How to Choose (and Implement) Relevant TPRM Frameworks





















Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
What do Toyota, Okta, and Keybank have in common?
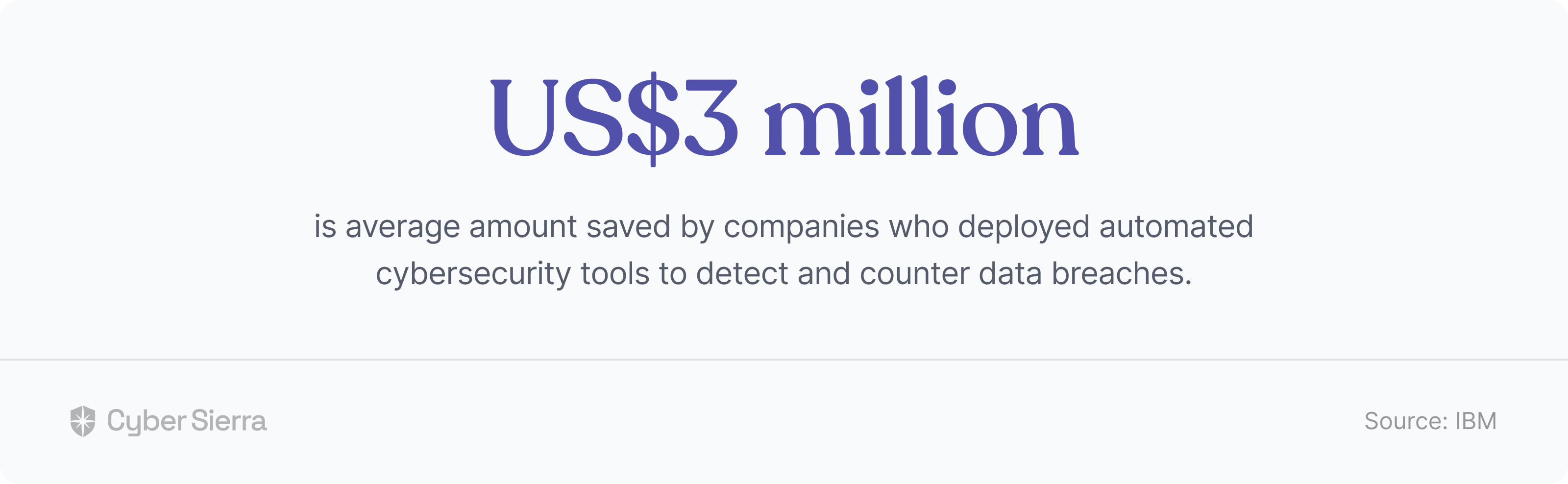
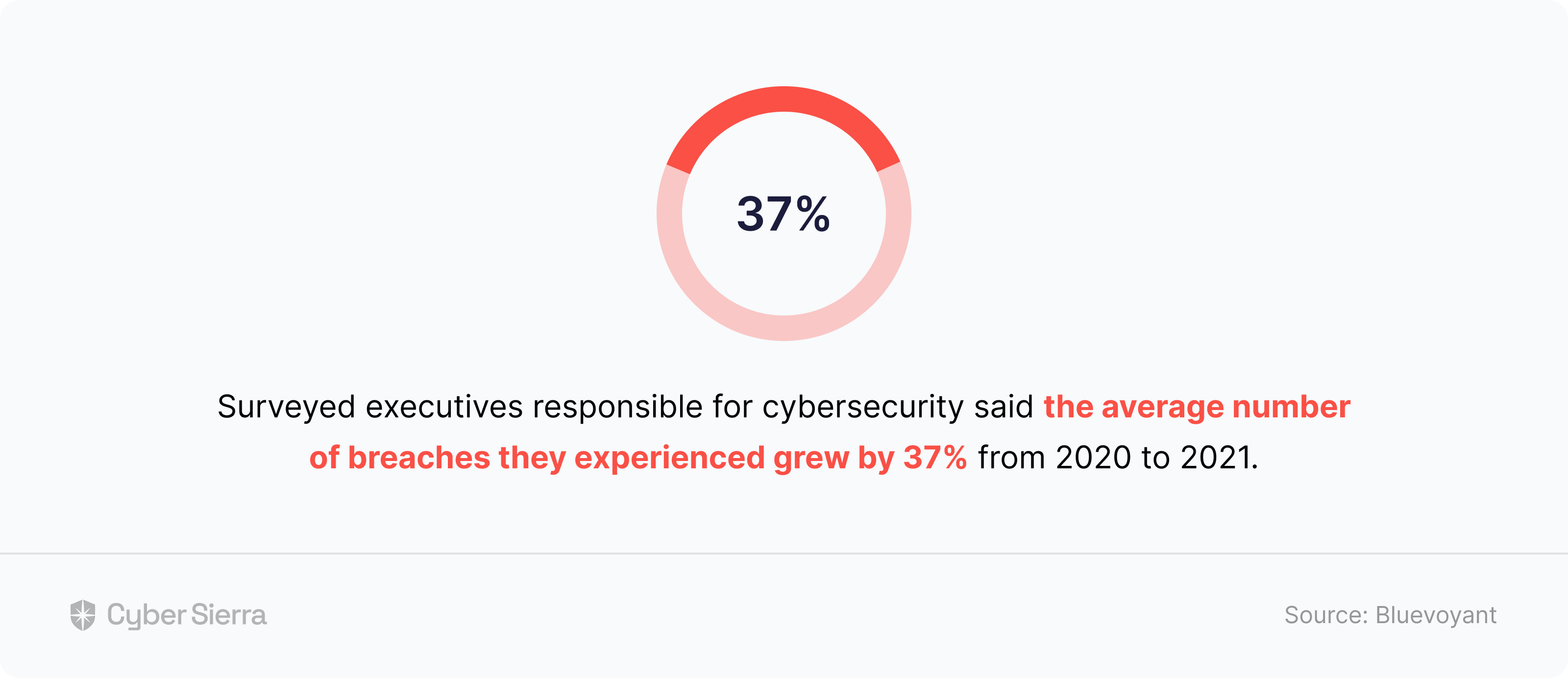
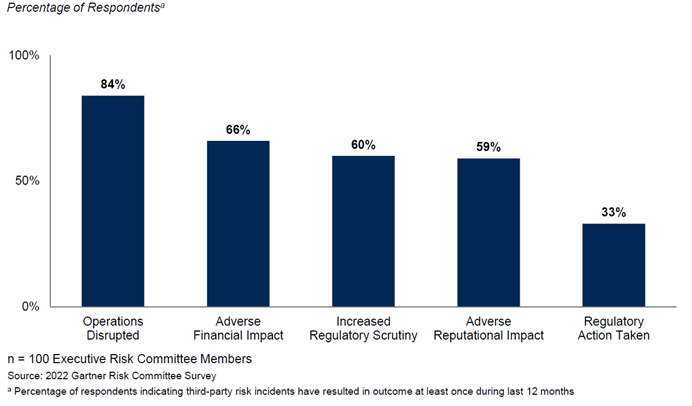
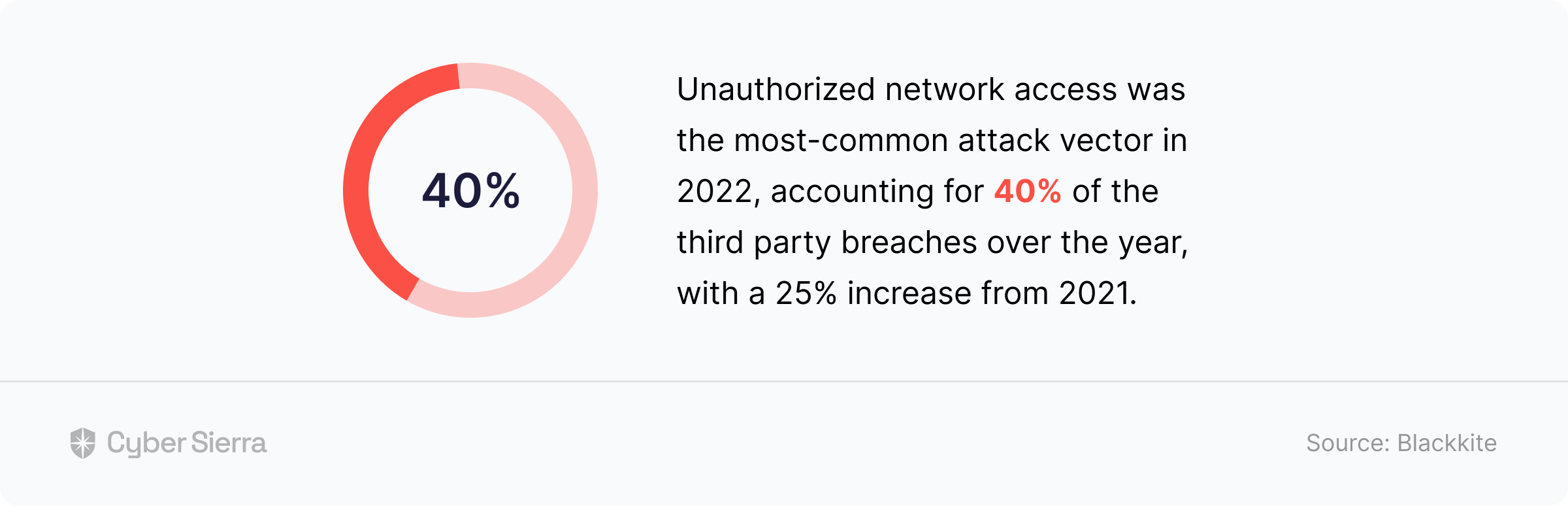
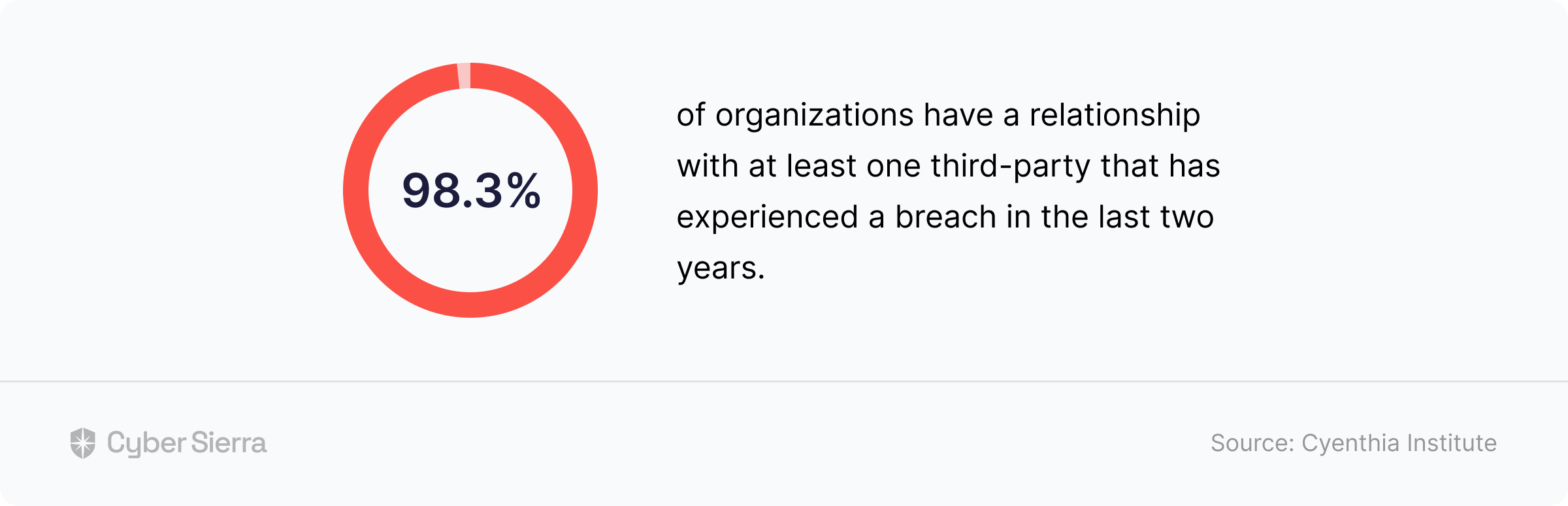
On the surface, not much, given they operate in different sectors —car manufacturing, B2B software, and banking, respectively. But review recent cyberattacks that made the news, and you’ll see the commonality: They all suffered major data breaches in 2022 through third-party vendors. Given these are global enterprises, one would argue they had some kind of Third-Party Risk Management (TPRM) framework in place.
It begs the question:
Why do companies suffer data breaches through third-parties, despite having some way to manage risks?
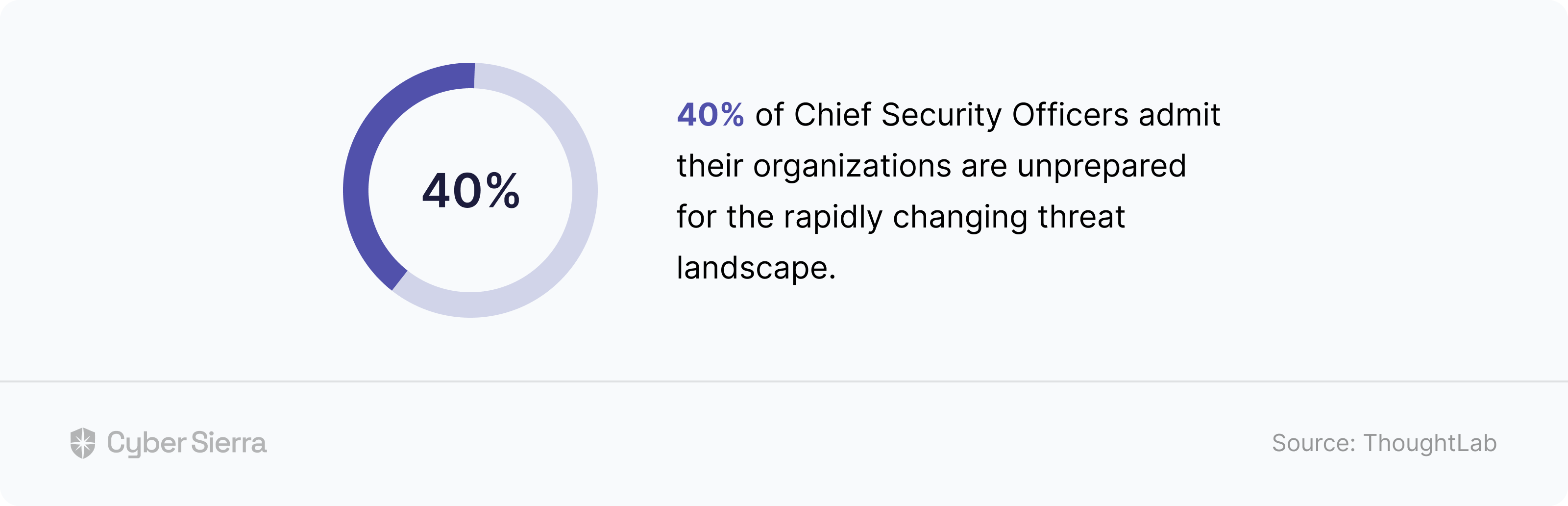
If you’re a CISO or an enterprise security exec pondering over that question, here’s the likely answer. First, choosing the right TPRM framework is crucial, but it’s not enough. This is because no matter how good one may be, it is only useful if effectively implemented.
And that brings us to the rest of this article.
We’d explore the top enterprise TPRM frameworks you can choose from. More importantly, you’ll see how our interoperable cybersecurity platform, Cyber Sierra, effectively streamlines their implementation.
The Top Enterprise TPRM Frameworks
According to a report by RSI Security:


In other words, TPRM frameworks developed by NIST and ISO come recommended. But there are variations of these, so choosing which ones to implement should be based on your company’s specific needs.
To help you do that, below are the various frameworks designed by both institutions and their relevance to enterprise TPRM.
1. NIST Supply Chain Risk Management Framework (SCRMF) 800-161
NIST 800-161 was developed to supplement the NIST 800-53 designed specifically to help federal entities manage supply chain risks.
However, given the large number of 3rd parties enterprise organizations now work with, private sector organizations can also adopt NIST 800-161. This framework breaks down the supply chain or vendor risk management process into four phases:
- Frame,
- Access,
- Respond, and
- Monitor:
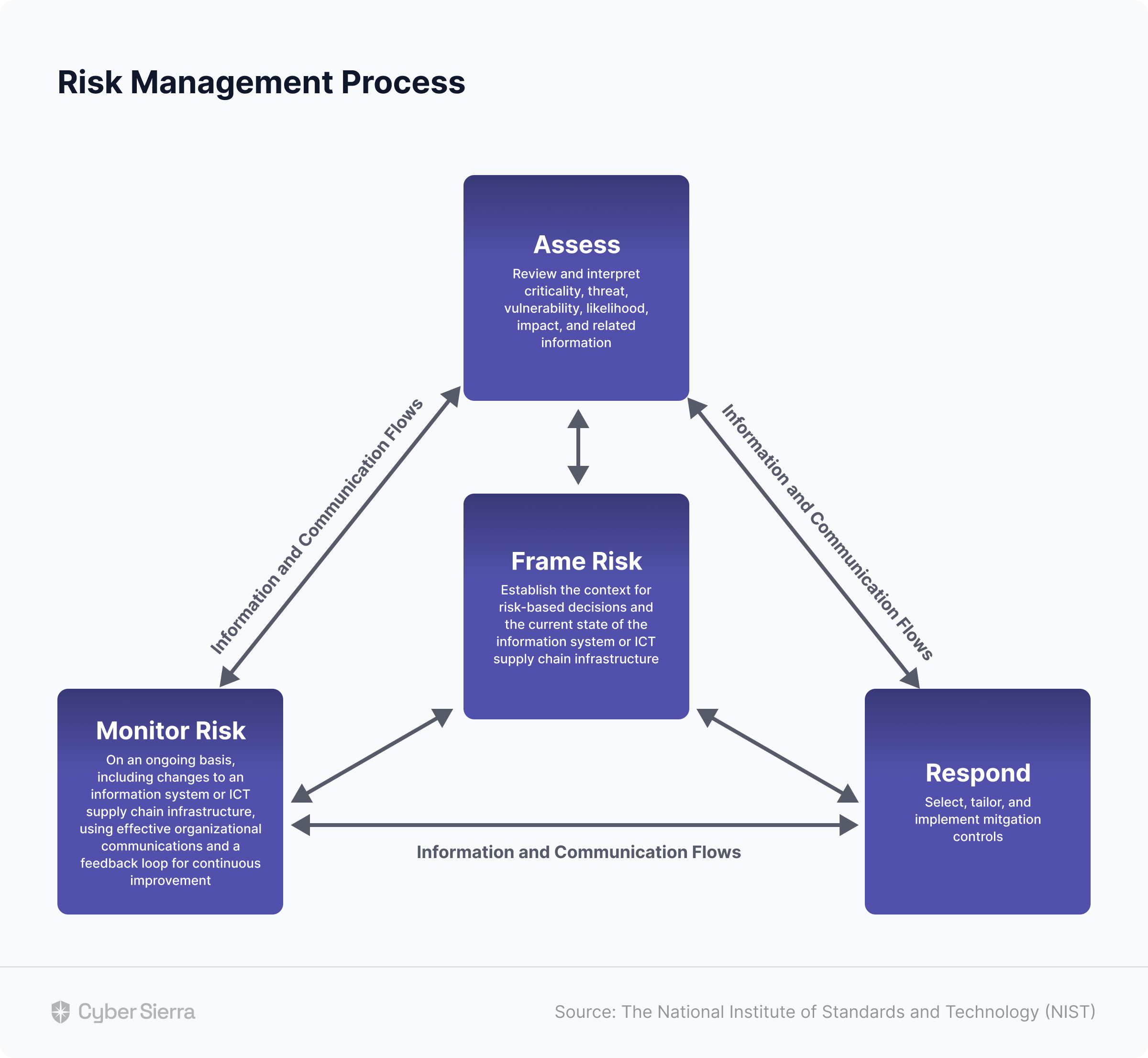

Across these phases, there are 19 data security control themes, ranging from employee training to systems and service acquisition.
