Automating Governance, Risk, and Compliance: Revolutionizing Management with GRC Automation





















Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
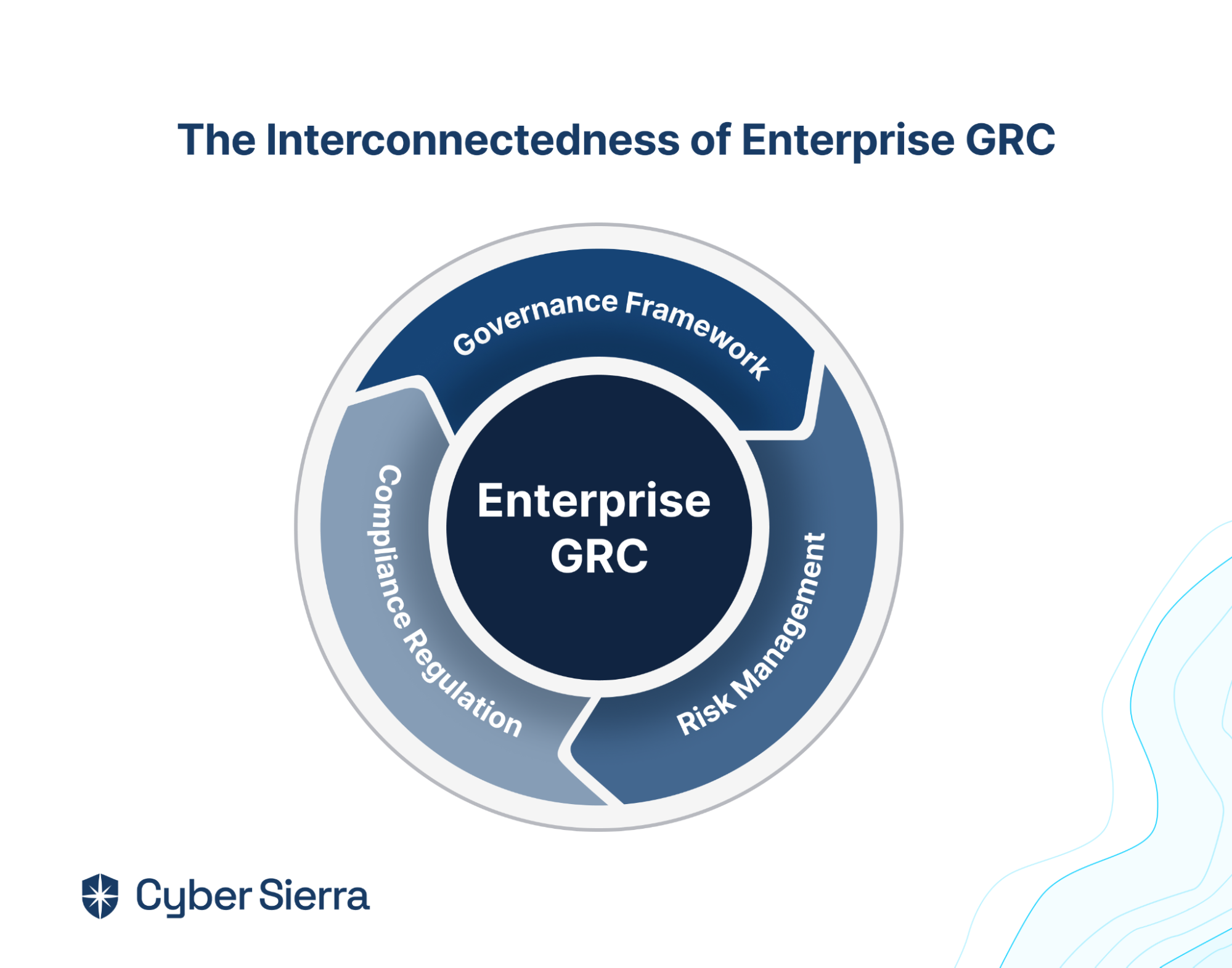
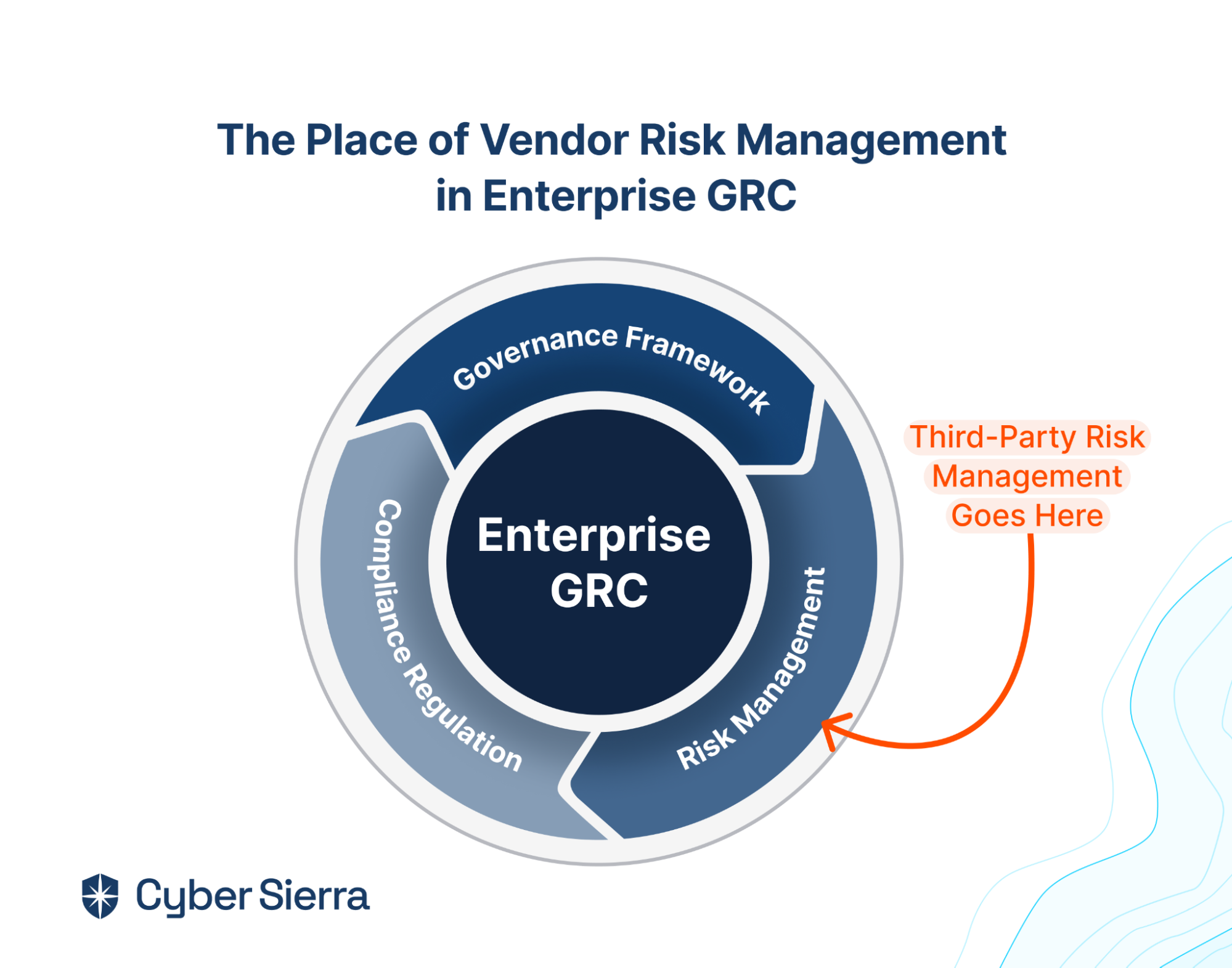
The importance of governance, risk, and compliance (GRC) cannot be overstated in today’s ever-evolving enterprise ecosystem.
Companies face an ever-growing array of regulations, risks, and governance challenges that can affect their operations, reputation, and bottom line.
Automating GRC manual processes has become a critical strategy for organizations aiming to enhance efficiency, ensure compliance, and manage risk effectively. According to a report by Grand View Research, the global GRC market size was valued at USD 32.2 billion in 2021 and is expected to expand at a compound annual growth rate (CAGR) of 14.5% from 2022 to 2030.
This statistic underscores the increasing reliance on and investment in GRC automation as businesses strive to navigate a complex regulatory environment more efficiently.
What is GRC Automation?
GRC automation refers to integrating technology to streamline and enhance the processes involved in an organization’s governance, risk management, and compliance frameworks.
By leveraging software and tools, companies can automate repetitive tasks, reduce human error, and provide real-time insights into risk and compliance status.
This technological approach saves time and allows for more strategic decision-making, freeing resources to be redirected to more critical areas of the business.
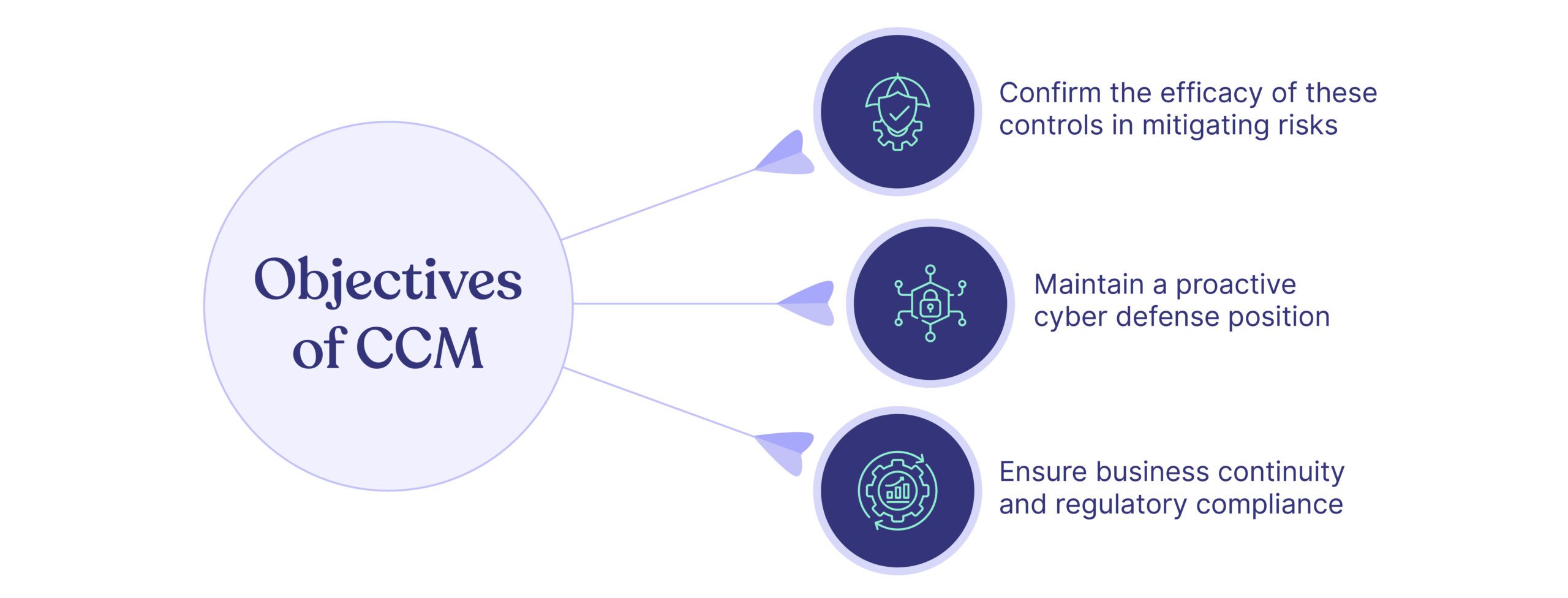
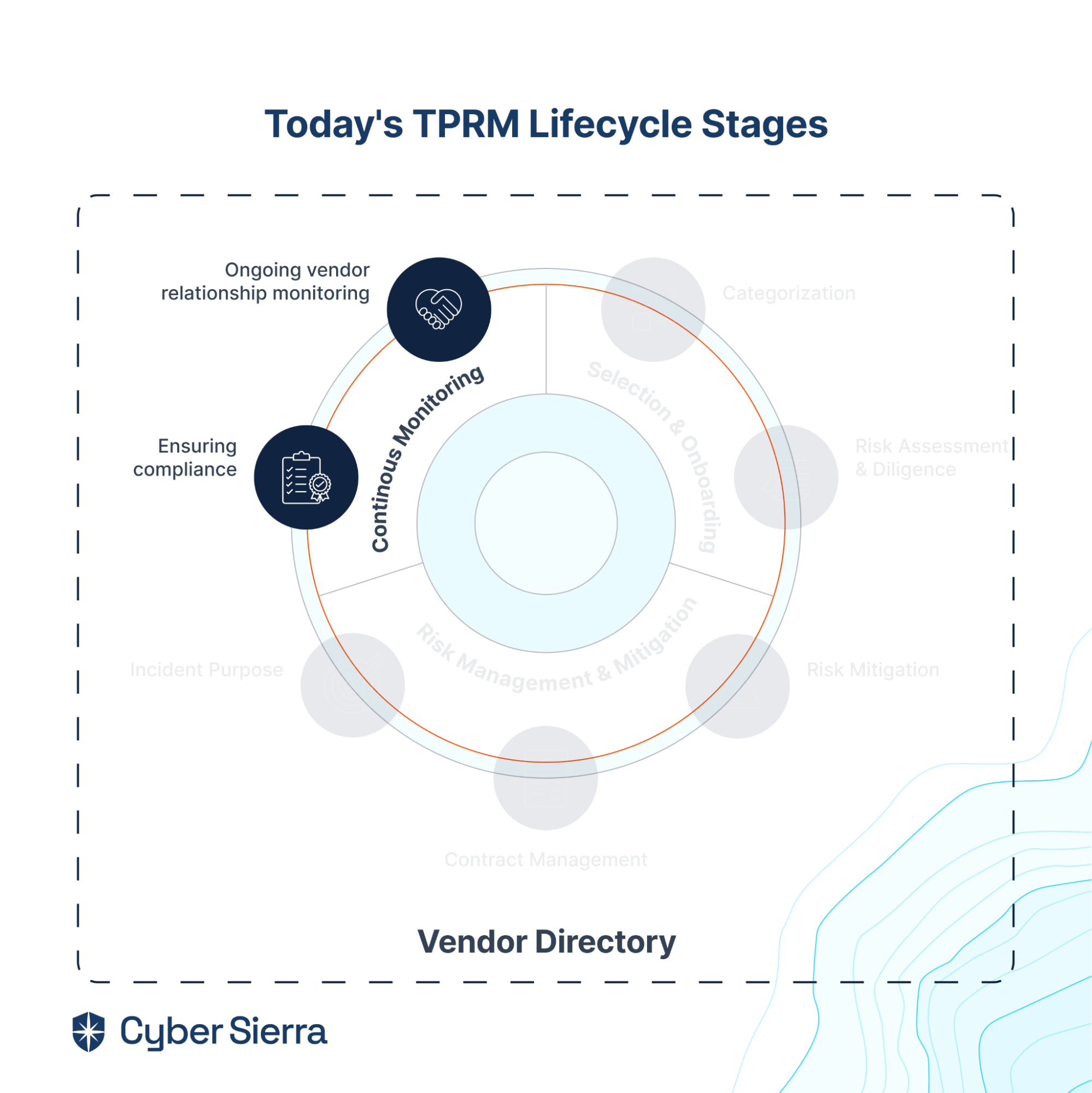
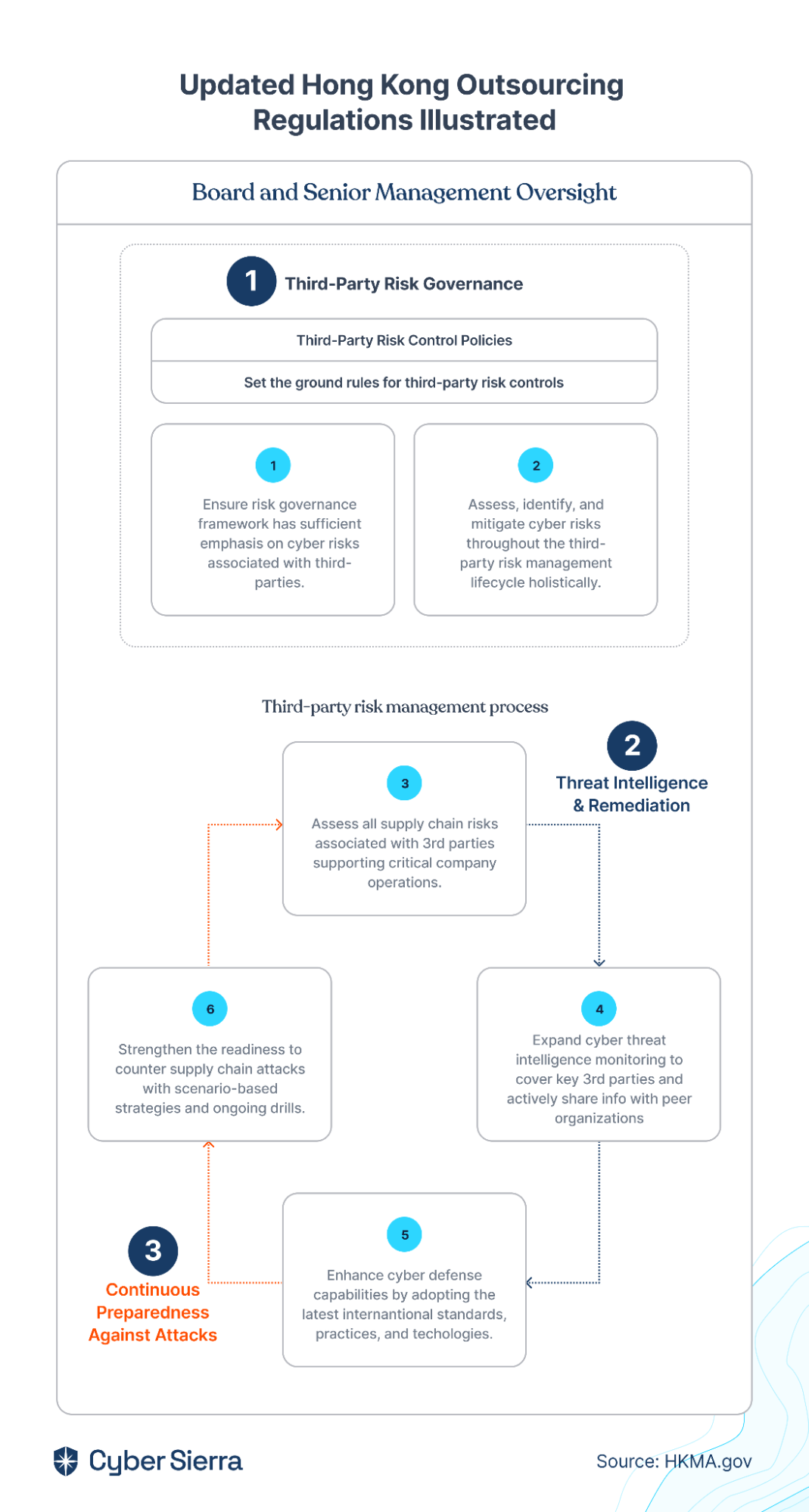
GRC automation is crucial for organizations to navigate complex compliance programs and risk management effectively, enhancing their security posture. When GRC frameworks and regulatory requirements emerged in 2007, manual methods like spreadsheets sufficed for many businesses.
However, by 2023, the compliance requirement and regulatory landscape had become much stricter, with numerous compliance and reporting demands. Spreadsheets are no longer adequate for managing these complexities, making GRC automation essential for seamless compliance and risk management.
How to Automate the GRC Process?
