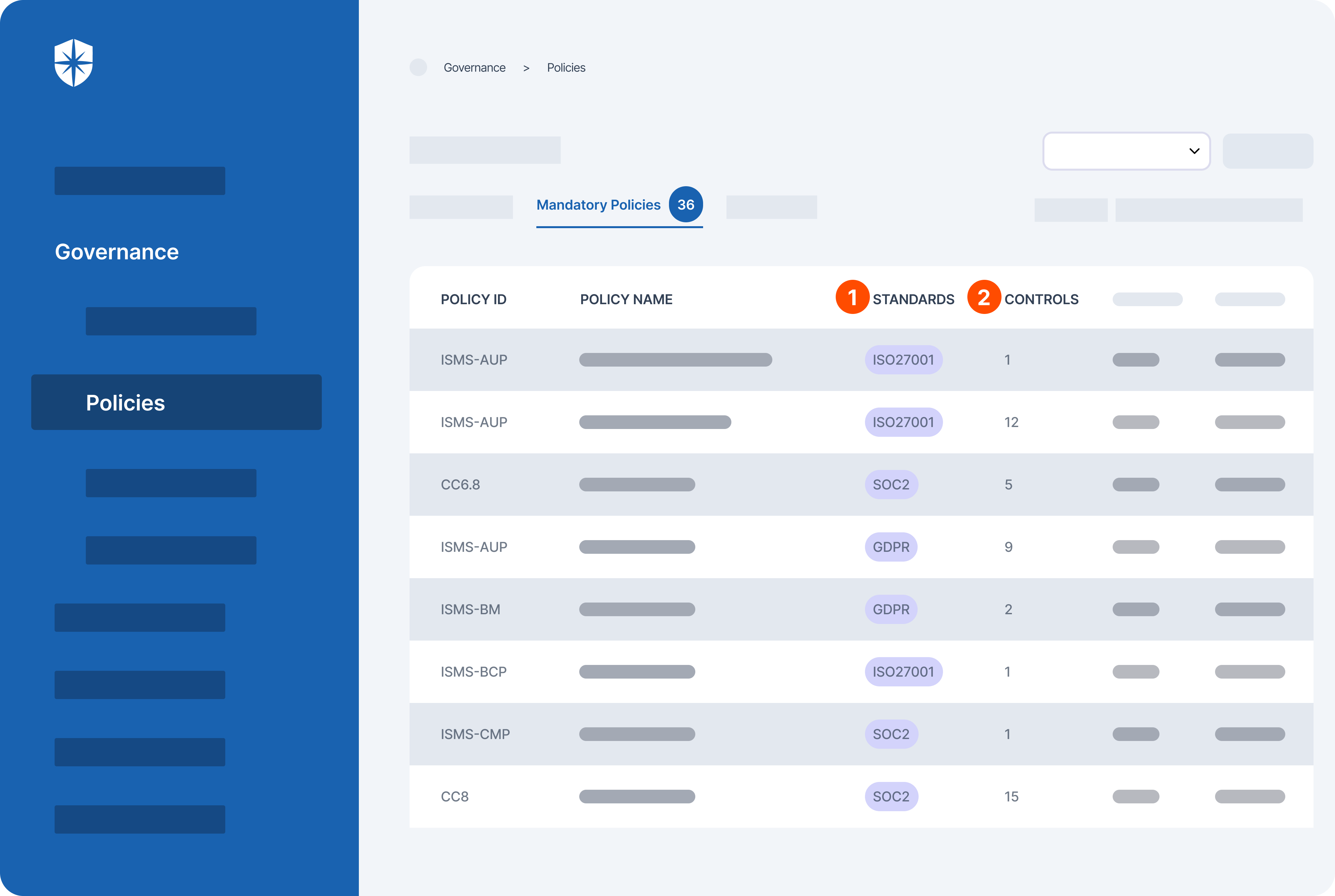

From the view shown above, you can evaluate:
- All the mandatory policies for all the compliance programs your company must become compliant with, and
- Each control required under every policy.
Your security team can also implement these controls on the same pane with Cyber Sierra. This is why executives at enterprise companies trust the capabilities of our platform.
Take Hemant Kumar of Aktivolabs:


More on Aktivolabs’ success story here.
Cyber threats’ remediation controls
One of the ways cybercriminals exploit companies is through loopholes and vulnerabilities in their network and IT assets. To stay one step ahead, enterprise security teams must:
- Continuously scan their network and cloud assets for threats.