2. NIST Vendor Risk Management Framework (RMF) 800-37
Originally developed in 2005, the National Institute of Standards and Technology (NIST) revised this framework in 2018.
Generally, the NIST 800-37 RMF outlines steps companies can take to protect their data and systems. This includes assessing the security of systems, analyzing threats, and implementing data security controls. For vendor risk management purposes, section 2.8 of the framework specifically fits the bill. It is invaluable as it helps security teams consider relevant risk mitigation tactics for onboarding new third-parties.
3. NIST Cybersecurity Framework (CSF)
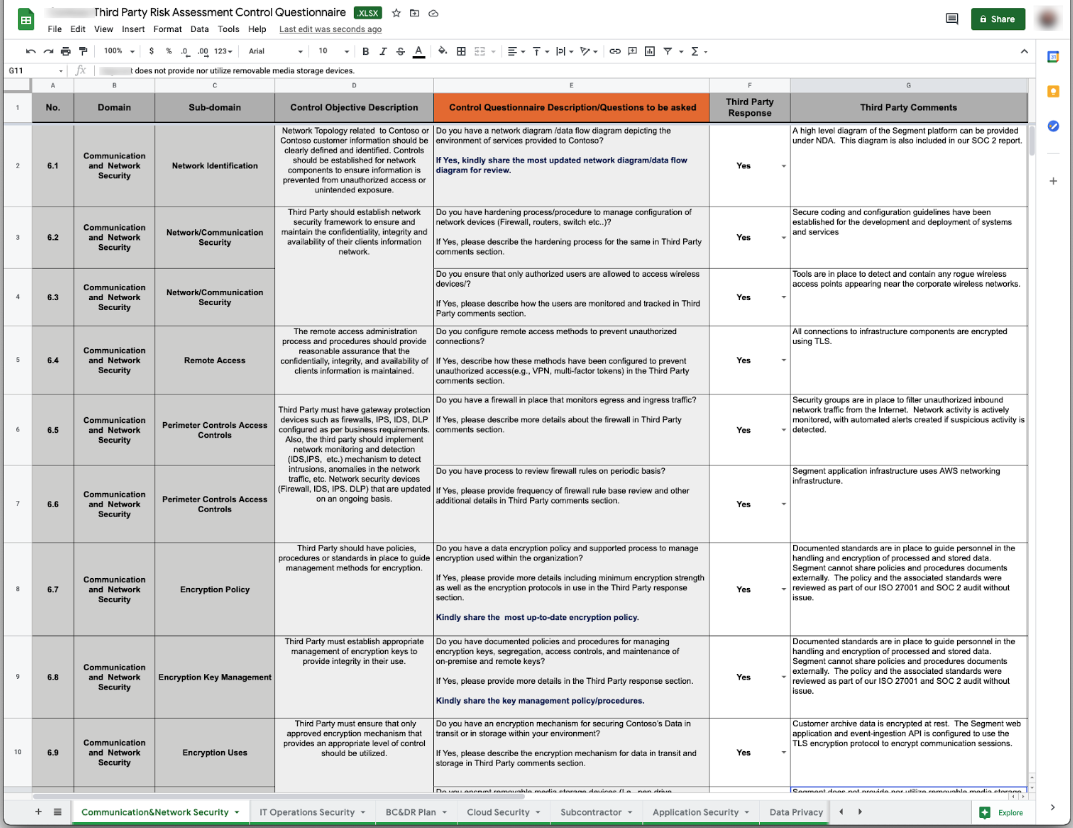
Considered the gold standard for building robust data security programs, the NIST Cybersecurity Framework can also be used when designing third-party risk management processes. Specifically, this framework outlines the best practices for creating vendor risk assessment questionnaires.
Base your third-party risk assessment questionnaires on security controls in the NIST CSF framework, and your team can accurately assess potential vendors’ cyber threat profiles. This is especially useful for enterprise organizations with strict privacy or regulatory compliance concerns.
4. ISO 27001, 27002, and 27018
The International Organization for Standardization (ISO) developed the ISO 27001, 27002, and 27018 standards. Although known more for implementing governance, risk, and compliance (GRC) programs, these standards can also be used in creating frameworks for evaluating third-party risks.
Specifically, each of these standards have sections guiding security teams to ensure their vendor risk assessments are thorough. This is in addition to each standard helping your team manage a broader information security program across your organization.
5. ISO 27036
Unlike other ISO standards focused more on companies’ overall GRC programs, ISO 27036 series helps organizations manage risks arising from the acquisition of goods and services from suppliers.
ISO 27036 has provisions for addressing physical risks arising from working with professionals such as cleaners, security guards, delivery services, etc. It also has more standard processes for working with cloud service providers, data domiciles, and others.
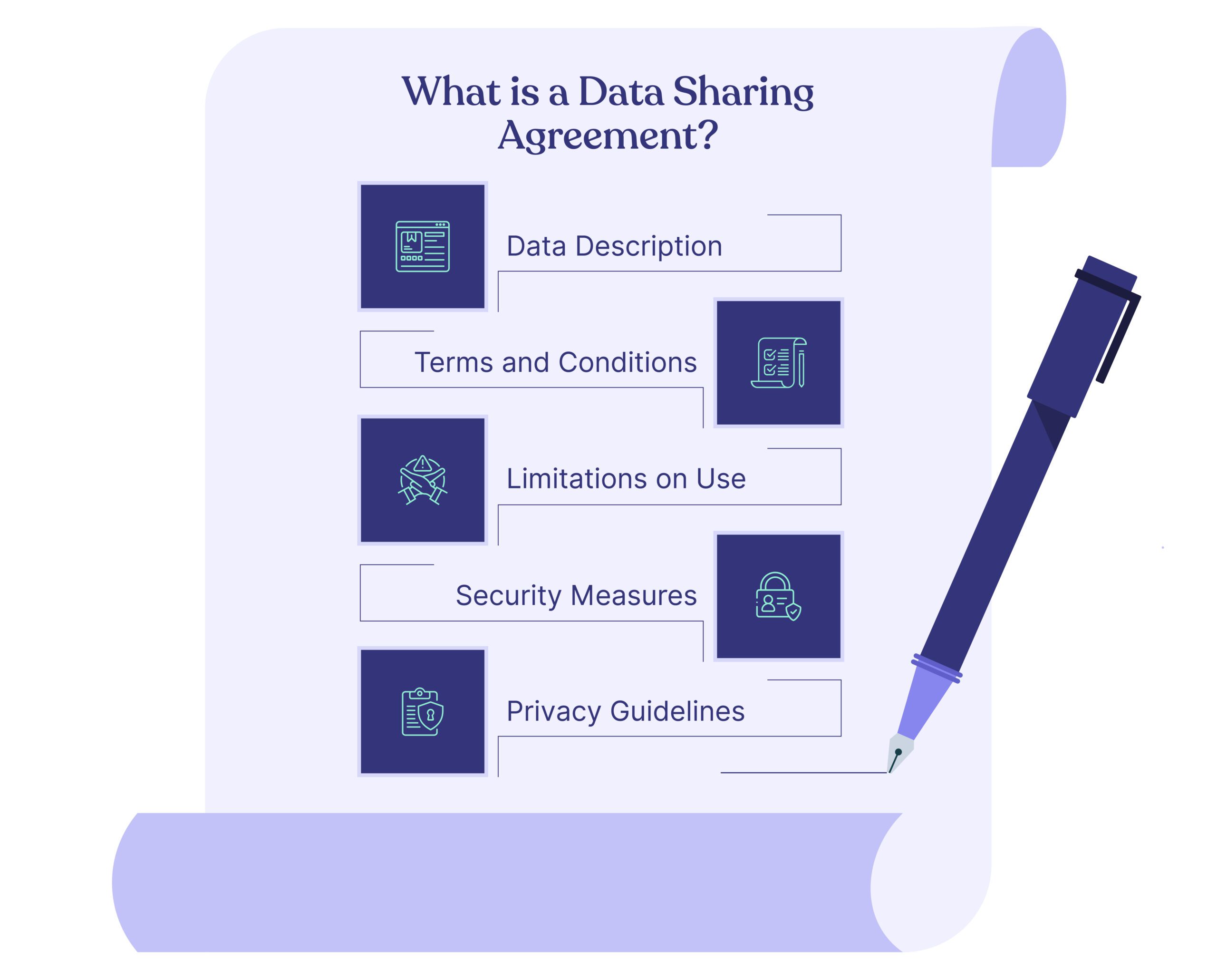
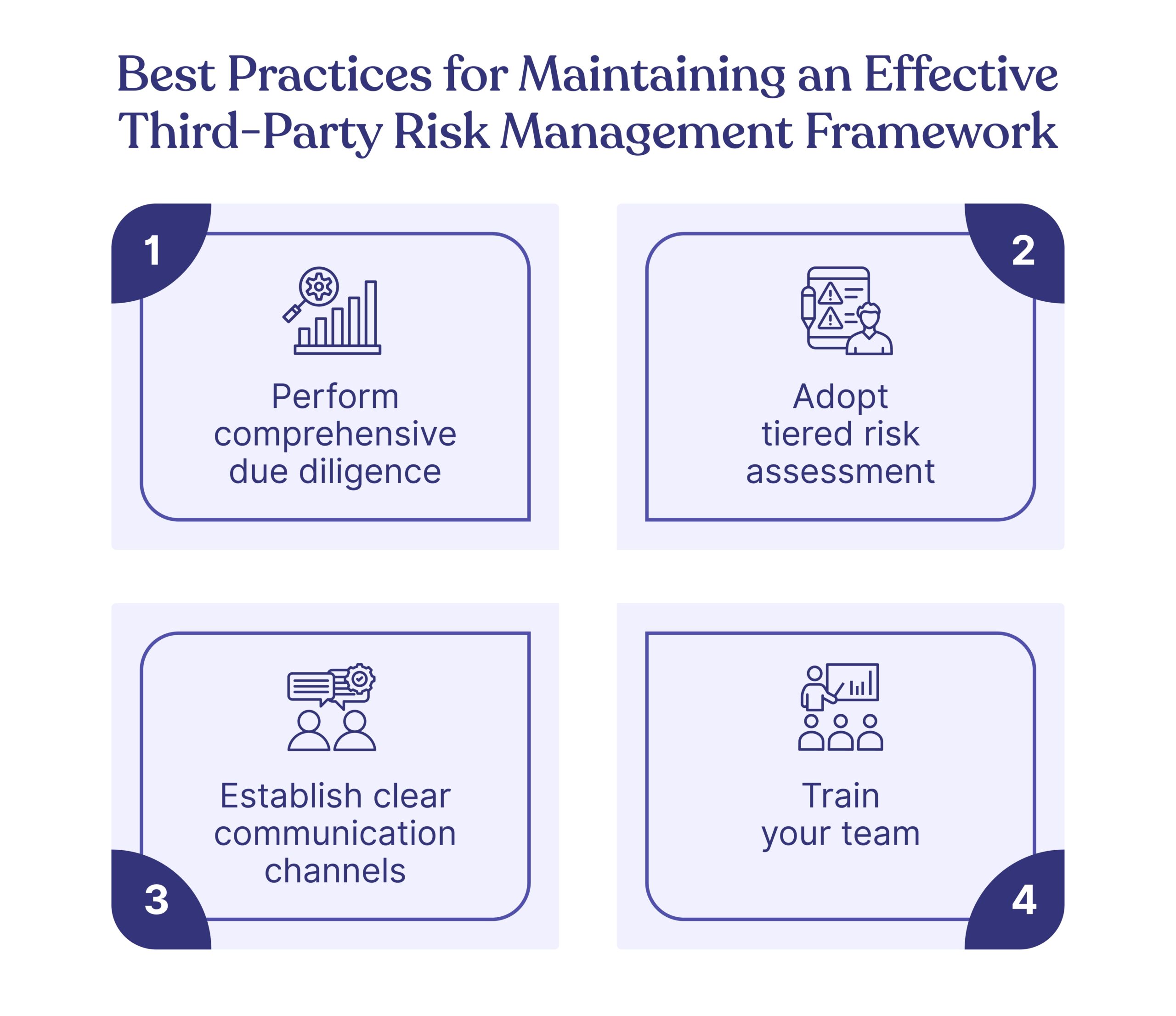
Elements of an Effective Vendor Risk Management Framework
Notice something in the frameworks above?
Each addresses an element of the TPRM implementation process. For instance, NIST 800-37 enforces risk mitigation tactics for onboarding vendors while the ISO 27001 standard helps security teams design comprehensive risk assessment questionnaires.