In today’s complex regulatory environment, automating Governance, Risk, and Compliance (GRC) systems is crucial for any proactive organization. This guide presents a seven-step approach to effectively automate your GRC processes, from setting clear objectives to continuously monitoring for improvements. It ensures streamlined compliance, real-time risk assessments, and strong governance.


1. Define Business Case And Objective
The first step in automating GRC systems is establishing a solid business rationale. Defining clear objectives provides a roadmap, guiding all stakeholders through the process. Whether your goals include streamlining compliance reporting, improving risk visibility, or enhancing cost efficiency, these objectives will directly influence your choice of technology and implementation approach.
At this critical stage, it is crucial to involve key stakeholders from legal, IT, compliance, and business operations. Their diverse insights help build a comprehensive business case, laying a strong foundation for the automation project.
2. Assess Current GRC Processes & Identify Areas Of Improvement
Before automating, thoroughly assess your current GRC systems to pinpoint bottlenecks, redundancies, and inefficiencies. This evaluation should identify challenges and reveal opportunities for improvement that automation can leverage.
Use process maps and flowcharts to trace data and task flows across departments. These visuals can highlight system weaknesses and offer clear targets for your automation initiatives.
3.Select the Right Tools To Support your Automation Objectives
Selecting the right technology platform is a critical decision with lasting effects. Ensure the platform meets your current needs and offers scalability for future expansion. Involve your tech team to verify compatibility with your IT infrastructure and integration potential with other systems.
Beyond technical features, you must also evaluate the vendor’s reputation, customer support, and reliability. Consulting customer reviews, seeking references, and reviewing case studies of successful implementations can offer deep insights into the platform’s fit for your organization.
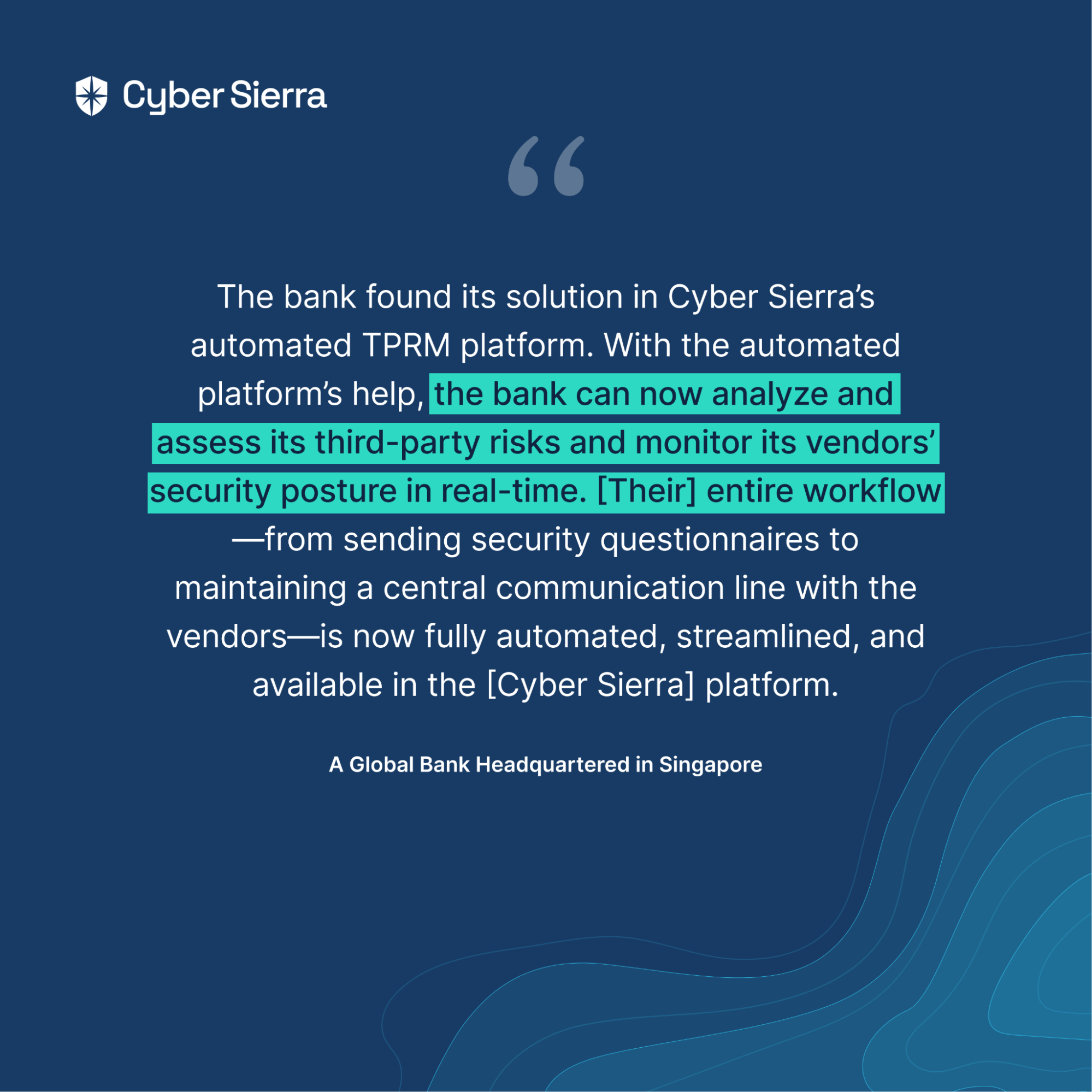
CyberSierra, for example, provides tailored GRC solutions that can accommodate the nuances of different organizational structures and industries.
4. Implement with Change Management
Implementing GRC automation tools involves significant change management. Training and supporting your staff to adopt new technologies is crucial for success. Ensure that all stakeholders understand the benefits of GRC automation and are engaged in the transition process.
