How to Create a TPRM Framework?- A Step-by-Step Guide























Join thousands of professionals and get the latest insight on Compliance & Cybersecurity.
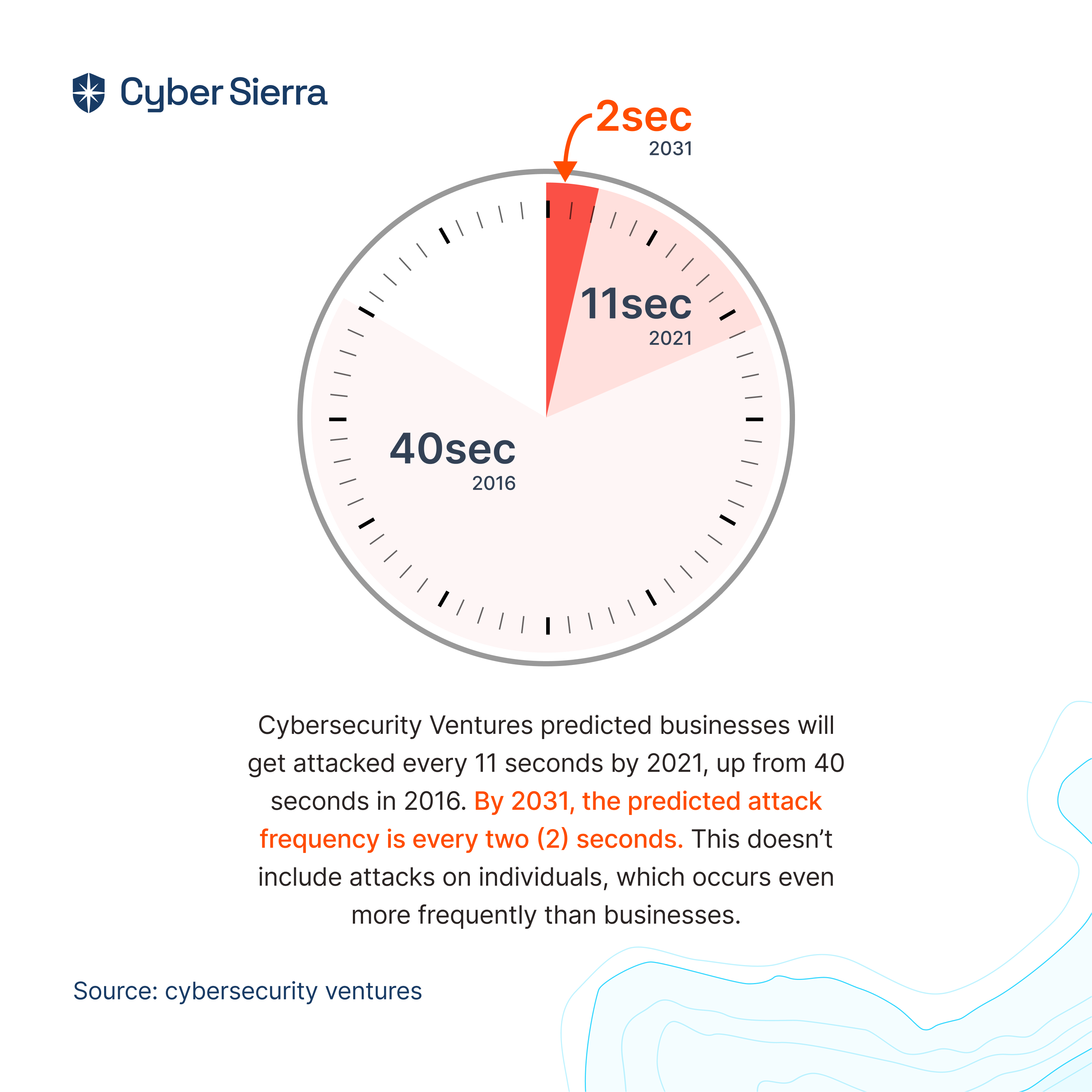
In today’s business landscape, operating without a third-party vendor can be challenging. Therefore, organizations often seek the strategic advantage of third-party vendors. But unfortunately, outsourcing third parties comes with inherent risks that must be actively managed.
Compliance leaders frequently note that organizations often face unforeseen risks following the initial onboarding and due diligence processes. This underscores the inherent complexity of third-party connections and highlights the critical need for comprehensive Third-party Risk Management (TPRM) strategies. While it is not possible to eliminate all third-party risks, establishing a comprehensive third-party risk management framework will help mitigate potential risks associated with each vendor.
“To build pervasive security across that third-party ecosystem, you not only need to know who those third parties are and what they’re doing for you,” said Edna Conway, chief security officer, global value chain at Cisco, “you had best understand the leadership and the operational processes utilized in your own enterprise that manage the commercial relationship with those third parties.” –
It is, therefore, imperative to understand your third-party risks. So, in this blog post, we will detail how to create a suitable third-party risk management framework for your organization and their associated benefits. Let’s get started right away!
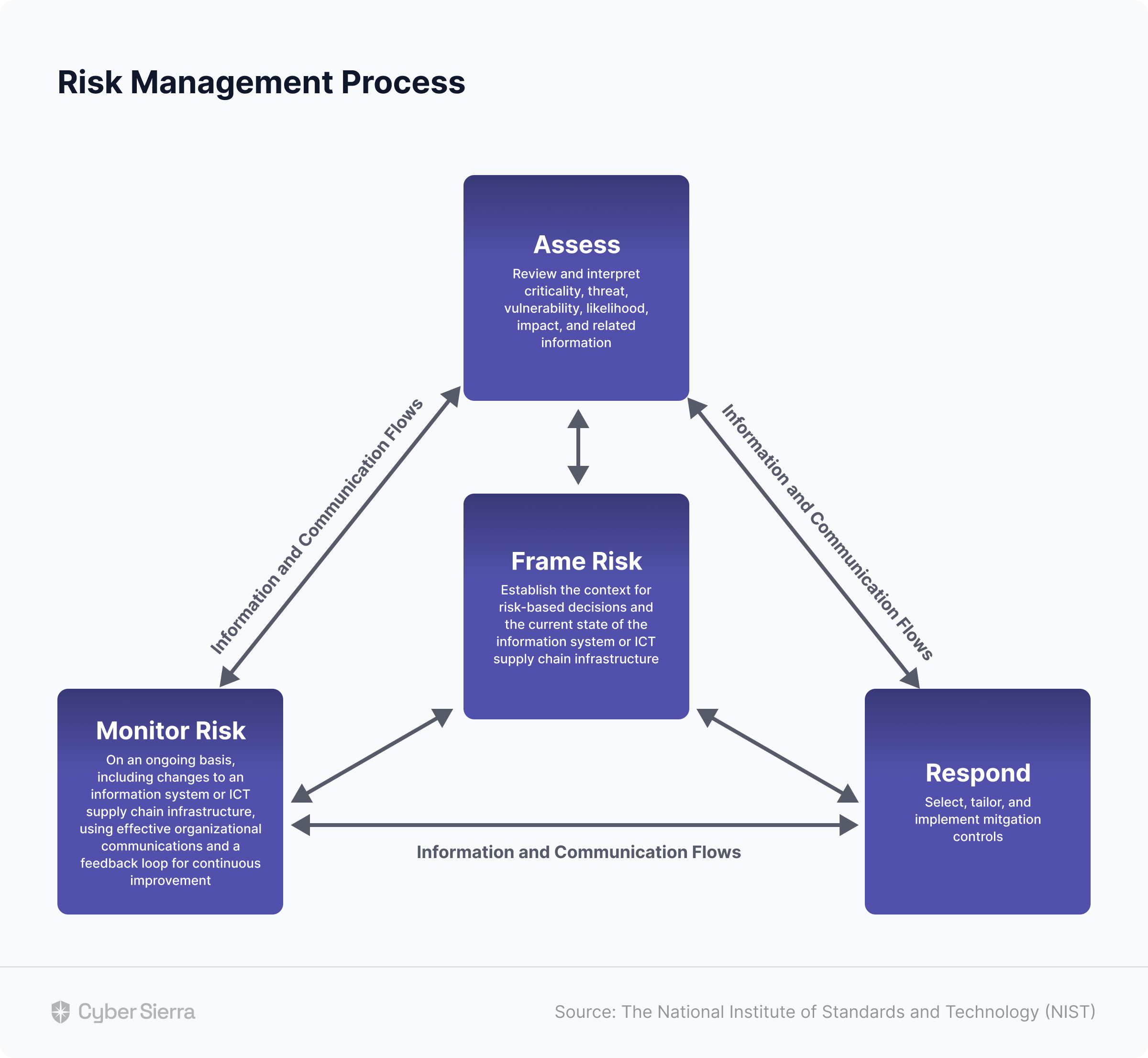
What is a TPRM Framework?
A third-party risk management framework evaluates and mitigates potential security risks associated with outsourcing to third-party vendors, partners, suppliers, or service providers. The framework provides a road map for organizations to build customizable risk management programs per their industry best practices.
A TPRM aims to comprehensively evaluate the risk landscape to minimize the likelihood of data breaches and vulnerabilities, and enhance the overall cyber resilience against threats from third-party vendor associations. The evaluation could range from access to your intellectual property to operational, legal, financial, and compliance risks.
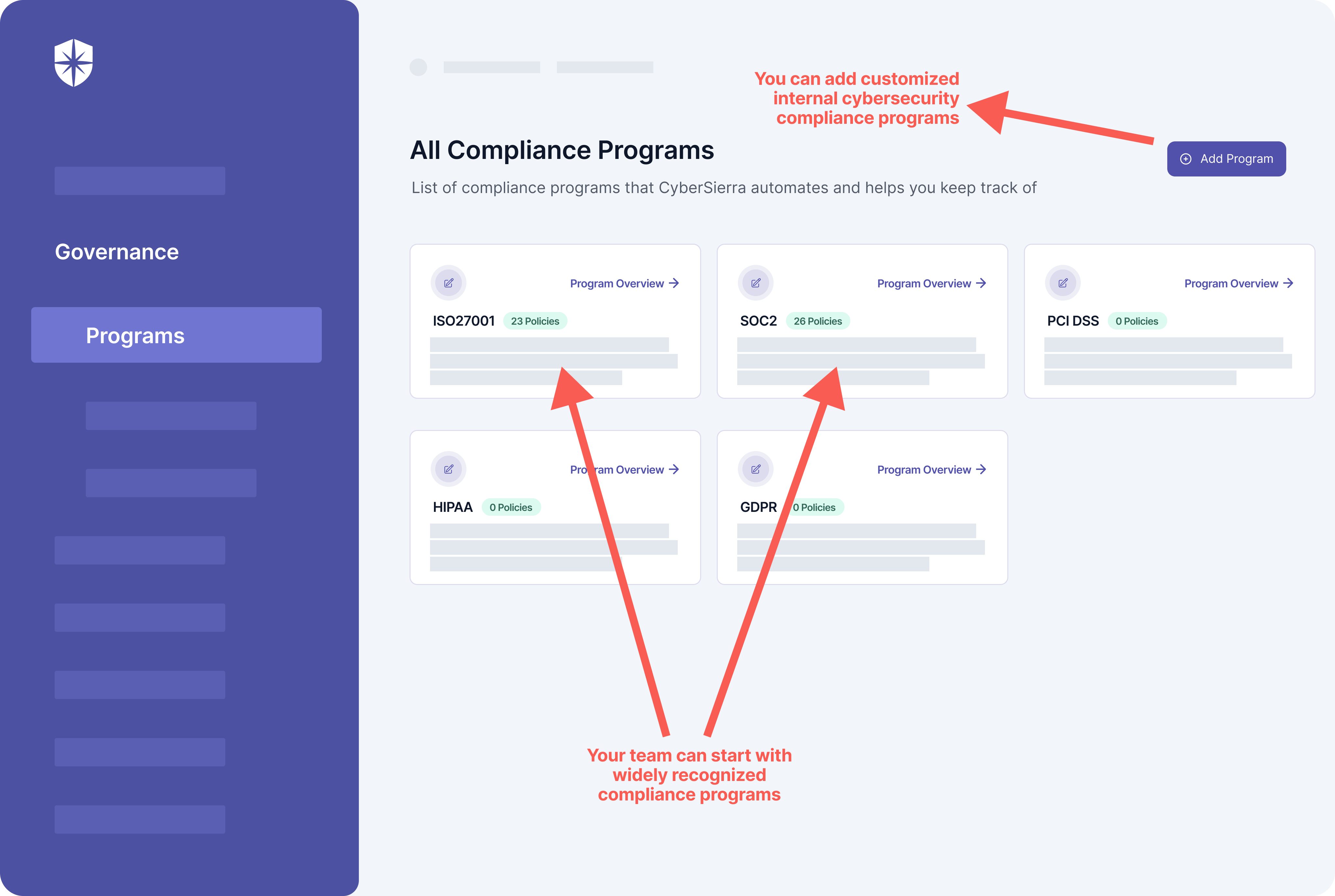
There are two main categories under the TPRM framework— 1) Tailored specifically for TPRM or Supply Chain Risk Management program (SCRM) like Shared Risk Assessment TPRM framework and NIST – 800-161. 2) Supplementary information security programs that enhance the TPRM program or assist in vendor risk management questionnaires, such as NIST CSF v1.1. ISO 27001, and ISO 27036. These standards outline building an effective infosec program by effectively managing controls associated with third-party risks.