- Implement controls for detecting and remediating them.
With Cyber Sierra, your team can accomplish both.
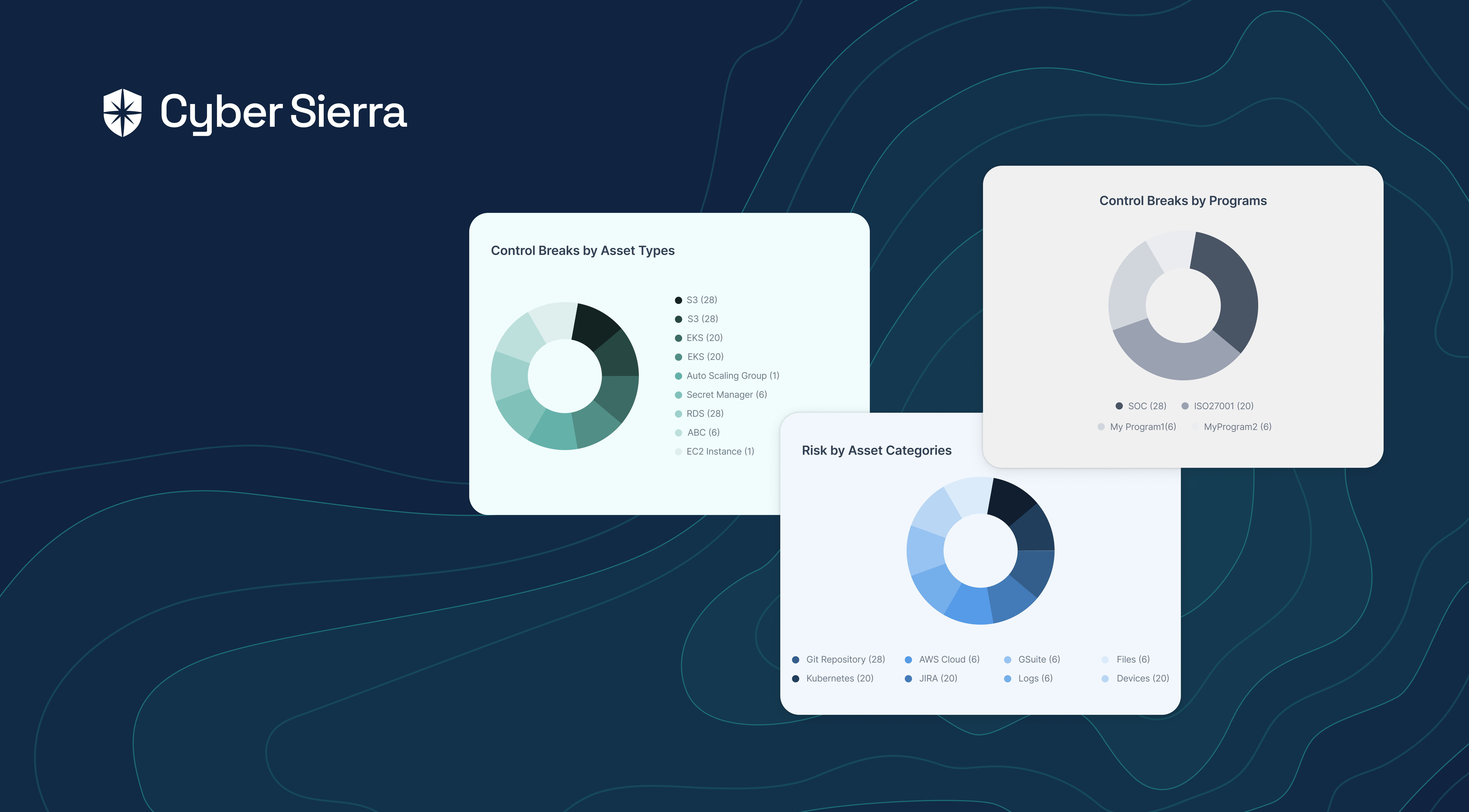
Our platform lets you integrate and connect all your network, Kubernetes, and cloud assets for continuous scanning. Through our Risk Register, you also get cybersecurity controls from