This means two things:
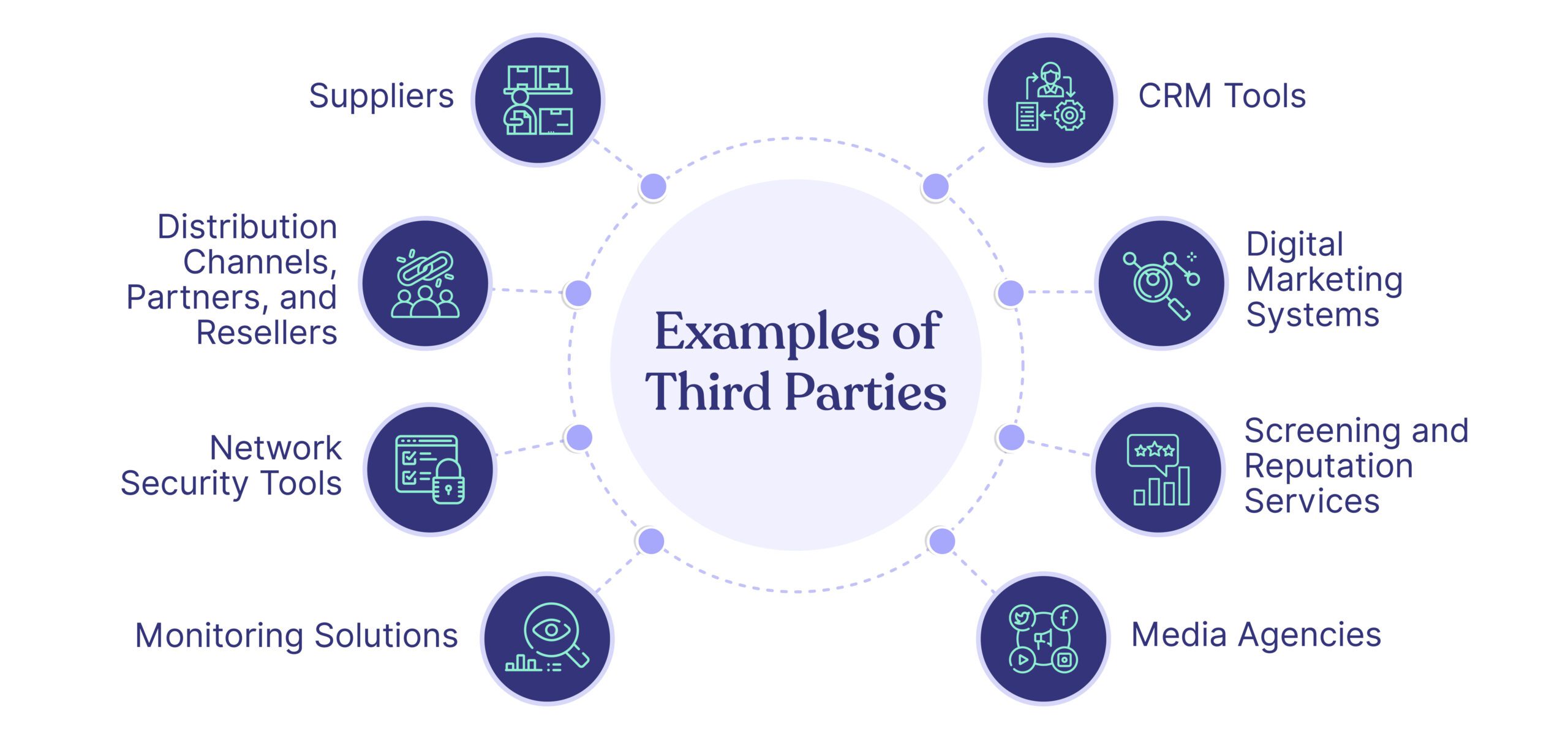
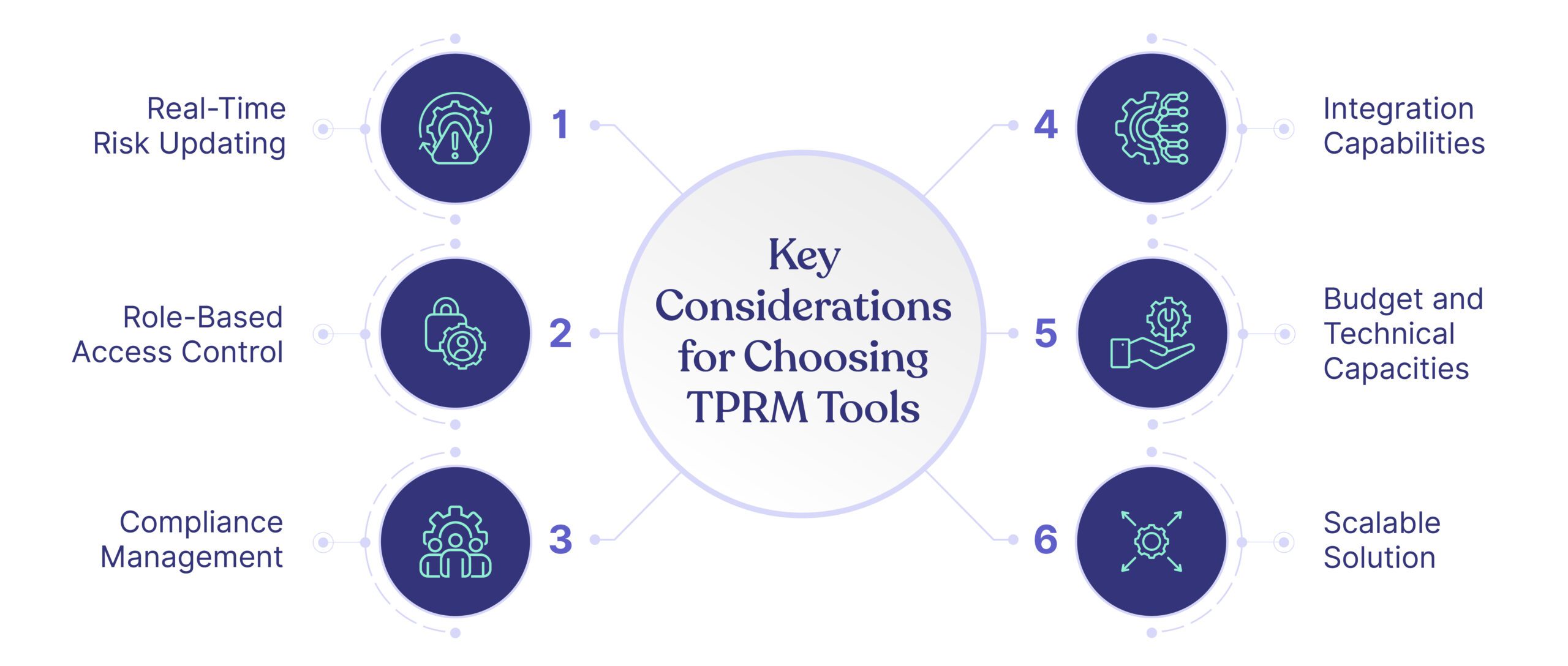
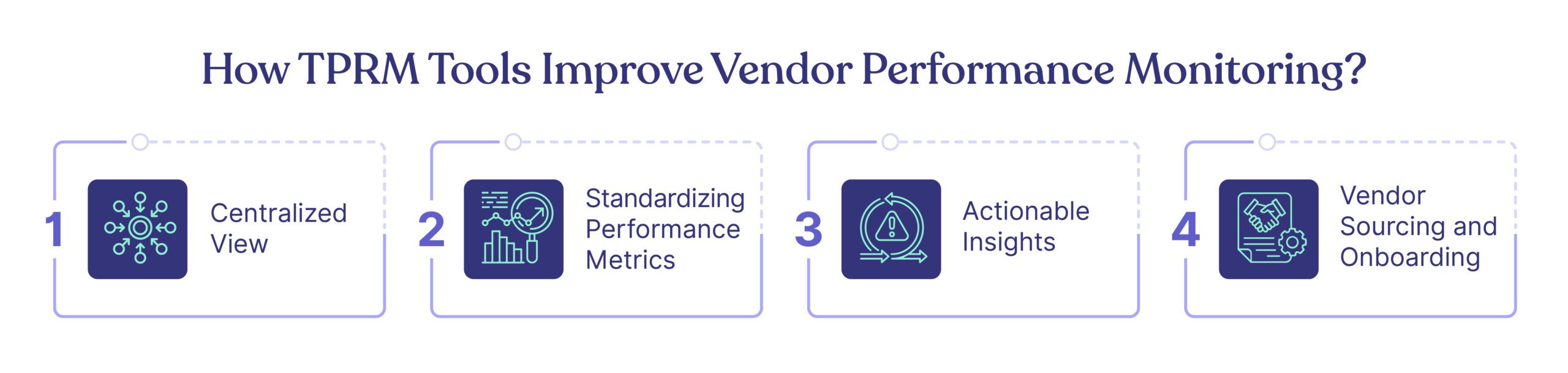
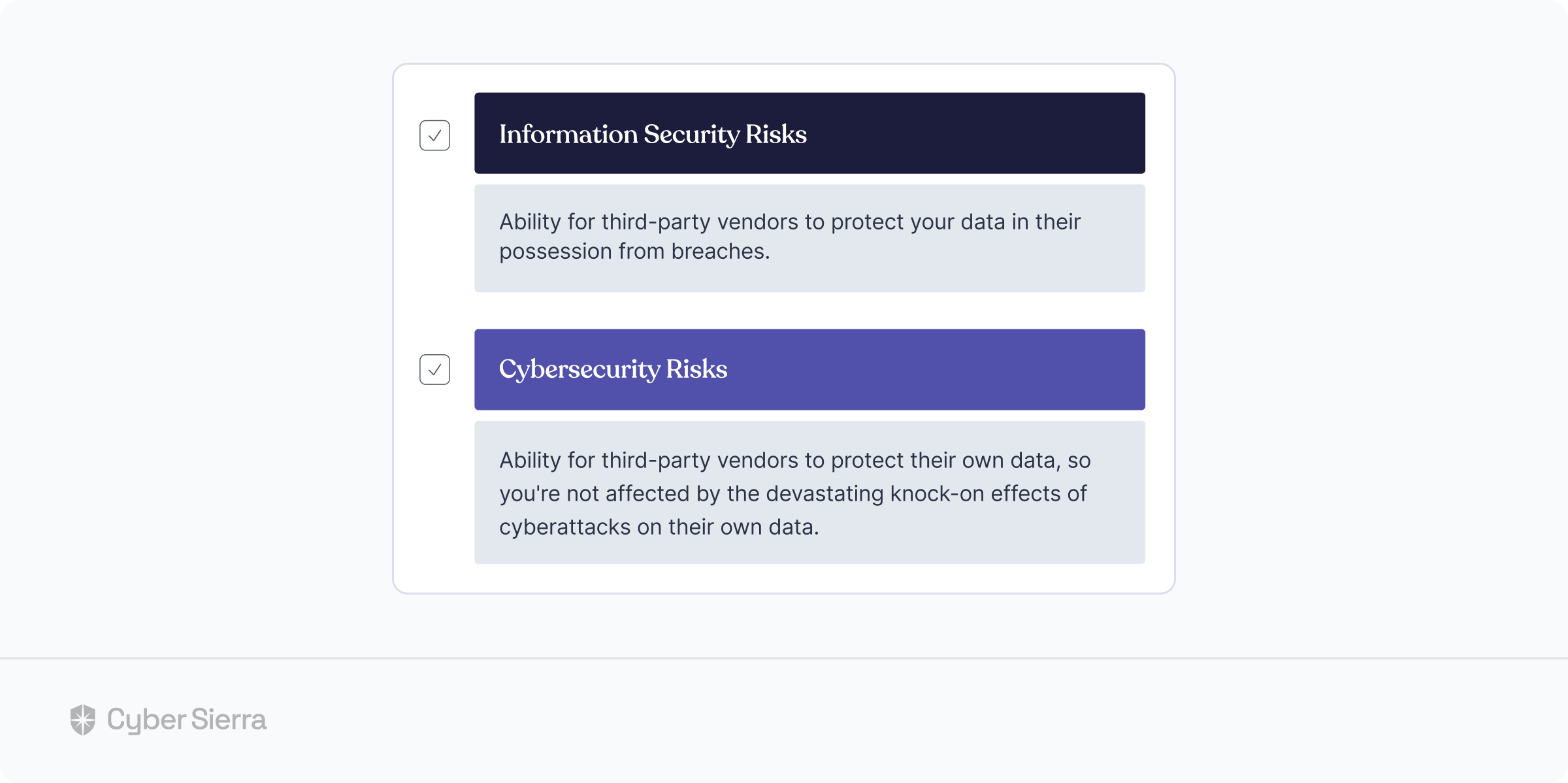
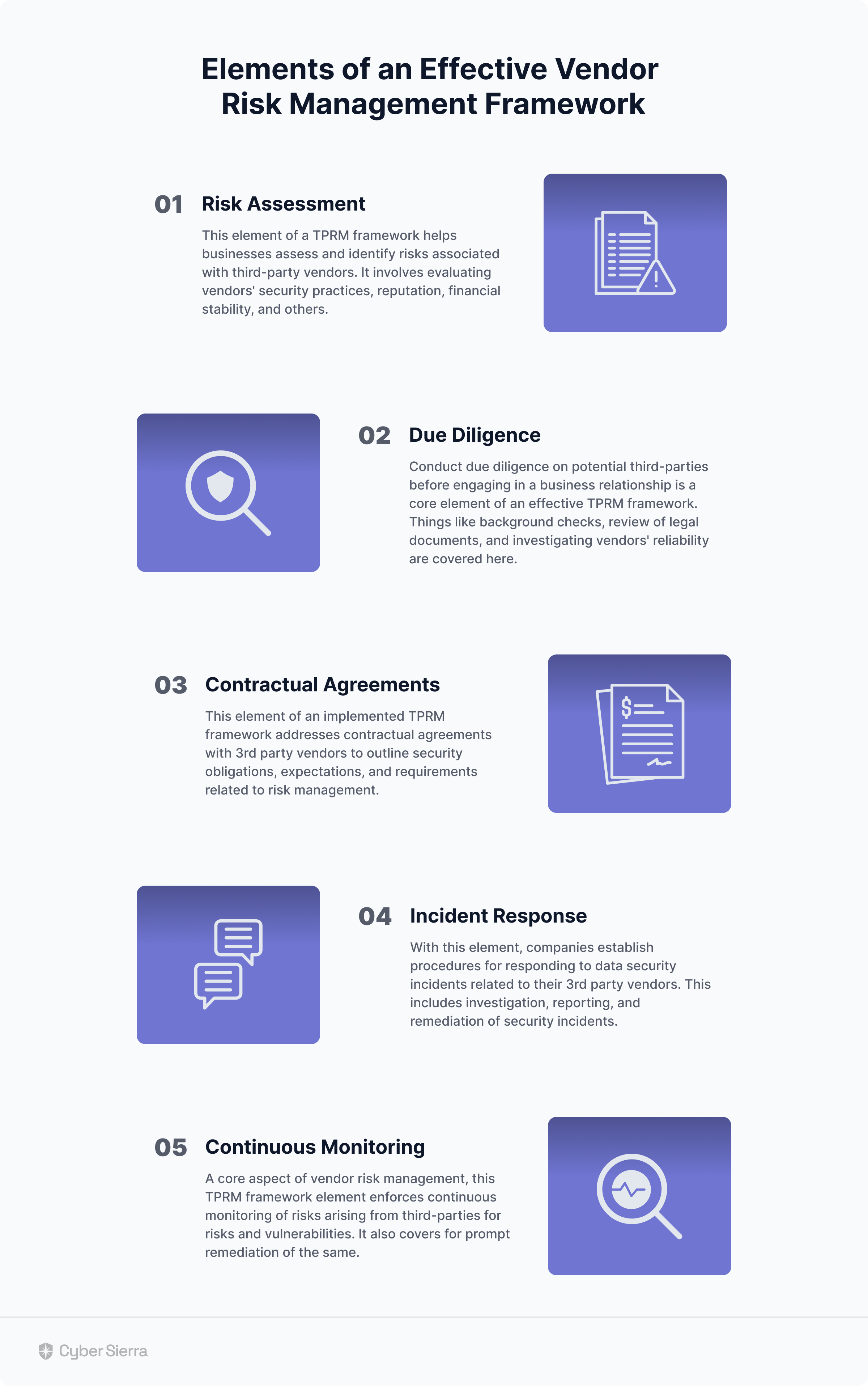
First, for effective vendor risk management, companies may need to combine elements from various TPRM frameworks. The elements (or components) to keep in mind are illustrated below:

Secondly, because trying to cut off sections of various frameworks to achieve all necessary elements is too much manual work, there’s a need to streamline the process with a TPRM tool.
This is where Cyber Sierra comes in:
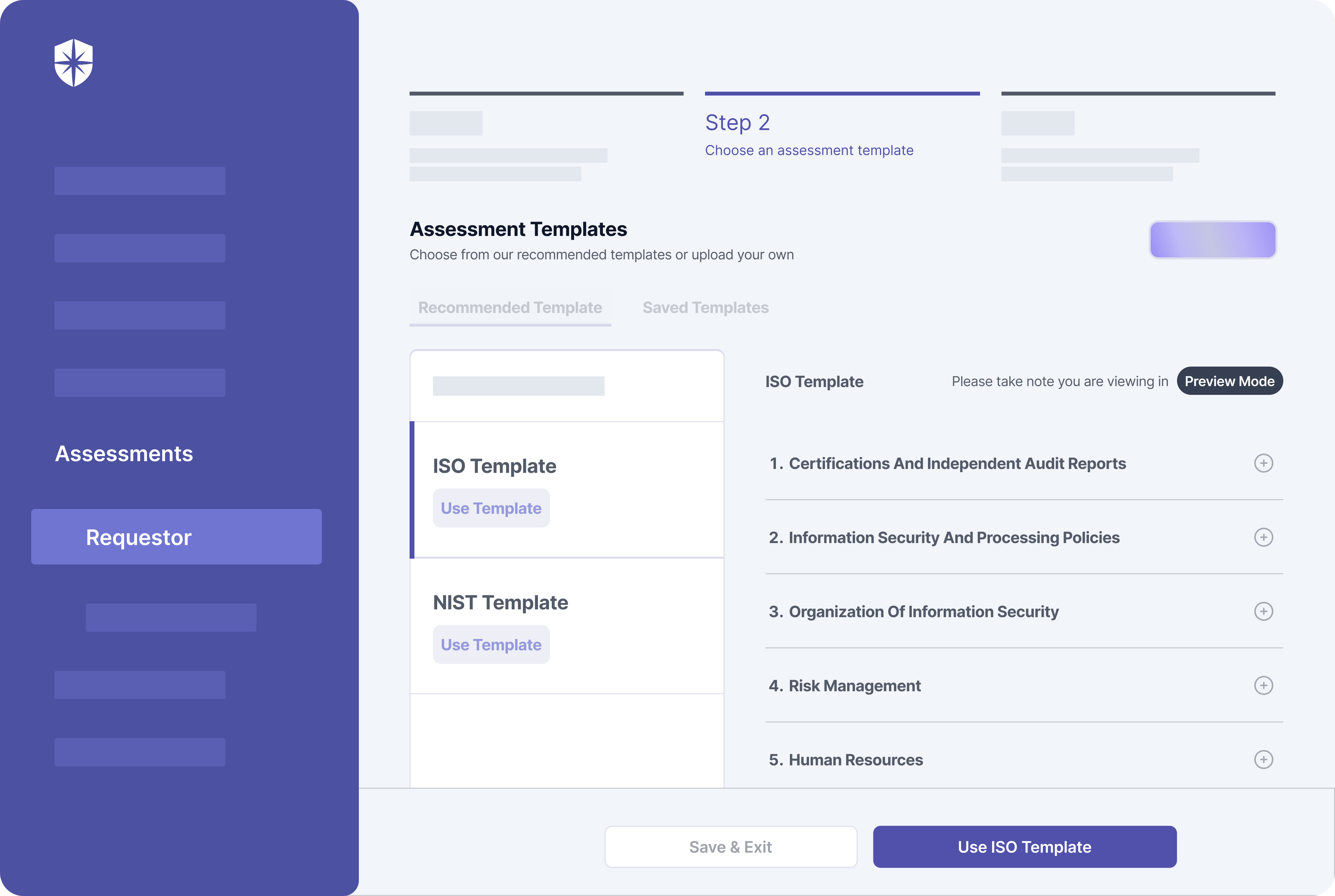


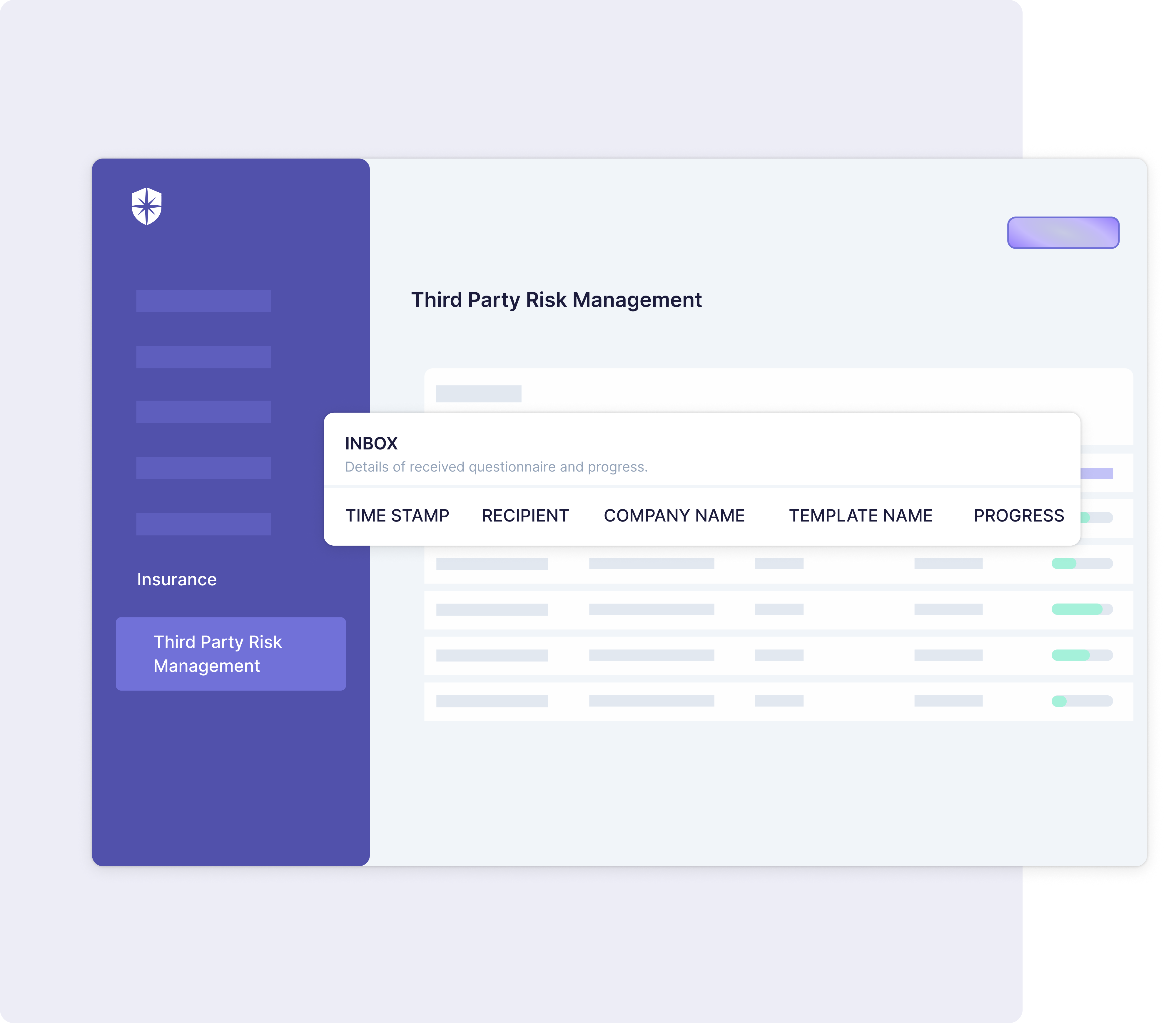
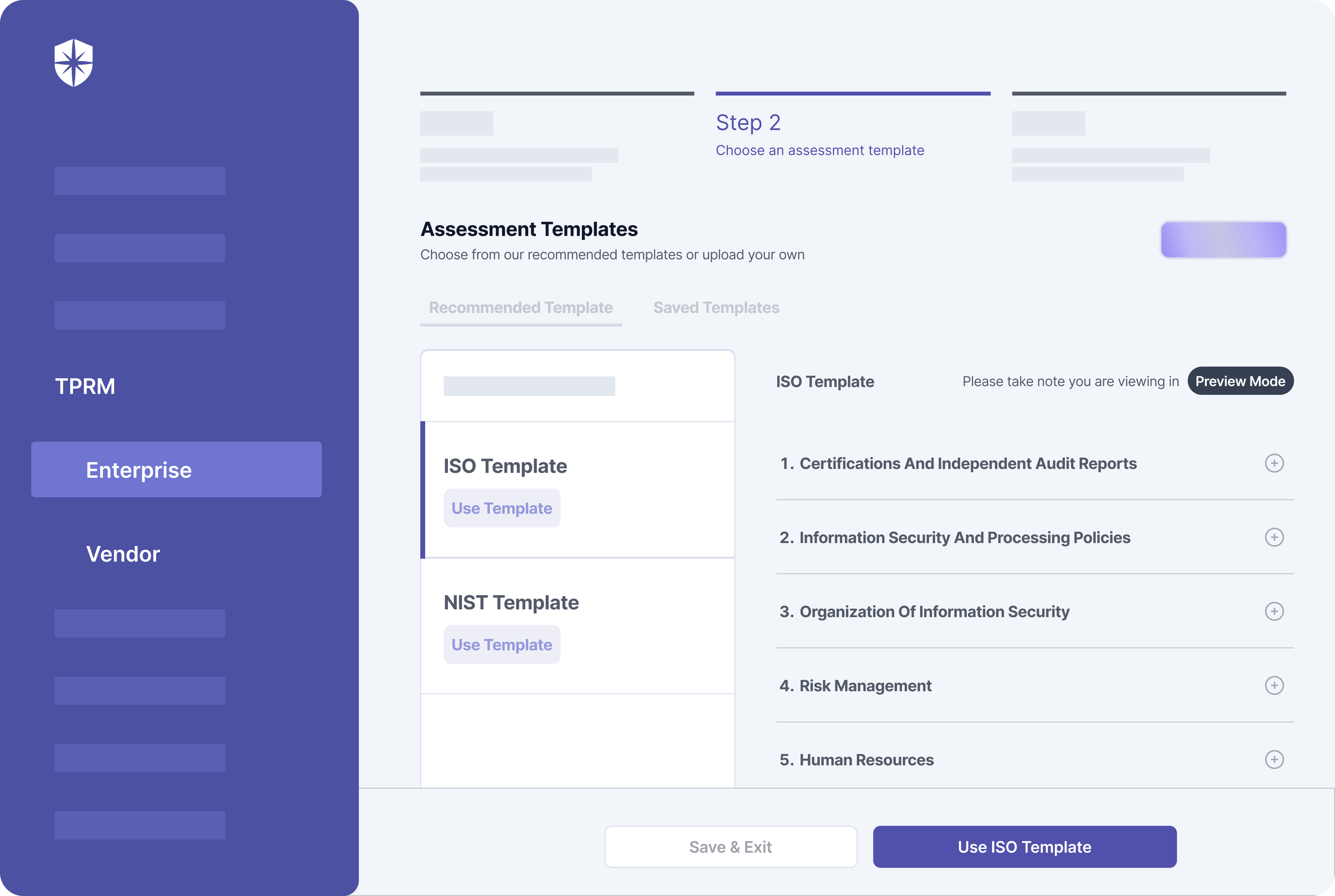
As shown above, our interoperable cybersecurity platform integrates NIST and ISO TPRM frameworks into easy-to-use templates for streamlined implementation.