Once you select your technology platform, it’s crucial to implement controls that ensure data quality and process integrity. The accuracy of your automated GRC reports and monitoring relies heavily on the reliability of your input data. A poorly designed data flow can lead to errors that may result in regulatory fines or strategic missteps.
You must establish rigorous data validation checks, error-handling procedures, and data reconciliation protocols. These measures act as your first line of defense against inaccuracies and inconsistencies, ensuring that your automated GRC systems are a reliable source of truth for your organization.
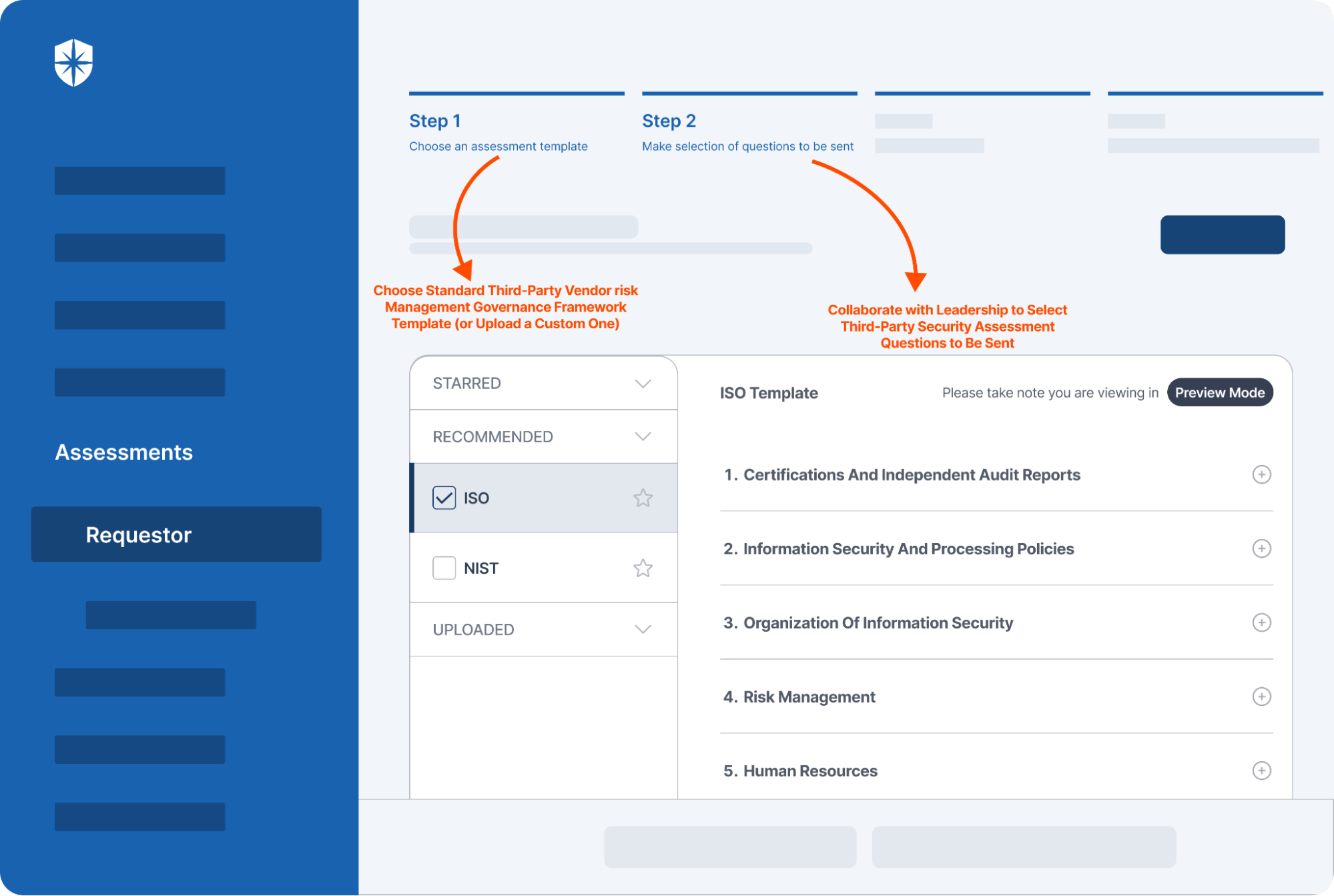
5. Configure the Automation Solution
Off-the-shelf software often doesn’t perfectly fit all your organization’s unique needs. After purchasing the software, you’ll likely need to customize it to match your business processes, organizational structure, and compliance requirements. Collaborate closely with your vendor or internal IT team to tailor features such as user roles, permissions, and alert settings to suit your specific needs.
Conducting a pilot test of the configured system within a controlled environment or a single department can reveal necessary adjustments before a full-scale rollout. This step is crucial for identifying and addressing any unexpected challenges or gaps in the configuration, ensuring a smoother implementation for your finance, tax, or compliance operations.
6. Train all Stakeholders before Rolling It Out Across the Organization
Implementation isn’t complete until all users are proficient with the new system. You should develop training programs tailored to your organization’s various roles, ensuring that both managerial and operational staff know how to use the system for their specific GRC tasks.
Use the training phase as a chance for final refinements. Feedback from users during this period can provide valuable insights into the system’s efficiency and user experience, allowing you to make essential tweaks before deploying the system across your organization.
This step ensures a smooth transition and optimal performance in your finance, tax, or compliance departments.
7. Continuous Monitoring and Optimization
After implementation, the journey isn’t over. Ongoing monitoring is crucial to ensure that the system continues achieving its objectives and remains current with regulatory changes and business process shifts.
You should closely track key performance indicators like compliance adherence rates, incident response times, and risk assessment durations.
Set up periodic audits and establish feedback loops with users for continuous improvement. As regulations change, business needs evolve, and technology advances, your automated GRC system must remain agile and adaptable.
Regular updates and iterative enhancements will ensure its continued relevance and effectiveness for your finance, tax, or compliance operations.
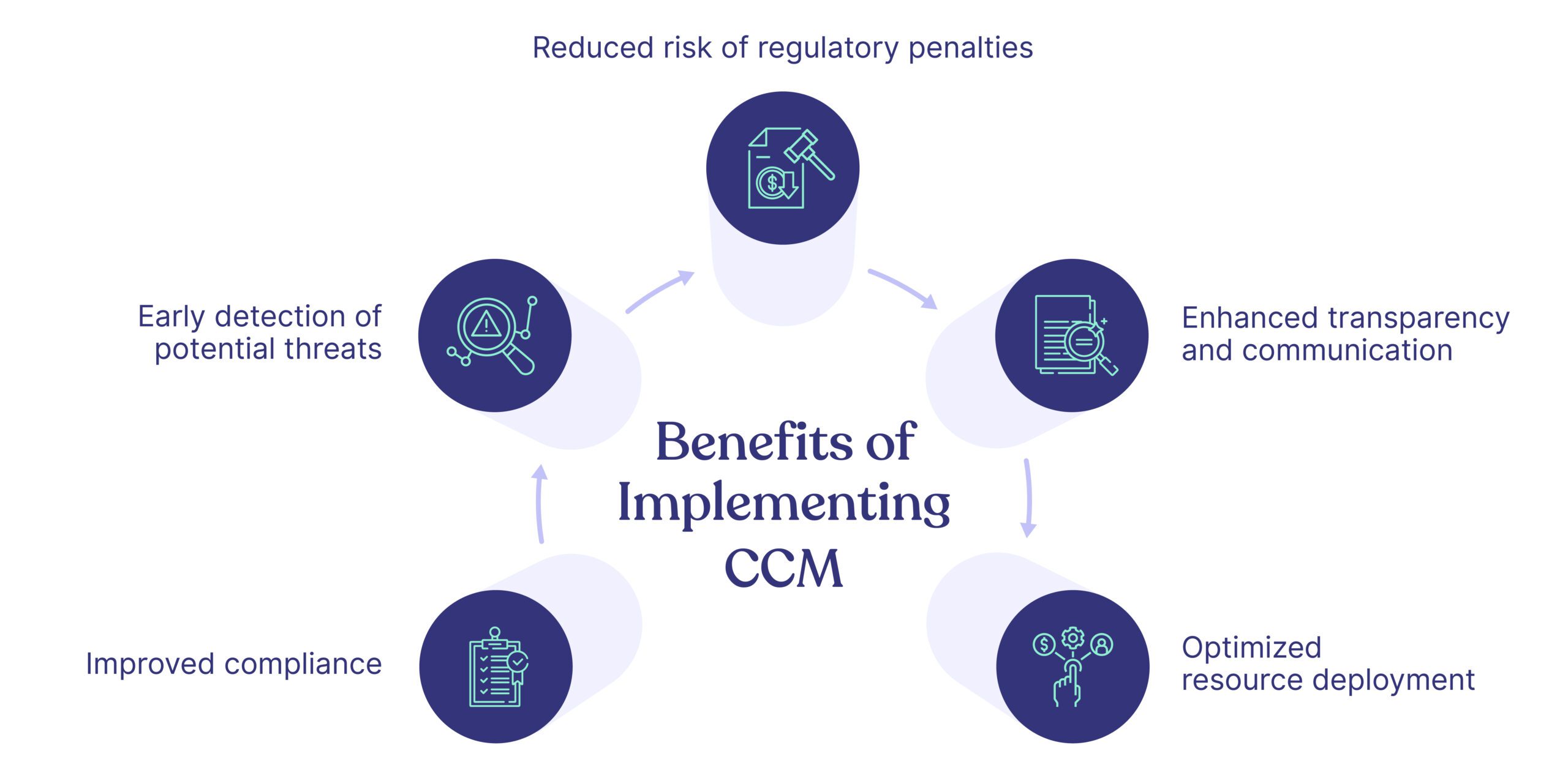
Advantages of GRC Automation
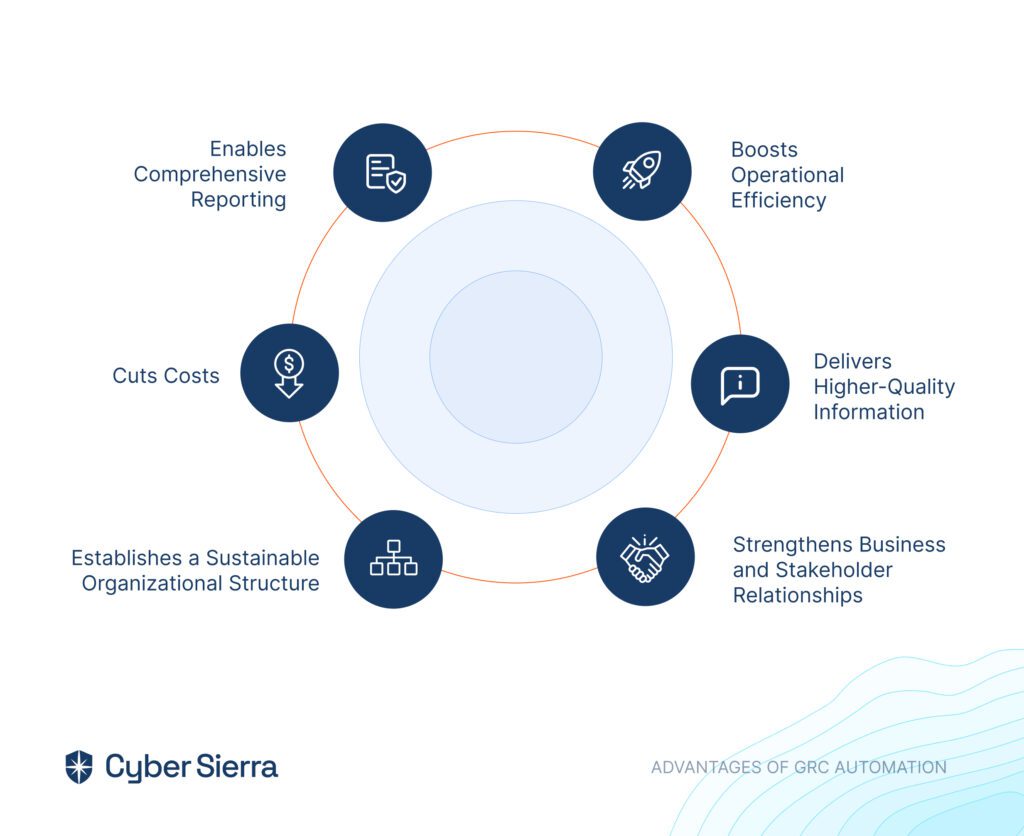

A GRC system can enhance your organization in several key ways:
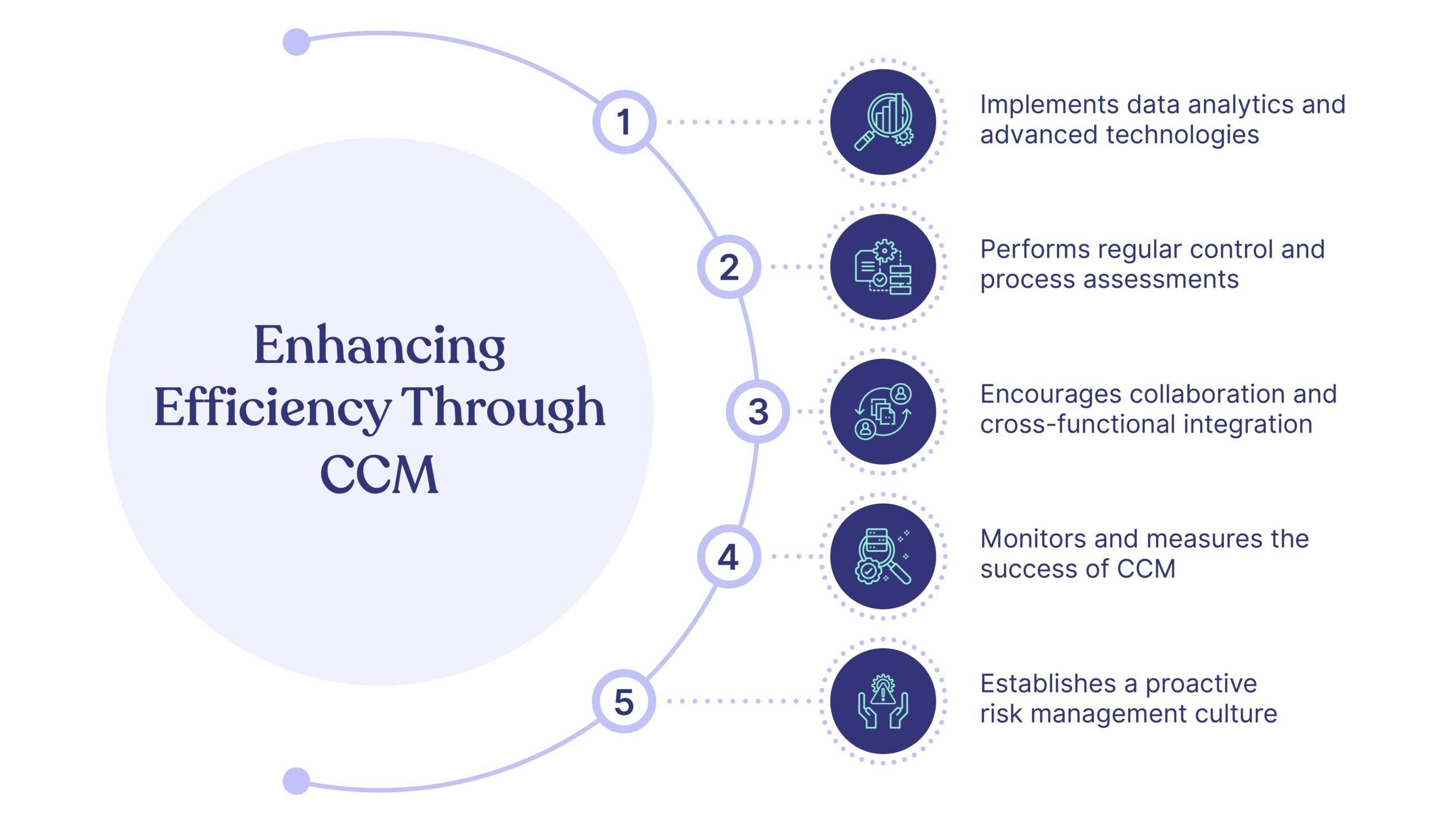
1. Boosts Operational Efficiency
A GRC system automates repetitive and time-consuming tasks by continuously monitoring controls and risk indicators. This leads to streamlined business operations and less duplication of effort, saving time and improving employee productivity across your organization.