Why do you need a TPRM Framework?
While most organizations focus on securing endpoints such as servers, routers, and firewalls mostly, it is worth noting that they are not the only threat actors. There could be potential risks from unfamiliar sources such as the networks of trusted third parties too. These connections can become the vulnerabilities that hackers use to infiltrate your defenses! Hence it is important to come up with a holistic third-party risk management framework.
By employing a TPRM framework, companies can increase their understanding of risks and gain insight into the risk profiles of their suppliers and service providers. This way, the business can make conscious decisions on whether it should partner with a given entity or terminate its relationship to safeguard its operations.
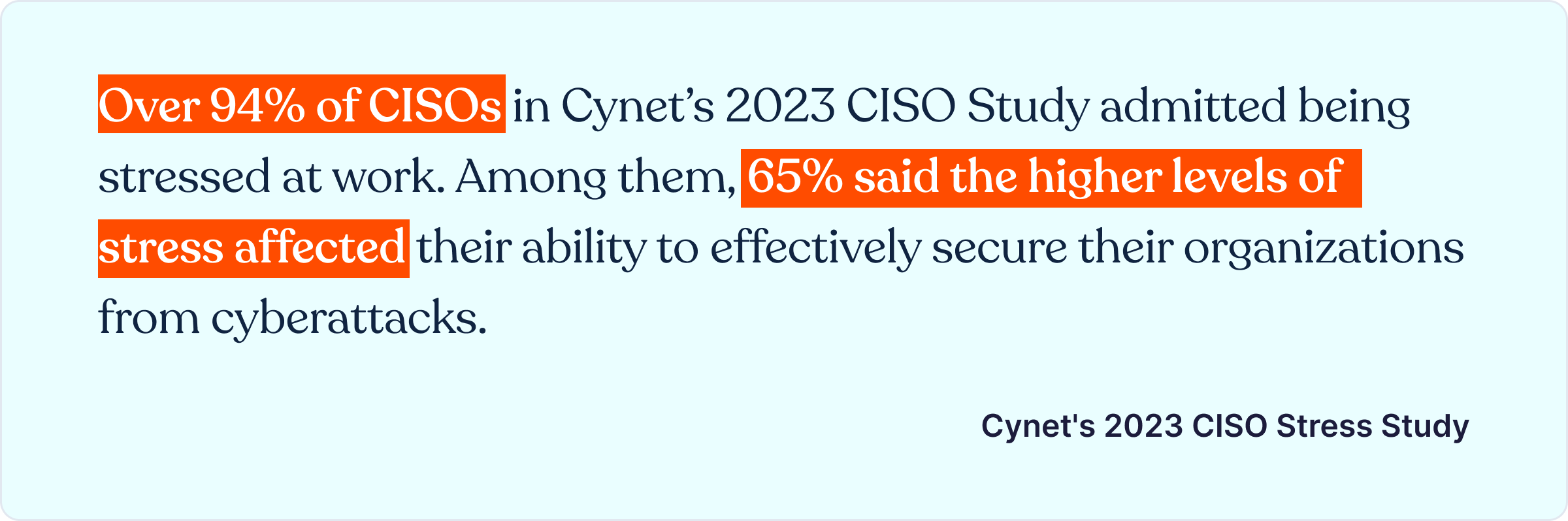
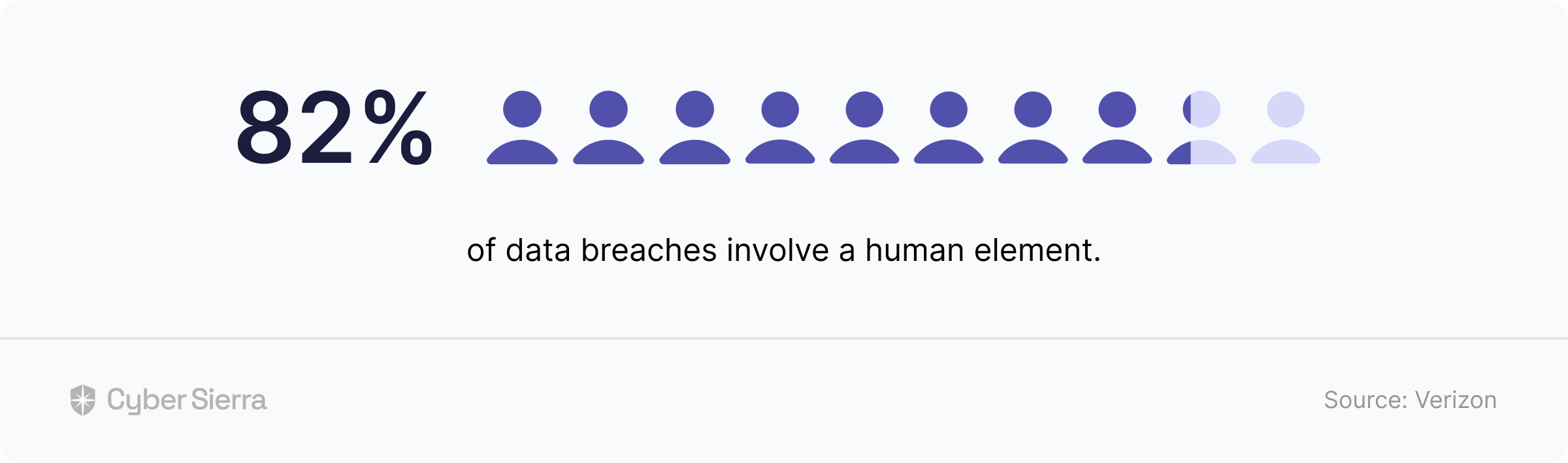
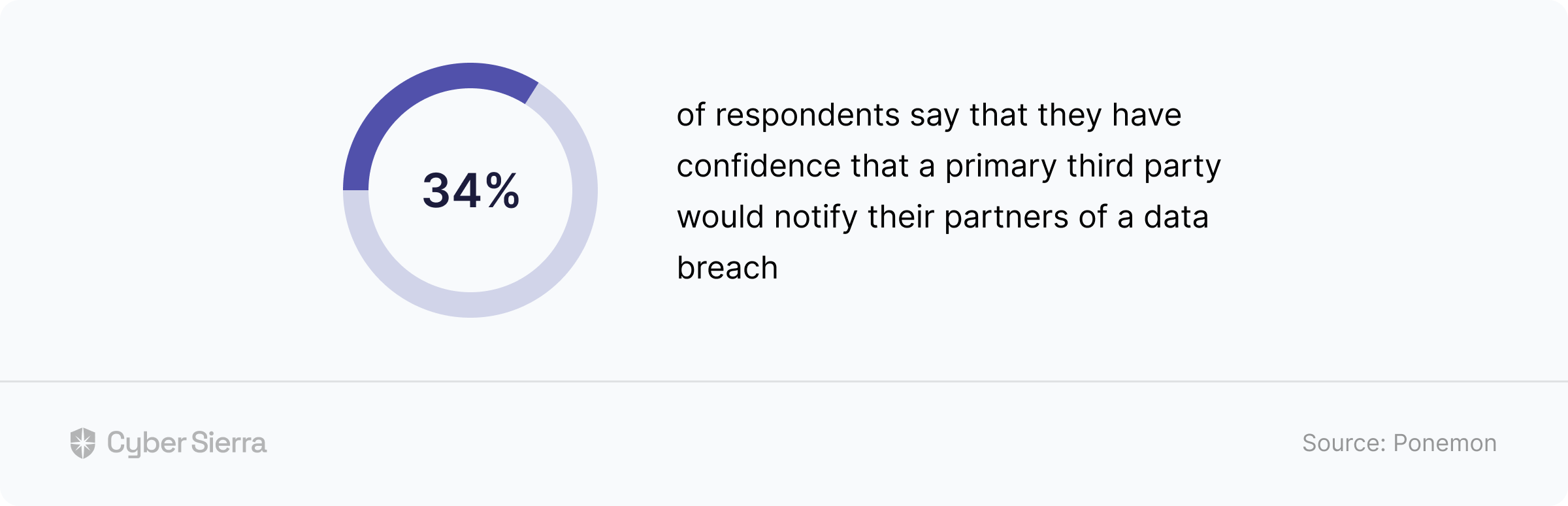
Recent research reveals that a startling 62% of data breaches originate from vulnerabilities in third-party vendor relationships. This indicates just how vital having a TPRM framework is for protecting sensitive organizational information. A properly instituted TPRM program enables organizations to consistently uncover and address potential risks, as well as provide a structured approach for developing and deploying effective risk mitigation tactics.
Regulatory bodies demand rigorous third-party risk management. Start with a thorough due diligence, meet contractual obligations, implement internal security controls, and ensure ongoing compliance with security standards throughout the vendor management lifecycle.
A comprehensive TPRM framework is an essential catalyst for meeting these requirements by providing guidelines to comply with the prescribed security standards and regulatory obligations.
Failure to mitigate third-party risks can result in legal repercussions, reputational and financial losses, and more importantly, erosion of customer trust. A TPRM framework acts as a credibility amplifier that protects your business from vendor risks, safeguards your resources and assets, and maintains your trust and reputation in your marketplace.