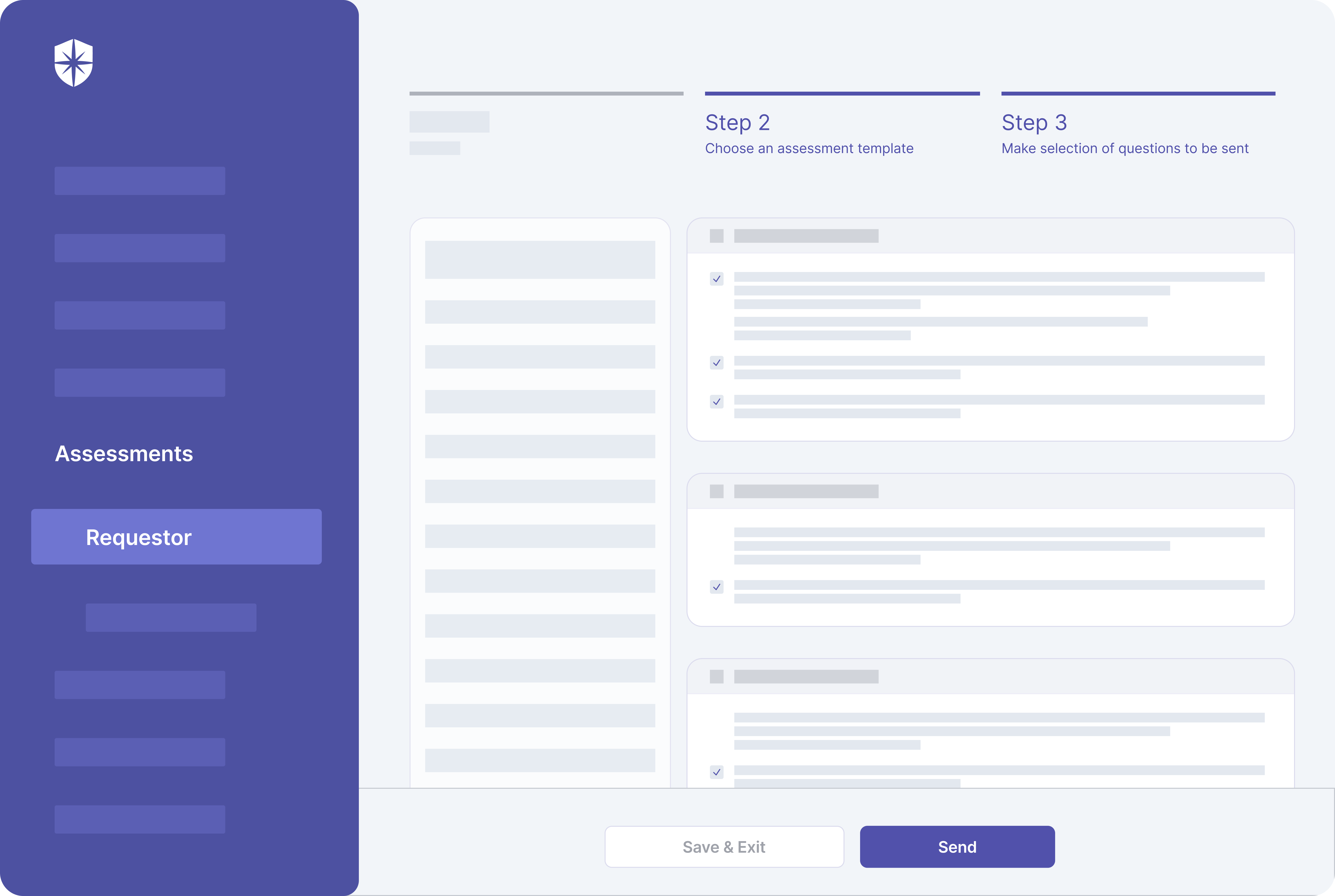
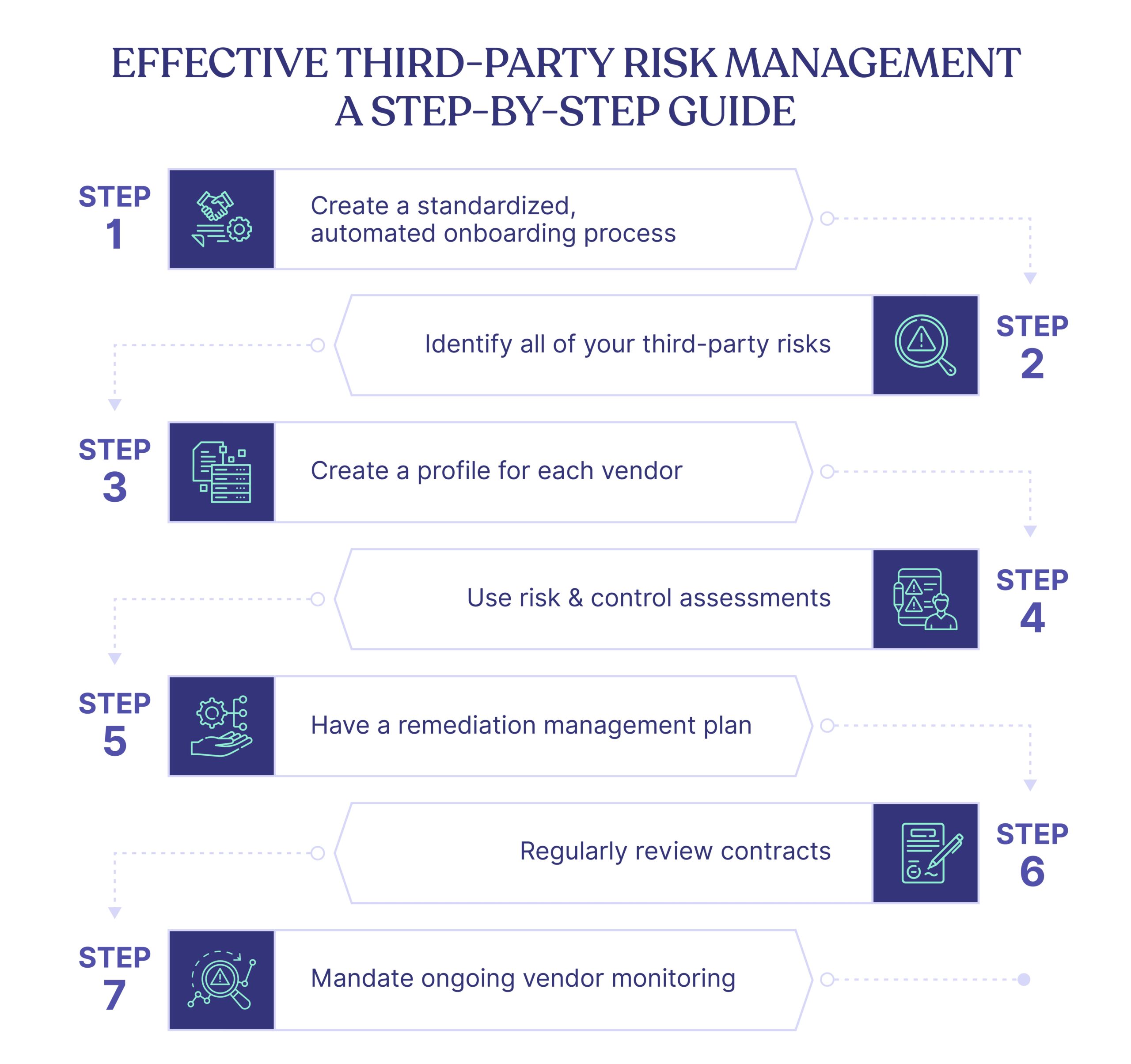
How to Streamline Third-Party Risk Management Framework Implementation
Effective implementation of an enterprise TPRM framework must have all elements illustrated above. Specifically, it must include components for ongoing risk assessment, due diligence, contractual agreements, incidence response, and continuous monitoring.
Here’s how Cyber Sierra automates the critical ones.
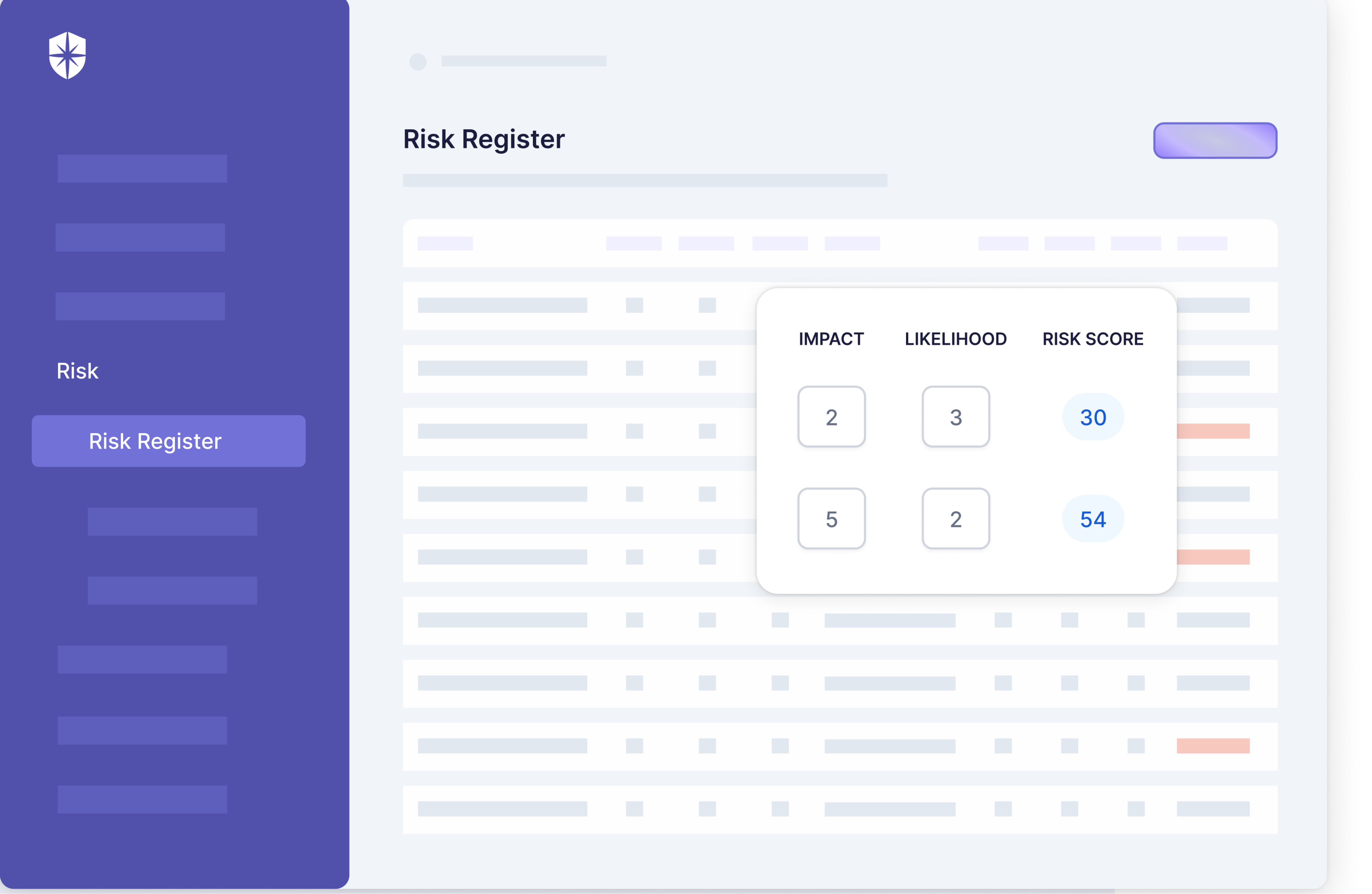
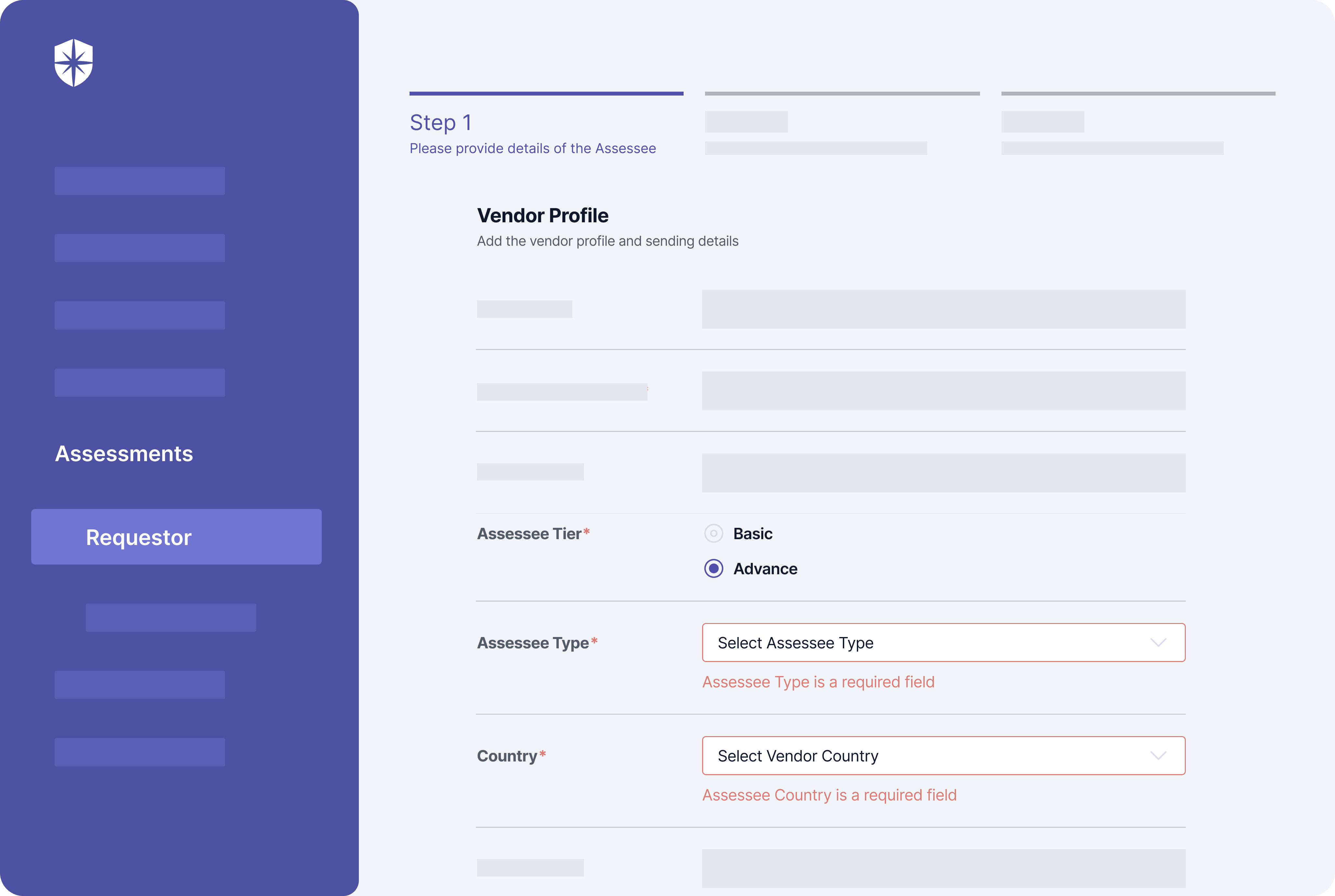
Risk Assessment
This element of a TPRM framework focuses on assessing risks associated with potential third-party vendors. It involves using security questionnaires to evaluate vendors’ security practices, reputation, financial stability, and others.
