Top 10 Alternatives to AuditBoard in 2023























Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
Top 10 Alternatives to AuditBoard in 2023
Are you searching for a perfect compliance management tool capable of boosting your data protection and compliance handling methods?
AuditBoard, though a frequently adopted choice in the business sphere for compliance issues, may not necessarily be the optimal match for every organization’s unique needs.
With a wide range of options available in the market, it is only natural that many businesses are still at a loss over the ideal compliance management solution for their business.
If you are one of those looking for an AuditBoard alternative with similar features but more benefits, here’s our list of 10 popular options to consider.
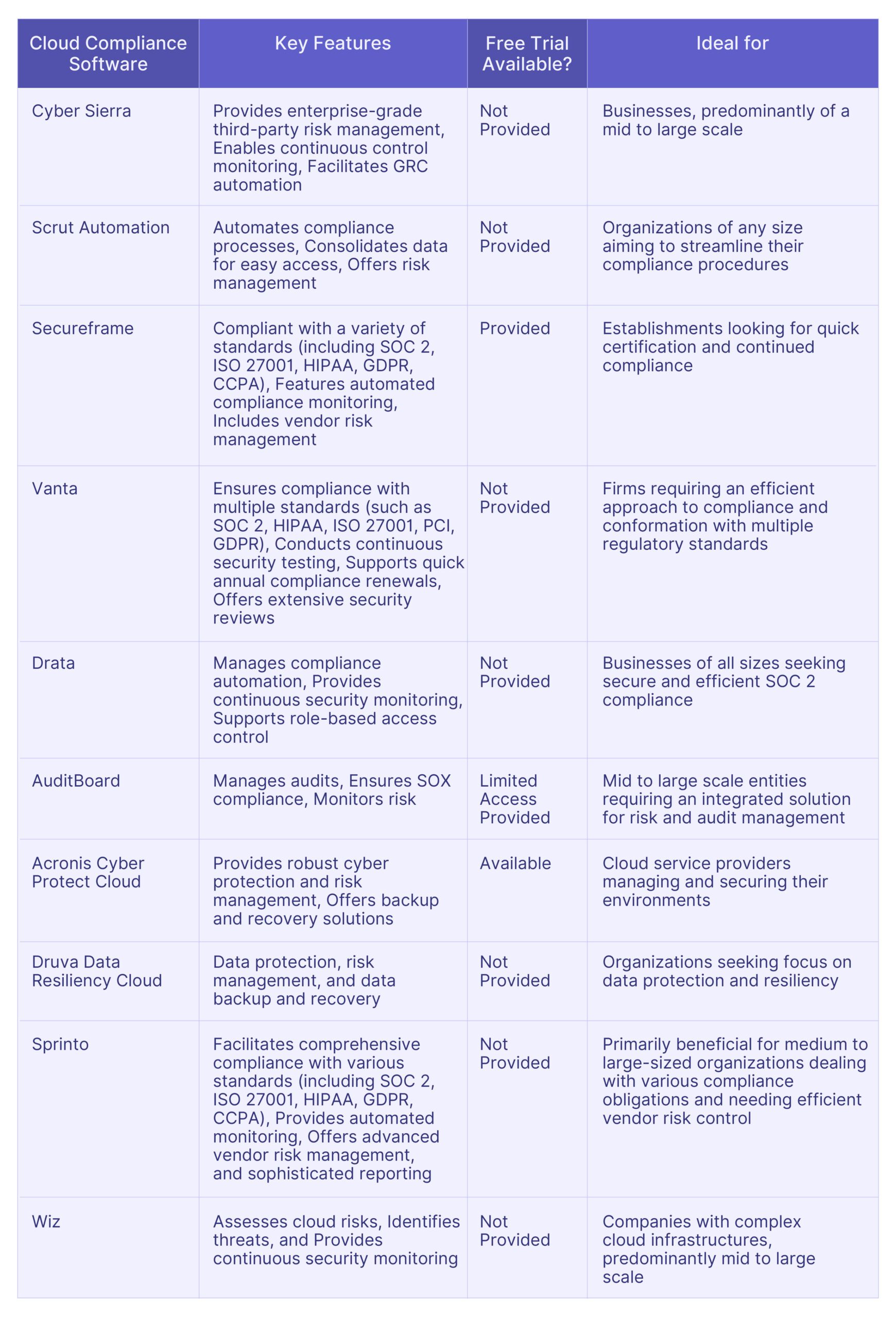
Top 10 AuditBoard Alternatives: Key Features, Pricing Plans, and More
Here are the top 10 alternatives to AuditBoard that we have shortlisted for you:
- Cyber Sierra
- Vanta
- Scrut
- Drata
- Sprinto
- Secureframe
- Wiz
- Acronis Cyber Protect Cloud
- Druva Data Resiliency Cloud
- Duo Security
Let’s look at them one by one.
1. Cyber Sierra

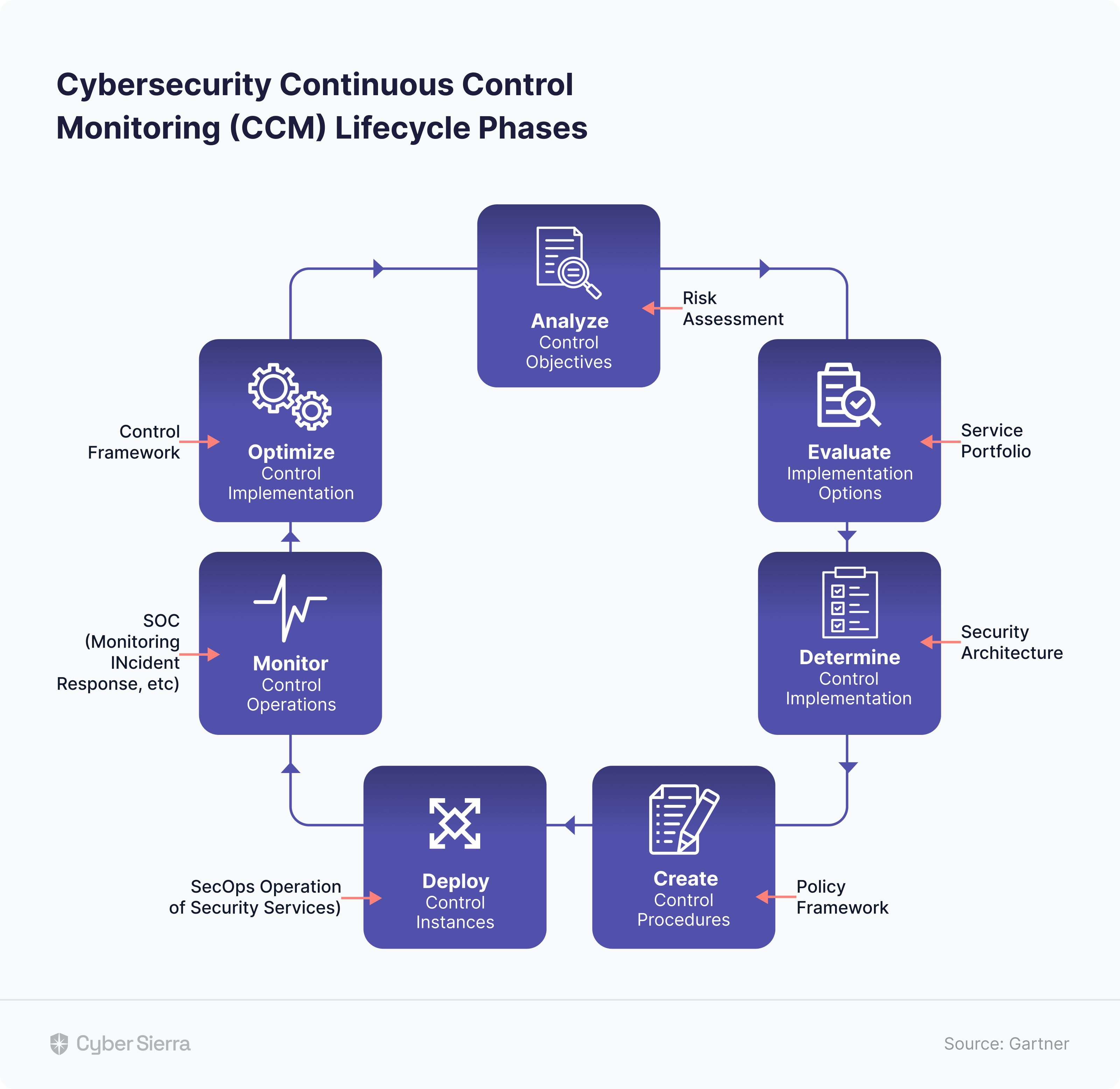
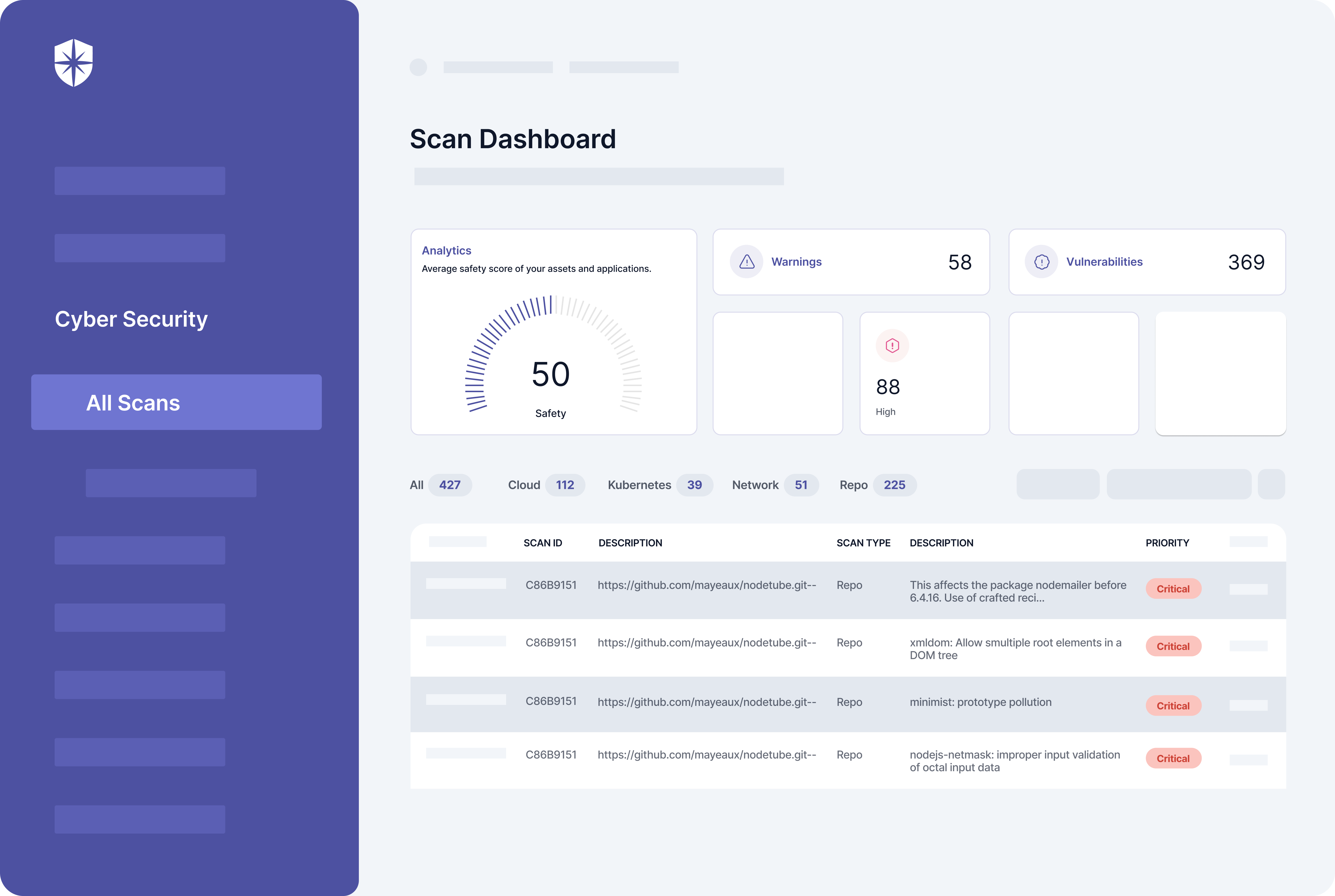
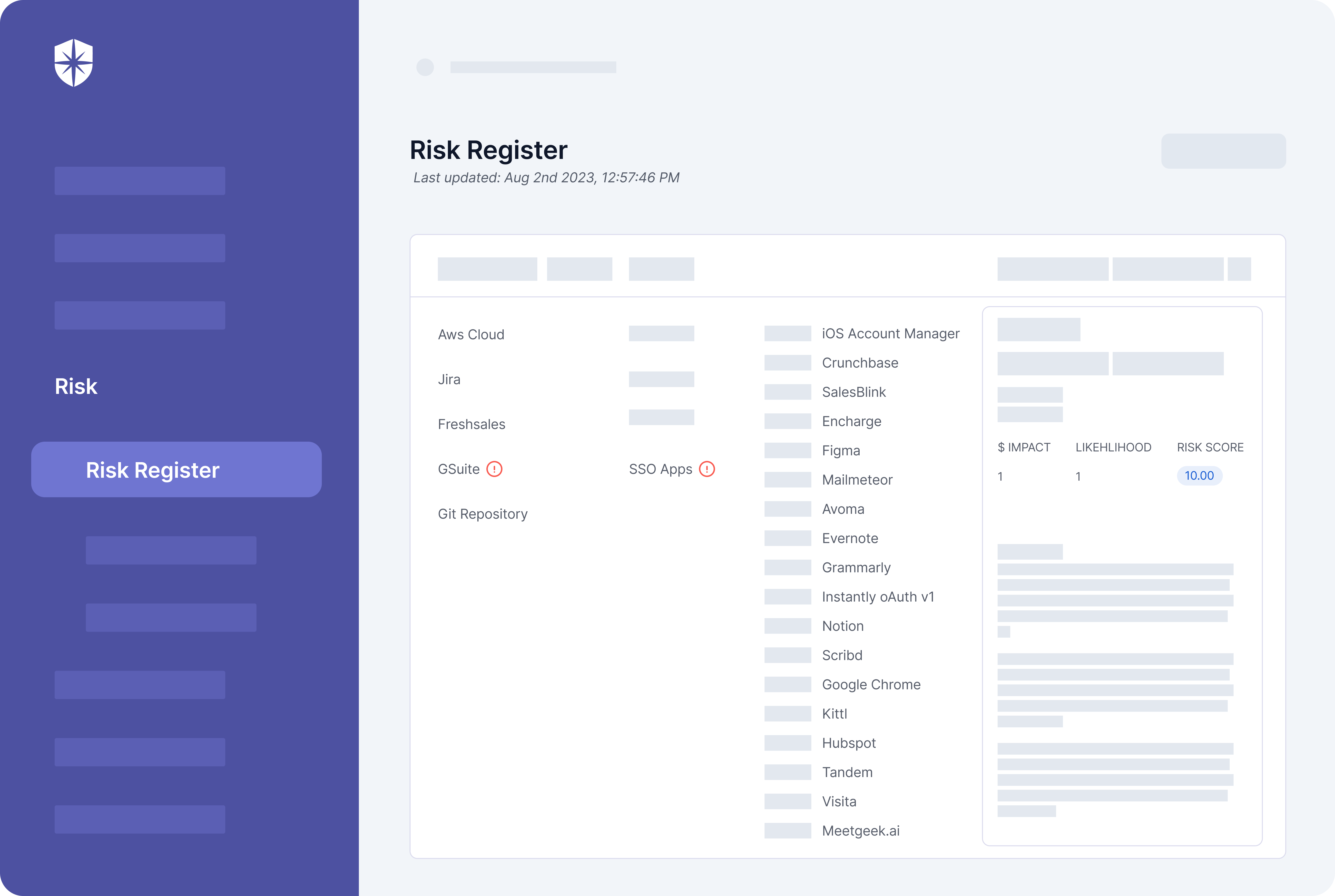
Cyber Sierra delivers a unique cybersecurity platform, developed to focus on the needs of Chief Information Security Officers (CISOs), tech trailblazers, and others related to data safety.