2. Delivers Higher-Quality Information
Automation integrates various data streams, providing staff with a comprehensive view of the organization. This improves the quality of information, aiding management in making smarter, more informed and on-time decisions.
3. Strengthens Business and Stakeholder Relationships
GRC tools facilitate easy sharing of information via cloud storage with controlled access. This reduces the need for frequent stakeholder interactions and provides clear insights into business units, risks, and challenges.
4. Establishes a Sustainable Organizational Structure
Implementing a GRC system helps clearly define and embed an organizational hierarchy, supporting role-based access and adaptability to changes in business structure.
5. Cuts Costs
By setting clear business rules and monitoring controls, a GRC system helps streamline GRC activities, which can significantly reduce operational costs.
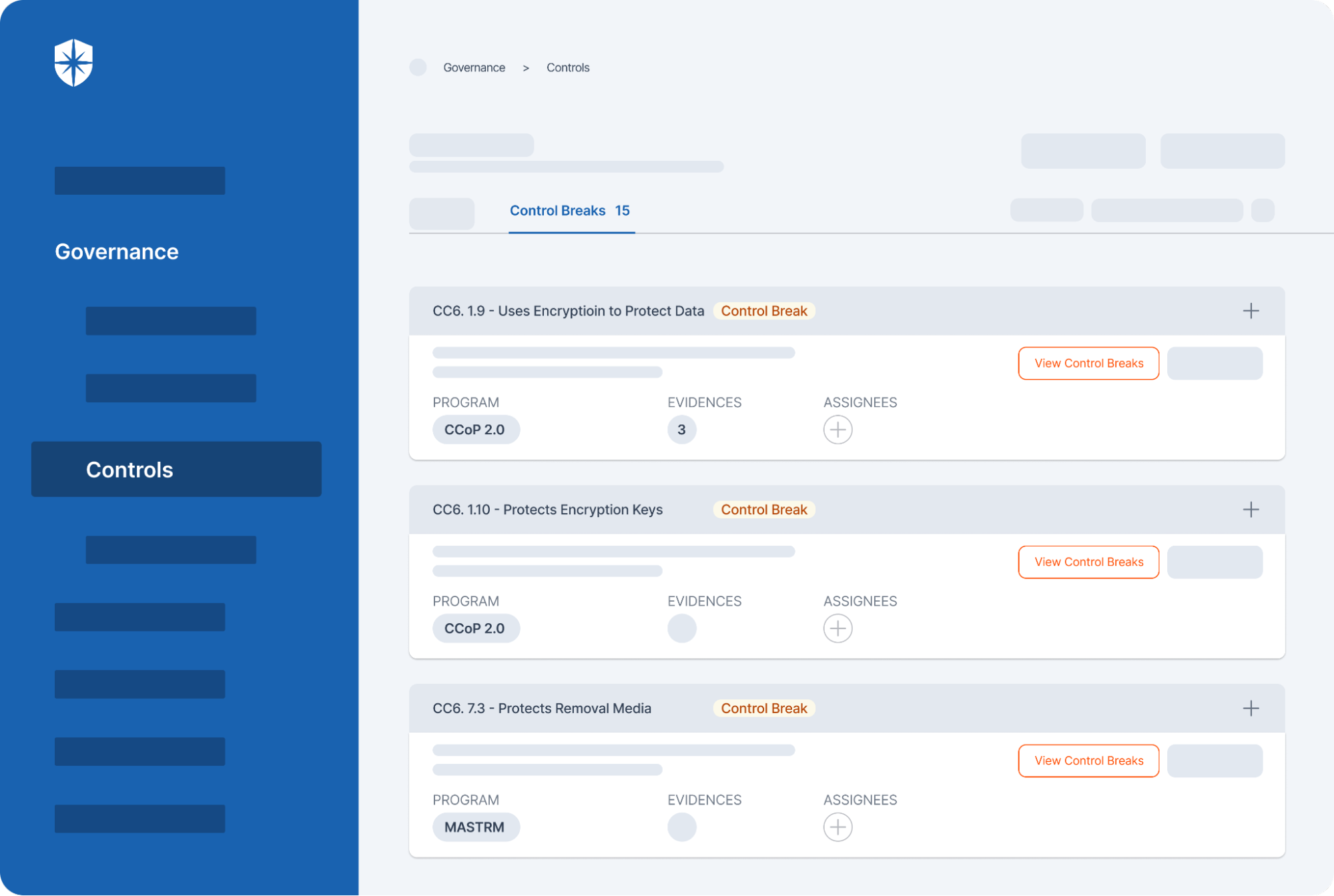
6. Enables Comprehensive Reporting
Unlike spreadsheets, GRC tools make it effortless for all the stakeholders involved in the compliance process to collaborate and allows for quick and easy generation of detailed reports, transforming what used to be a time-consuming process into a swift and simple task.
Challenges in GRC Automation
Implementing Governance, Risk, and Compliance (GRC) effectively is crucial, yet many organizations encounter significant hurdles. Understanding these challenges can help you prepare better and implement effective GRC strategies.
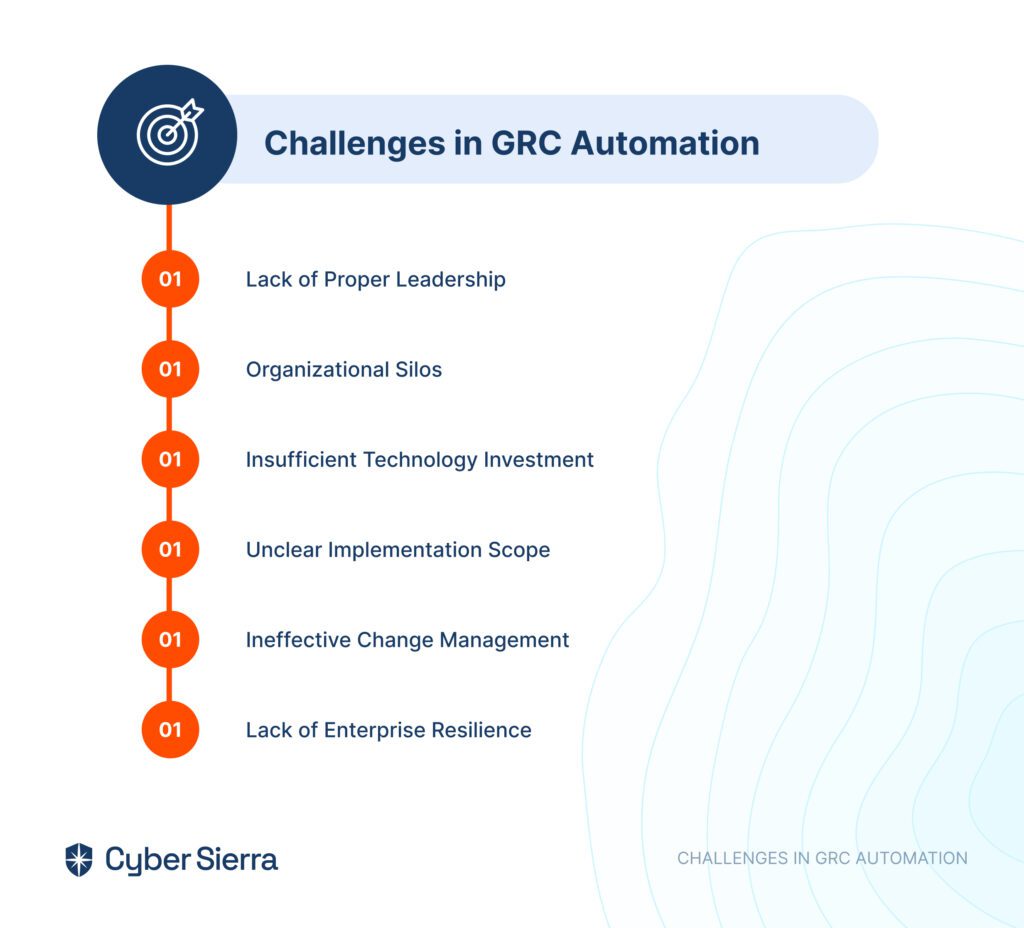

Here are six common pitfalls:
1. Lack of Proper Leadership
Successful GRC implementation starts with the right team. Business leaders who want to implement GRC automation must know the latest market trends and industry-specific risks, such as equipment sabotage in manufacturing or phishing in financial services. It’s vital to tailor your GRC team to these unique challenges.
2. Organizational Silos
The lack of collaboration across departments can severely impact GRC efforts. Security and compliance should be a company-wide initiative that goes beyond the IT department. Misalignments or a siloed approach among departments can lead to misunderstandings and impede the effective implementation of GRC.
3. Insufficient Technology Investment
Outdated processes can derail GRC efforts. While investing in modern technologies like automation, ensure that your teams are trained on these tools. This is crucial for improving efficiency and compliance.
4. Unclear Implementation Scope
Determining whether to adopt a phased or an all-at-once approach to GRC integration is vital. An undefined approach can be detrimental. Leadership must realistically assess the organization’s capacity and set feasible timelines to avoid overwhelming the system and causing delays.