But there’s a caveat.
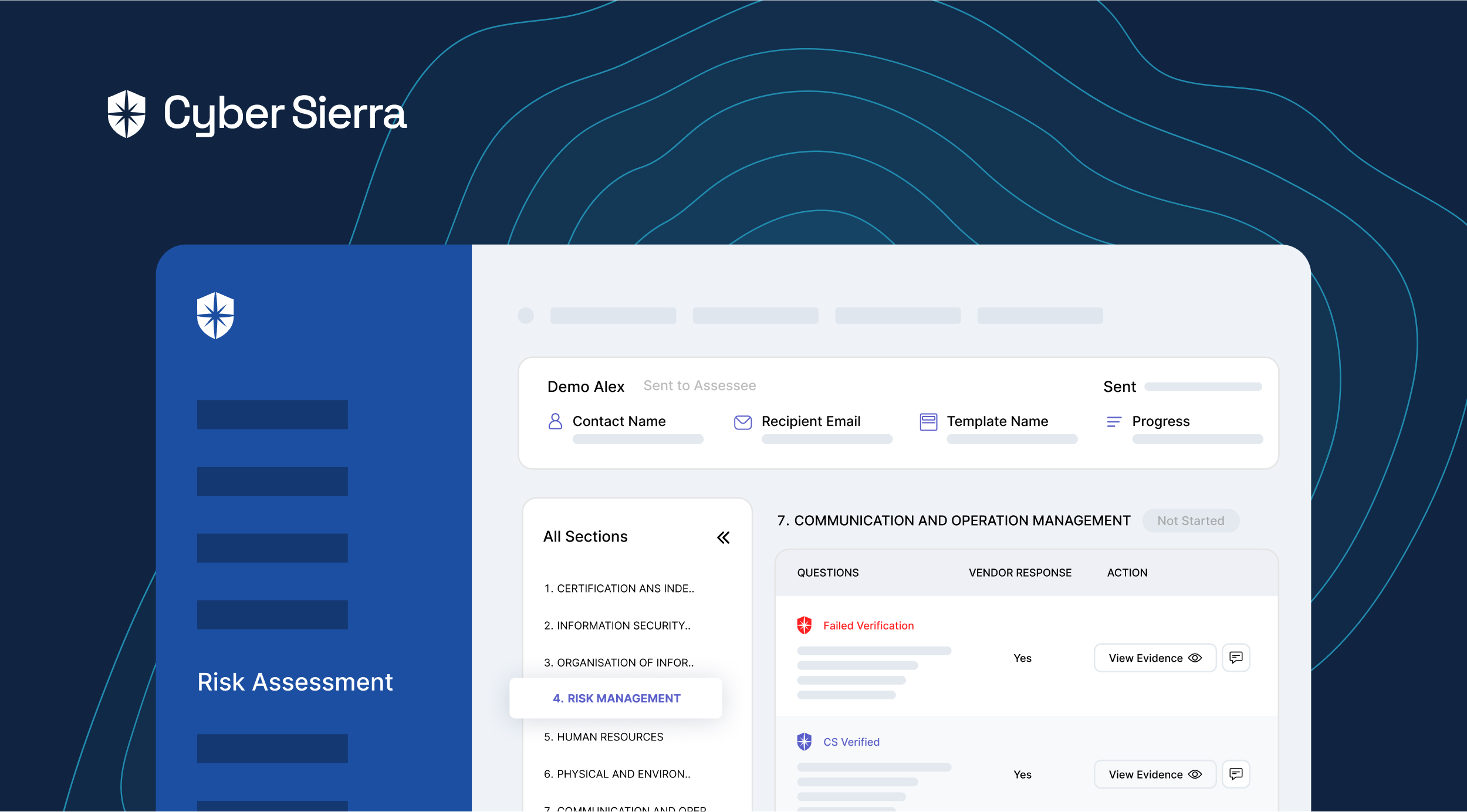
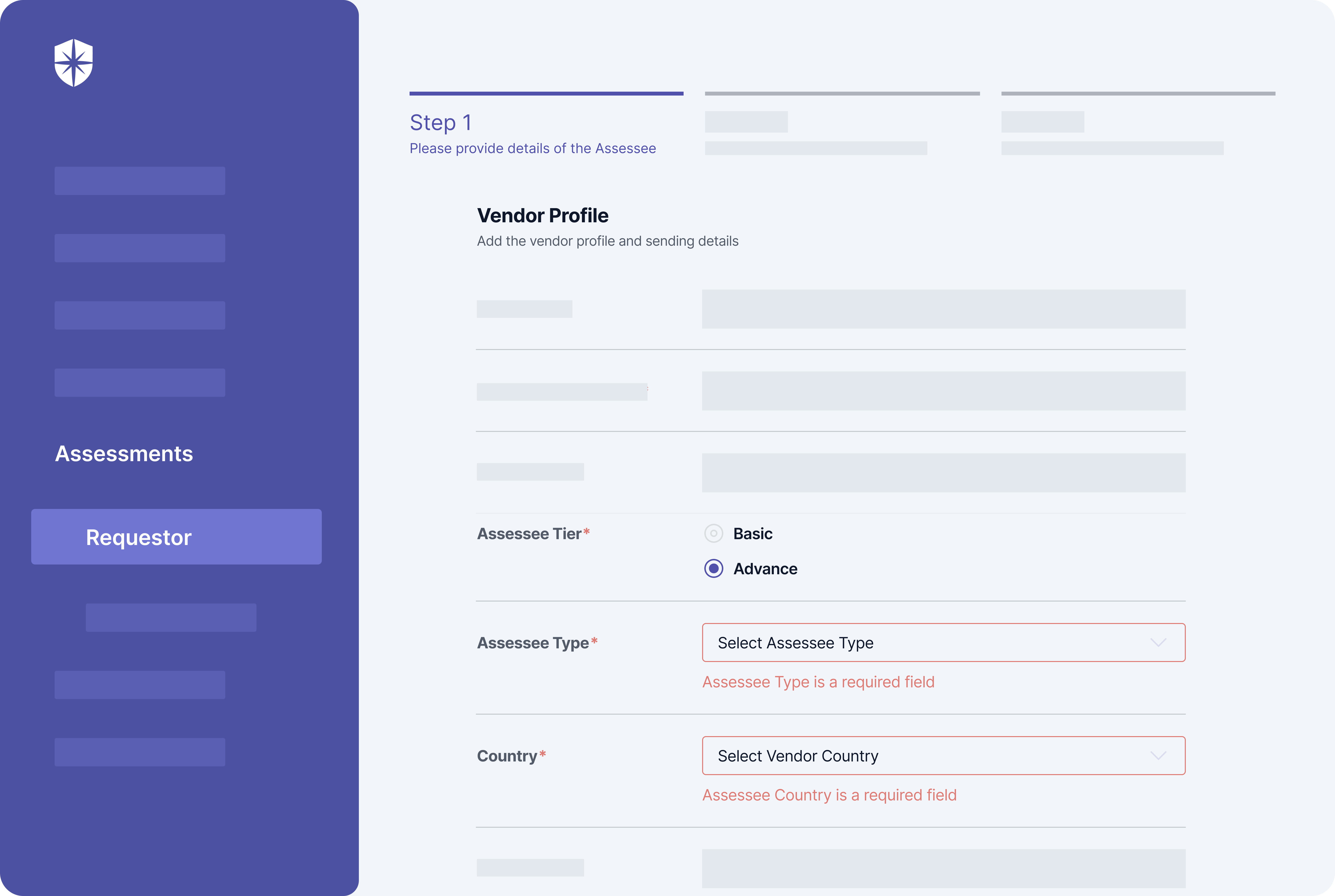
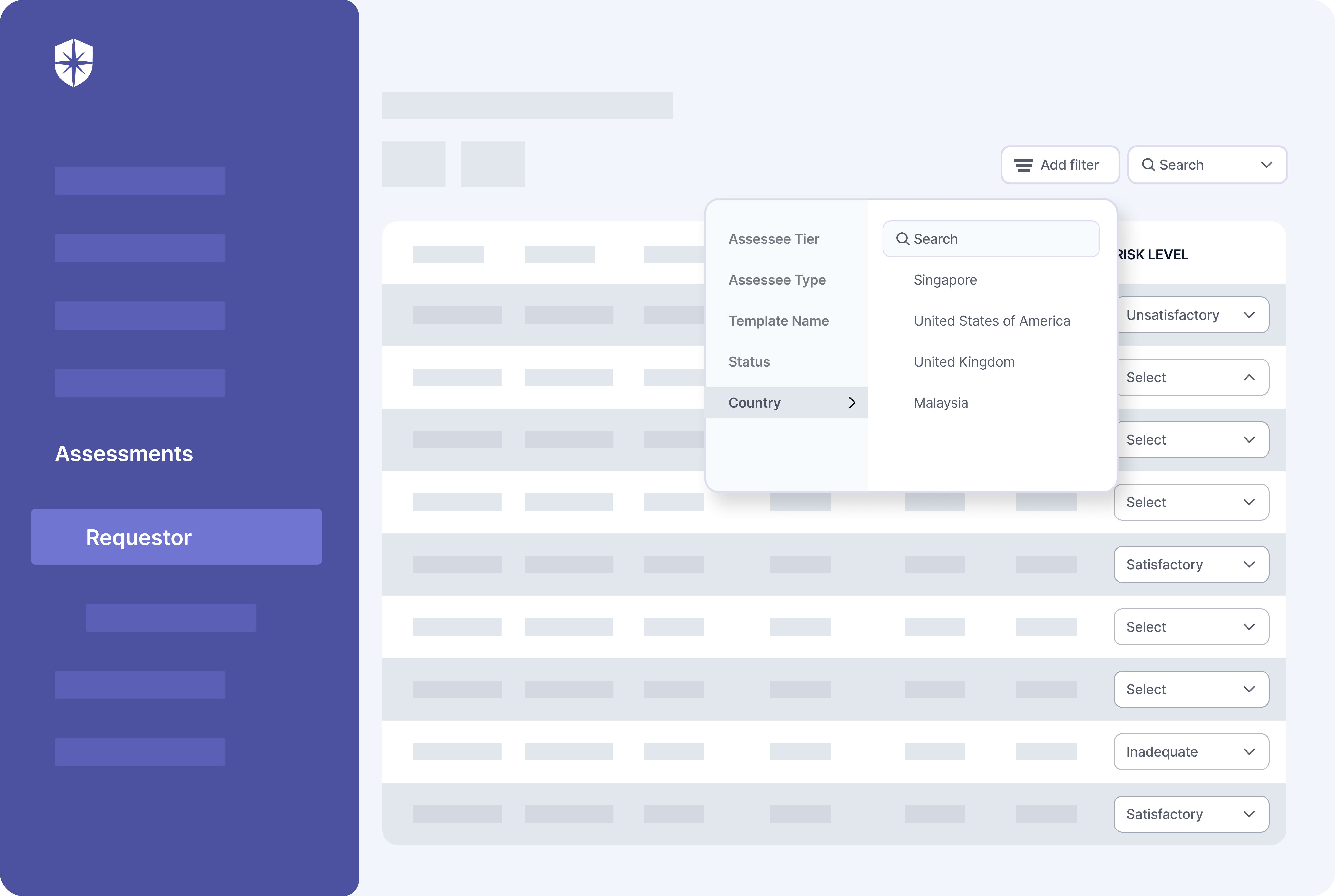
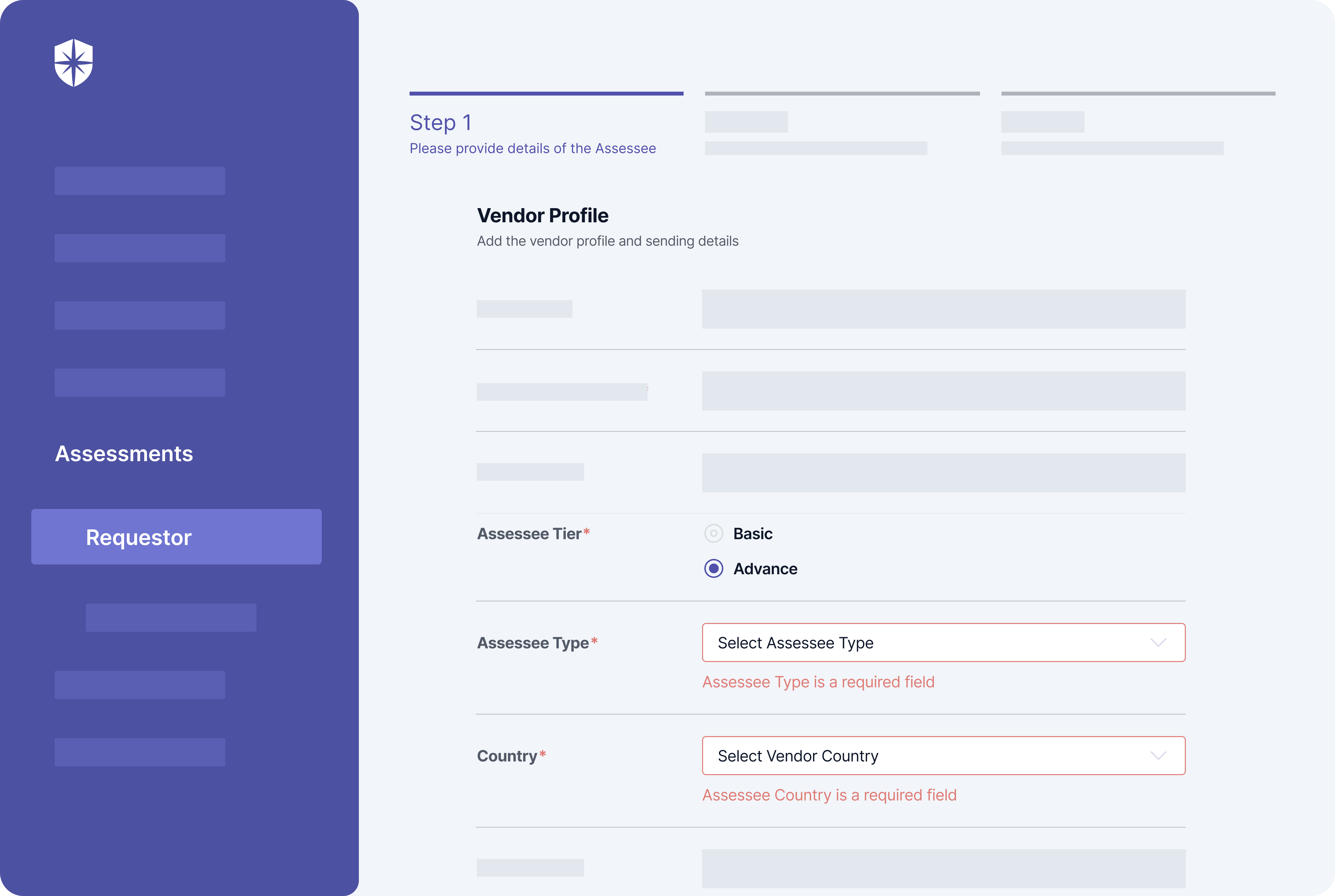
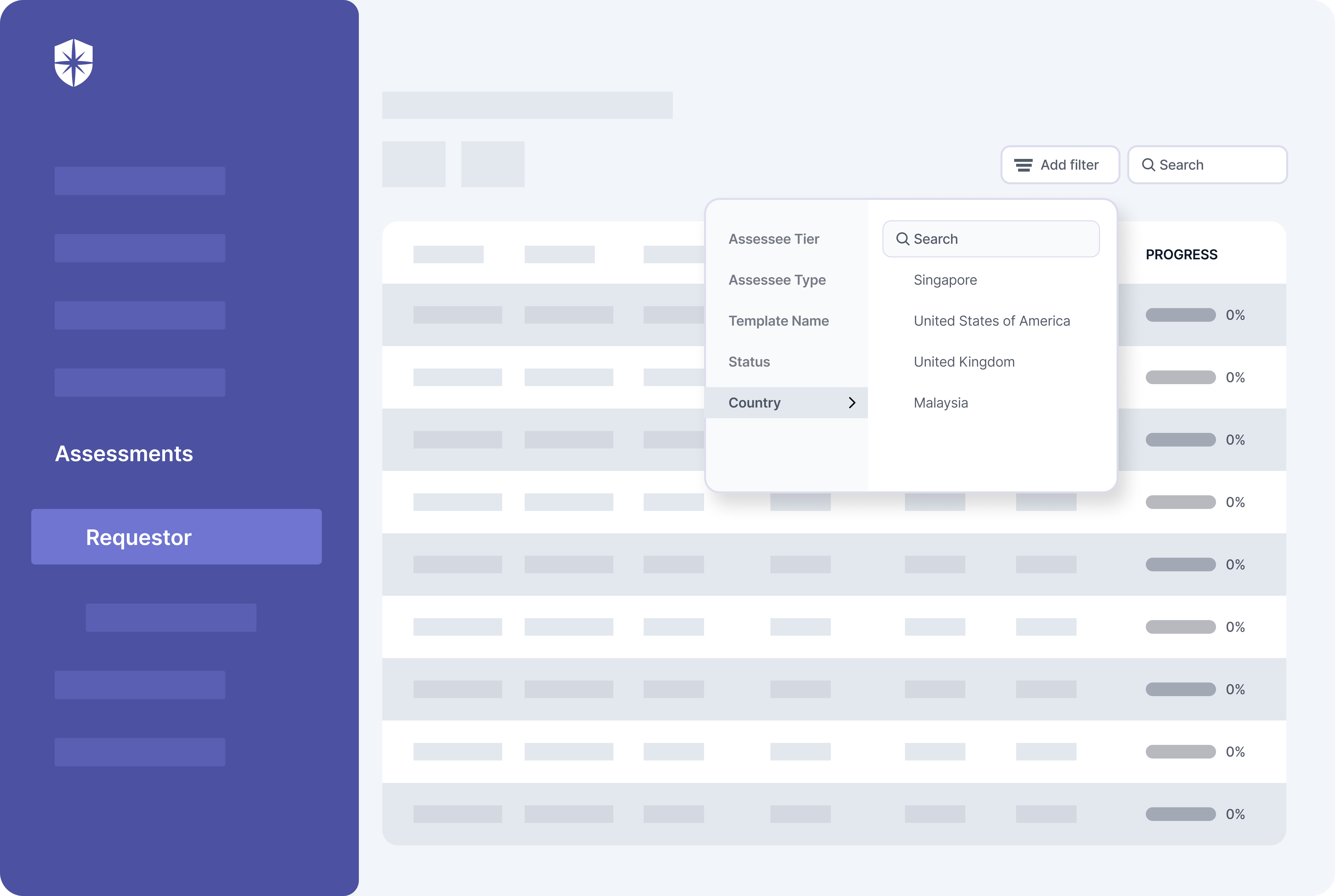
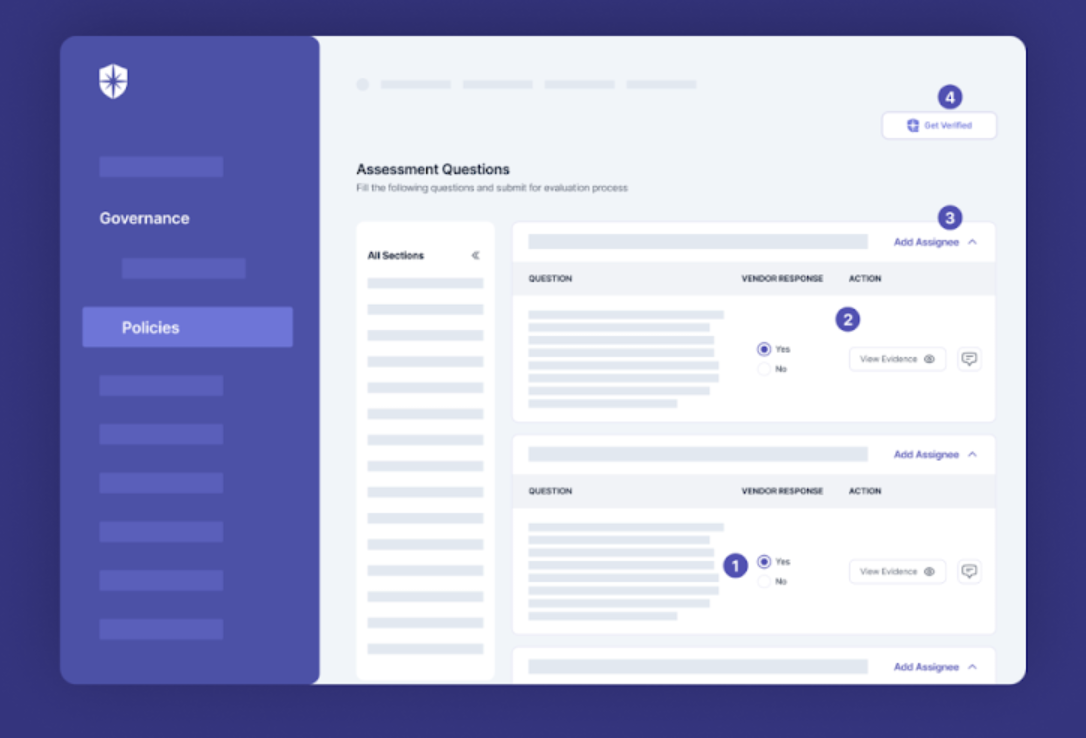
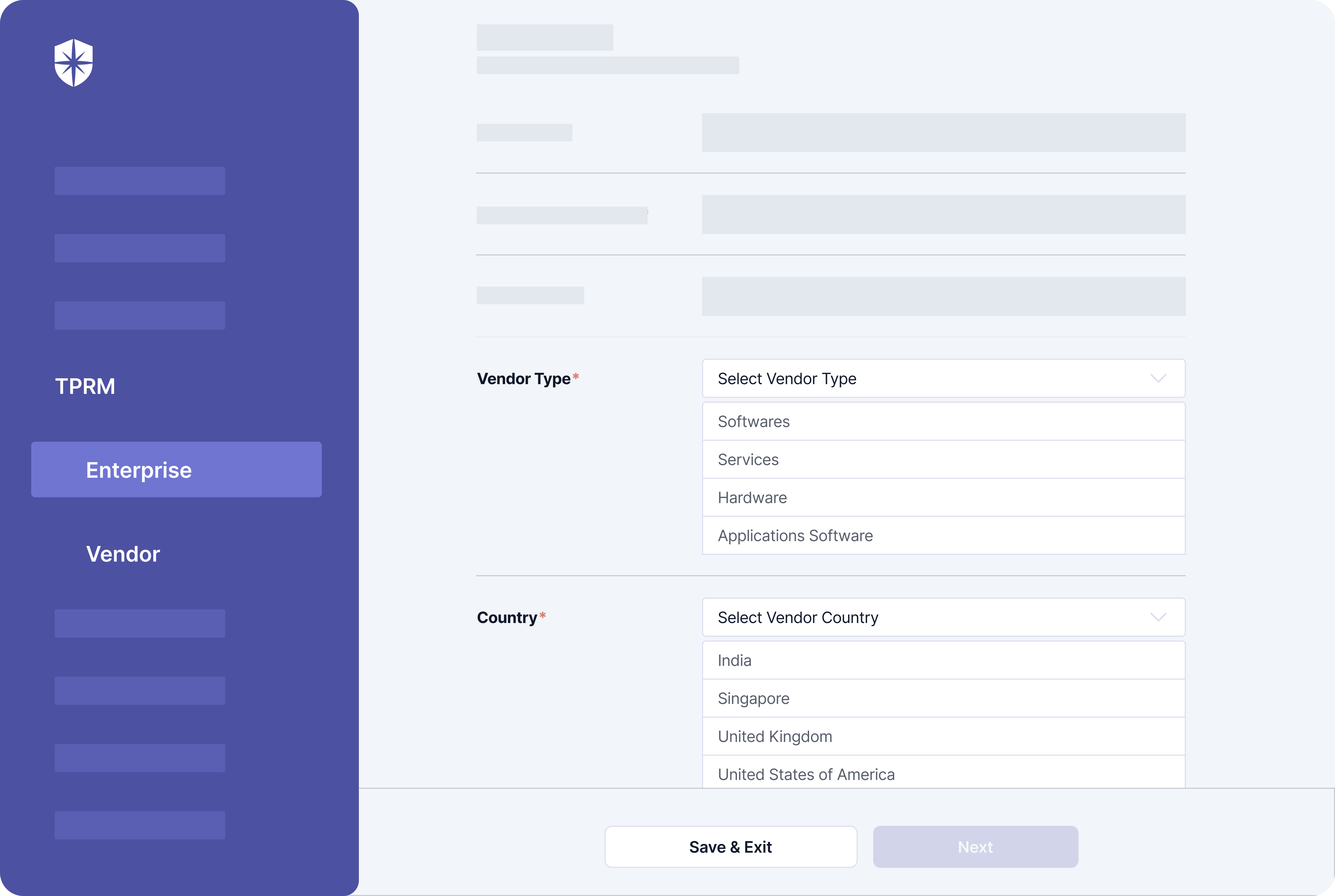
Assessee tier (basic or advanced) and possible threats to deal with often depends on a vendor type and their geographic location. To this