What stands out about Cyber Sierra is its excellent integration of varied security elements, resulting in a comprehensive cybersecurity solution.
It consolidates governance, risk management, cybersecurity rules compliance, cyber insurance offerings, threat monitoring, and personnel training programs into a single, simplified platform, effectively minimizing the usual division often seen in managing cybersecurity.
Key Features
- Universal Control: Assists businesses in upholding compliance standards recognized globally – like ISO 27001, SOC 2, HIPAA, GDPR, and PDPA.
- Cybersecurity Health Audit: Manages detailed examination and detects threats associated with your digital presence.
- Staff Security Training: Furnishes a study course to teach employees how to identify and counteract phishing schemes.
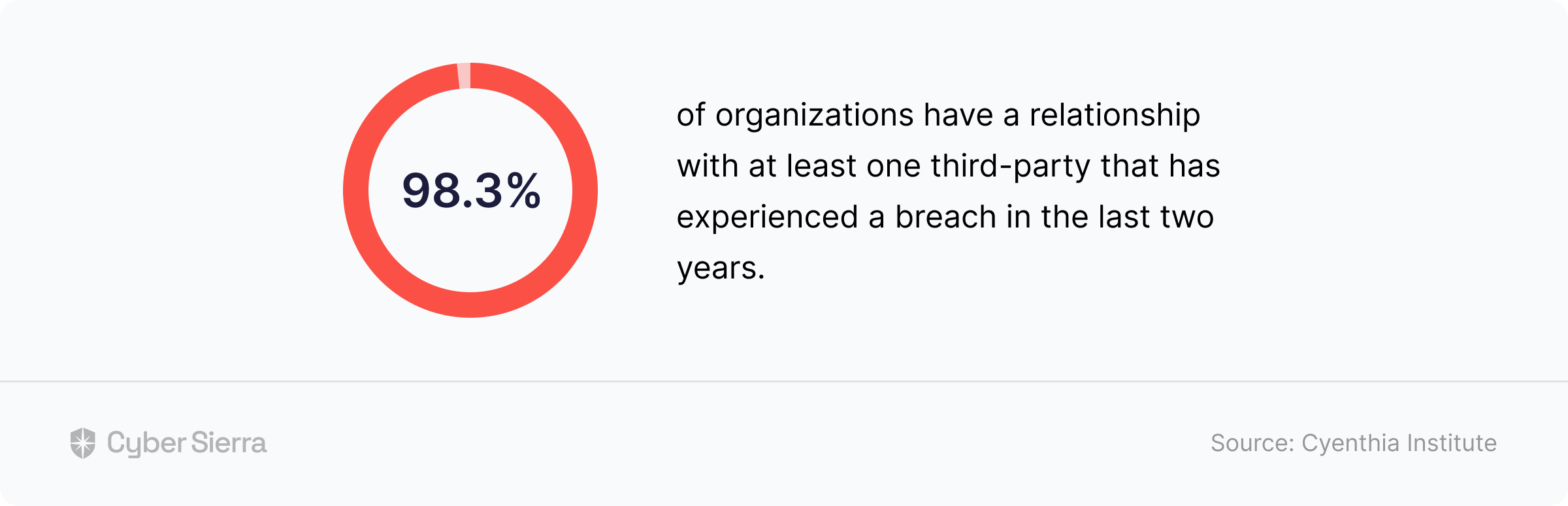
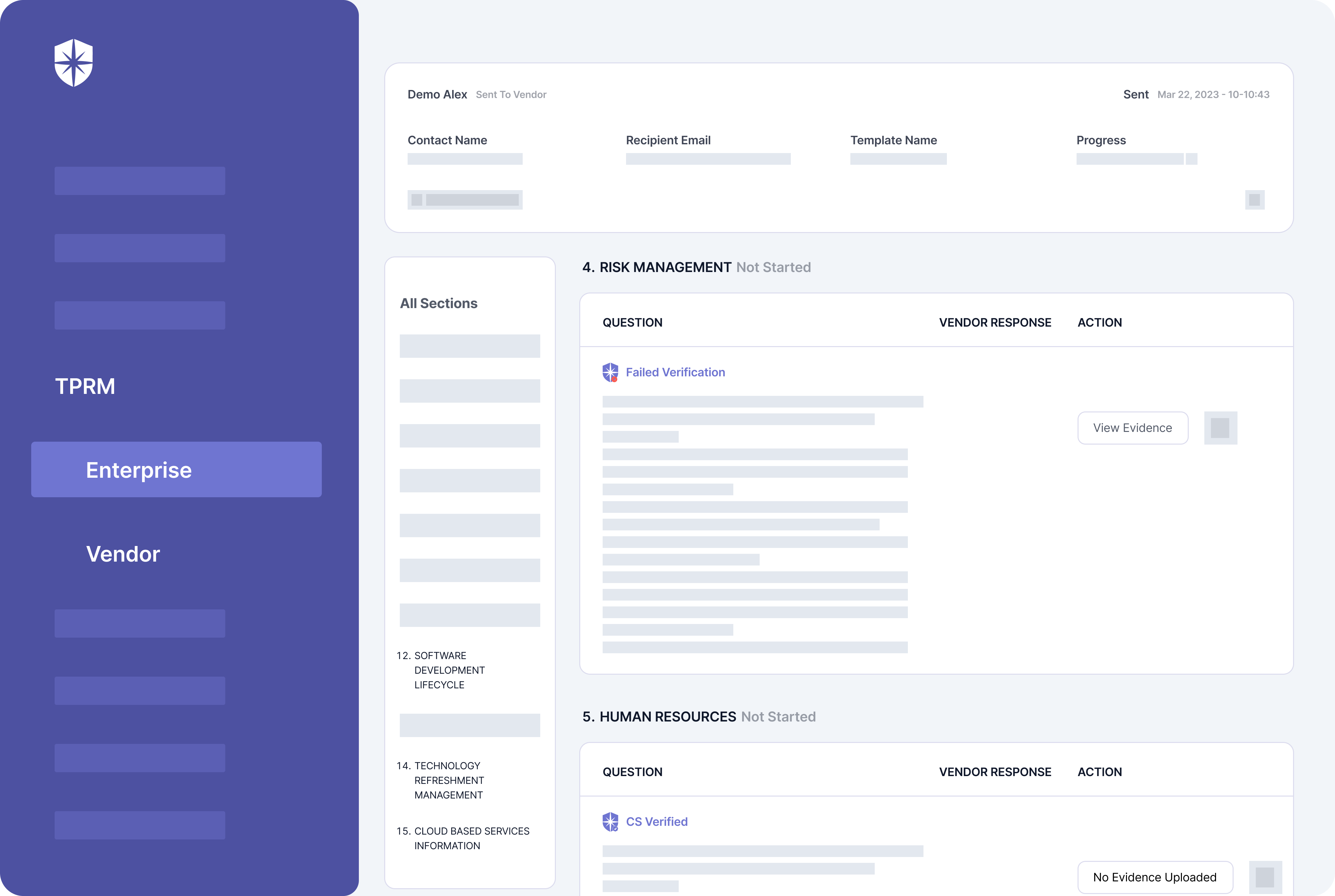
- Third-party risk management: Effortlessly handles the process of security clearance for partners and ensures consistent surveillance of possible risks.