5. Ineffective Change Management
Inadequate organizational change management and failure to understand how new technologies integrate with existing systems are common reasons for GRC failures. Leaders must evaluate the compatibility of new technology with current systems and ensure clear communication with technology providers to facilitate smooth integration.
6. Lack of Enterprise Resilience
Failing to incorporate resilience into the enterprise structure can hinder the benefits of GRC implementation. Organizations with a proactive approach to monitoring risks and building resilience tend to excel in GRC efforts. Leaders should establish processes that promote a risk-aware culture within the organization.
Addressing these challenges head-on can significantly enhance your GRC strategy’s effectiveness and security. This makes your organization’s choice of GRC partner critical to your success.
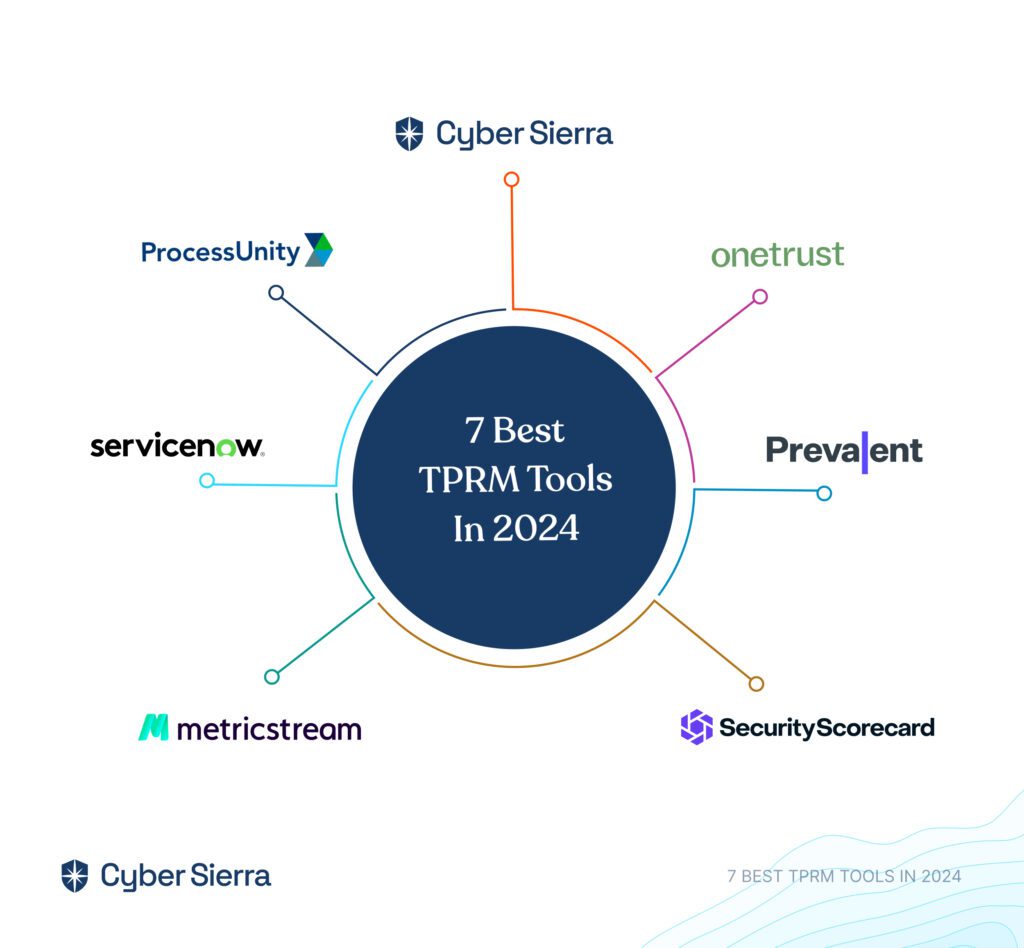
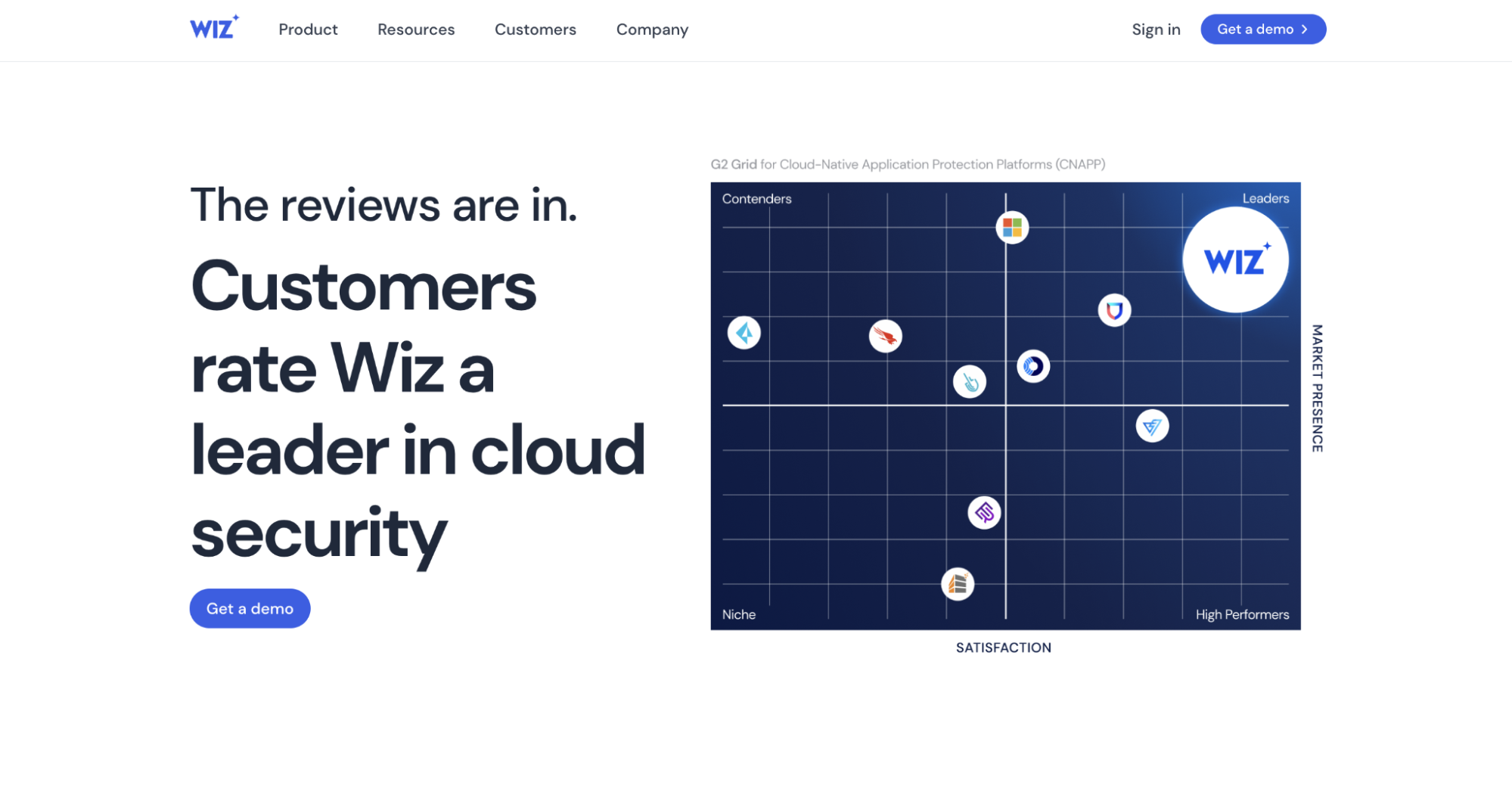
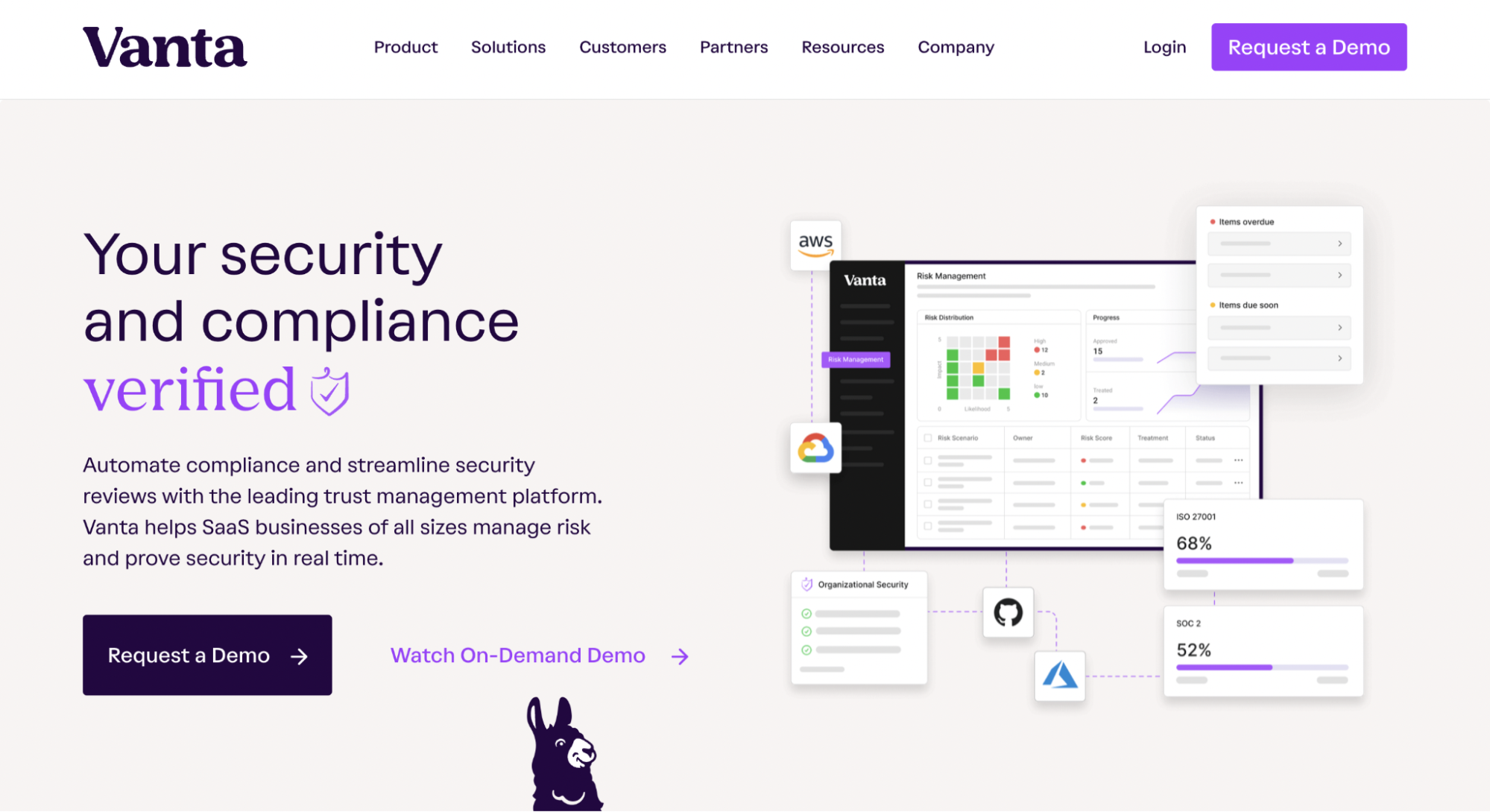
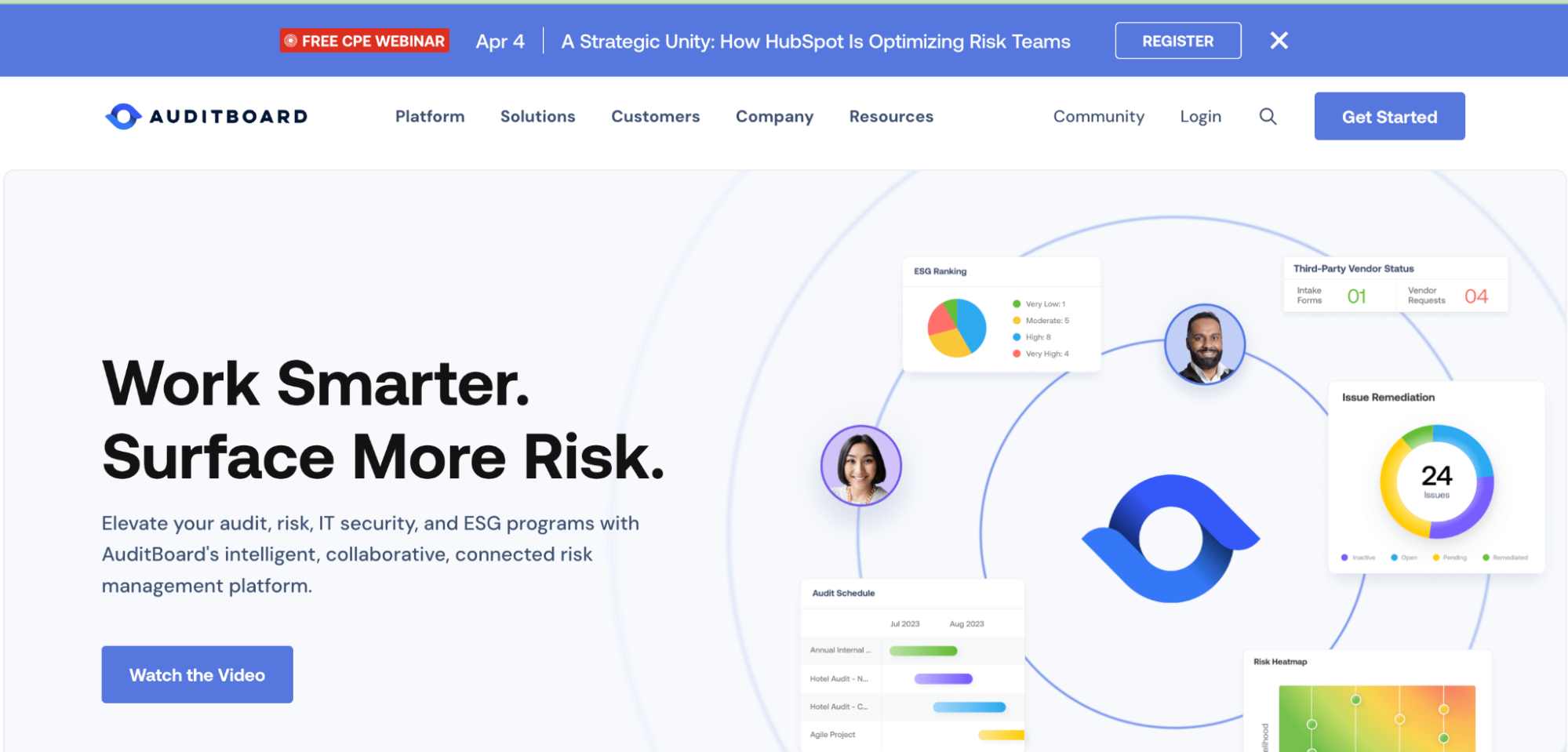
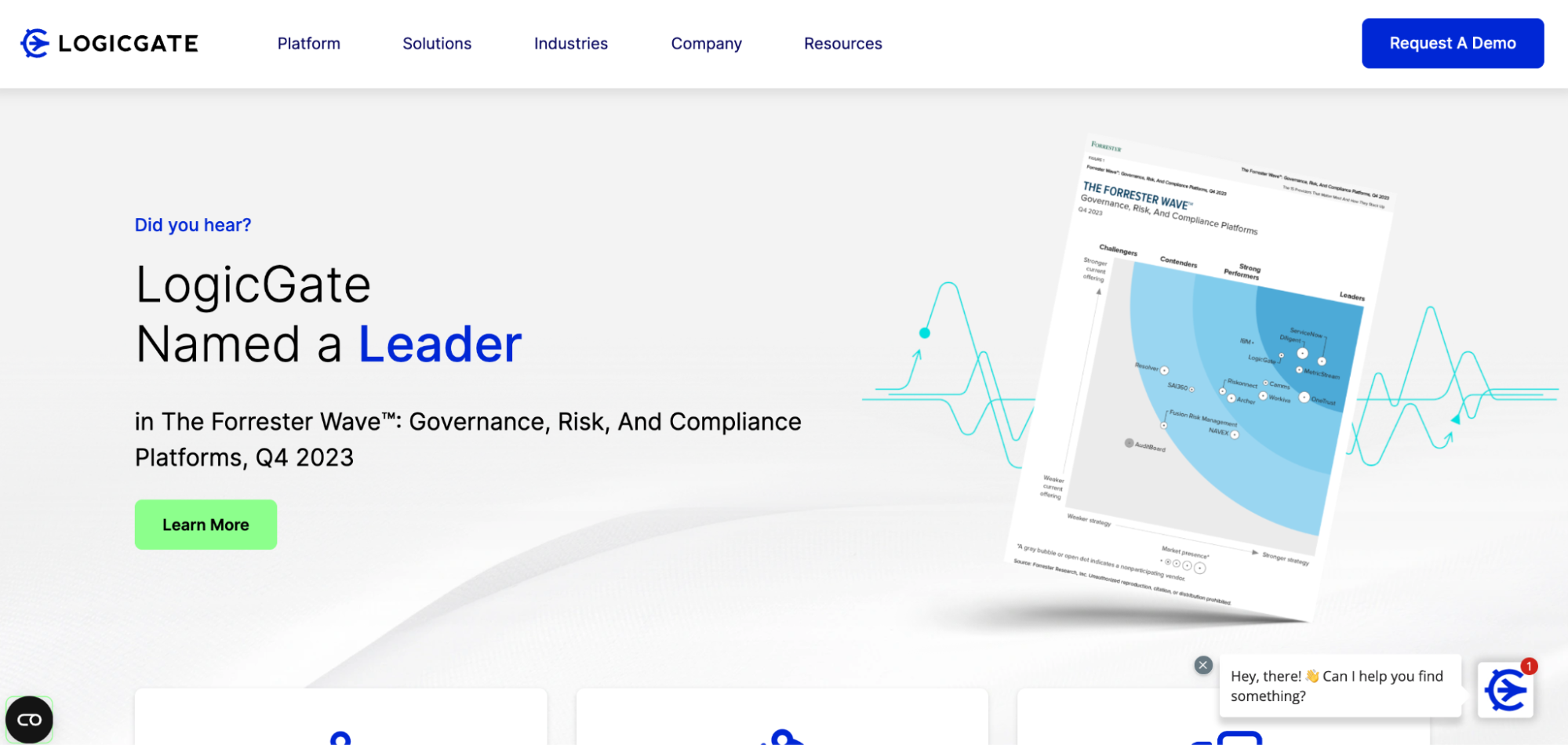
Top 7 GRC Tools You Should Consider in 2024