end, Cyber Sierra enforces security teams to choose a vendor type, geographic location, and if an advanced assessment is needed when initiating each third-party risk assessment flow:

Due Diligence
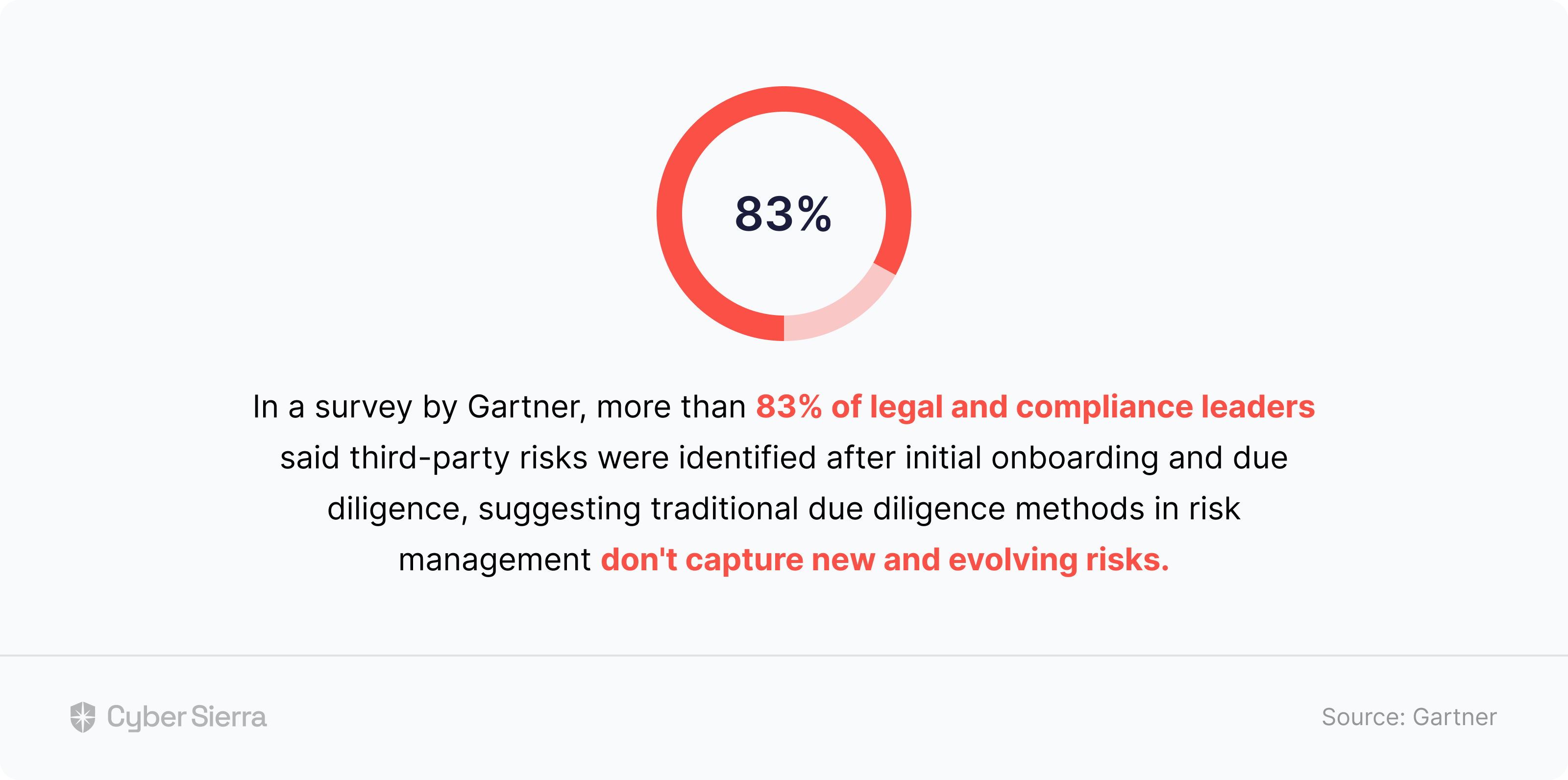
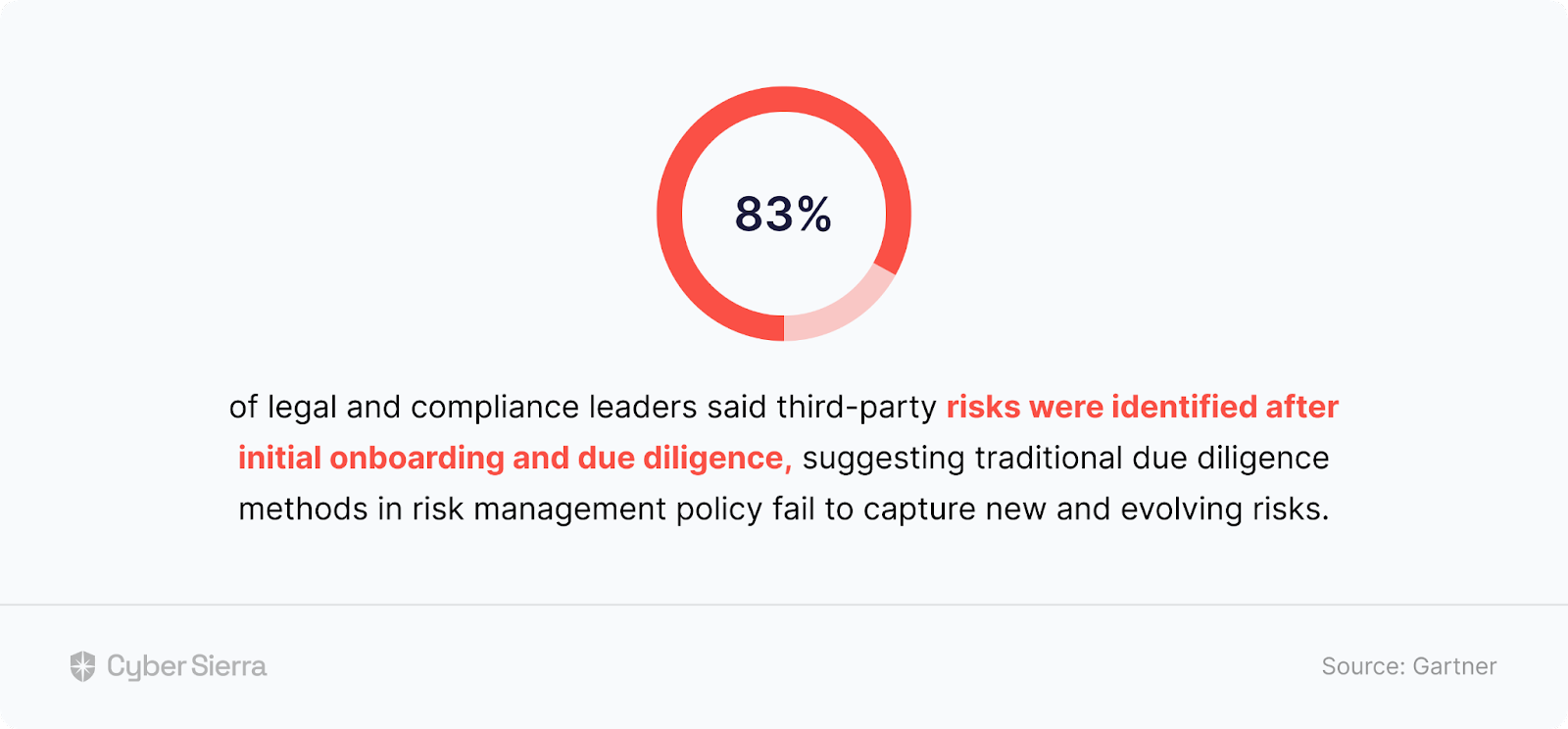
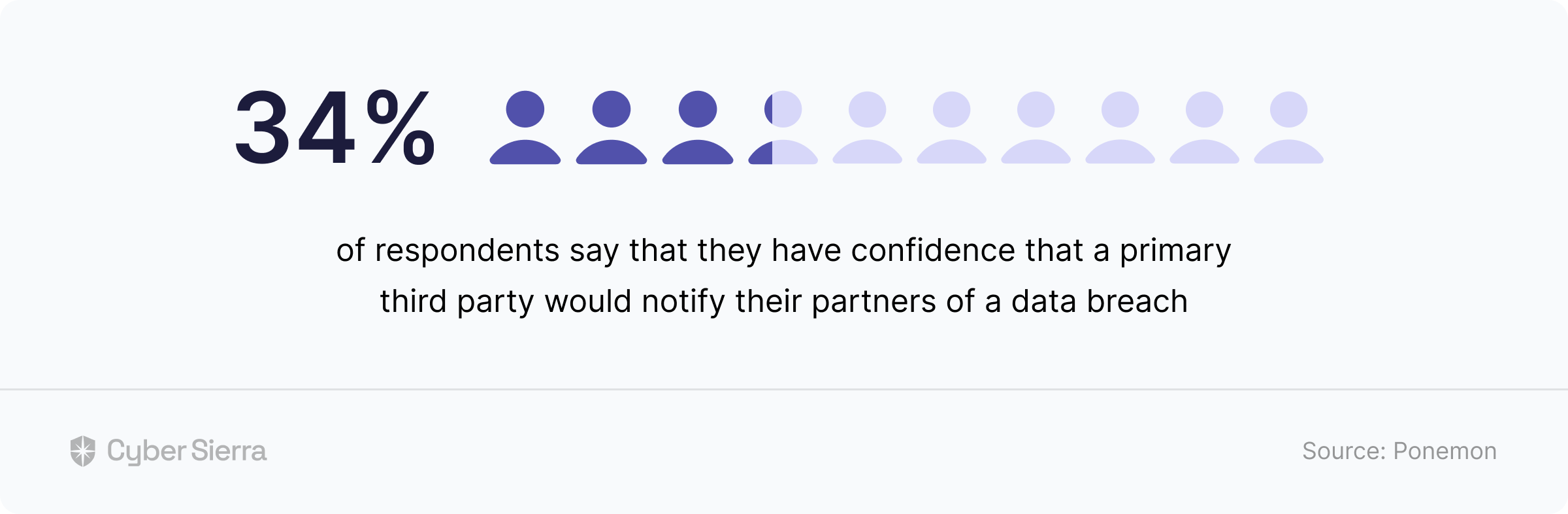
A study by the Ponemon Institute revealed why due diligence is a core component of an effective-implemented TPRM framework.