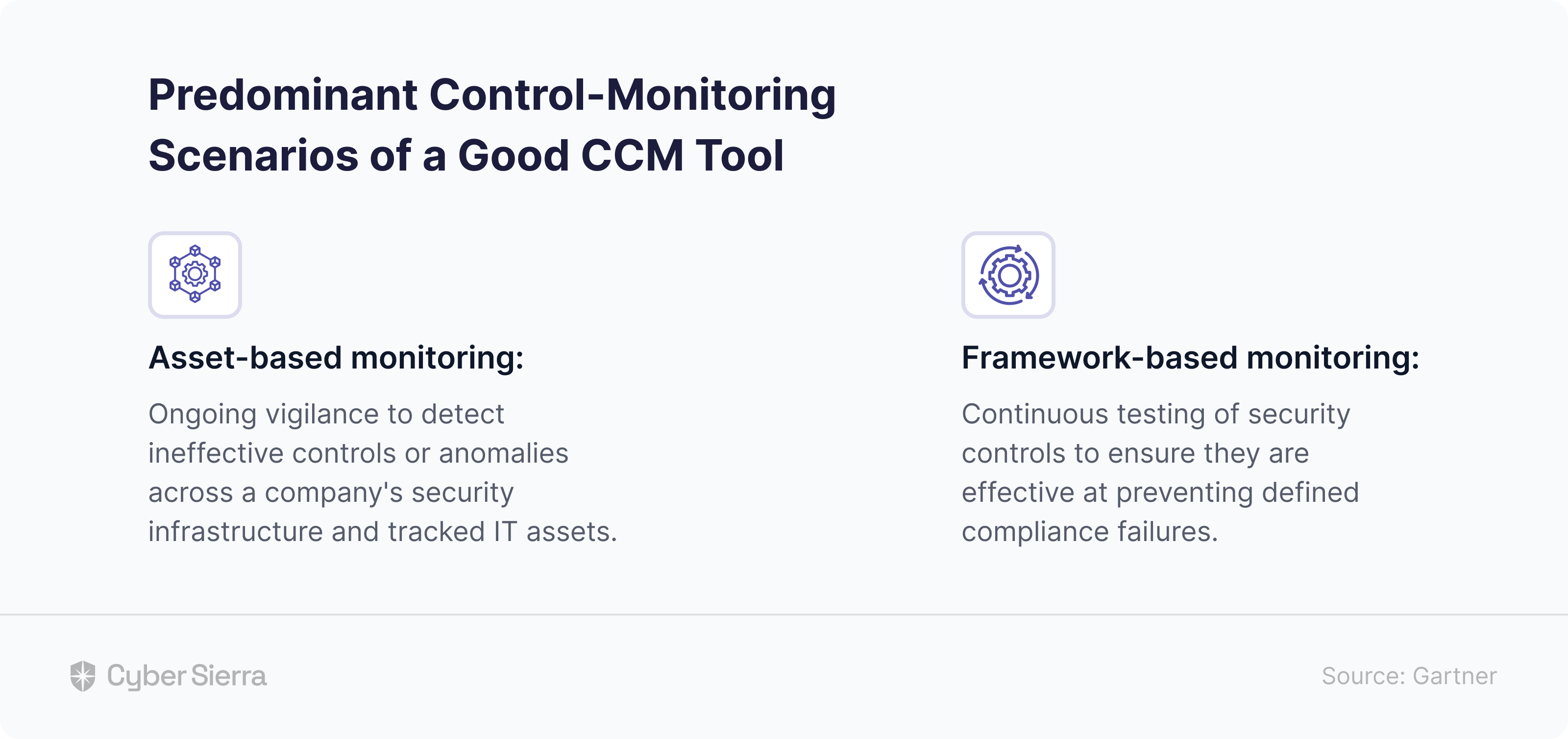
- Continuous controls monitoring: Monitors in near real-time the security controls, flagging off controls breaks and risk mitigation strategies.
Strengths
- Integrated Security Solution: Unites governance, risk management, cybersecurity compliance, cyber insurance offering, threat observation, and employee training modules onto a single platform.
- Constant Vigilance: Continuous risk management, threat prediction, and risk scoring.
- Third-party risk management: Makes handling third-party risks less complicated and brings down associated risks.
Weaknesses
- The platform is relatively new in the market.
Ideal For
Cyber Sierra is an excellent choice for both flourishing businesses and startups dealing with regulatory compliance, data safety, and related issues.
Moreover, it offers an advantage to businesses set to merge their cybersecurity, governance, and insurance strategies, shifting from several vendors to a unified platform.
2. Vanta




Vanta is a specialized platform focusing on security and compliance management, zealously easing the pathway to SOC 2 compliance. It underscores the relevance of secure technology within a business, enabling the convenience of routine monitoring and automation of compliance procedures.
Key Features
- Continuous Monitoring: Vanta’s continuous security monitoring ensures constant compliance, enabling firms to stay current and secure continuously.
- Automation: To optimize the SOC 2 certification procedure, Vanta automates compliance activities, thereby simplifying workflows and minimizing the need for manual work.
- Integration: It allows for easy integration with popular services and platforms, including AWS, GCP, and Azure. This assortment of integration choices fosters adaptability to variable tech situations.
Strengths
- Time Efficiency: Vanta effectively curtails the duration and human effort required to meet SOC 2 compliance, offering companies much-needed resource savings.
- Integration: Its ability to integrate with various established platforms enhances its adaptability to different technological environments.
Weaknesses
Limited Scope: As Vanta specializes in SOC 2 compliance, it might not cater to other security frameworks or standards necessary for some businesses.
Customization: With restricted customization options, Vanta might not offer sufficient flexibility for businesses with unique compliance requirements.
Ideal For:
Vanta is an excellent fit for mid-scale to large businesses, notably those operating in sectors demanding stringent security compliance standards, such as tech, healthcare, or finance. Compliance with rigorous security standards like SOC 2, ISO 27001, HIPAA, PCI, and GDPR is inevitable in these sectors.
3. Scrut Automation






A dedicated cloud security solution for automating cloud configuration testing, Scrut Automation provides potent cloud-native protection layers for AWS, Azure, GCP, and other platforms.
Key features
- Automated cloud configurations testing: Constantly verifying cloud configurations against 150+ CIS benchmarks, Scrut Automation ensures compliance.
- Historical records: A history of your security state helps track improvement over time, providing valuable insights.
- Integration: Enjoy seamless integration with major cloud platforms like AWS, Azure, and Google Cloud.
Strengths
- In-depth security coverage: Over 150 CIS benchmarks are employed to guard your cloud environment effectively.
- Time-efficient: As it automates time-consuming tasks and ranks remediations, your information security progression speeds up.
Weaknesses
- Learning curve: Users new to cloud security configurations may require time to grasp and utilize certain functionalities.
- Limited customization: The platform has limited customization and personalization options, depending on specific user requirements.
Best for
Scrut Automation is ideal for organizations using cloud computing services from providers such as AWS, Azure, and GCP. Thanks to comprehensive security and compliance coverage, it serves large enterprises in need of dependable cloud security. Medium and small businesses looking for cloud security reinforcement via automation will also benefit significantly.
4. Drata






Drata acts as a security and compliance management platform that delivers all-encompassing support to companies endeavoring to achieve and maintain SOC 2 compliance. The platform’s audit management software automates the tracking, administration, and supervision of necessary technical and operational controls for SOC 2 certification.