vulnerabilities related to all scanned assets automatically implemented. This means your team can focus on identifying and remediating control breaks:
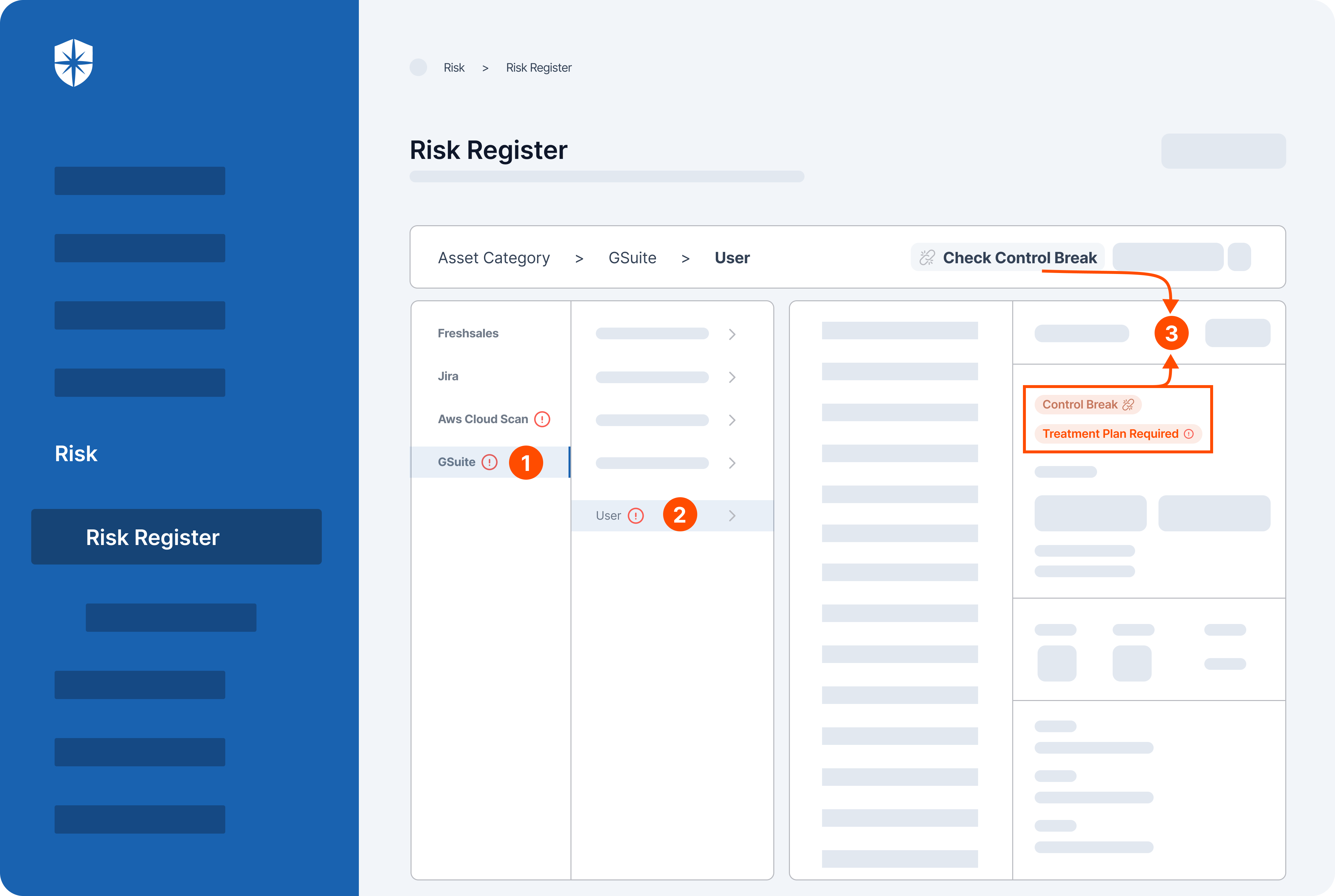

As shown, Cyber Sierra’s Risk Register automatically detected a vulnerable control break (3) by a user (2) of the GSuite cloud asset (1).