They found that:
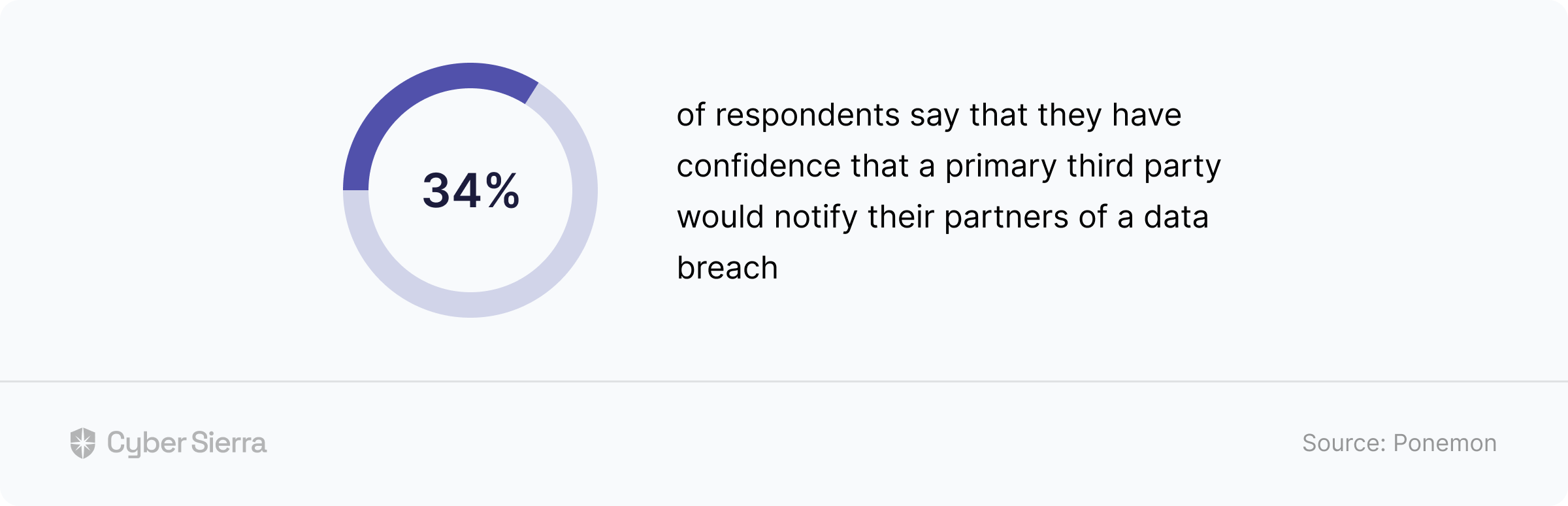

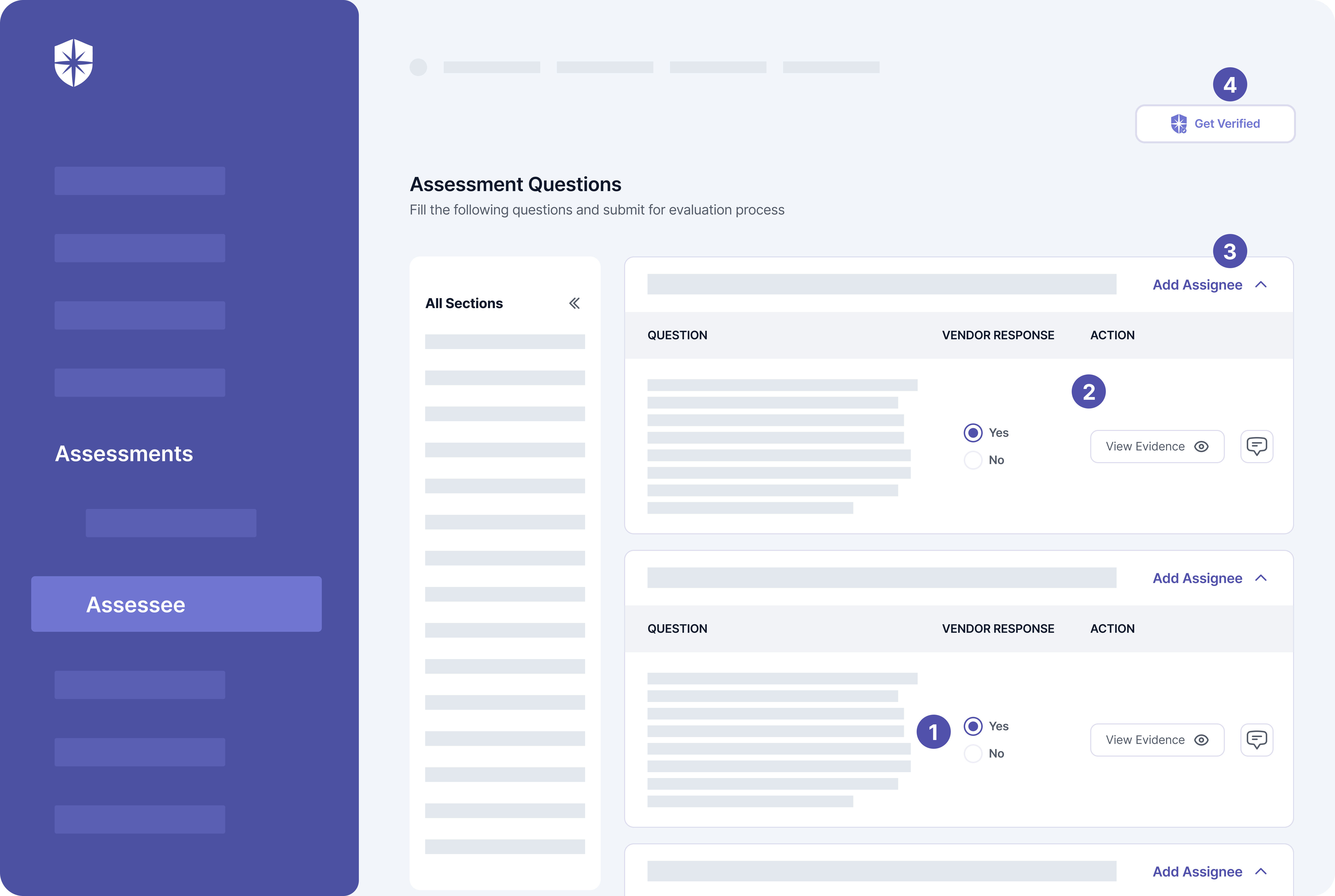
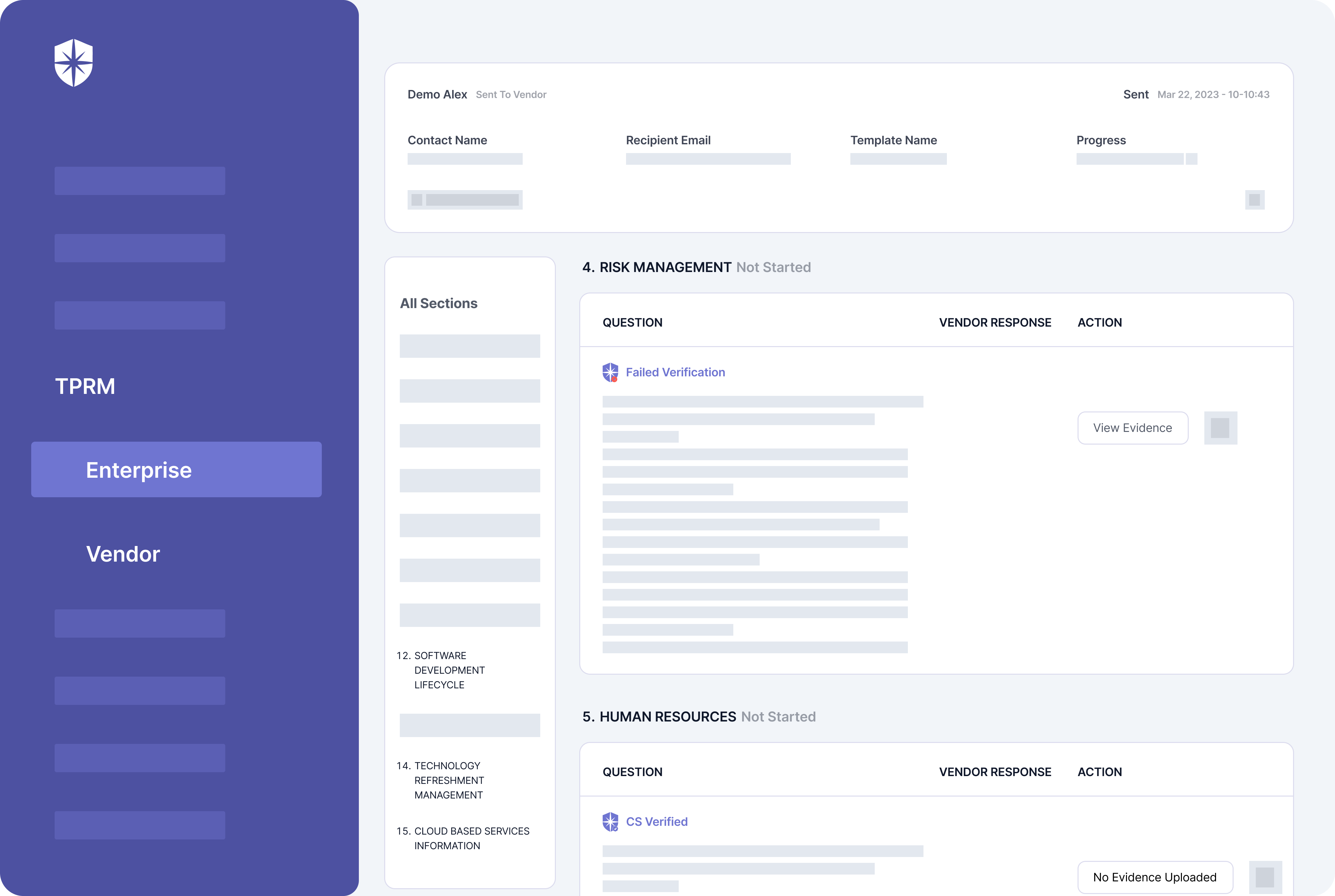
In other words, don’t expect 3rd parties to be honest about responses to risk assessments on their threat profiles. Instead, use a TPRM platform like Cyber Sierra to auto-verify and automate due diligence on evidence uploaded for each security assessment question:
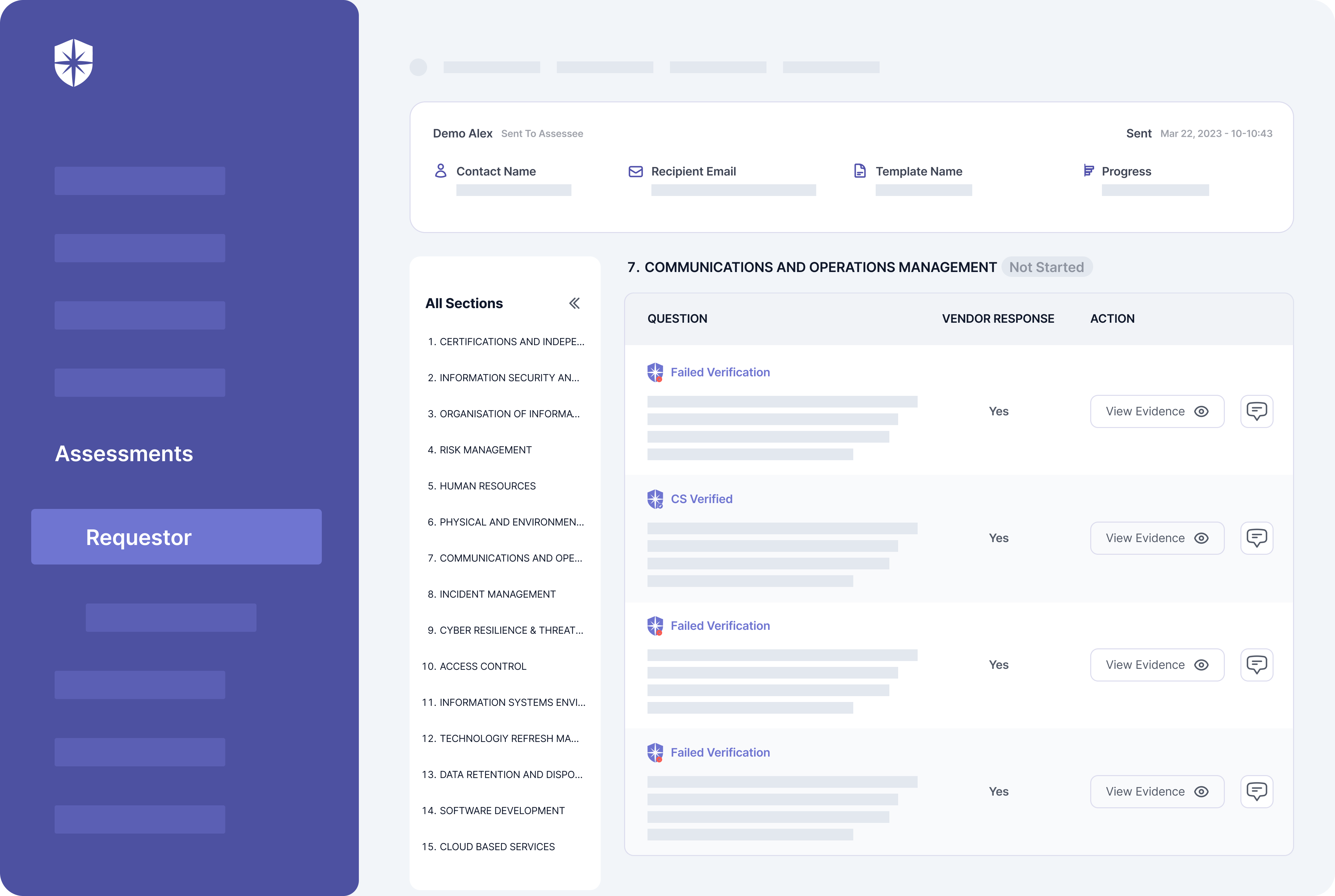

Contractual Agreements
This component of implementing a TPRM framework requires working with trained legal and compliance professionals. Such expertise is needed for designing custom contractual agreements that effectively outline each 3rd party’s security obligations, requirements, and expectations relative to risk management.
Incidence Response
How will your security team respond to cyber risks and security threats that emerge from vendors in your supply chain network?
This element of an implemented TPRM framework addresses that crucial question. It involves establishing proactive measures for remediating data threats and cyber risks arising from 3rd party vendors in your entire supply chain network.
But to respond to incidents, your security teams must first identify them before they lead to a data breach. This requires proper implementation of the fifth element of a TPRM framework.
Continuous Monitoring
This element of a TPRM framework entails:
- Monitoring third-party security controls based on implemented risk management, governance, and compliance policies.
- Verifying third-parties’ uploaded evidence of meeting their obligation of having required risk management controls.
- Identifying and flagging vendors in your supply chain network without that fail to meet data security requirements.