Key Features
- Asset management: Drata allows organizations to detect and manage assets such as servers, devices, and applications for more effective control.
- Policy & procedure templates: Companies benefit from pre-built templates on the platform, enabling efficient generation of pertinent compliance documentation.
- User access reviews: Systematic user access assessments by Drata help maintain appropriate access controls.
- Security training: The platform grants continuous employee education and phishing simulations to elevate security threat awareness and best practices.
Strengths
- Automated evidence collection: Drata’s evidence collection process automation minimizes manual labor and chances of human error.
- Exceptional customer support: Its highly responsive and knowledgeable customer support team guides users throughout the compliance process.
Weaknesses
- Onboarding process: A longer and more complex onboarding process, as reported by users, may cause initial setup delays.
- Complex functionality: Drata’s wide range of functions could be challenging for non-technical users to comprehend.
- Scalability: Being a relatively recent market addition, Drata might face growth-related challenges when catering to larger organizations with intricate compliance needs.
- Pricing: Budget-constrained smaller businesses might find the pricing model of Drata a hindrance.\
Best For
Organizations looking to secure and preserve SOC 2 compliance while diminishing manual tasks can greatly benefit from Drata. Its sophisticated automation functions make it an appealing choice for businesses in pursuit of a more efficient audit process.
5. Sprinto






Sprinto functions as a security and compliance automation platform. It is designed to support businesses in maintaining compliance with notable frameworks such as SOC 2, ISO 27001, GDPR, HIPAA, and PCI-DSS. Its capacity for customization and real-time monitoring lets companies consistently scrutinize and manage their security and compliance state efficiently.
Key Features
- Asset Management: Sprinto’s security compliance tool allows businesses to aggregate risk, streamline entity-level controls, and run fully automated checks.
- Policy Implementation: The platform pronounces automated workflows, policy templates, and custom training modules for multiple security compliance needs.
- Exceptional Support: With Sprinto, businesses get guidance through every compliance process stage, from risk assessment to audit requirements fulfillment.
- Cloud Compatibility: Sprinto flawlessly integrates with a wide range of modern business cloud services, enabling exhaustive risk assessment and control mapping.
Strengths
- Automation: The automation offered by Sprinto notably reduces the effort and time needed to accomplish compliance.
- Broad Compliance Coverage: Sprinto caters to a wide range of compliance frameworks, empowering businesses to manage multiple compliances in tandem.
- Expert Support: From day one, Sprinto provides expert-guided support, guaranteeing that appropriate controls and practices are established.
- Integration Capability: The platform harmonizes effortlessly with many business cloud services, facilitating efficient control mapping and well-rounded risk evaluation.
Weaknesses
- Adaptive Requirements: To fully utilize the benefits of automated checks and continuous monitoring, businesses might need to first adapt to the Sprinto platform.
- Customer Support: A section of users suggest that Sprinto’s customer service could improve, especially concerning response times.
Best For
Sprinto is optimally suited for burgeoning cloud companies striving to simplify their security compliance processes.
Its advanced automation features and extensive compliance coverage positions it as a prime choice for companies in search of an efficient and hands-off method to uphold security compliance.
6. Secureframe






Secureframe is a compliance management platform that empowers businesses to simplify SOC 2 and ISO 27001 compliances. The platform emphasizes efficient, ongoing monitoring for several services, including AWS, GCP, and Azure.
Key features
- Continuous Compliance Monitoring: Facilitates ongoing compliance for a variety of services.
- Automation: Enhances security compliance tasks by minimizing the required time and resources.
- Integration Features: Interacts smoothly with widely-used cloud services like AWS, GCP, and Azure.
Strengths
- Efficiency in Time Saving: Drastically reduces the duration typically required for documenting and overseeing compliance that can span weeks.
- Integrated Approach: Works seamlessly with popular cloud services, providing potential advantages to companies utilizing these platforms.
Weaknesses
Inadequate Customization: According to some users’ feedback, Secureframe might benefit from more sophisticated customization options, indicating it may not provide the flexibility some businesses necessitate.
Best for
Secureframe is an optimal solution for businesses of all sizes aiming to simplify their SOC 2 and ISO 27001 compliances. It’s particularly beneficial for companies that rely on AWS, GCP, and Azure for their cloud services, thanks to its strengthened integration capabilities.
7. Wiz





Wiz is an advanced cloud security solution that grants businesses a comprehensive outlook on security risks throughout their entire cloud ecosystem. This innovative Cloud Security Posture Management (CSPM) tool surpasses agent-based approaches by scanning the full cloud stack to identify vulnerabilities, configuration mishaps, and latent dangers.
Key features
- Full Spectrum Visibility: Wiz delivers all-encompassing visibility for entire multi-cloud settings, presenting a unified look at security matters.
- Intelligent Risk Mitigation: Wiz pinpoints vulnerabilities and provides practical guidance to alleviate security hazards.
- Team Collaboration: Wiz encourages collaboration across DevOps, cloud infrastructure, and security teams via a singular platform.
- Real-Time Security Monitoring: Wiz examines cloud ecosystems continuously, detecting and alerting users of any security concerns or misconfigurations as they occur.
Strengths
- Thorough Security Review: Wiz conducts extensive security assessments involving all primary cloud platforms.
- Streamlined Automation: Users can implement effective security processes due to role automation and clear dashboards.
- Effortless Setup and Usage: Wiz is reportedly easy to execute, requiring minimal configuration prerequisites.
Weaknesses
- Inadequate Documentation: Some users have suggested that Wiz’s documentation could benefit from being more thorough and detailed.
- Unclear Pricing: A portion of reviewers remarked that pricing details are not readily available, posing challenges when estimating the cost of Wiz’s deployment.
- Excessive Notifications: As Wiz actively monitors cloud conditions, a few users may perceive the notifications as excessive.
Best for
Wiz is optimal for businesses operating within multi-cloud contexts that value a detailed, all-encompassing perspective of their cloud security posture. Those with complex cloud infrastructures will appreciate Wiz’s aptitude for rendering a harmonized security view.
8. Acronis Cyber Protect Cloud



Acronis Cyber Protect Cloud is a sweeping cybersecurity suite that consolidates backup, disaster recovery, AI-driven malware and ransomware defense, remote aid, and security in a unified system. It aims to provide a well-rounded approach to safeguarding data across an array of devices and settings.
Key Features
- Backup and disaster recovery: Acronis secures data by offering dependable backup options and disaster recovery tools in the event of severe setbacks.
- Cyber security: Employs AI-and machine learning-powered techniques to detect and tackle new menaces.
- Patch management: Assesses and automatically upgrades outdated software versions to mitigate risks posed by vulnerabilities.
- Remote assistance: Features remote support, enabling users and administrators to swiftly resolve issues from any point.
Strengths
- Holistic Protection: Furnishes multi-layered security by melding backup, disaster recovery, and security provisions.
- Easy to Navigate: The platform receives praise for its straightforward, easy-to-use interface.
- Trustworthy Backup and Recovery: Users express satisfaction with Acronis’ performance regarding data backup and restoration.
Weaknesses
- Potential Performance Constraints: A few users reported stuttering, particularly during resource-intensive backup operations.
- Support Team Challenges: Some customers experienced less-than-stellar service and delays when engaging with the support team.
- Inadequate Reporting: Some users pointed out that the reporting functionalities could offer more granular detail for deeper analysis.
Best for
Acronis Cyber Protect Cloud is particularly well-suited for businesses prioritizing solid, comprehensive cybersecurity postures. Given its all-encompassing nature, the solution proves valuable for firms in industries such as IT, retail, healthcare, finance, and any other field where data security is crucial.
9. Druva Data Resiliency Cloud




Druva Data Resiliency Cloud is a cloud-native data protection and management solution using a SaaS model. It offers robust backup, disaster recovery, and information governance across different environments, including endpoints, data centers, and cloud-specific applications.