Vendor Risk Management Controls
Third-party vendors, while crucial to all enterprises’ operations, introduce lots of cybersecurity risks. According to Joseph Kelly, EY’s Third Party Risk Leader, enterprise security teams have no option than to find a way to deal with the risks they introduce:


To answer the question Joseph raised…
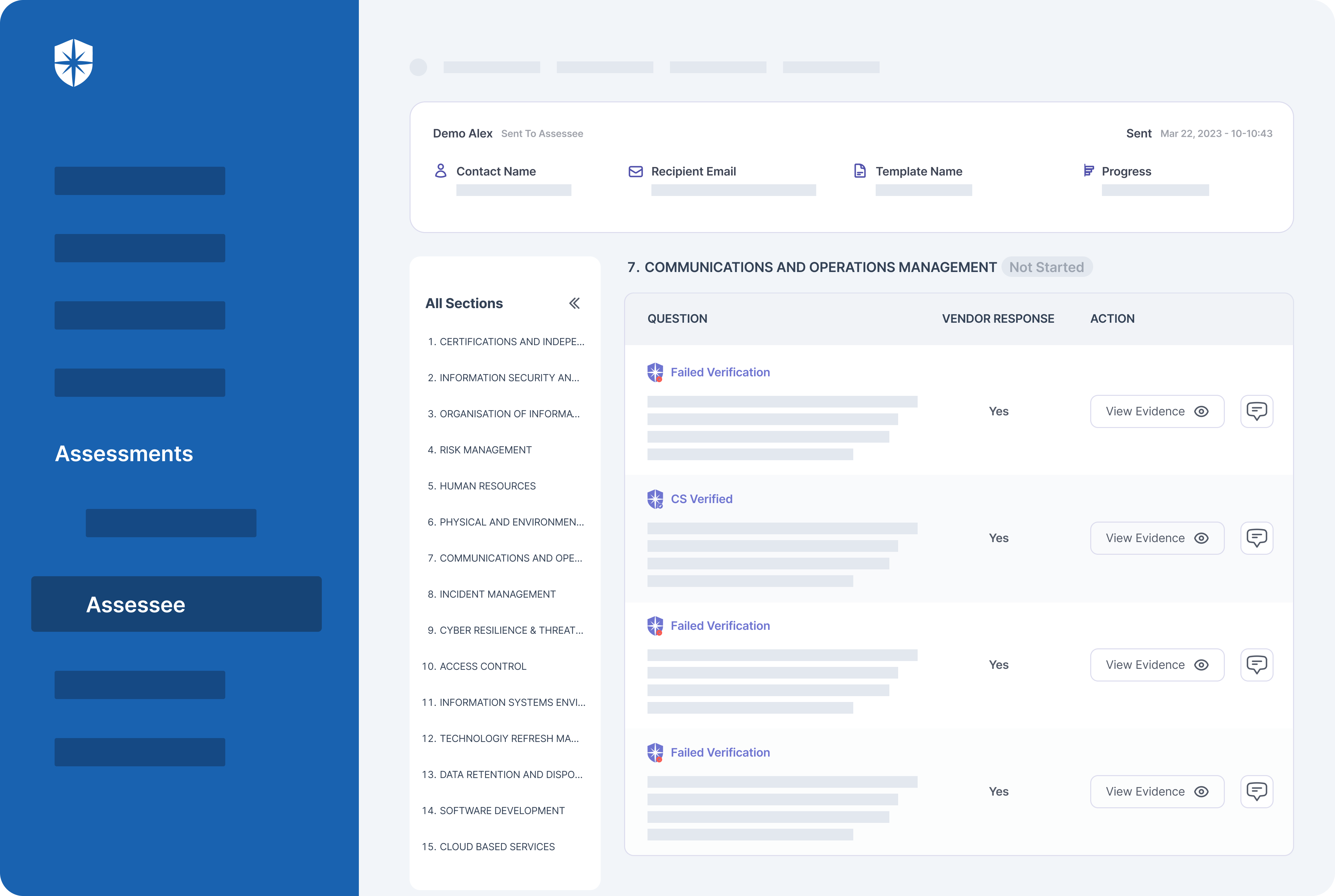
Have vendor risk management controls for identifying, managing, and mitigating vendor risks. Specifically, you must analyze, assess, and monitor 3rd parties’ security postures in real-time. Your team can achieve this with a platform that automatically assesses evidence of security controls defined by your company. Such a platform should also be intelligent enough to flag vendors who fail verification for immediate remediation.
Cyber Sierra does both out of the box:

How to Ease Cybersecurity Controls’ Implementation
Using a centralized platform eases the implementation of all cybersecurity controls. The reason is that cybersecurity controls aren’t mutually exclusive. For instance, those required by compliance programs affect cyber threats’ remediation from cloud assets and third-party risk management.
Research by EY confirmed this.