How CyberSierra Can Help You
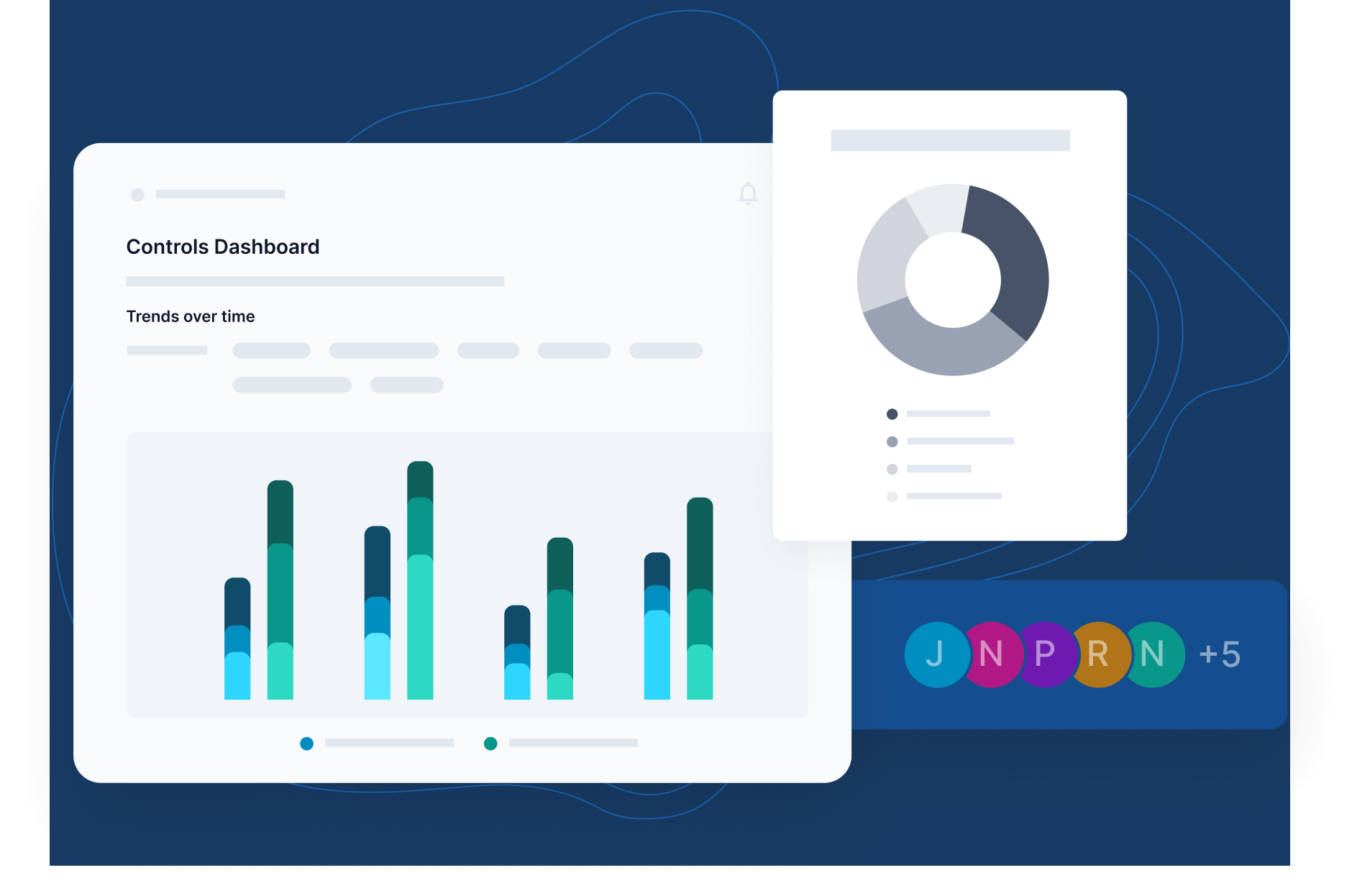
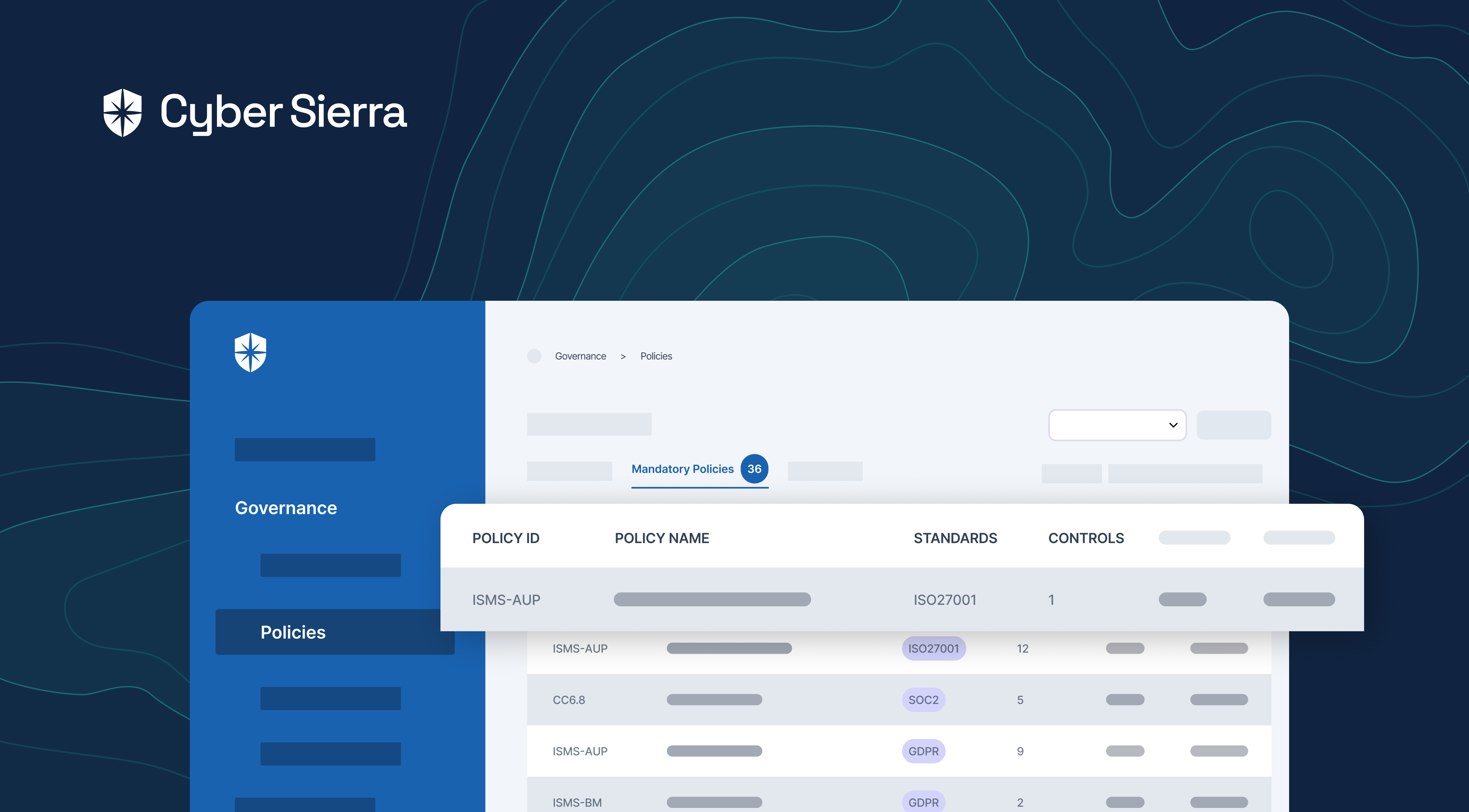
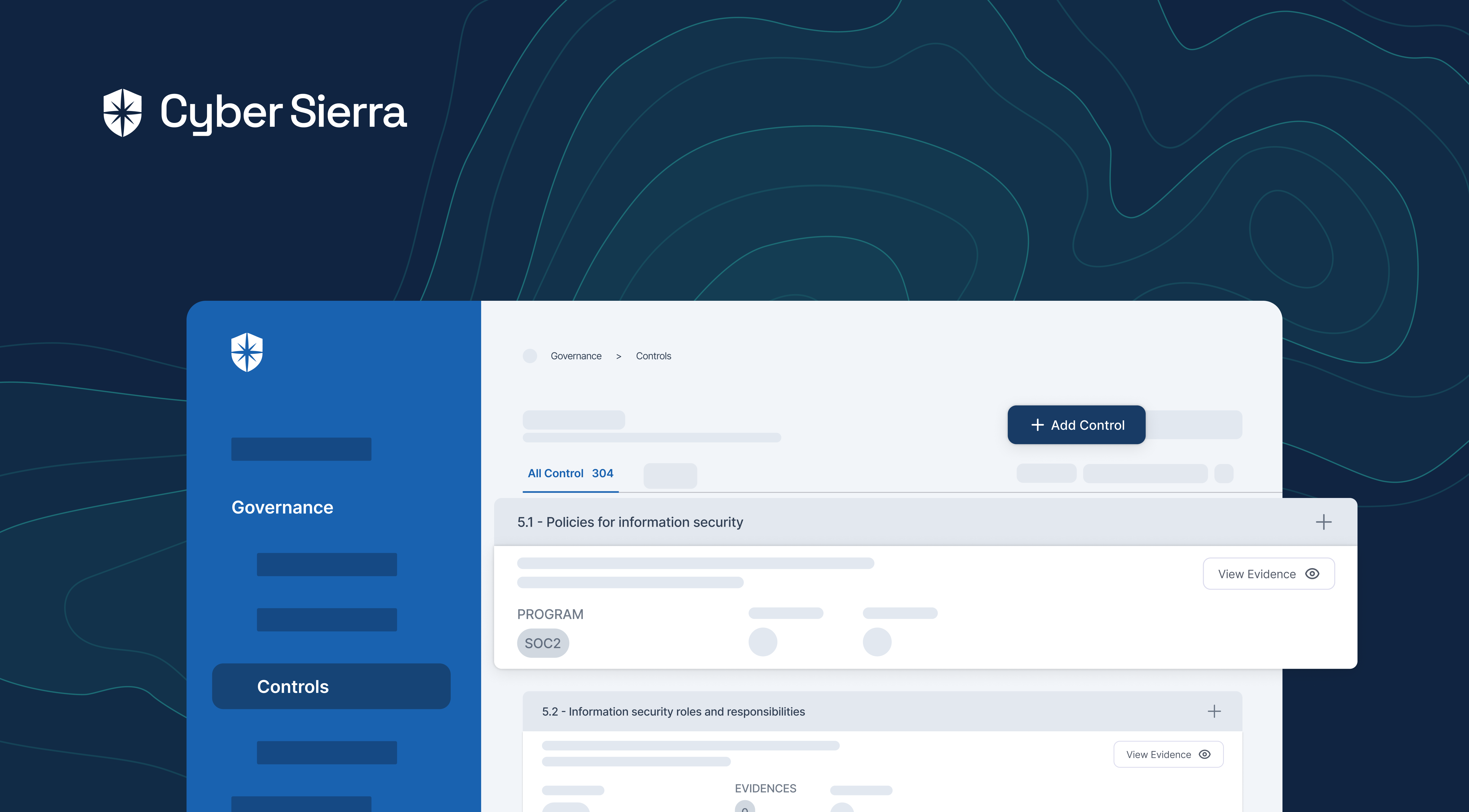
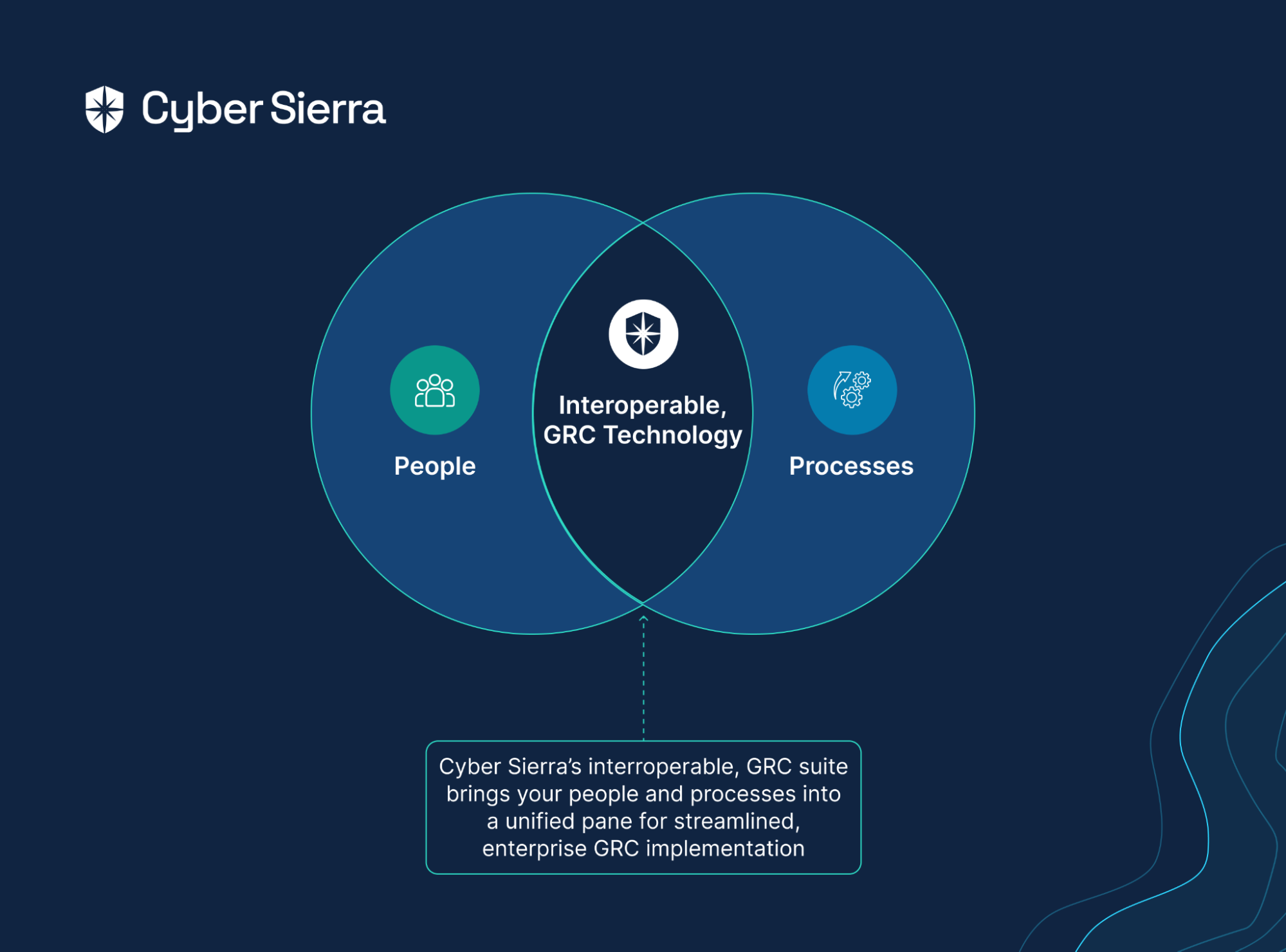
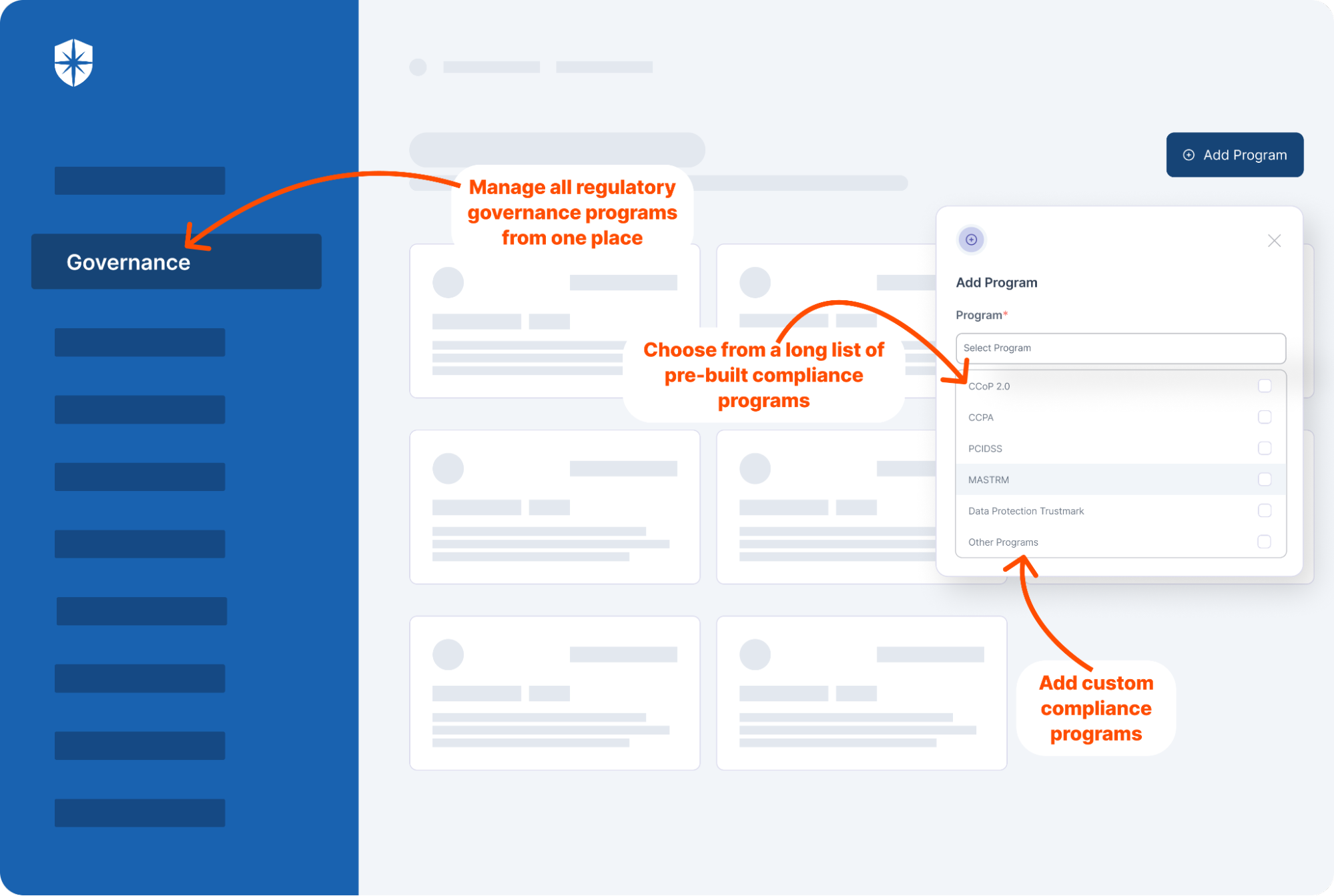
Cyber Sierra’s approach to Governance, Risk, and Compliance (GRC) automation is designed to assist enterprises overcome the host of challenges they face while automating the compliance process. The platform takes complexity and guesswork out of compliance and helps handle all parts of your GRC program in one place.