Key Features
- Holistic Data Protection: Druva furnishes a solid, comprehensive backup and recovery solution for endpoints, data centers, SaaS applications.
- Disaster Recovery: It offers a time-efficient, cost-saving strategy for on-the-spot disaster recovery.
- Global Deduplication: With Druva’s deduplication feature, users can ensure effective storage and bandwidth usage, expediting backups, and curbing costs.
- Security and Compliance: The solution complies with a range of data protection regulations, including GDPR, with provisions for encryption, access control, and audit trails.
Strengths
- SaaS Model: As a SaaS-based offering, Druva is easy to roll out, maintain and scale, which minimizes stress on IT departments.
- Efficient Data Management: Druva presents a centralized interface for overseeing data protection tasks across various platforms, streamlining data management.
- Cost-Friendly: The elimination of hardware and infrastructure costs contributes to Druva’s cost-effectiveness.
- Customer Support: Druva’s customer support team scores high in responsiveness and usefulness.
Weaknesses
- Performance with Large Data Sets: It has been noted that the performance may dip when processing with large data sets.
- Pricing Structure: Users have pointed out that Druva’s pricing model could be more straightforward and clear.
Best for
Druva Data Resiliency Cloud is highly recommended for businesses of all sizes seeking a SaaS-based, cost-effective, user-friendly data protection service. It is especially useful for organizations managing distributed systems, including endpoints and various data center applications.
Companies with extensive data processing requirements might wish to explore other options or test Druva’s performance before making a long-term commitment.