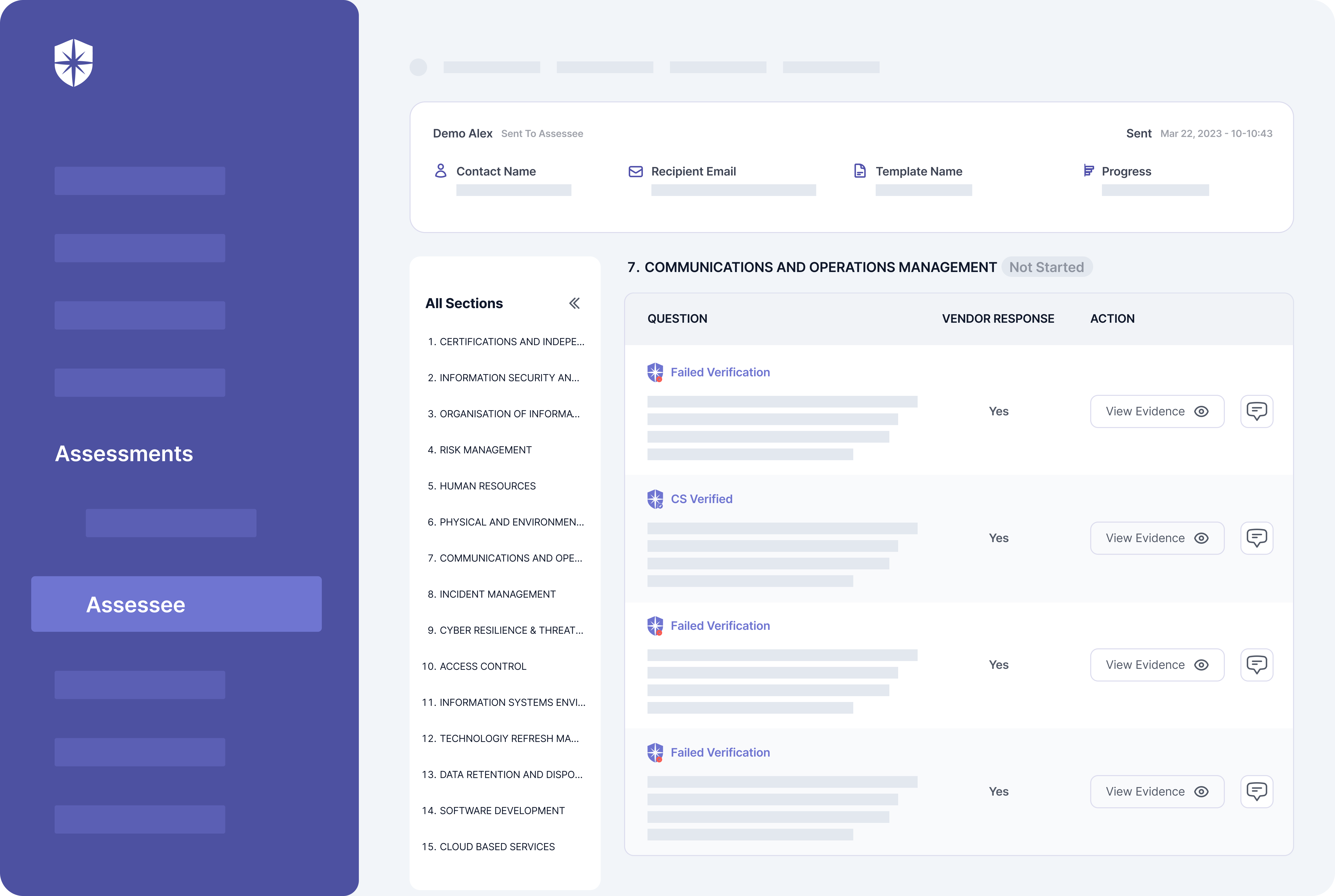
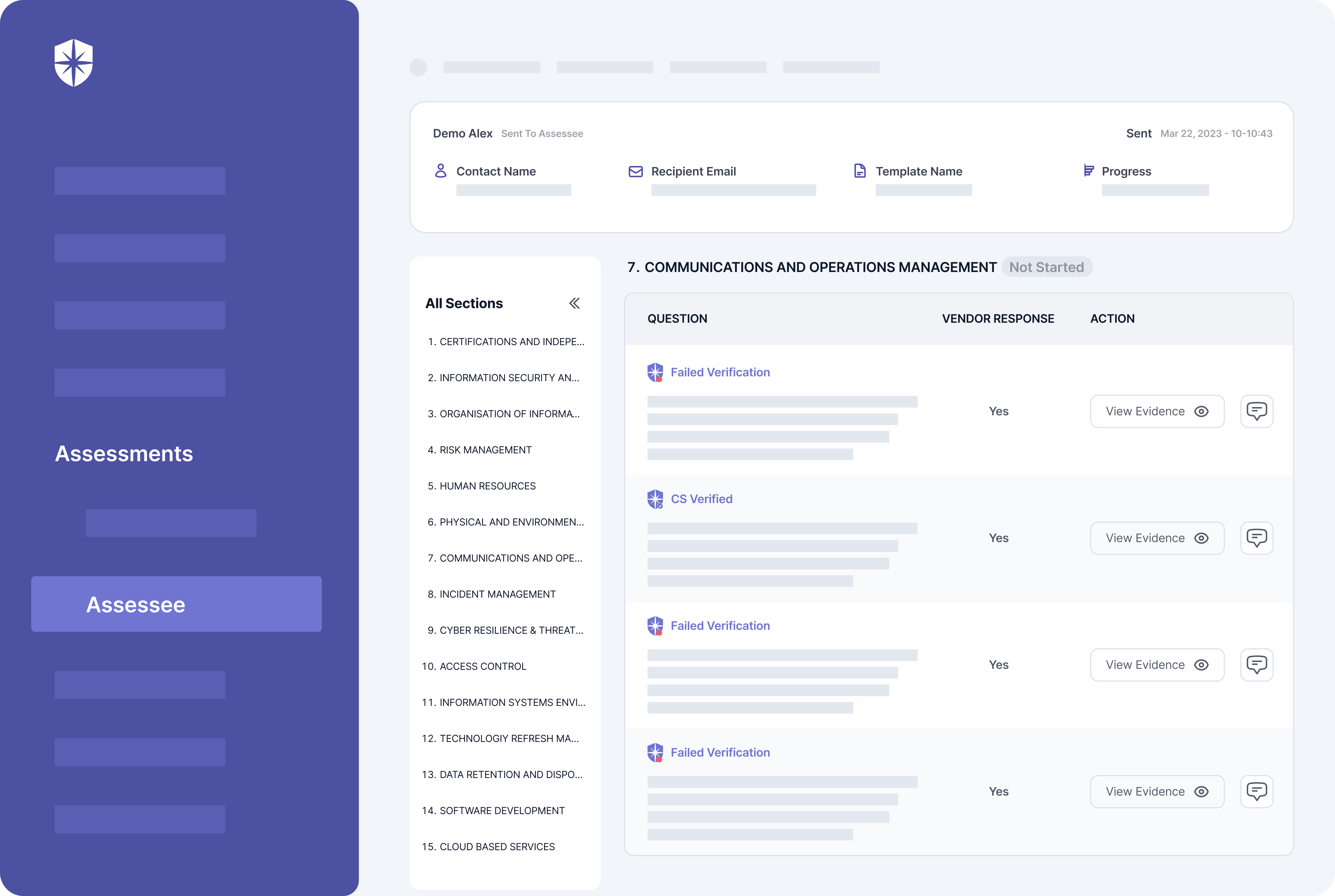
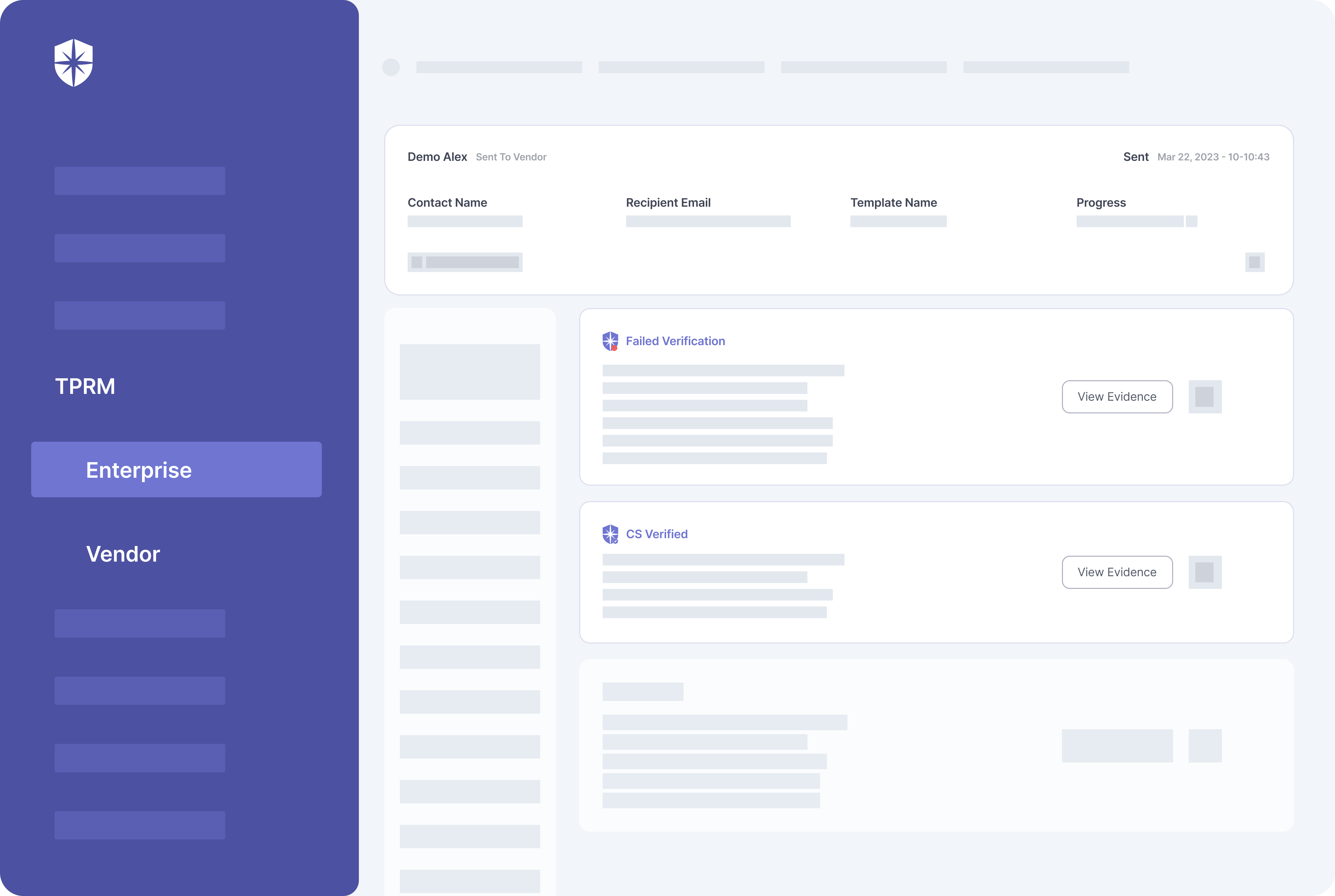
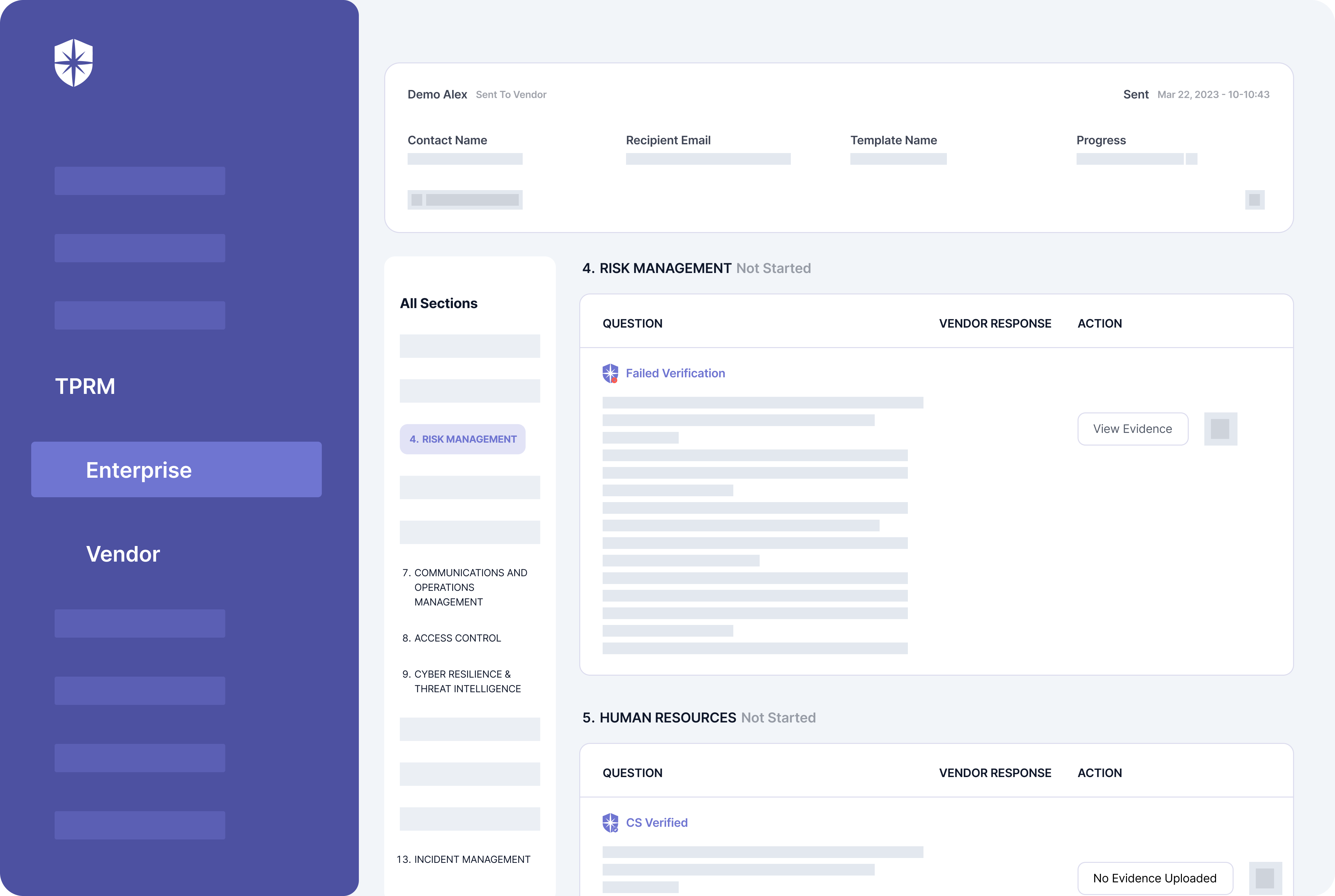
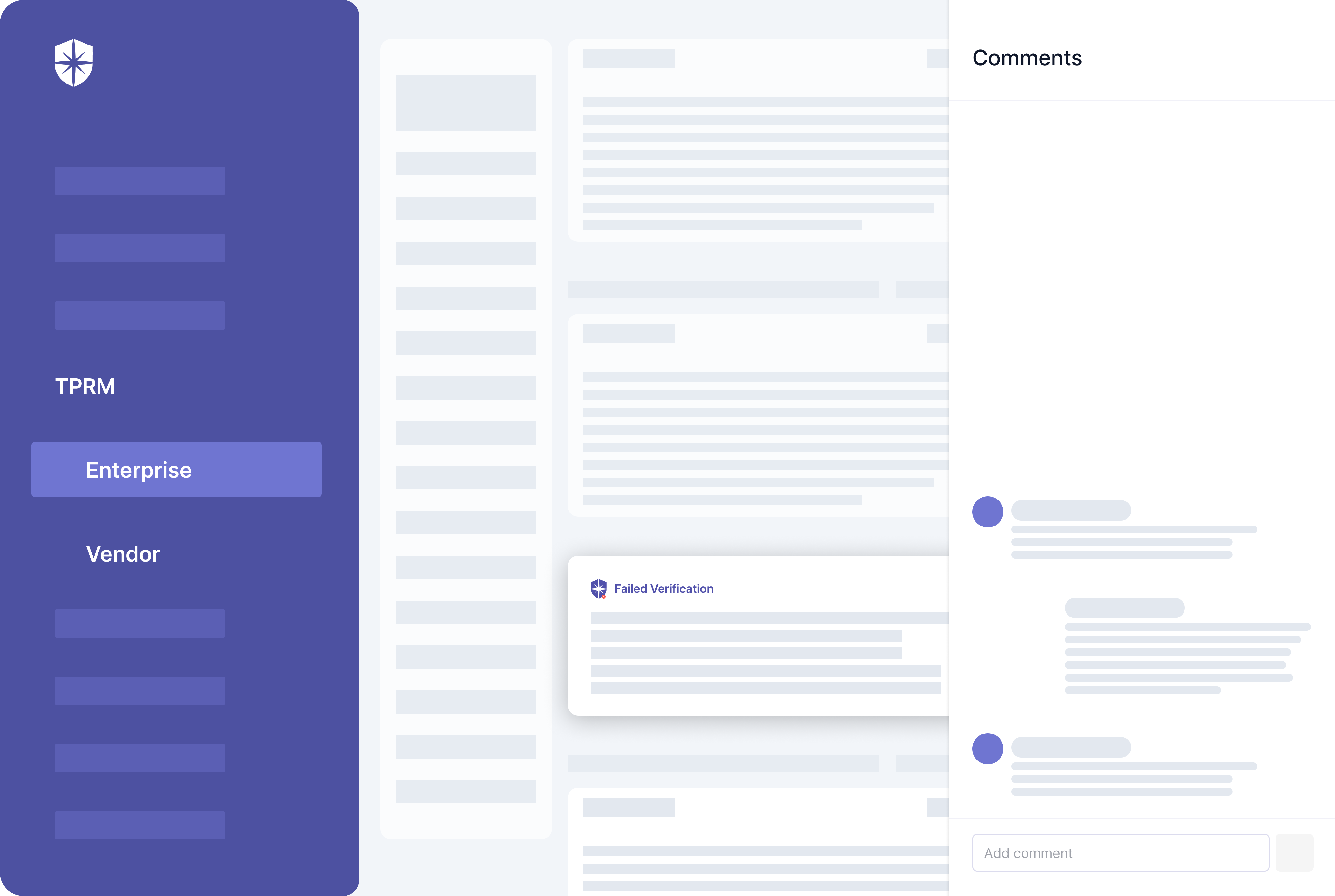
Cyber Sierra streamlines these gruesome processes for vendors and organizations. First, our platform enforces ongoing third-party risk monitoring by auto-verifying 3rd parties’ uploaded evidence of having required security controls.
You can enforce this by asking vendors managed with the Cyber Sierra platform to click on “Get Verified,” say, monthly:


On your team’s dashboard view, our platform automatically verifies vendors’ uploaded evidence of having mandated security controls.
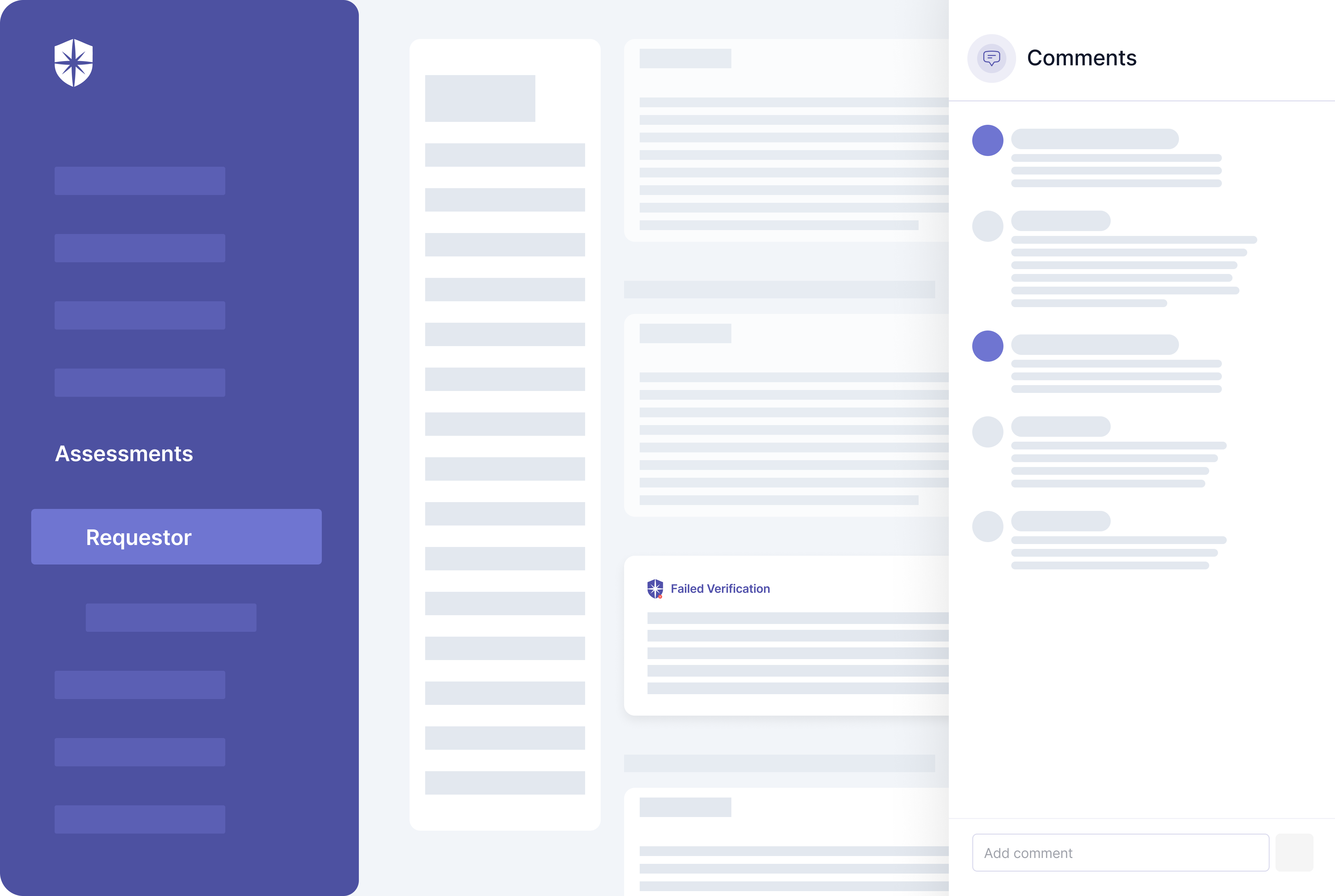
It also flags evidence that fails verification and your team can work with vendors to resolve them on the same pane:

Implement TPRM Frameworks In One Place
As demonstrated in the steps above, you can implement critical elements of an enterprise vendor risk management program with Cyber Sierra. More importantly, our platform lets you choose between the NIST or ISO TPRM frameworks:



This means whichever recommended framework makes more sense for assessing and managing third-party vendor risks in your supply chain, you can do it with our platform without jumping loops.
You can even use both for specific vendors.



















A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.