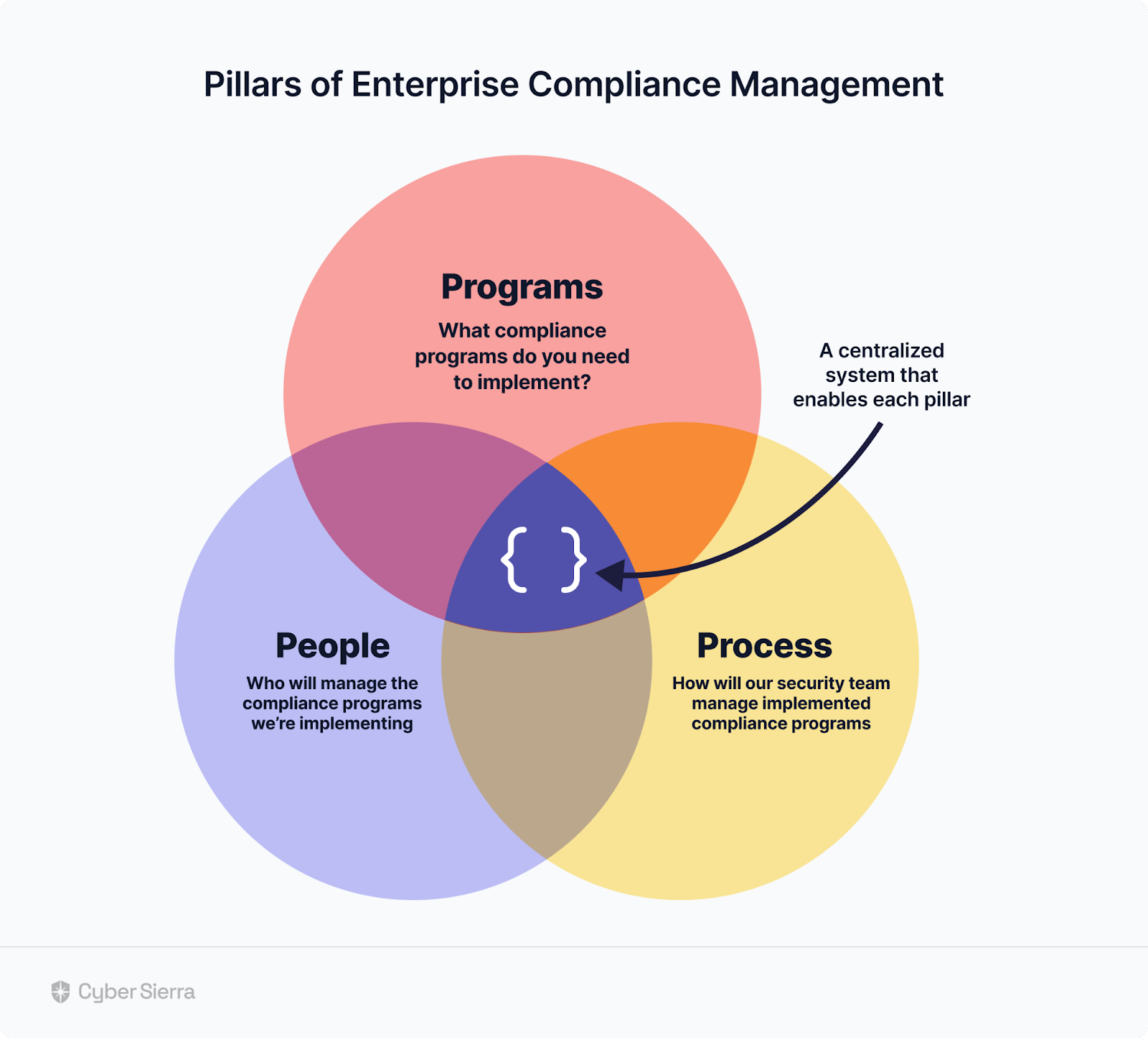
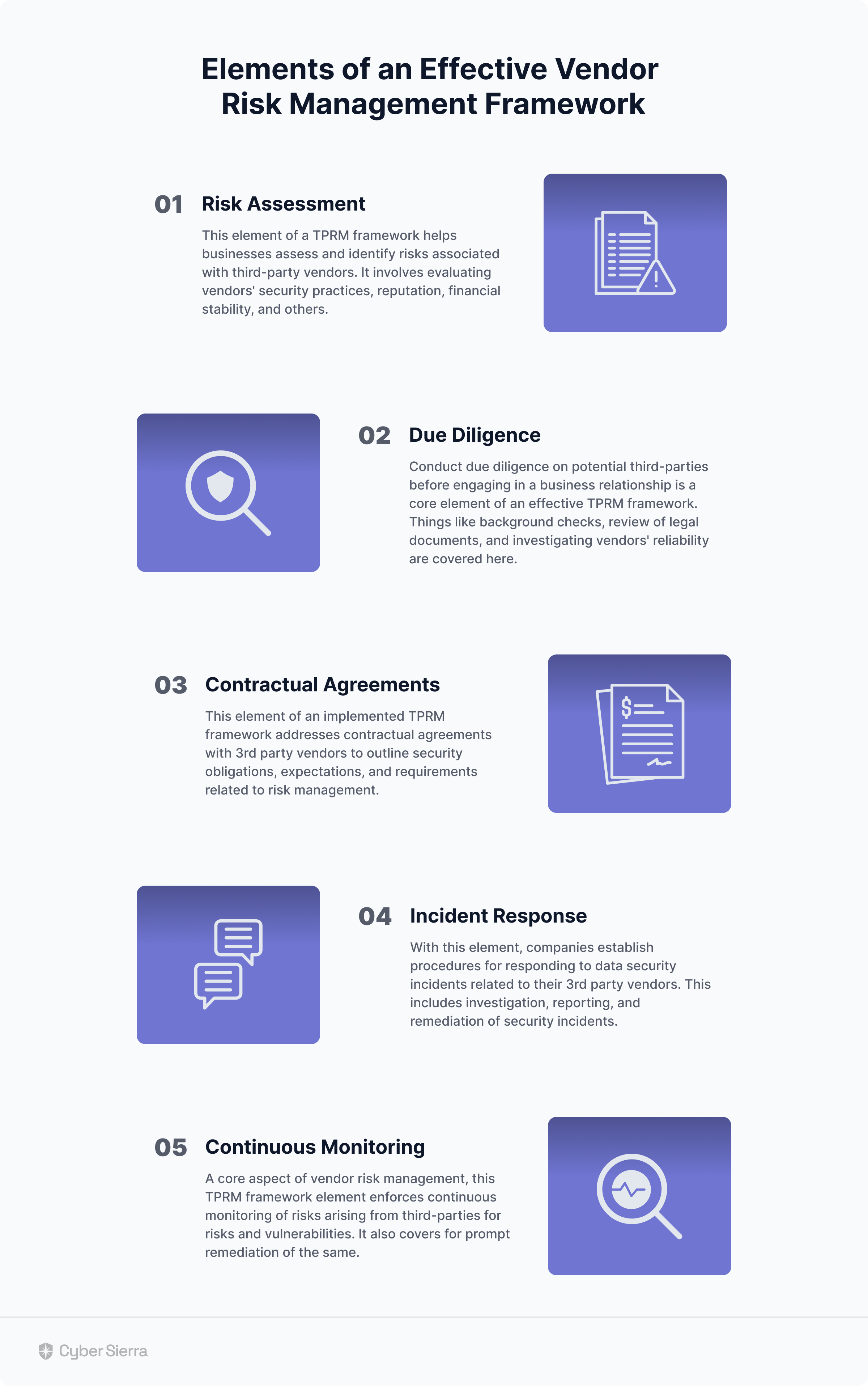
Different Components in the TPRM Framework


There is no one-size-fits-all TPRM program; you can customize your TPRM framework based on your business needs.This can be accomplished by either utilizing a TPRM automation software or developing a fully integrated risk management solution. Any effective TPRM approach should incorporate these six essential elements:
Due diligence
Third-party due diligence is a critical step in risk management, allowing companies to evaluate vendors before engaging in a business relationship. This involves conducting background checks and mitigating risks associated with conflict of interest, legal, cyber security, or compliance issues, ensuring these external partners are legitimate, reliable, and won’t harm the company’s reputation or finances.
Risk identification
The next step in choosing a TPRM framework is recognizing and assessing potential risks related to third-party vendors. Here, you evaluate the nature of the risks, such as operational, compliance, or data privacy risks, the scope of the risk, and the involved parties.
Risk assessment
Following risk identification, this phase involves determining the impact of the likelihood of identified risks. By analyzing the severity and probability of various risks, organizations can prioritize them and allocate resources accordingly to manage and mitigate the highest priority risks.
Risk monitoring
Risk monitoring is a sustained practice utilizing specialized tools and procedures to track, assess, and analyze risk factors continuously. This ongoing process enables organizations to stay abreast of changes in the risk landscape, swiftly identify emerging risks, and proactively address potential vulnerabilities in their third-party relationships.
Risk mitigation
This phase centers on mitigating identified risks to an acceptable level. Strategies may involve implementing internal controls, establishing well-defined contractual agreements, conducting routine audits, formulating contingency plans, and fostering transparent communication with third parties. The objective is to minimize the impact of risks, ensuring the ongoing integrity and security of the organization’s operations within the context of the third-party relationship.
Continuous assessment
Continuous vendor monitoring and risk assessments help you align with the industry best practices. It is essential to establish procedures for security incidents related to third-party vendors. This includes reporting, investigating, and remediating any possible security incidents.
How to Choose a Third-Party Risk Management Framework
When choosing a third-party risk management framework for your company, it’s important to carefully assess your company’s specific needs and risk exposure profile. This includes regulatory requirements, tolerance limits on risk, compliance requirements, vendor dependence, and many organizational considerations. Some key matters to consider are outlined below:
Regulatory Compliance & Risk Appetite:
- Consider the prevailing regulations in addition to your organization’s risk tolerance
- Ensure the framework aligns with regulatory requirements as well as reflects your risk appetite.
Dependence on Third Parties
- Determine to what extent your organization depends on third parties Examine growing threats related to outsourcing and usage of technologies such as cloud services.
Core Business Functions Performed by Vendors
- Understand that tasks previously handled by internal employees are now carried out by third parties.
- Be aware of how the disruptions or failures caused by vendors can affect you. Increased reliance on vendors can amplify risks
Characteristics of TPRM Frameworks to consider:
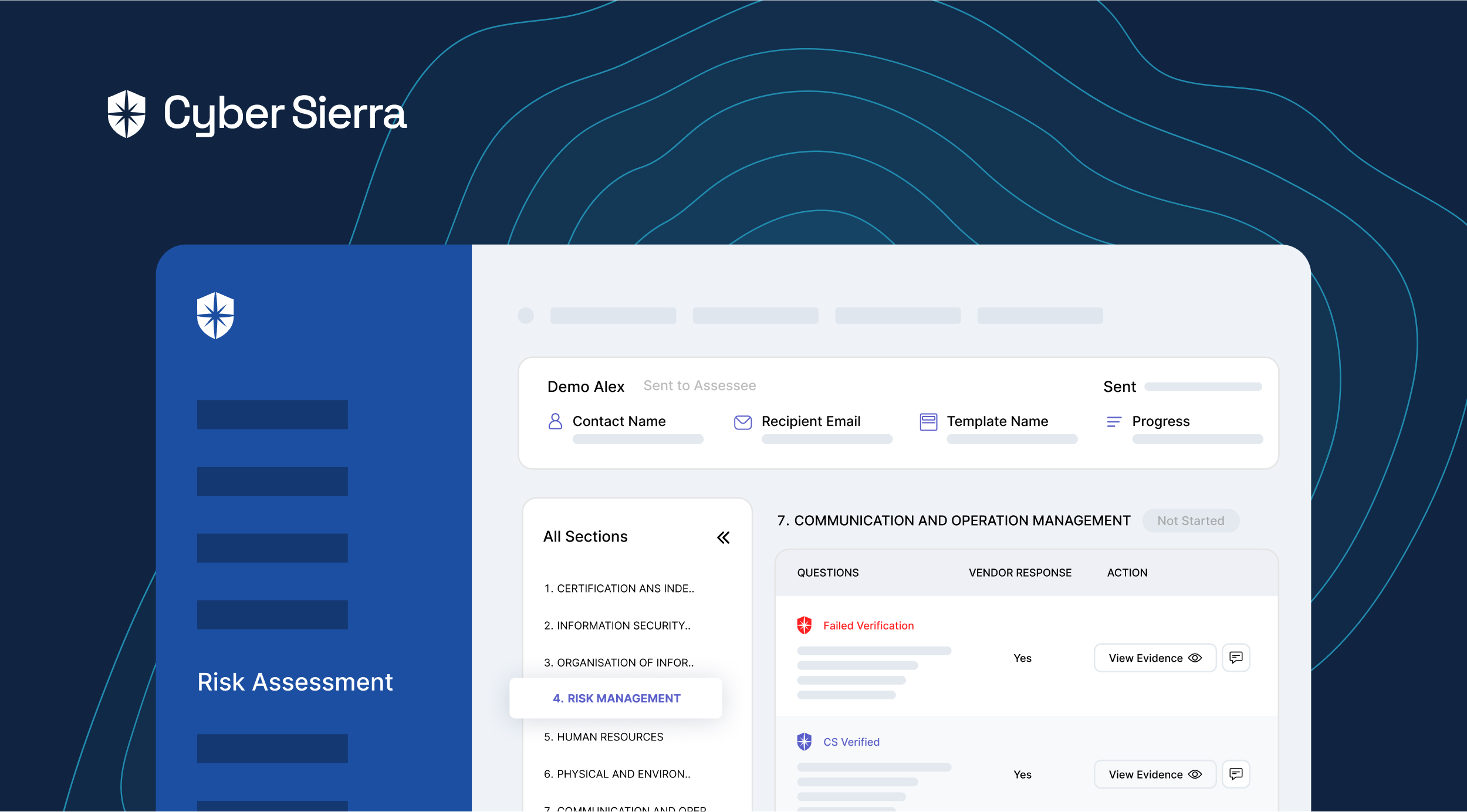
- Vendor risk assessment program: Ensure that it provides a structured approach within which vendors’ risks can be assessed using custom features based upon the nature of the relationships and the significance of services rendered.
- Third-party vulnerability detection: Look for mechanisms that identify vulnerabilities, including cybersecurity gaps, and have features that enable vulnerability scanning, penetration testing, and continuous monitoring of third-party environments.
- Compliance gap detection: Assess whether the framework enables continuous compliance monitoring with relevant regulations and industry-specific requirements. Look for functionalities that identify compliance gaps and deviations from established standards.
- Risk assessment questionnaire: Evaluate if the framework offers automation capabilities for administering security questionnaires and collecting information from third-party vendors. Look for functionalities that streamline the assessment process, automate responses, and provide detailed risk analyses.
- Remediation program: Check if the framework supports developing and implementing remediation plans to address identified risks and vulnerabilities. Check for availability of features that facilitate stakeholder collaboration, tracking of remediation progress, and help prioritize corrective actions based on risk severity.
- Reporting: Ensure the framework includes reporting capabilities to communicate TPRM activities to stakeholders. Look for customizable reporting templates, dashboards, and metrics that provide insights into risk exposure and mitigation efforts.
Some cyber frameworks that align well with TPRM requirements and security controls include NIST CSF, ISO 27001, ISO 27002, ISO 27019, ISO 27036, and NIST RMF 800-37. These frameworks provide structured approaches to addressing cybersecurity risks and can be tailored to support your organization’s third-party risk management initiatives. By taking into account these elements and establishing a robust TPRM framework, organizations can adeptly handle third-party risks while optimizing the value gained from these partnerships.