10. Duo Security





Operating under the umbrella of Cisco, Duo Security is a cloud-oriented access security platform shielding users, data, and applications from potential security risks. It ascertains users’ identities and the condition of their devices prior to granting access to applications—a step that helps comply with business security protocols.
Key Features
- Two-factor Authentication (2FA): Extending beyond just the primary password, Duo strengthens the security framework by requiring an additional authentication form to access networks and applications.
- Device Trust: Through Duo, businesses can obtain a comprehensive understanding of each device accessing their applications, thereby ensuring adherence to security standards.
- Adaptive Authentication: It utilizes adaptive strategies and machine learning to enhance access security based on user behavior and device insights.
- Secure Single Sign-On (SSO): Users experience uninterrupted, secure access to all applications through the SSO feature provided by Duo.
Strengths
- Intuitive Use: Duo receives appreciation for its ease of use, easy deployment process, and an intuitive user interface.
- Robust Security Framework: The two-factor authentication feature by Duo significantly mitigates the likelihood of unauthorized access.
- Broad Integration Potential: Duo interfaces smoothly with a variety of existing VPNs, cloud-based applications, and other network infrastructures.
- Responsive Customer Support: Duo’s customer support is renowned for their prompt and efficient problem-solving.
Weaknesses
- Limited Customizability: Duo Security can be perceived lacking in granular control, especially for users needing specific controls or advanced customizability options.