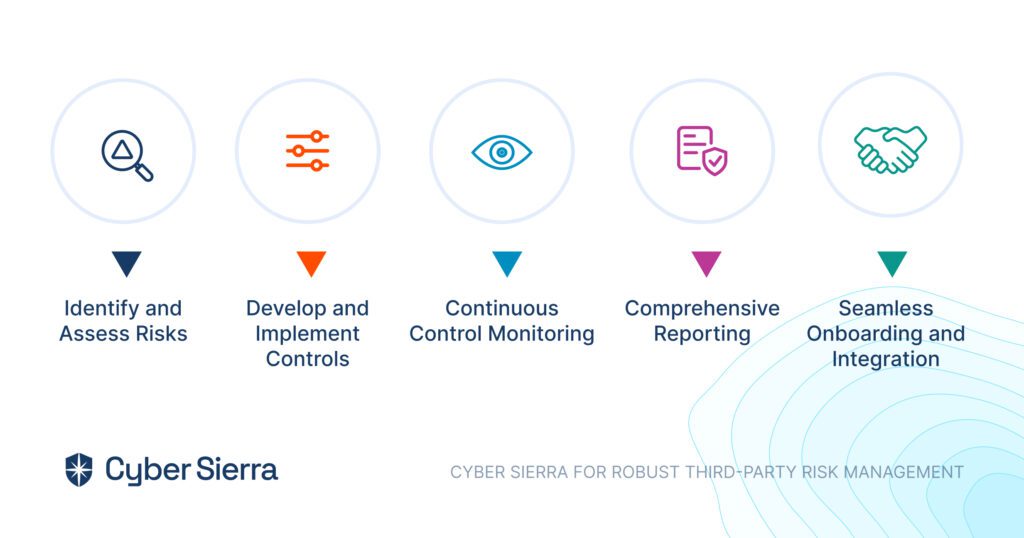

Whether you need compliance, risk management, better auditing, or improved controls management, Cyber Sierra’s platform is built to help you through the process swiftly and efficiently.
Cyber Sierra offers robust solutions tailored to enhance efficiency and security across your organization. Here’s how our platform can assist:
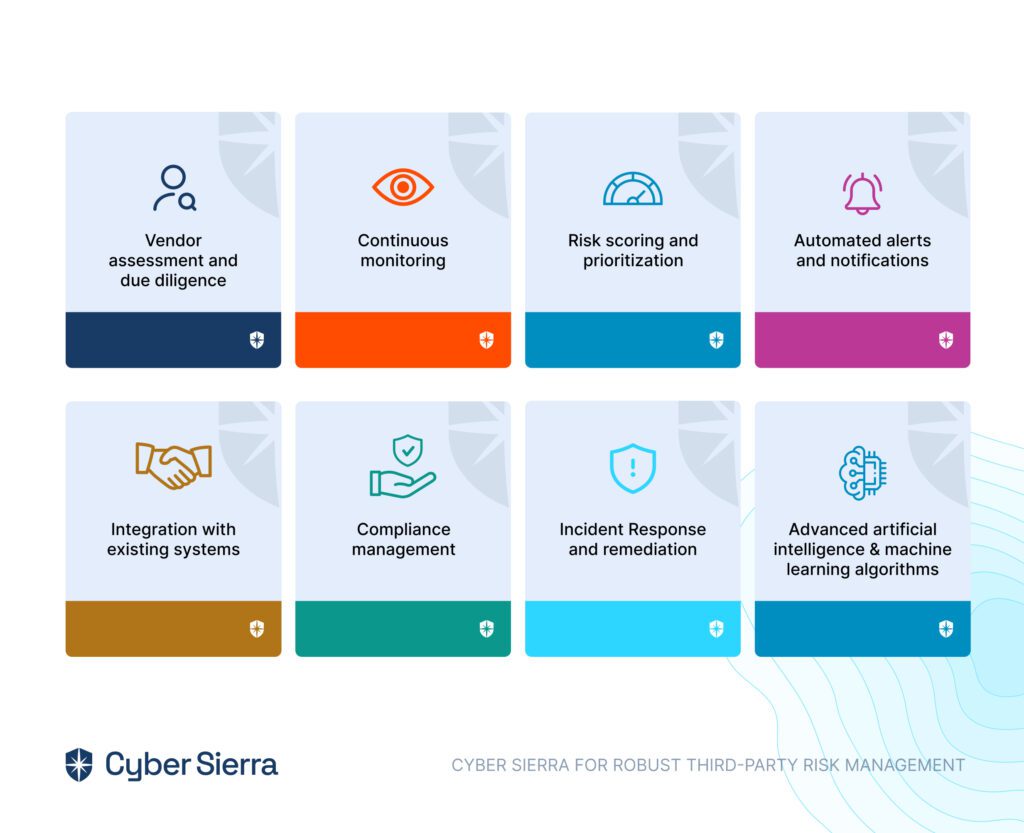
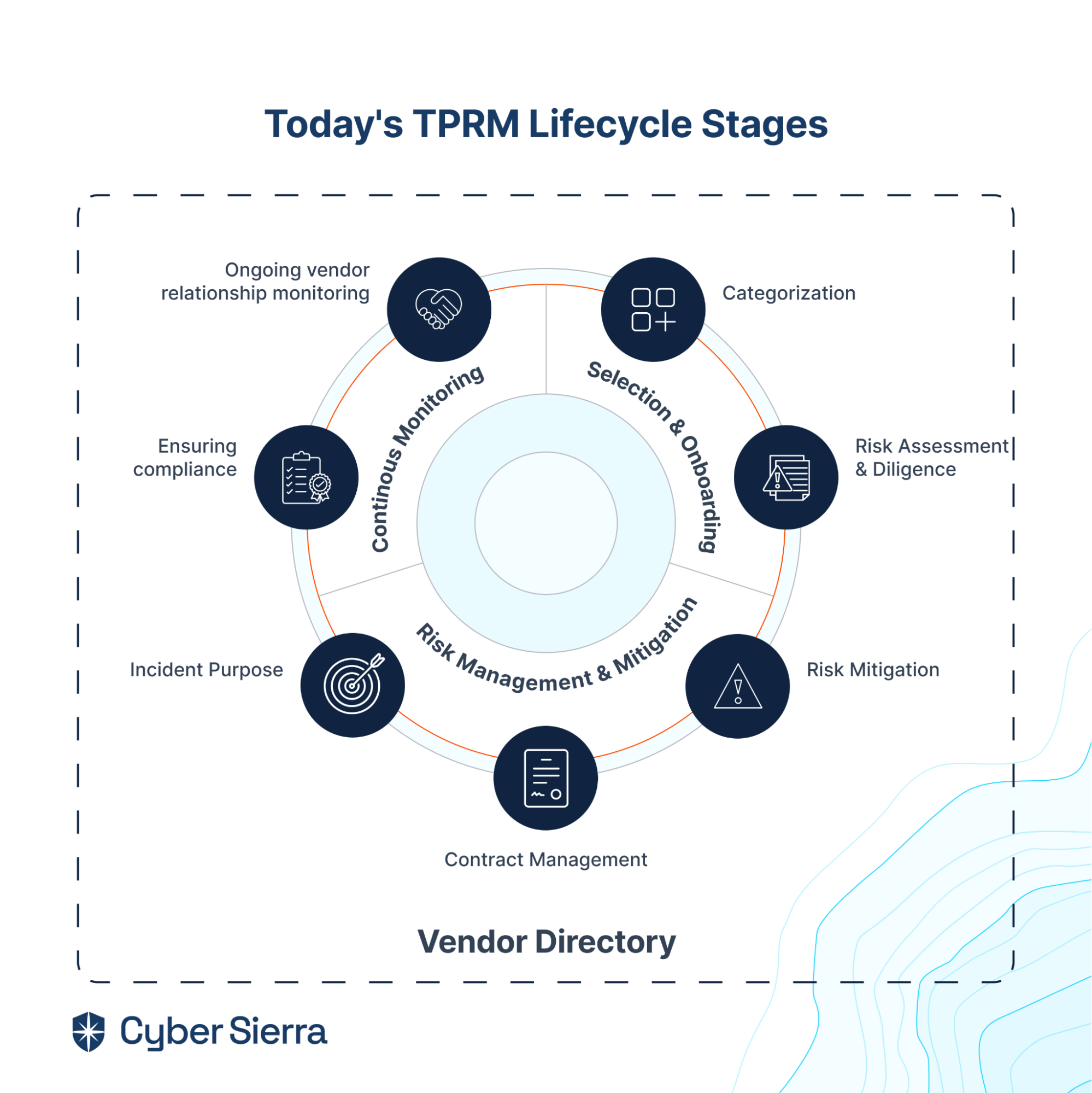
- Identify and Assess Risks: Cyber Sierra helps pinpoint risks across all asset categories, providing a comprehensive overview of your organization’s potential challenges.
- Develop and Implement Controls: We assist in creating and applying measures to mitigate identified risks, ensuring they align with your organizational goals and compliance requirements.
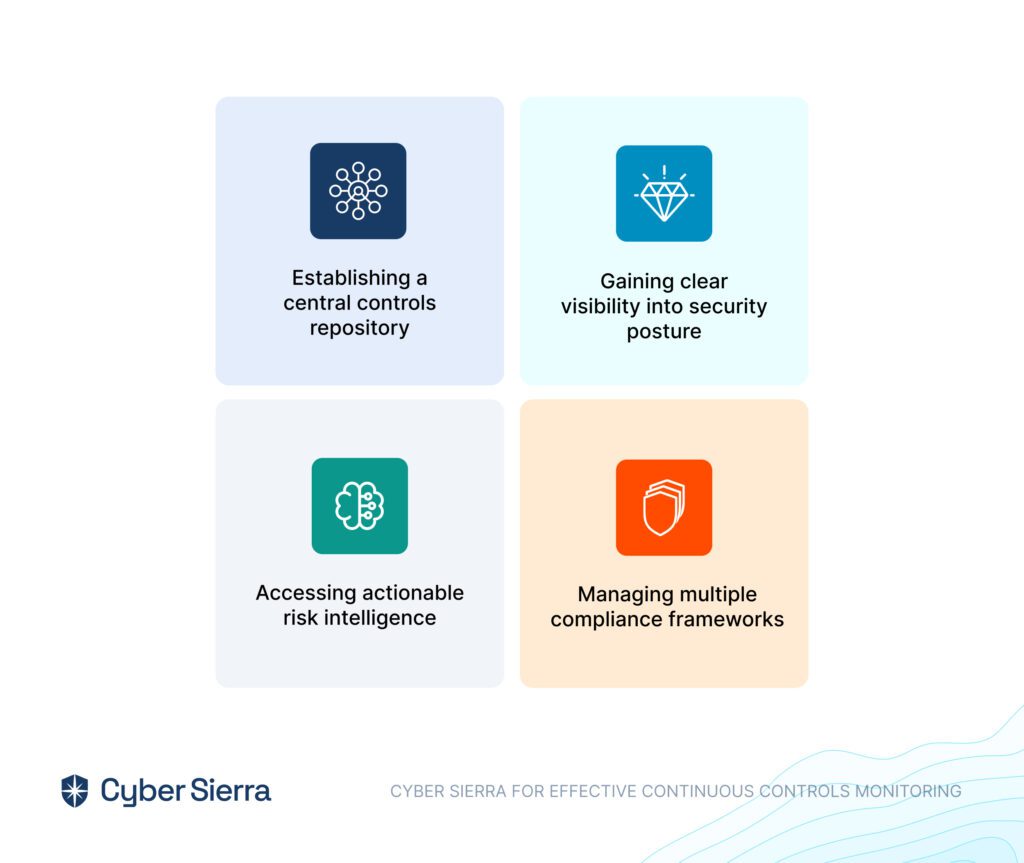
- Continuous Control Monitoring: Our platform offers ongoing 24×7 monitoring of control effectiveness, allowing you to maintain and improve your security posture dynamically.
- Comprehensive Reporting: Cyber Sierra enables streamlined reporting on your GRC activities, keeping stakeholders informed and engaged with up-to-date governance, risk, and compliance data.
- Seamless Onboarding and Integration: Cyber Sierra offers a seamless onboarding experience and comprehensive resources to ensure a smooth transition to our GRC tool.
By centralizing GRC management, Cyber Sierra simplifies compliance and strengthens your entire security framework, making it invaluable for any industry facing regulatory pressures.
Conclusion
In conclusion, as organizations strive to manage increased regulatory pressures and complex risk landscapes, the role of GRC automation becomes increasingly vital.
By embracing technology solutions like Cyber Sierra, companies can ensure compliance, manage risk effectively, and refocus resources on strategic growth initiatives.
Investing in GRC automation supports regulatory compliance and drives business efficiency and resilience, preparing your organization for the challenges of tomorrow.




















A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.