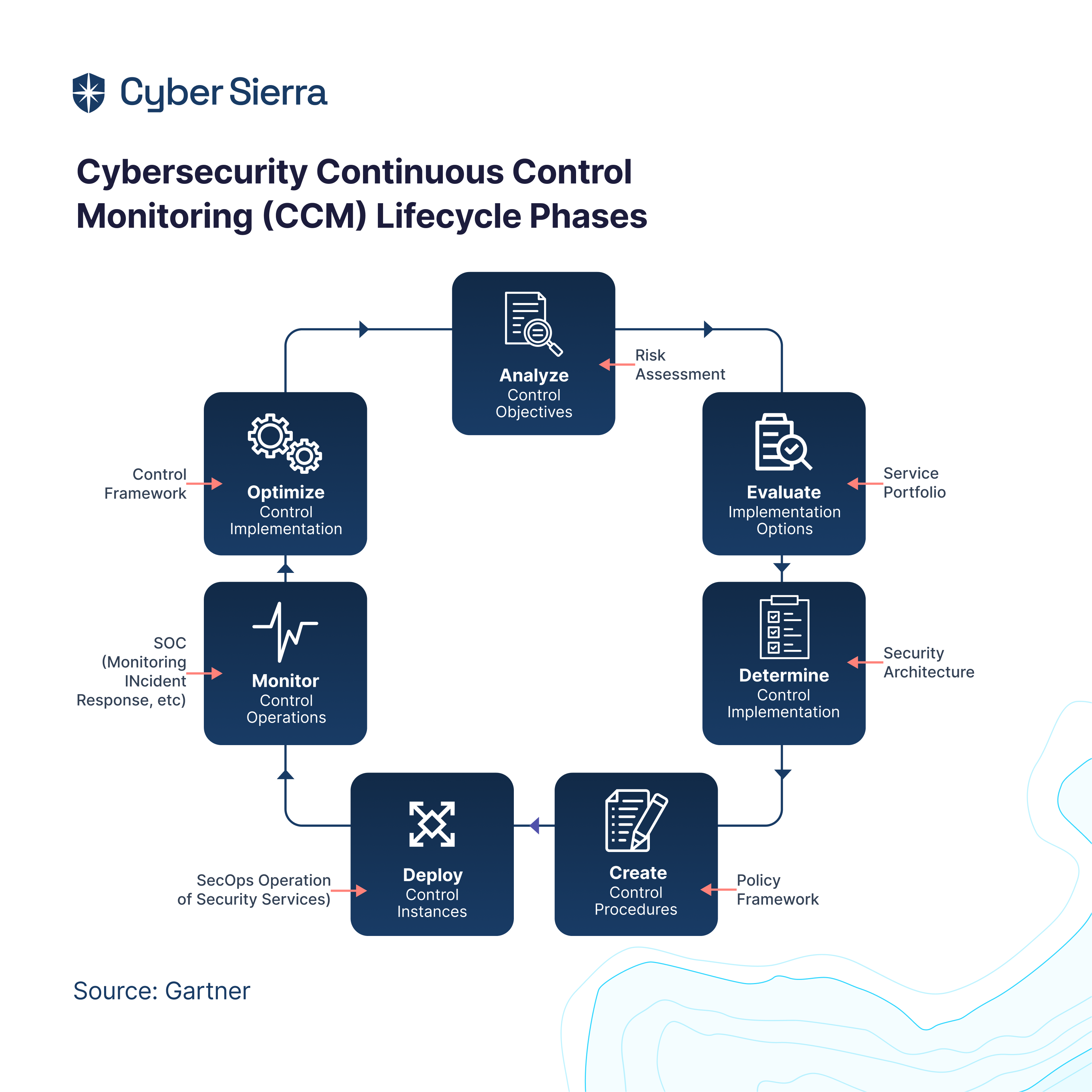
How to Create a TPRM Framework

A strong third-party risk management framework helps avoid potential hazards and ensures vendor complexities do not derail a business. It safeguards assets, ensures regulatory compliance, and protects the company’s reputation. Here is an easy process for creating a third-party risk management framework:
1. Engage your stakeholders
The first step towards developing the TPRM framework is putting together a cross-functional team. It’s important to involve representatives from departments like risk management, operations, procurement, finance, IT, cybersecurity, legal, and compliance. This achieves alignment and allows each group to contribute their perspective and expertise in managing vendor risks effectively.
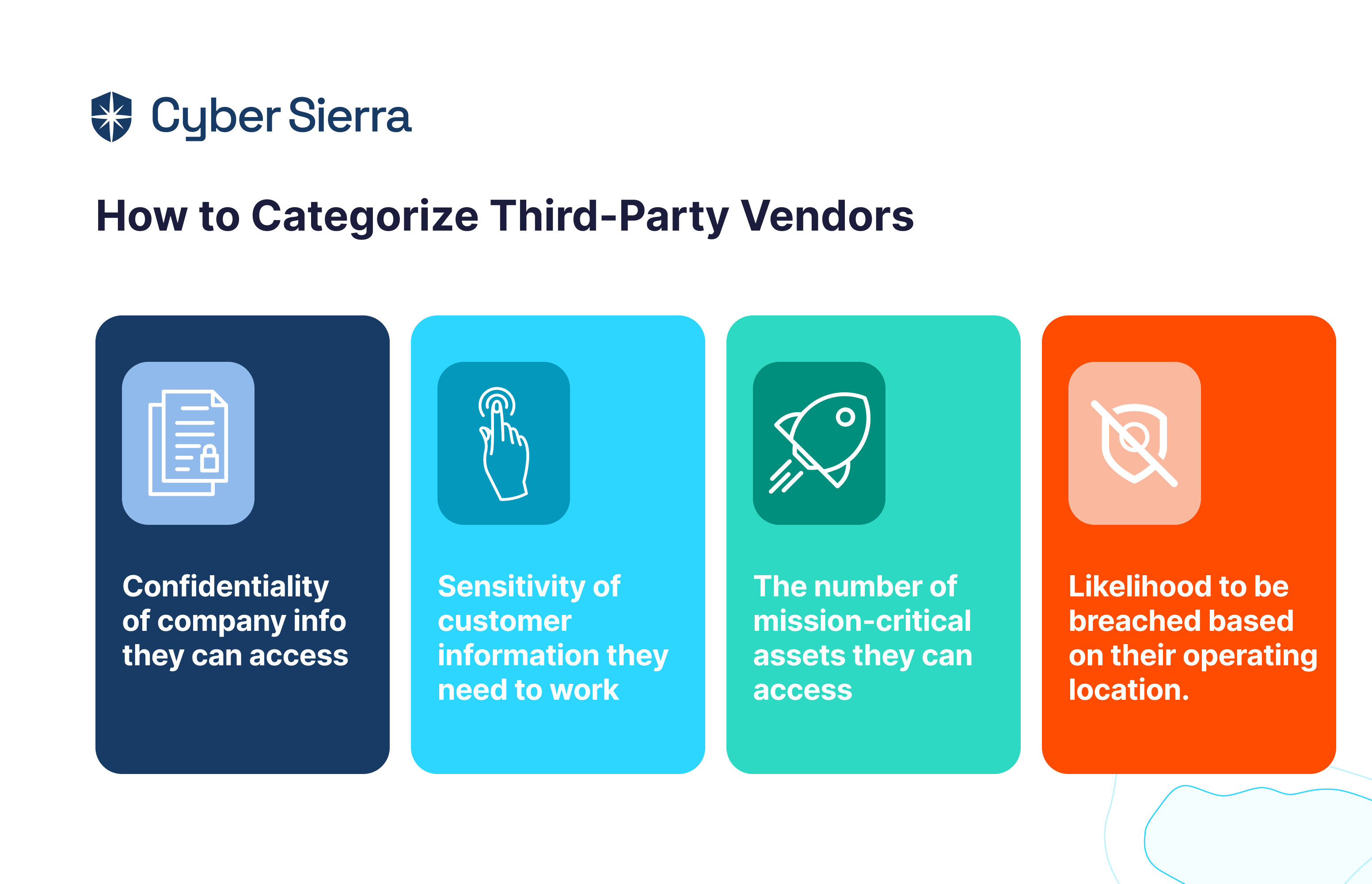
2. Group your third-parties
List down all your third-party service providers. Categorize them based on—the nature of the service or product offered, types of data accessed, the extent of data access and its necessity, and any fourth-party providers availed by the vendor.
Evaluate how important each third-party relationship is for the accomplishment of your organization’s goals. Also, consider geographic location of vendors for regulatory differences or geopolitical instability.
3. Define scope and risk tolerance
After thoroughly categorizing the vendors, define the scope of the TPRM framework by identifying the type of third parties involved and the risk factors to be considered. In addition, determine the organization’s acceptable level of risks.
Determine the organization’s risk appetite and tolerance levels, including cybersecurity, compliance, and operational disruptions. Account for industry-specific regulations and standards when defining the scope of the TPRM framework.
You can implement a risk matrix to categorize all the identified risks based on their criticality. This allows identifying risk thresholds.
4. Establish a TPRM process
Start by drafting vendor onboarding guidelines and pre-screening processing to categorize the vendors per their risk profile. Establish third-party risk assessment questionnaires to gather information on vendors’ internal controls, security practices, compliance, and industry-specific standards and best practices.
These questionnaires should cover areas like data encryption, access controls, regulatory compliance, and financial health, aligning with your organizational needs. Standardized or customized questionnaires can be used depending on our preferences and prevailing practices in our industry.
5. Risk identification and mitigation
Implementing a strong TPRM framework requires identifying and assessing risks systematically. This involves categorizing risks based on their potential impact and likelihood, and then conducting assessments to prioritize mitigation efforts.
Next, effective mitigation strategies, such as implementing security controls or enhancing contractual provisions, are defined. By following these steps, organizations can proactively manage third-party risks and safeguard their operations.
6. Due diligence
Before entering into third-party relationships, you must carry out a robust due diligence to thoroughly assess potential partners’ suitability and reliability. This involves monitoring and evaluating vendor performance, verifying their compliance with the required regulations, and adherence to contractual obligations. By staying vigilant and proactive in vendor management, organizations can develop fruitful partnerships and effectively mitigate risks over time.
7. Incident response plans
Develop corrective action or incident response plans to address security and data breaches, or other incidents involving third-party vendors. Also, establish business continuity and contingency plans to mitigate the impact on organizational operations, in the event of such disruptions or failures in third-party relationships.
8. Compliance
Ensure compliance with the applicable laws and regulations, industry benchmarks, and contractual obligations governing your third-party relationships. Establish open channels of communication with stakeholders, such as executive management, board members, and regulators on TPRM activities, results and risk status.
9. Continuous improvement
Ongoing monitoring and evaluation mechanisms must be implemented for the TPRM framework. This helps in identifying lessons learned from past experiences and highlights emerging risks or changes in the business environment to enhance policies, procedures, and risk assessment methodologies.
10. Training
Develop training modules and awareness sessions to educate employees about their roles and responsibilities in managing third-party risks. Doing this fosters a security-first culture and promotes risk awareness and accountability throughout the organization.
Best practices to maintain third-party risk management framework

A TPRM framework requires continuous monitoring and adoption to changing business conditions. Essential practices to ensure effective risk management in vendor relationships includes:
Develop standards and frameworks for third-party monitoring
- Establish standardized operating procedures to be used throughout the organization.
- Utilize established risk management frameworks such as NIST and ISO to complement the assessment process and ensure comprehensive coverage of third-party risks.
Risk cataloging and assessment
- Catalog cybersecurity risks posed by third-party vendors and assess them based on potential impact and likelihood.
- Adjust risk profiles per the changes in vendor operations, the scope of services provided, or any relevant regulations.
- Segment vendors based on identified risks and prioritize mitigation efforts according to your organization’s risk appetite.
Conduct due diligence
- Conduct annual audits to review the effectiveness of your risk management efforts
- Compare performance against pre-defined risk tolerance thresholds.
- Identify key security controls and monitor its adherence by the vendors.
Continuous improvement
- Implement mechanisms to monitor third-party relationships, including performance, compliance, and risk indicators.
- Develop incident response plans to ensure effective responses to security breaches or other incidents involving third-party vendors.
- Provide training programs to educate employees and stakeholders on TPRM best practices and emerging risks.
Utilize automation tools for improvement
- Leverage technology to automate evaluations and oversights, where possible.
- Ensure continuous monitoring and improvement of third-party management processes.
- Establish clear success criteria aligned to the level of risk tolerance.
- Act on lessons and observations from incidents, audit findings, or best practices in the industry to strengthen due diligence processes.