Their study found that companies using a centralized platform performed vendor risk control assessments much faster:


Done with an automated, centralized platform like Cyber Sierra, enterprise companies can even do more. For instance, a global bank leveraging our platform was able to streamline their entire workflow.
A snippet of their success story reads:


It doesn’t end there.
Other cybersecurity controls are better implemented with a centralized, automated platform. Take the ongoing implementation of governance and compliance program controls. With a platform like Cyber Sierra, enterprise security teams get two benefits.
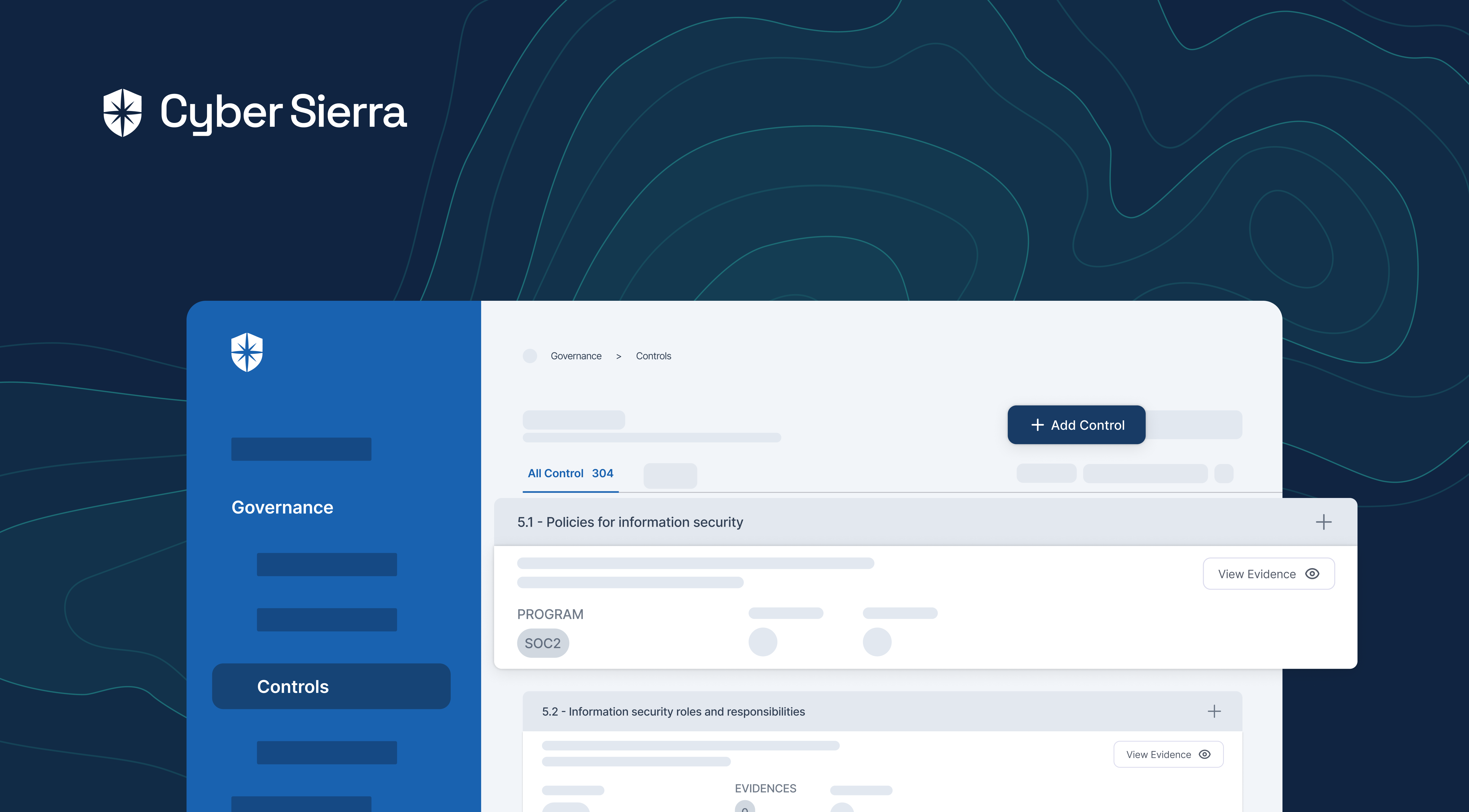
First, all controls of compliance programs you need to become compliant with are auto-consolidated into a single dashboard:
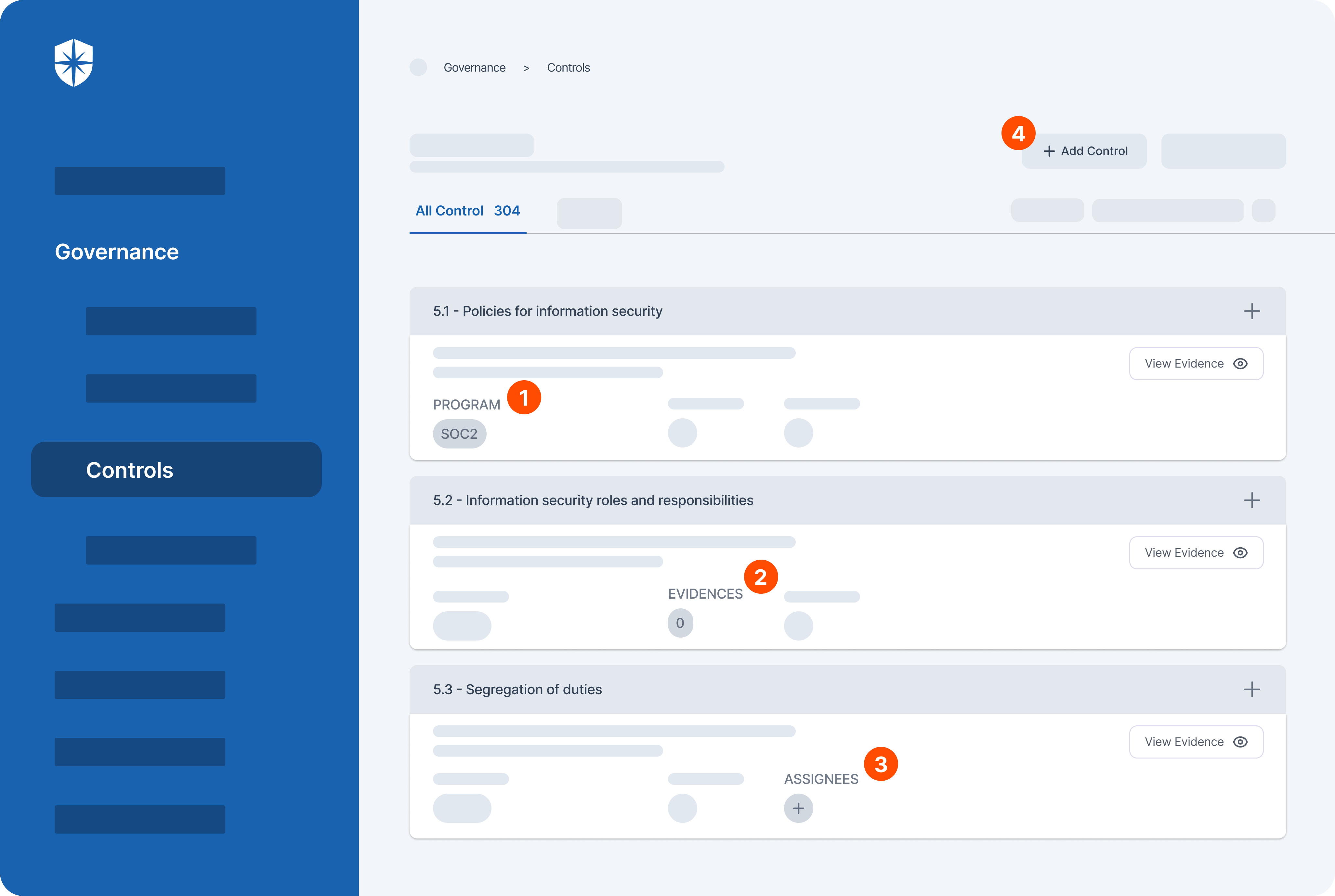

As shown, from this pane, you can:
- See what programs a control is attached to
- View and update evidence of having that control
- Assign control implementation to team members
- Add new compliance program controls as they emerge.
Second, after initial implementation, our platform automatically monitors and flags all control breaks for immediate remediation.