- Software Updates: Some users reported potential hiccups or difficulties following software updates.
- Cost Considerations: For smaller businesses or startups, Duo’s pricing structure may appear to be on the steeper side.
- User Interface Improvements: Although user-friendly, some users have indicated that the interface could be more engrossing and modernized in its appeal.
Best for
Businesses with diverse software applications and device integrations will benefit significantly from Duo, thanks to its wide-ranging compatibility.
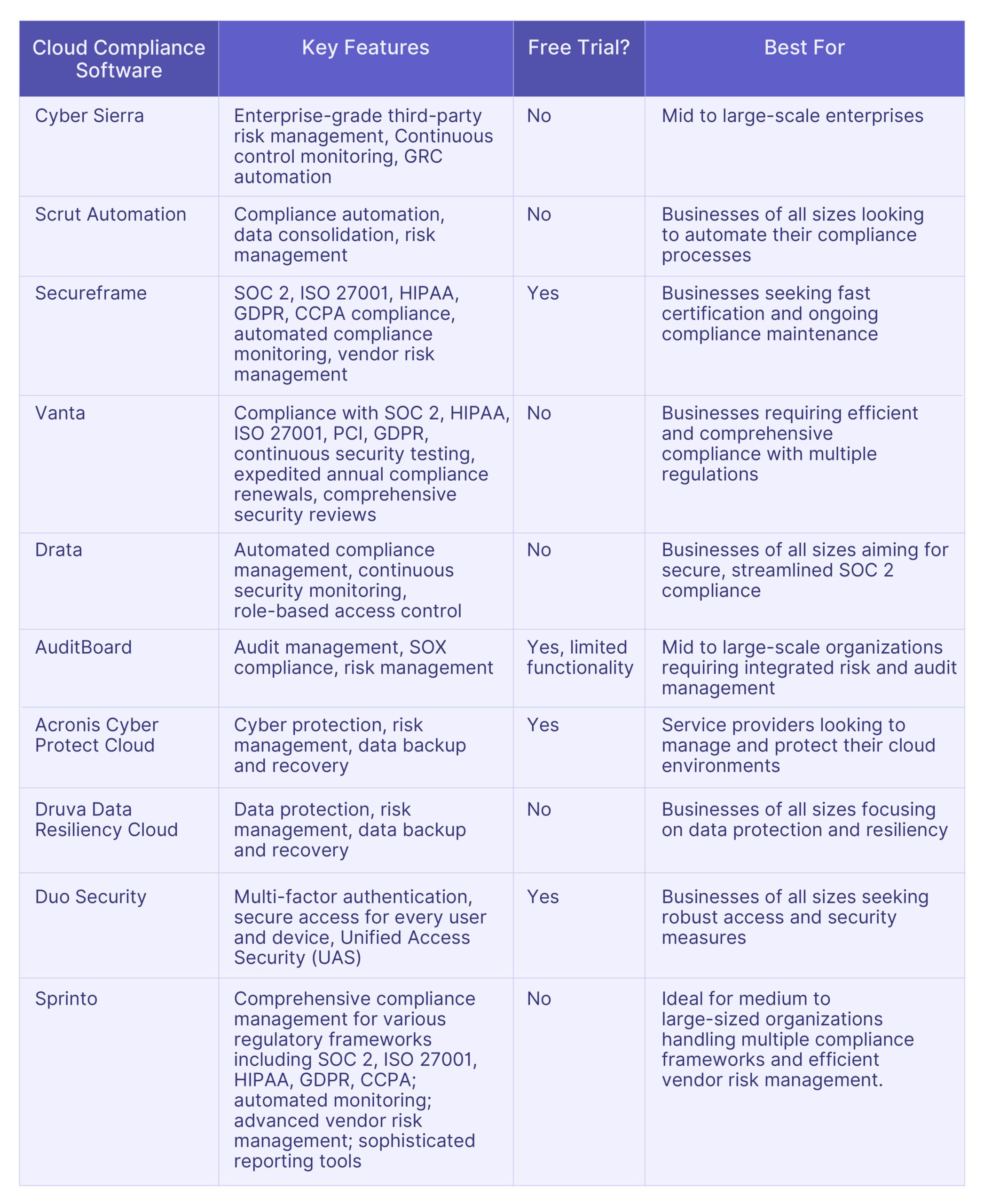
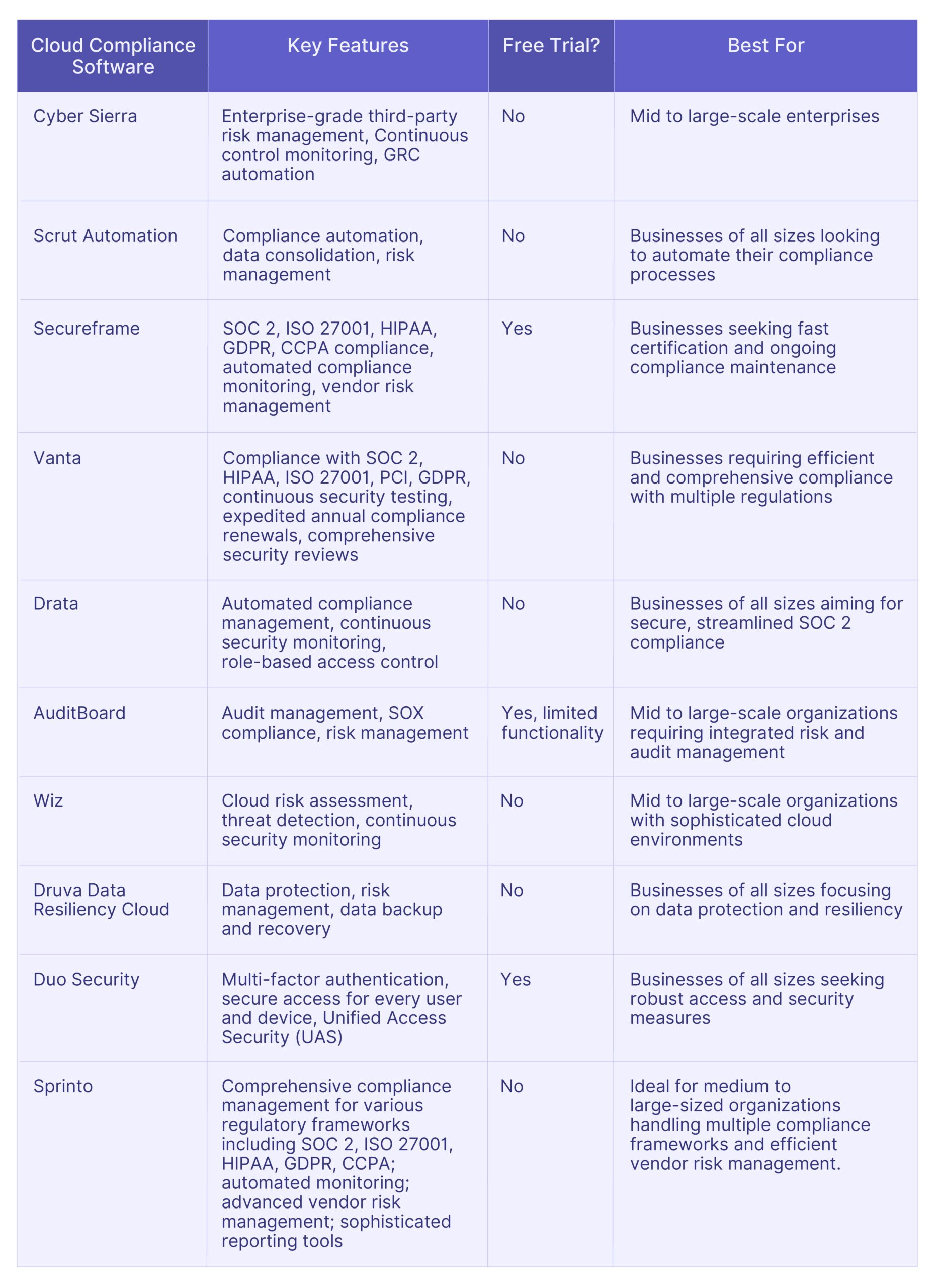
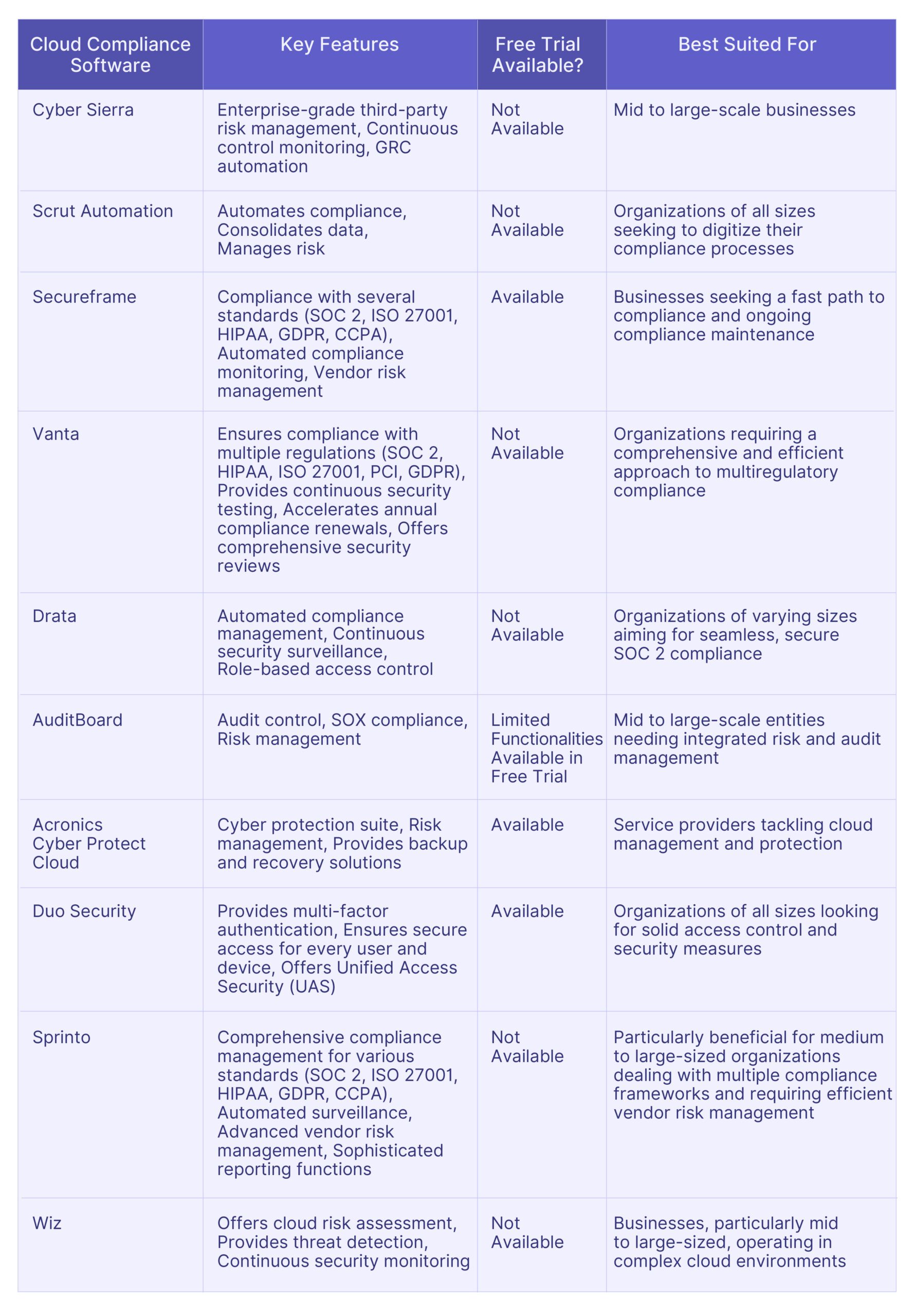
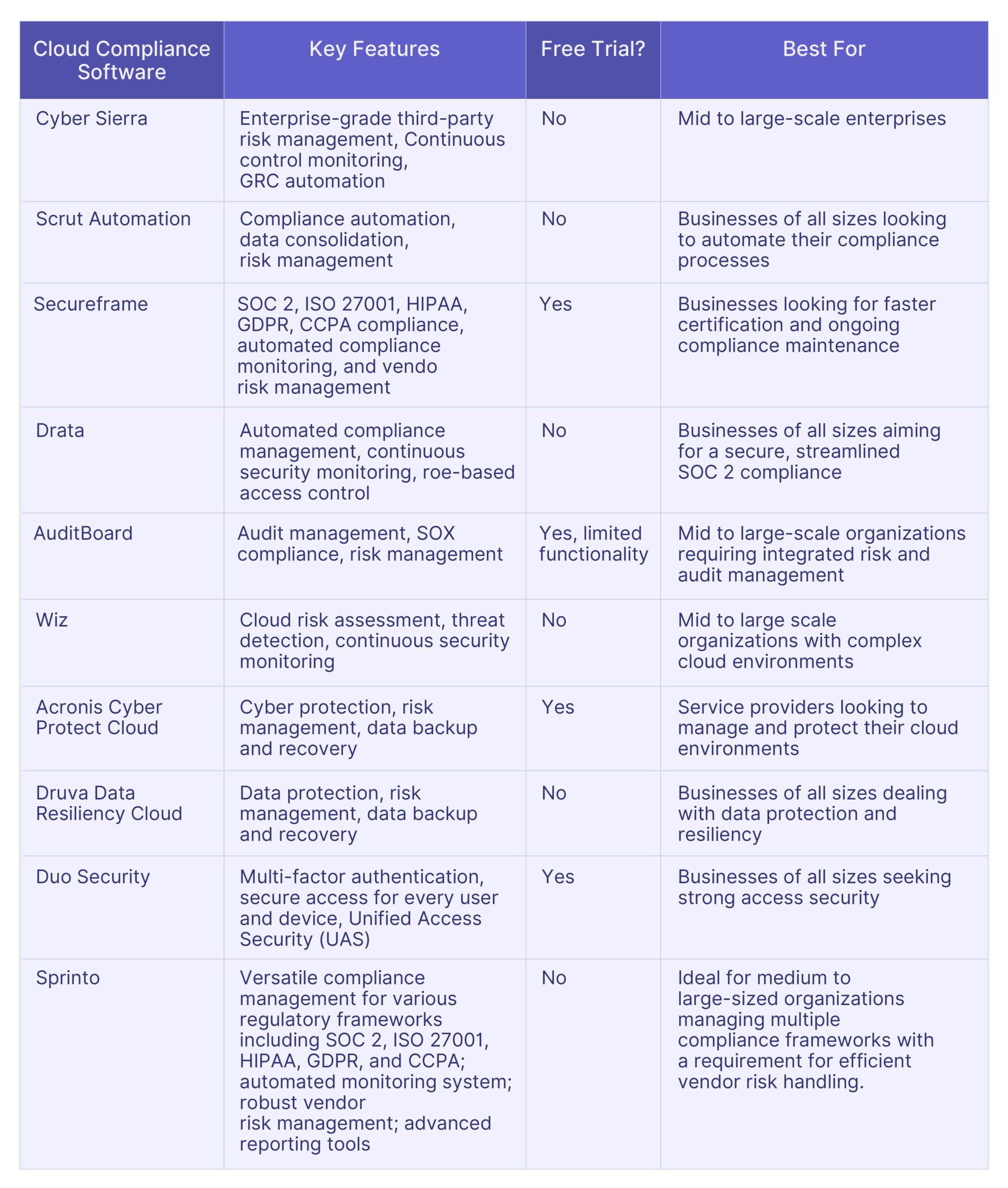
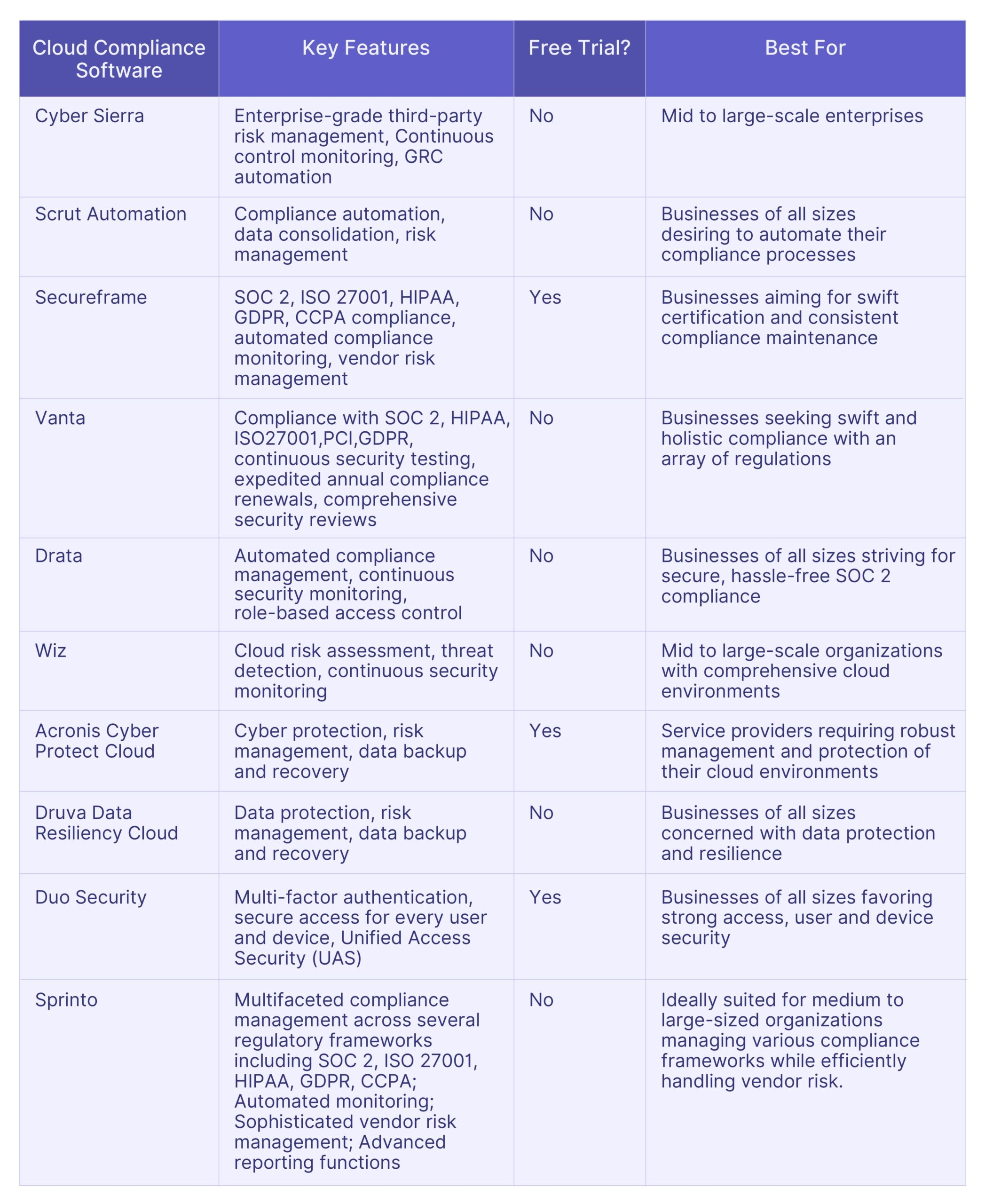
Top 10 AuditBoard Alternatives: Comparative Analysis
Here is a comparative analysis of the top 10 alternatives to AuditBoard, tailored to assist you in identifying the optimal software specific to your needs.

Selecting the Best Software
Now, the task of identifying the right software for your needs can be simplified by meticulously considering relevant features, cost factors, and user feedback.
Given the breadth of software solutions proposed to enhance your organization’s management functions, it’s essential to choose one that resonates with your specific necessities.
Among security systems, Cyber Sierra distinguishes itself by integrating high functionality and robust protection within a single platform.
Cyber Sierra’s simple design enables the prompt and straightforward application of needed security controls, giving your business fortified protection against potential cyber threats.
Schedule a demo today and learn how Cyber Sierra can optimally secure your business.





















A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.