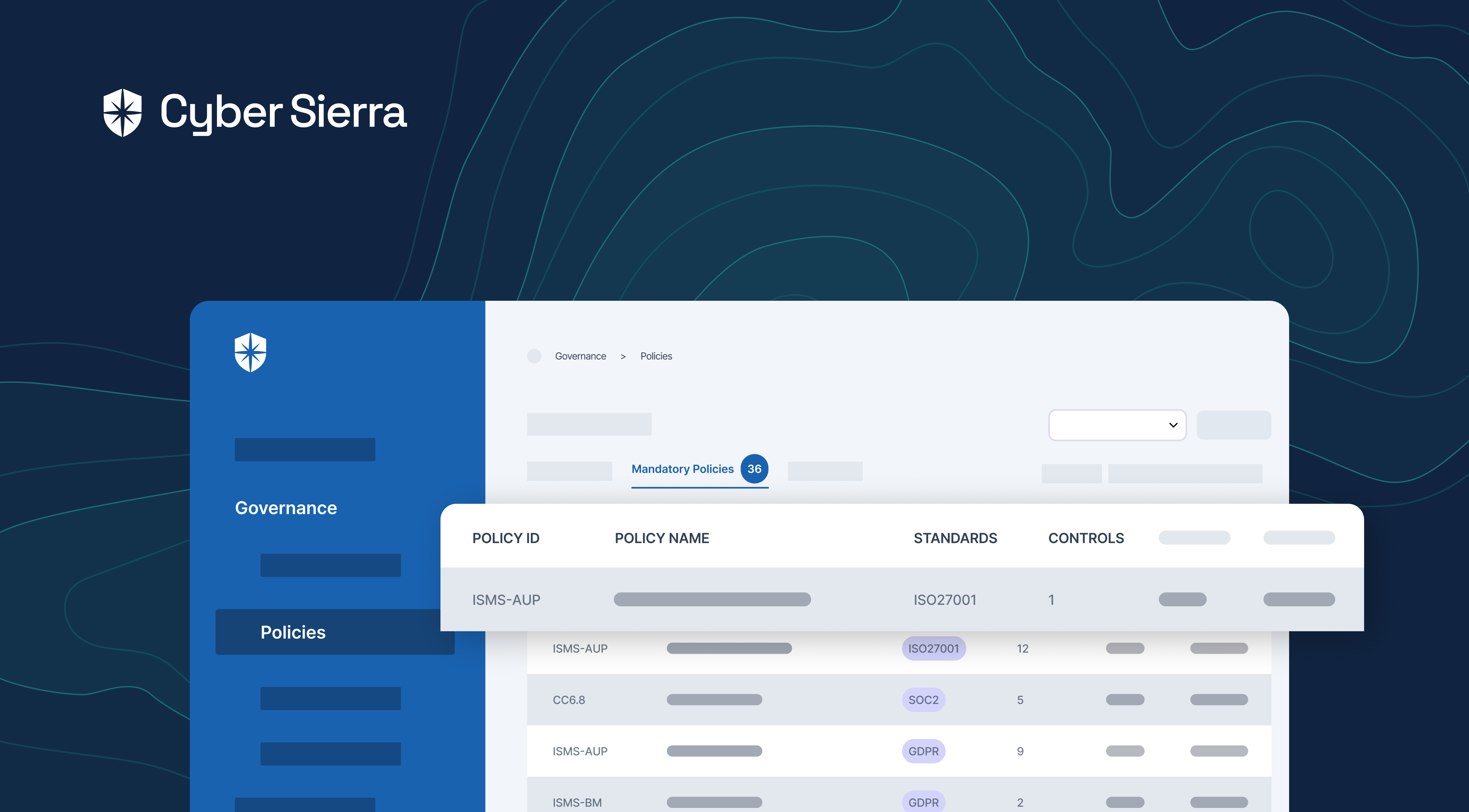
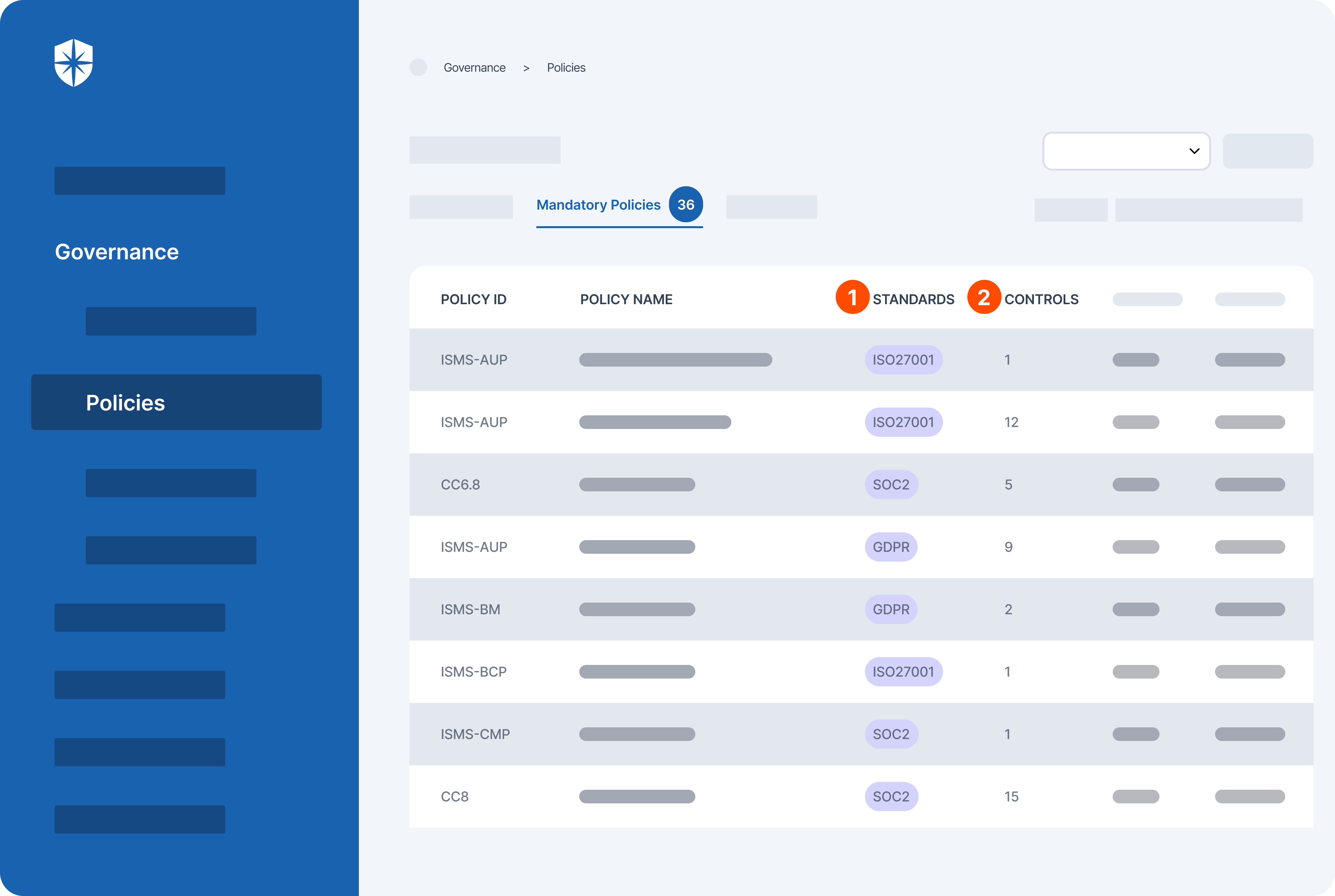
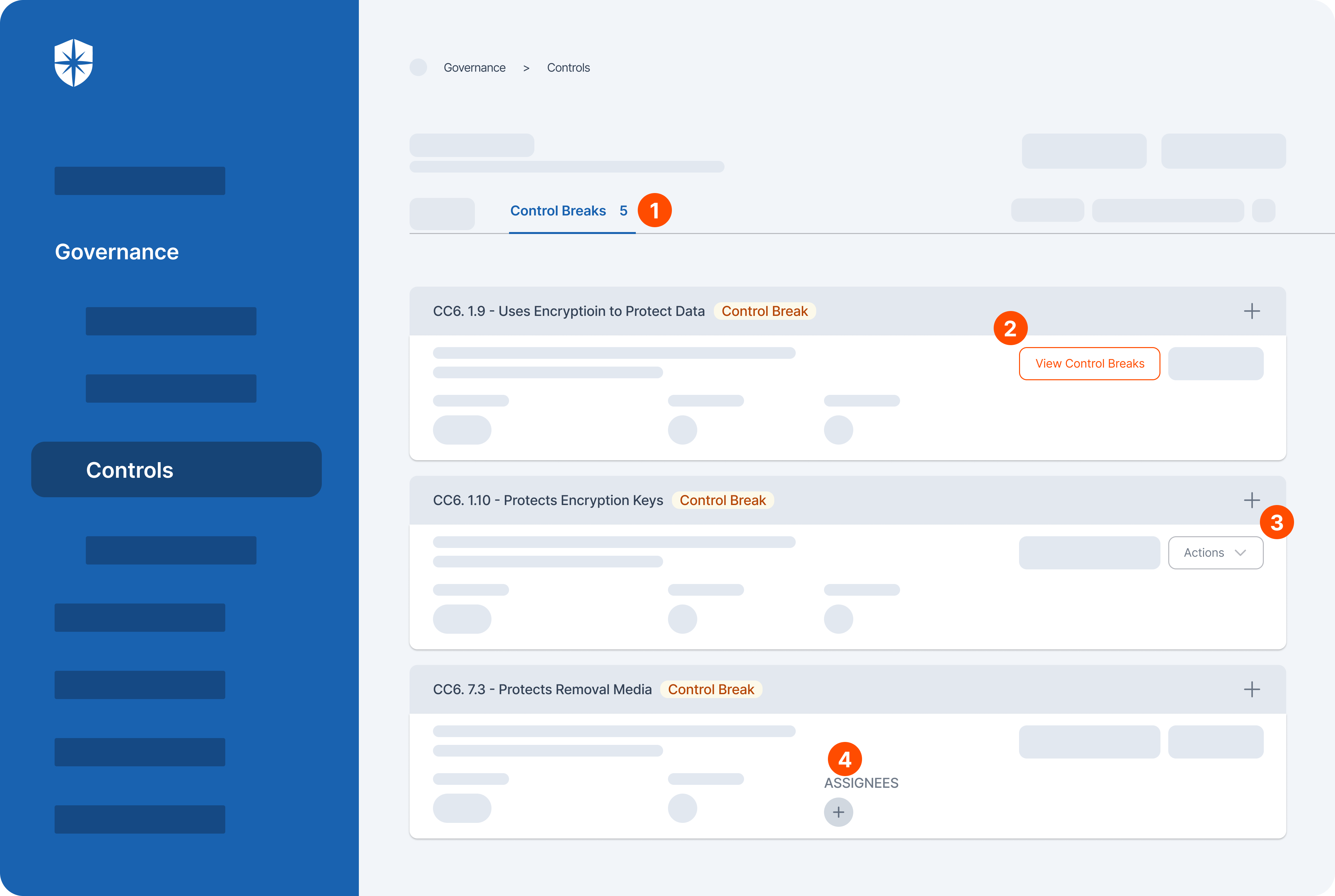
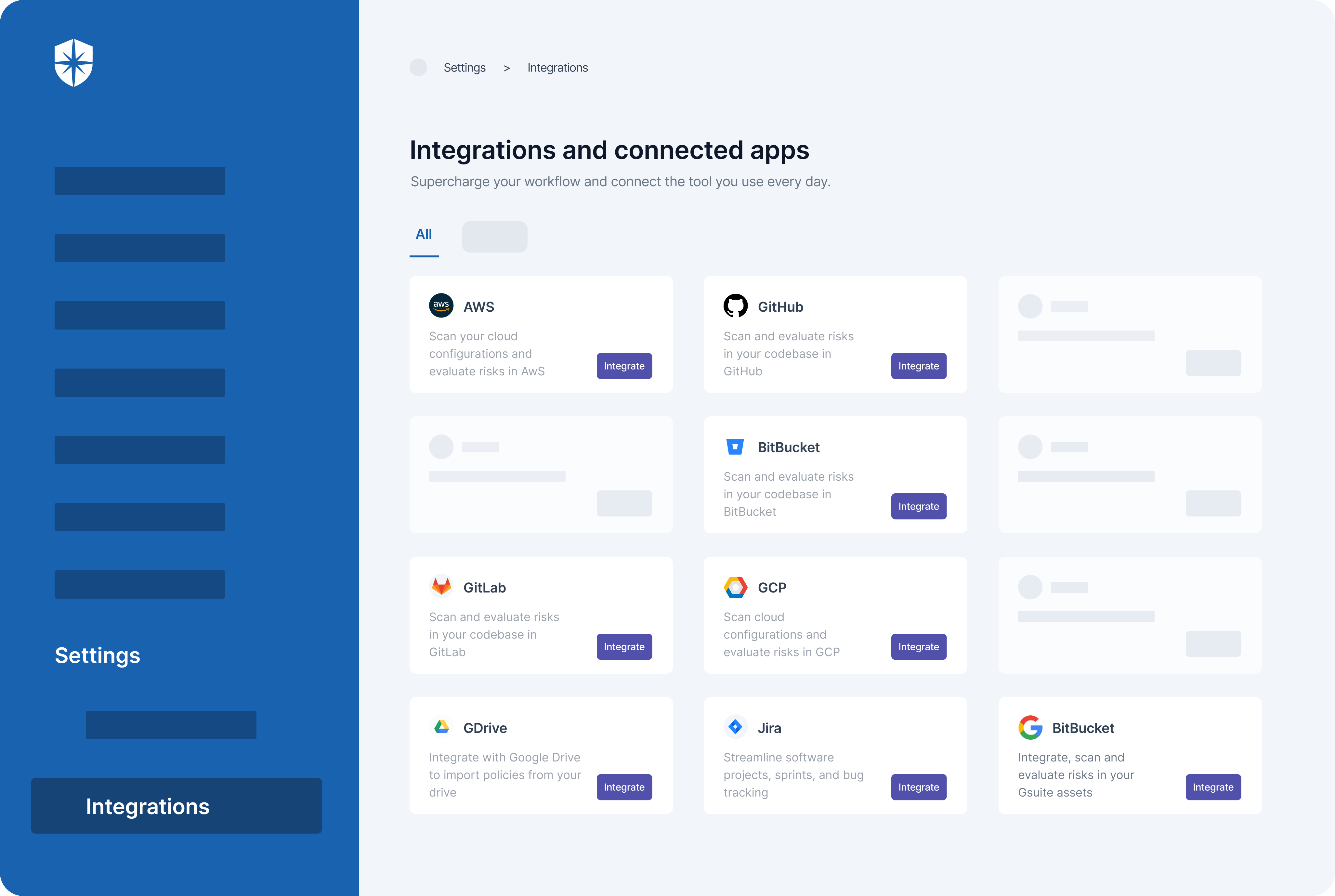
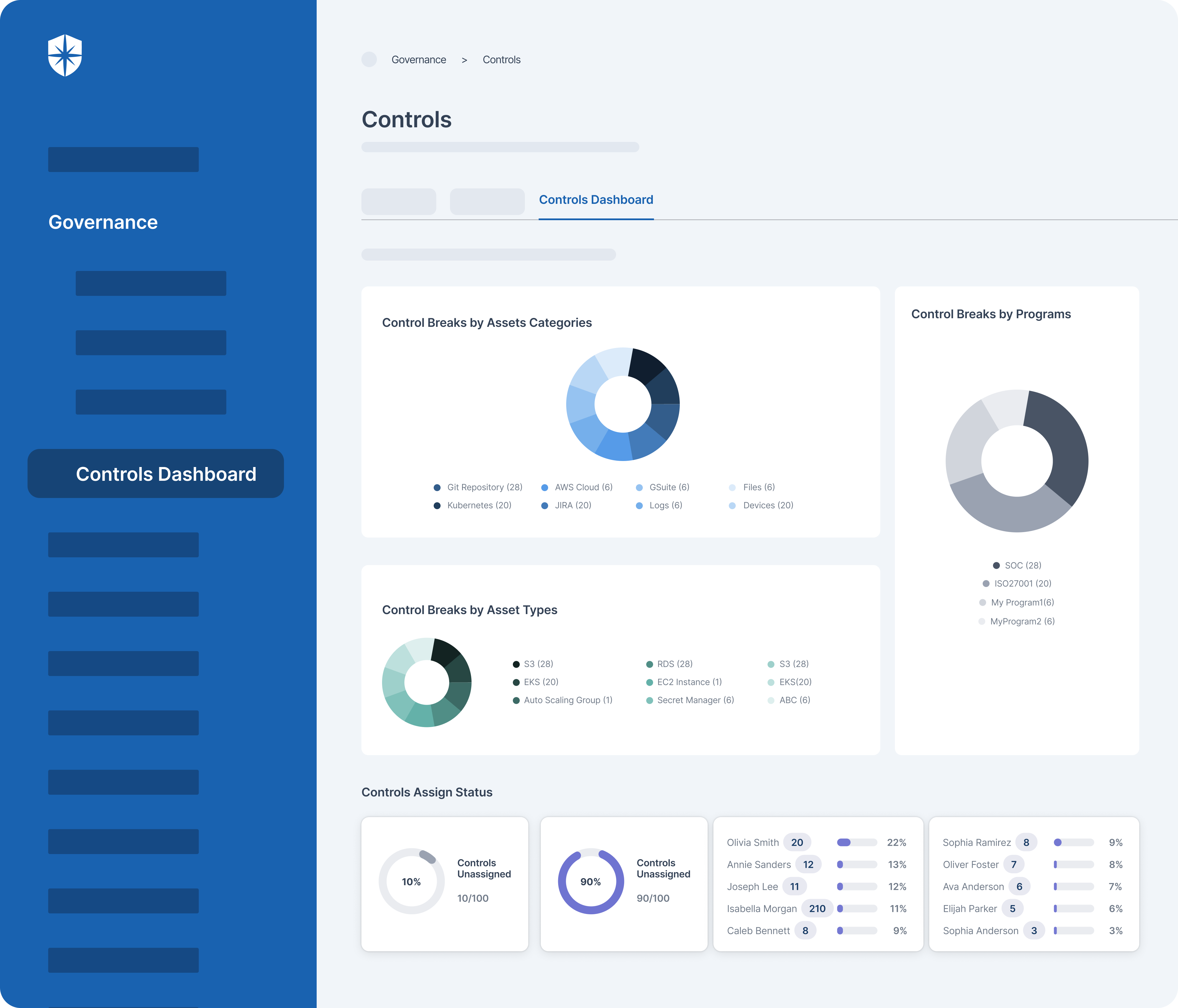
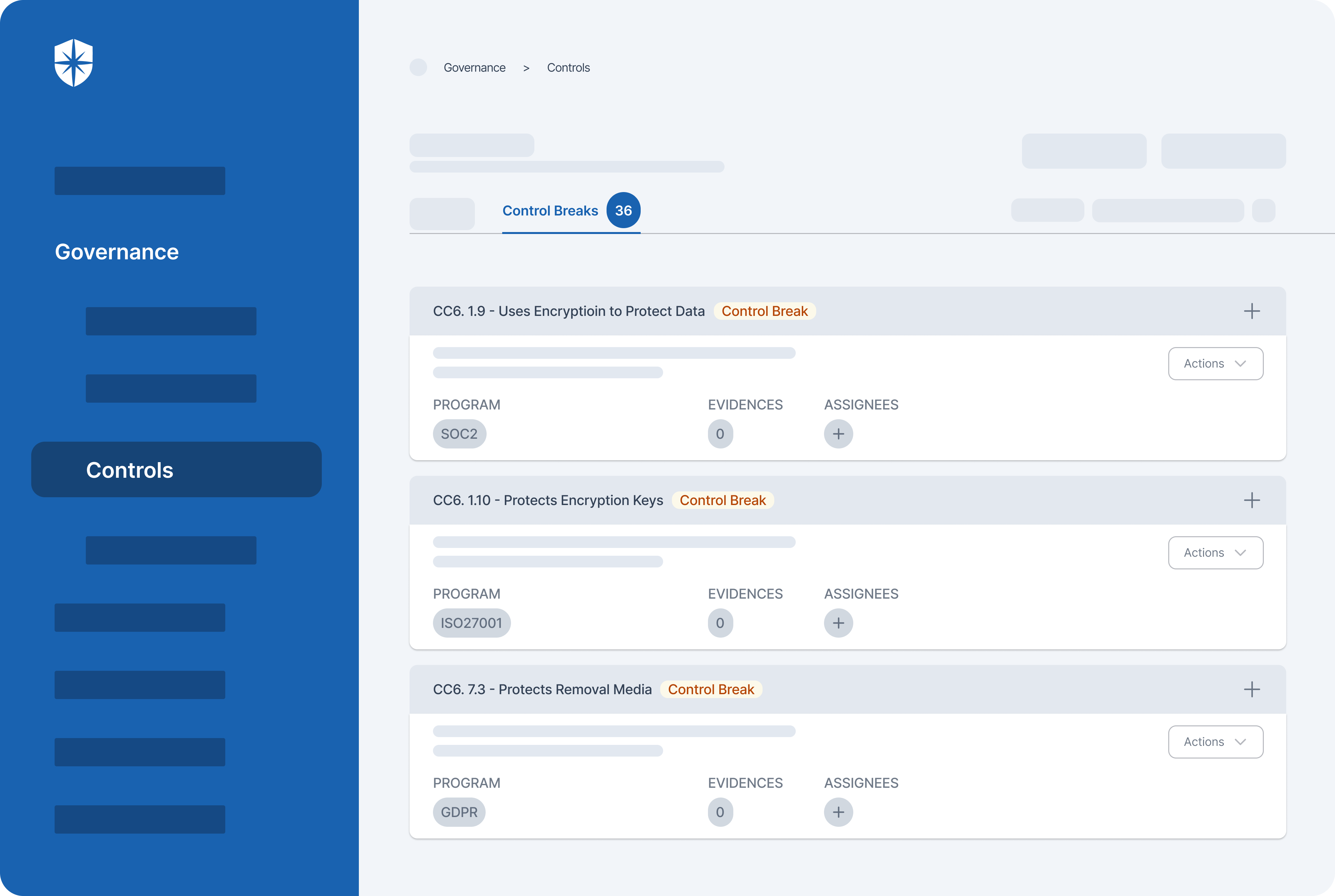
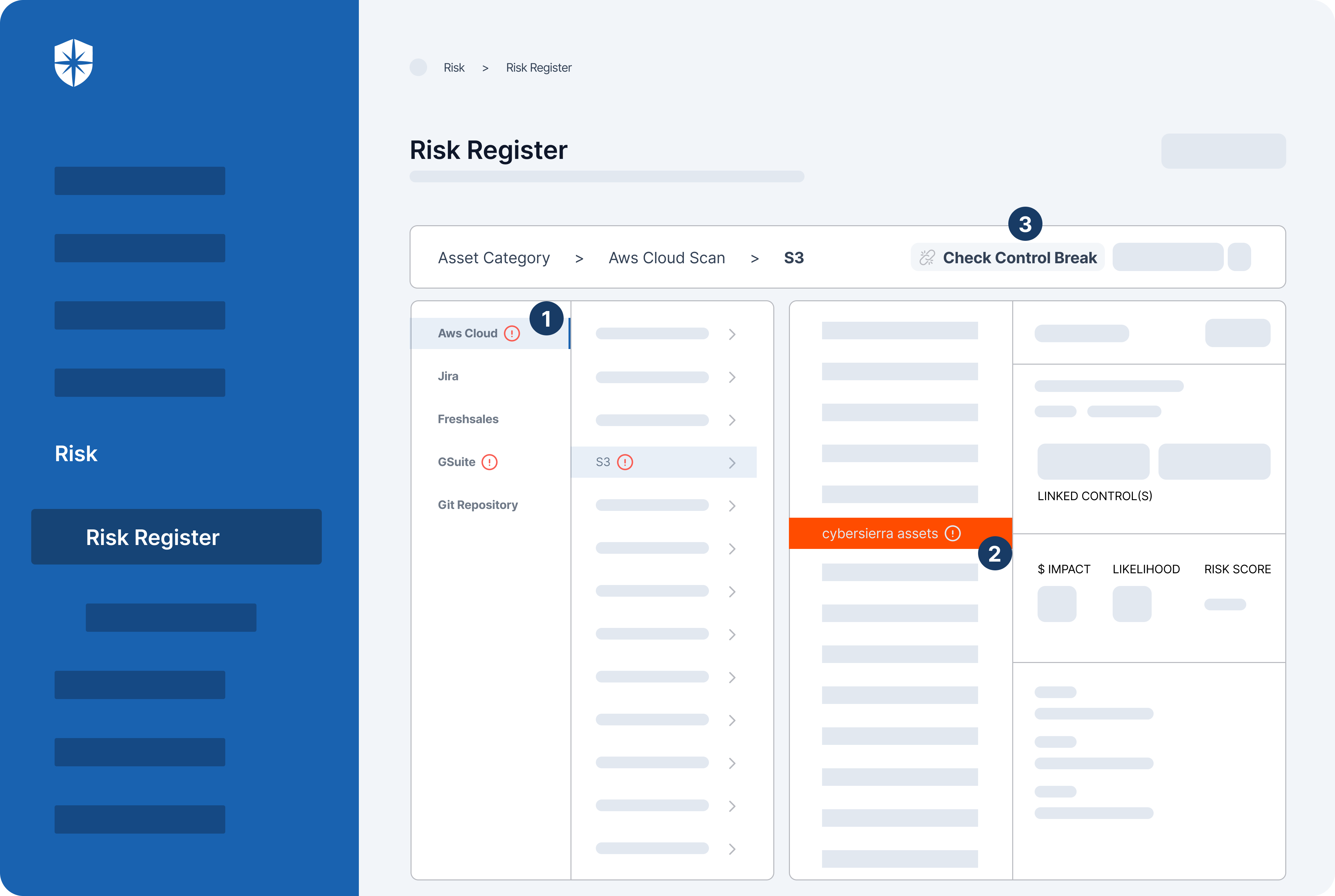
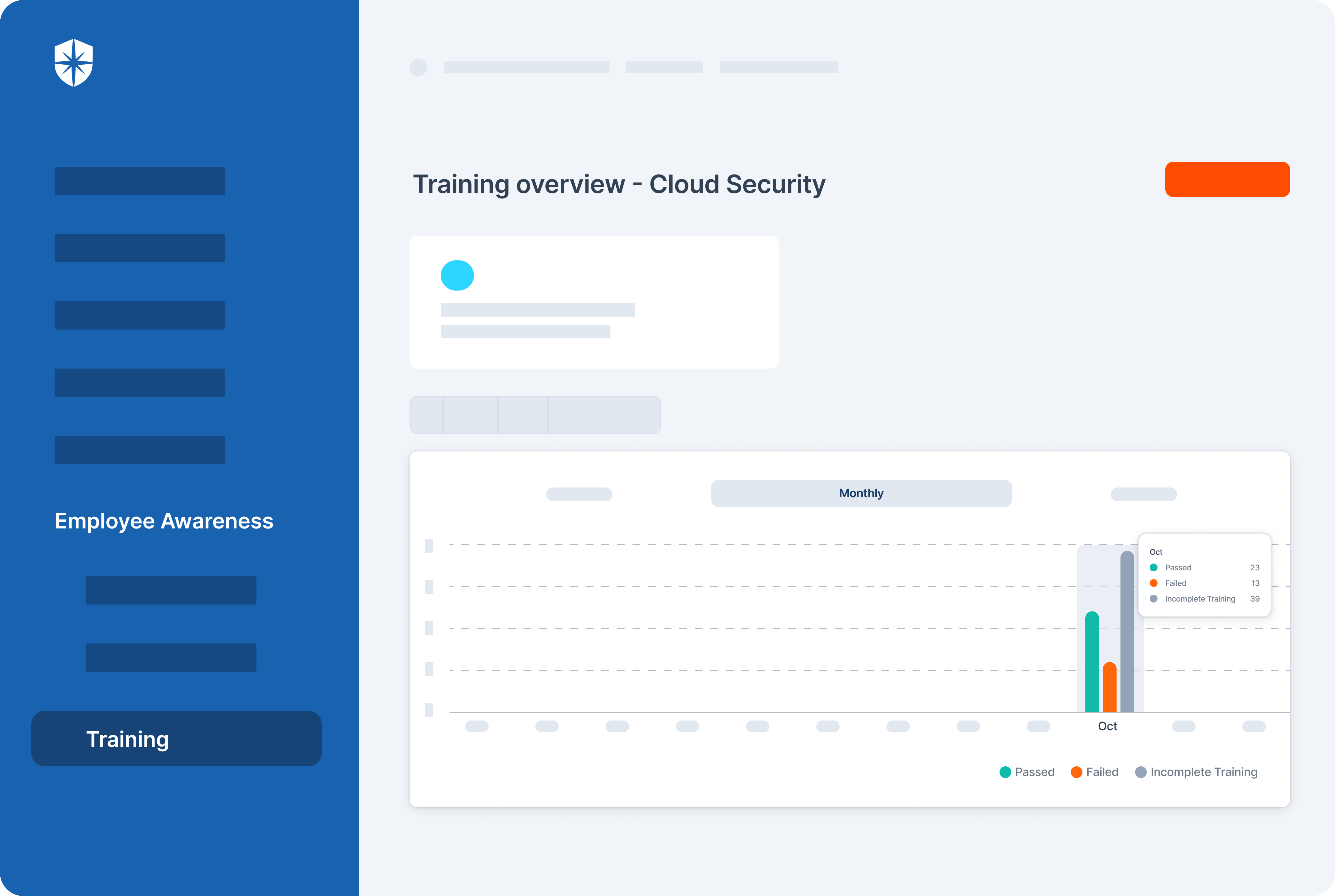
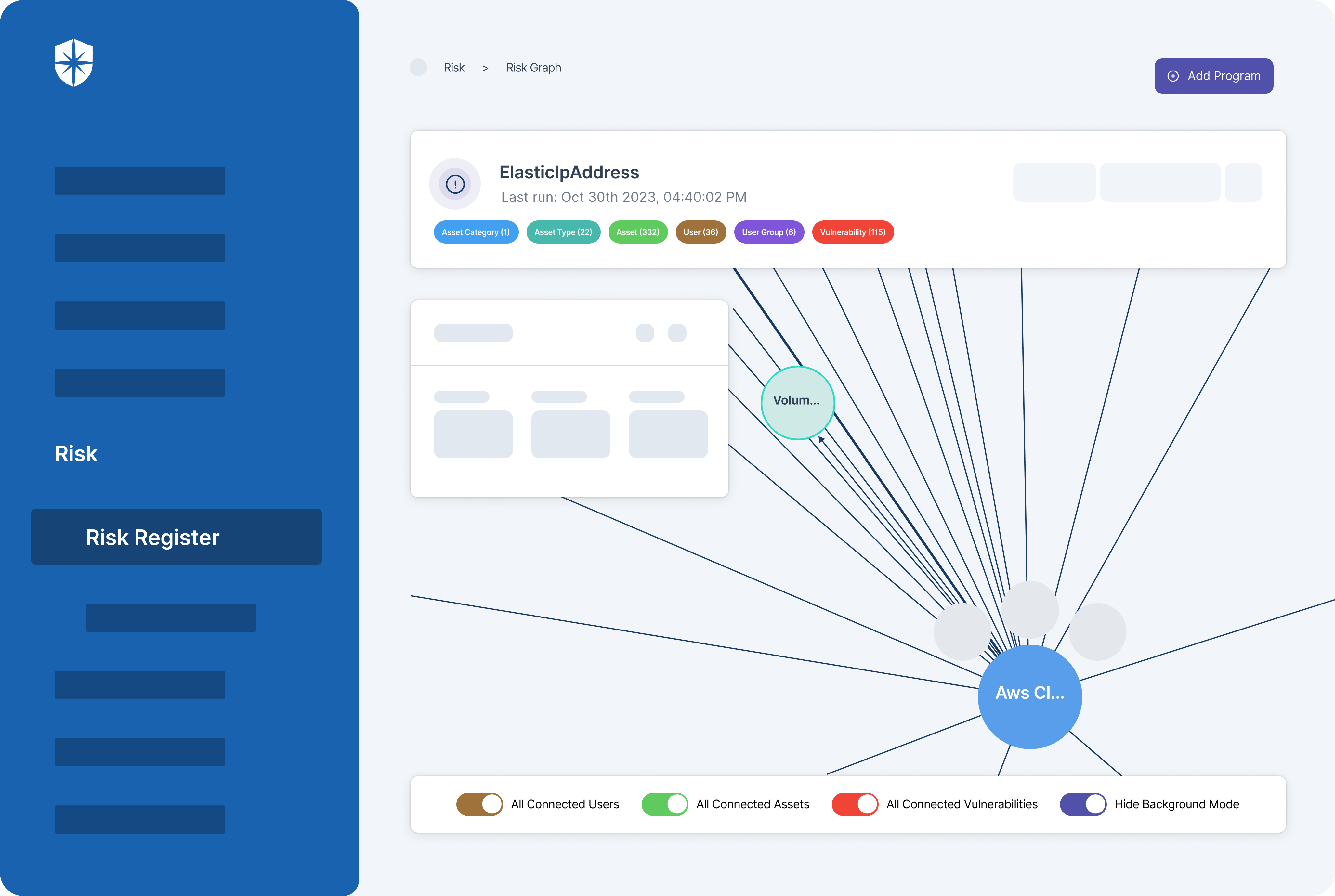
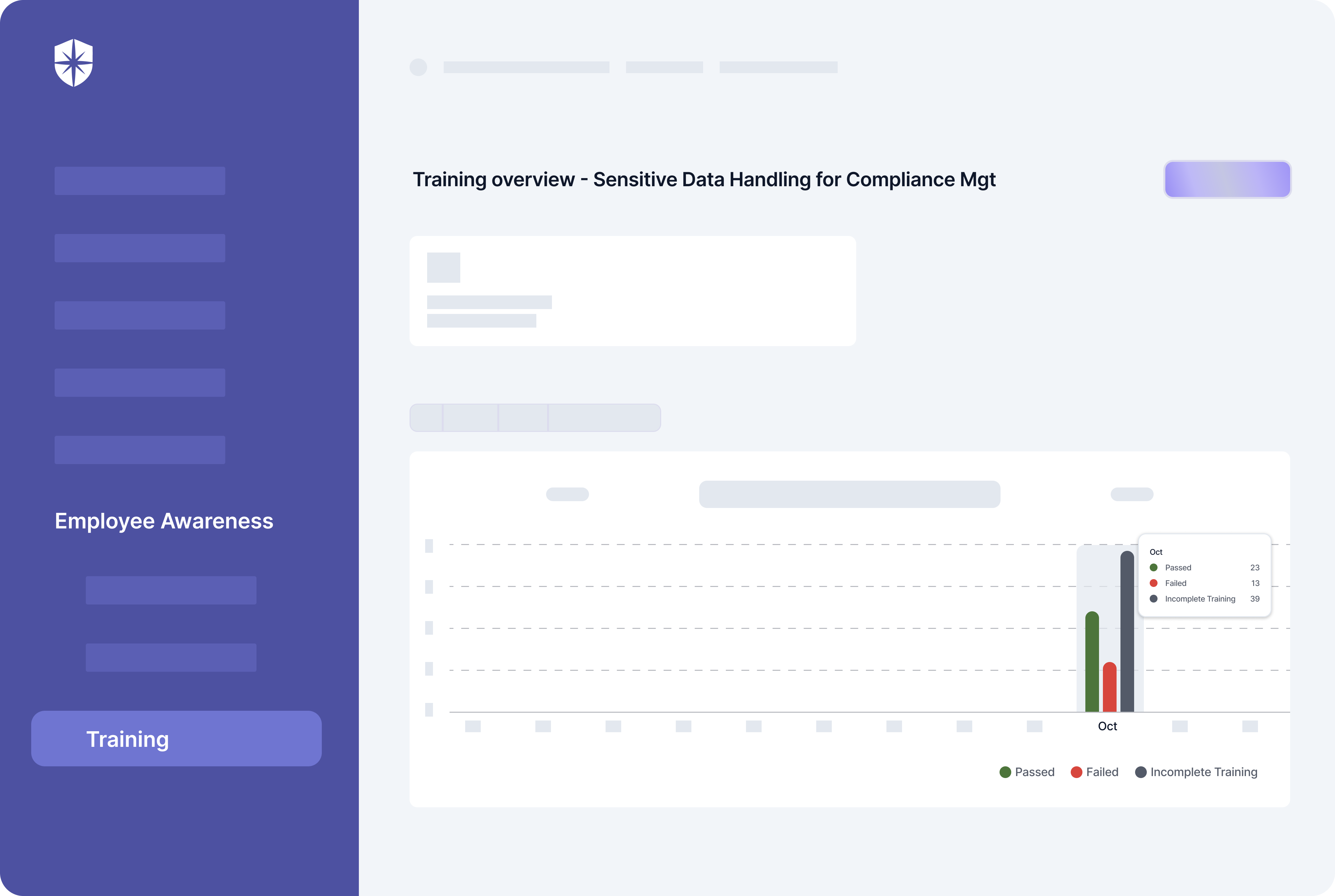
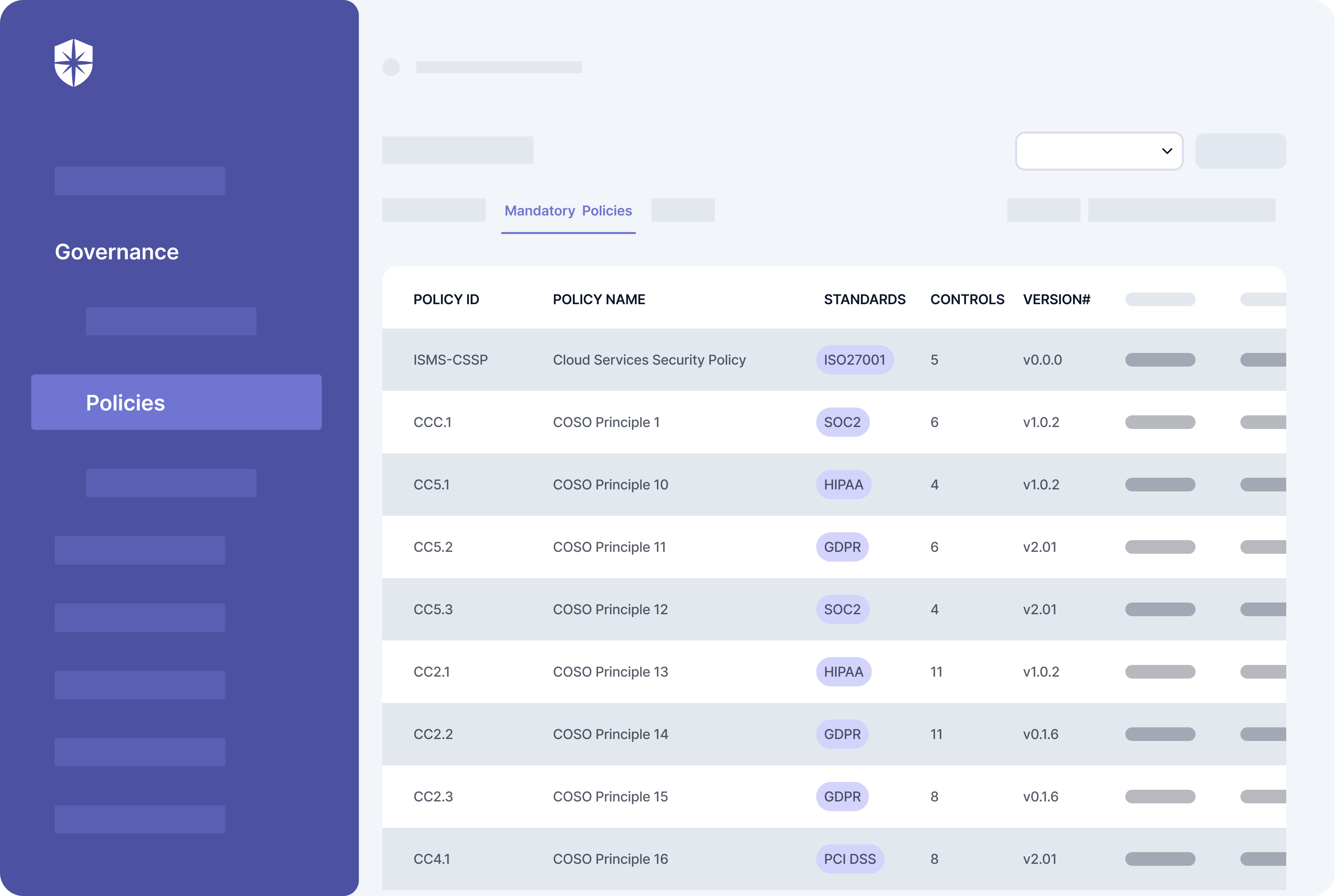
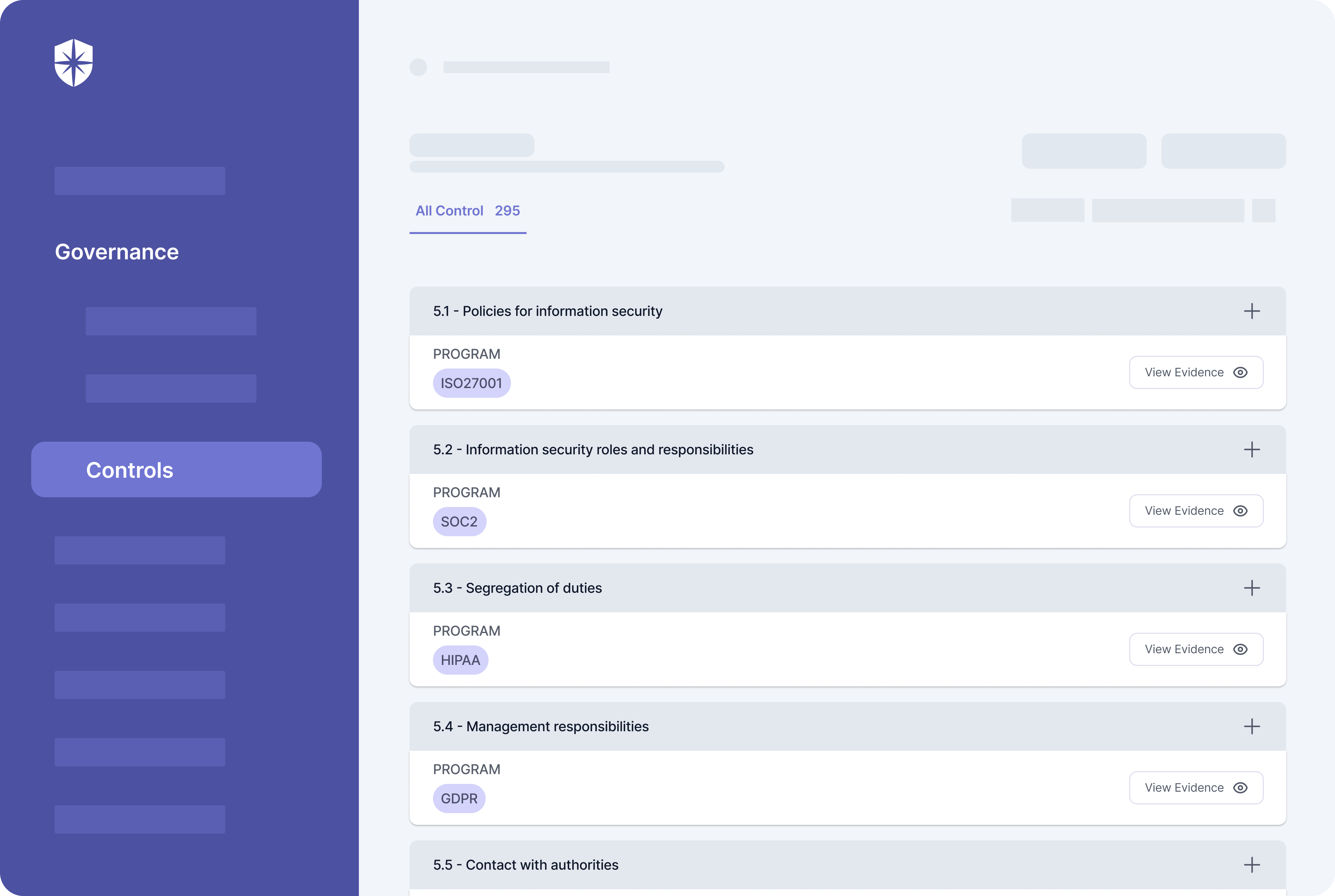
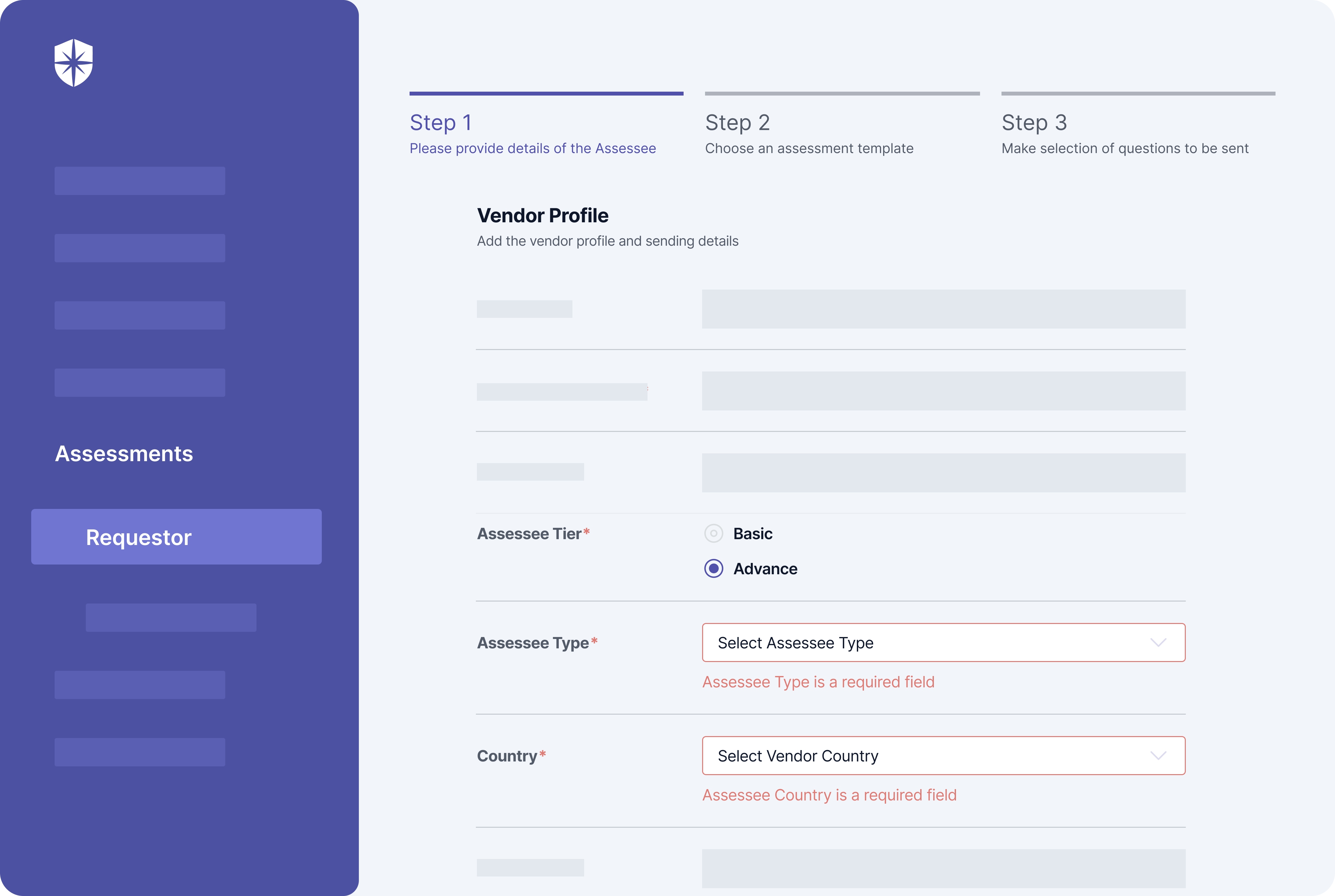
How does Cyber Sierra help you manage third-party risk?
As emphasized, conducting thorough checks on third-party partners is crucial for businesses. It goes beyond merely ticking a checkbox; it’s an ongoing effort filled with inherent risks.