Here’s a peek:
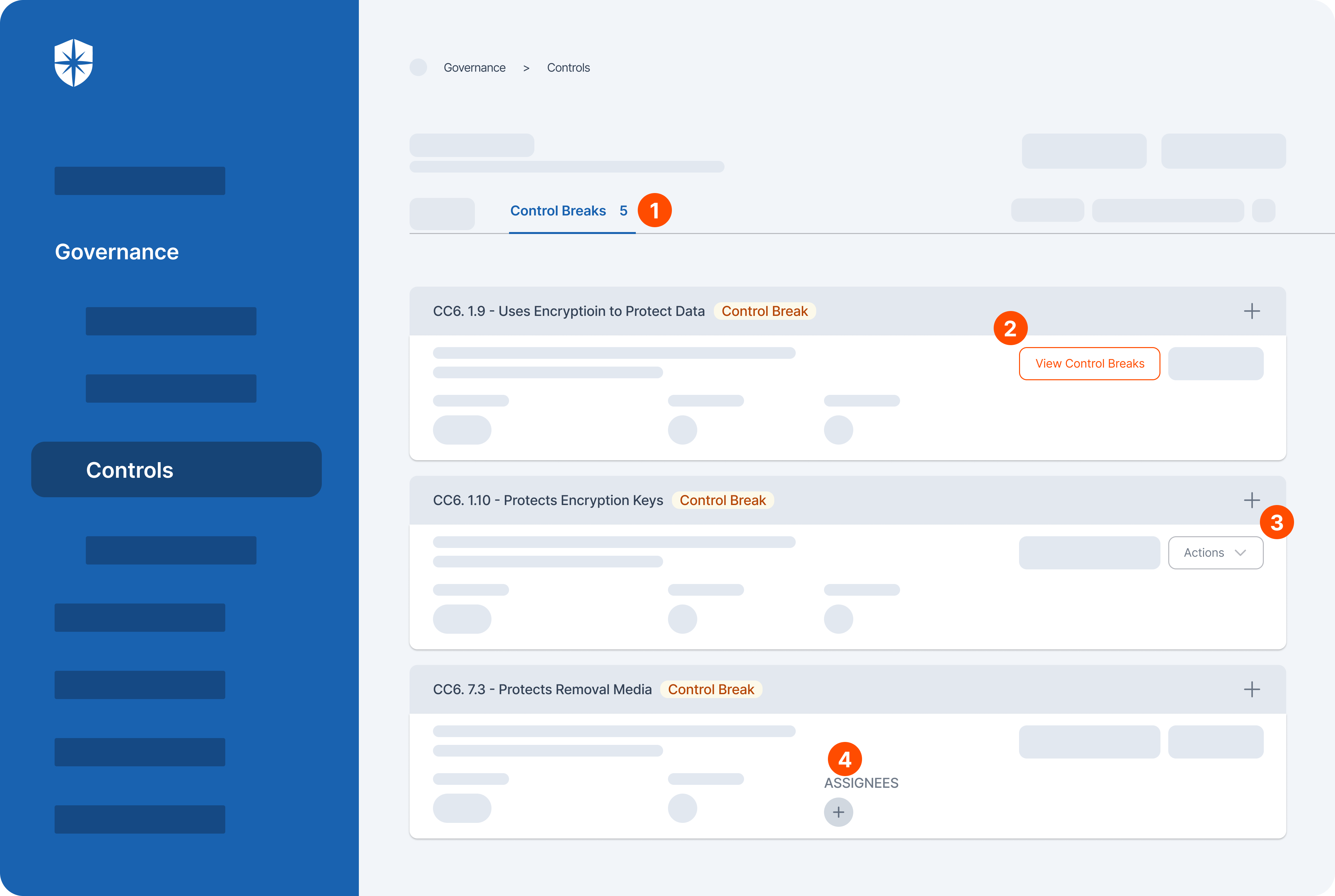

From here you can easily:
- Monitor control breaks across all compliance programs
- View details of each control break
- Get action tips for remediating each control break, or
- Assign their remediation to anyone on your security team.
Implement Cybersecurity Controls with Ease
A point worth re-stressing is that cybersecurity controls aren’t mutually exclusive. The controls you need for becoming and staying compliant to governance and compliance programs relate to your internal risk management controls. To this end, it makes sense to constantly implement and monitor all controls from a single platform.
Aditya Anand shared how the security team at Hybr1d achieves both with Cyber Sierra’s intelligent, interoperable cybersecurity platform.
In his words:


Hybr1d shows that to easily implement and monitor cybersecurity controls, enterprise companies should consider using an automated, interoperable platform like Cyber Sierra.
And you can start with a free demo:



A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.