Developing a robust Third-Party Risk Management (TPRM) program may seem daunting without a dedicated solution. Fortunately, your team can streamline critical processes of your vendor risk management program with Cyber Sierra.
Our unified cybersecurity platform empowers your team to assess, onboard, and manage your vendors’ security and compliance posture in near real-time, enabling you to mitigate vendor risks much faster. Ultimately, Cyber Sierra serves as a proactive partner, integrating governance, risk management, and cybersecurity adherence into a complete cybersecurity solution. Schedule a demo today!
FAQs
How can a TPRM framework benefit your organization?
A TPRM framework provides several benefits, including enhanced risk awareness, better decision-making regarding vendor partnerships, improved regulatory compliance, and protection of organizational assets and reputation. By systematically managing third-party risks, organizations can minimize the likelihood of vulnerabilities, data breaches, financial losses, and disruptions to operations, thereby safeguarding their overall resilience and competitiveness in the market.
How often should you conduct third-party risk assessment?
It is recommended to assess new third parties during onboarding, before audits, upon contract renewals, during incidents, during termination of partnerships, and also periodically whenever there are changes in the control environments.
Is there software for conducting third-party risk assessments?
Yes. There are specialized third-party risk management software and tools to perform risk assessment. These tools enable you to conduct assessments following a questionnaire, automate tasks, manage data, and offer insights into risks, streamlining the entire third-party risk management process.





















A weekly newsletter sharing actionable tips for CTOs & CISOs to secure their software.
Thank you for subscribing!
Please check your email to confirm your email address.
Find out how we can assist you in
completing your compliance journey.